With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.
Alright, fellow HoloLens code wranglers, load up your word processor because it's time to spruce up your résumés. According to a report by Variety, Netflix is looking to hire a new Senior Software Engineer — and Windows and HoloLens were mentioned as an end point.

Dr. Michael Pound, a computer science researcher and professor at the University of Nottingham, uses hashcat and 4 GPUs in parallel to go through 1o billion hashes a second in this Computerphile video. He calls his deep-learning server the "Beast." If you're new to cracking passwords, he does a great job breaking down the process of what's going on as hashcat does its magic.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

Here's a small-medium sized PvP arena that I made with my friend a few days back on my personal bukkit server.

The importance of paint cannot be underestimated when it comes to correctly constructing a reborn baby doll. There are many tutorials showing you how to correctly replicate the hair on your baby doll's head, but what about the eyebrows? This tutorial shows you how to use a variety of paints and fine tip brushes to correctly achieve realistic eyebrows as well as head hair for your next reborn project.

This tutorial shows you a variety of couture techniques you can use when home sewing to attach buttons and create buttonholes. Use bound buttonholes, space your buttons and make sure that your buttons and buttonholes line up to each other.

A shield makes a fantastic defense in boffer combat. If your character uses a shield, you're going to want to make sure to get the most out of it. This video shows you a variety of shield techniques you can use to protect yourself in boffer combat or fighter practice.

When you think of biscotti, you probably picture sweet, hard slices of bread dipped in chocolate and covered in almonds. While it's true that most forms of biscotti are of the sweet variety, you can also whip up salty, savory biscotti.

Contrary to popular opinion, Chinese food does not only consist of orange chicken and friend rice (though, admittedly, they are quite delish). In fact, there exists quite a variety of elegant, delicate dishes for the picky gastronome.

In this video, Betty makes a variety of floats for summer. She shows you how to use various flavors of soda and ice cream to make interesting treats for the warm weather. Enjoy these sweet, cold, refreshing treats for desserts or everyday snacks in the warmer months. Yum!

Angel fish live in tropical waters and are known for their extremely sharp-looking, angular fins and pointy faces. They also happen to be incredibly beautiful, coming a variety of opalescent colors and often striped like a zebra.

Sometimes the background you're using in a photograph doesn't quite match up with your subject and you want something different to highlight whatever you're photographing. There's where Photoshop and/or green screens come in.

Did you know you can create your own brushes on Photoshop? You're probably already overwhelmed by the variety of brushes, brush diameters, and other various picture settings that Photoshop offers, but if you're a professional artist or graphic designer it's sometimes necessary to create your own brush for a project.

See how to create arrays of objects in 3D Studio Max. While there are a variety of methods for generating object arrays, this clip looks at two of the faster methods for creating 1D, 2D & 3D arrays. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the application, you're sure to be well served by this video tutorial. For more information, take a look!

In jewelry making, string art is one of those techniques that creates a complicated looking result but is actually very easy to do. Composed of differently hued strings wrapped around a teardrop shaped pendant, string art can be used for various jewelry projects.

Want a fruit smoothie? While we can't recommend asparagus or cheddar-flavored drinks, we encourage you to experiment, using this road map to the ultimate healthy blended beverage. Remember to be creative -- mix a variety of fruity flavors.

Chest hooping is no more complicated than spinning at the waist, and has a great variety of movement possibilities because of the variable choices of arm and shoulder placement. Safire, expert hula hoop dancer, walks through the simple steps of doing this stunt, breaking down each movement to exact body positions and also thoroughly explaining any of the hula hoop choreography terminology she uses. Watch this video hula hoop tutorial and learn how to rotate a hula hoop at chest level.

Grafting, also known as "top working," is simple-but-essential technique that enables you to change the variety of fruit a tree bears. In this tutorial, Stephen Hayes of Fruitwise Apples Heritage reviews the essentials of top working while discussing an apple tree that was successfully grafted a year prior.

Life is not always a walk in the woods, but when it is, make sure you don’t step in the poison ivy. Leaves of three, don't touch me or Leaves of three, let it be is a pretty good rule of thumb as poison ivy comes in many colors and varieties. This video nature safety tutorial shows how to look out for and prevent the uncomfortable burning that results from any contact with poison ivy.

Aperture's book feature enables you to make elegant customized photo books in a variety of formats.

Final Cut Express provides easy setup options for a variety of video formats, but if you're not sure what format you're working with, Final Cut Express can automatically set the sequence to match the size and frame rate of your clips. When adding the first clip to a new sequence, the program will ask if the sequence should be changed to match the new clip. You don't have to work with all the same format, either, thanks to Final Cut Express' powerful open format timeline.

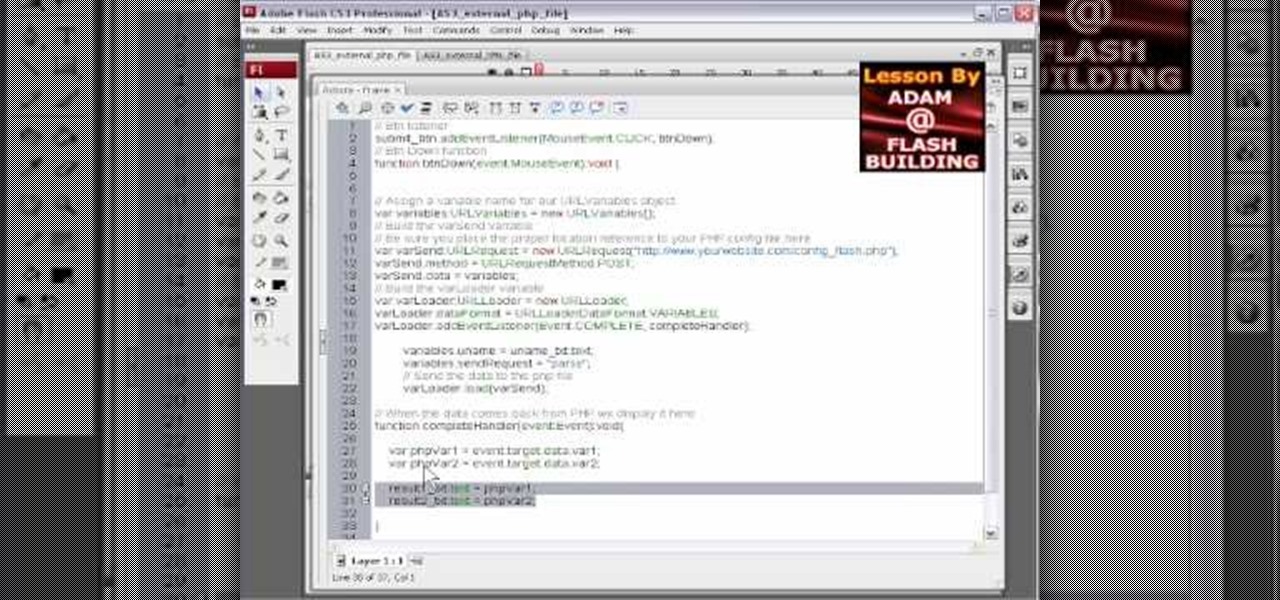
All the files you need are in a free download on DevelopPHP. PHP has to be on a server. It will not run on a local machine. Type your name. There are two variables which show up in the dialog boxes (which are stacked.) You can change the user name. It sets up a URL request and a URL loader and sends some URL variables and are placed into the value of names and pairs. They get posted to the PHP file. Place the URL reference location of where the PHP files are on your server in the line that sa...

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

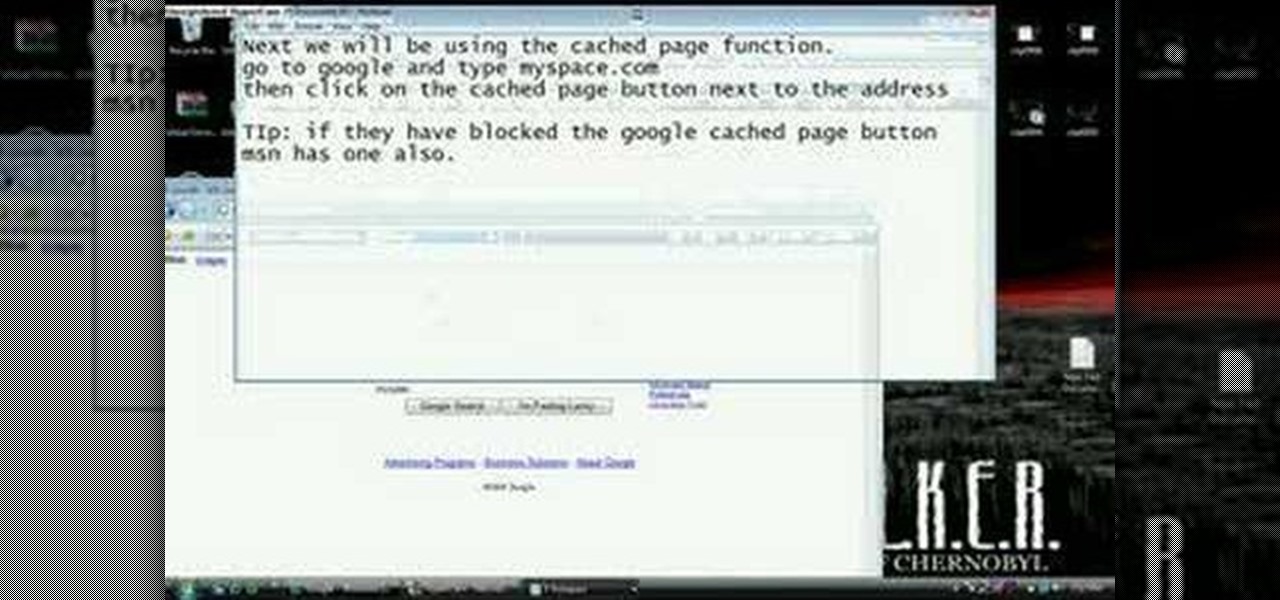
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Before watching this video we never knew there were so many different varieties of chile peppers, nor that each variety has a different degree of spiciness, measured in heat units.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.