A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

If you have an iPhone or an iPod Touch then you probably think that the only places you can listen to your MP3 files are on your laptop, your i-gadget of choice, and your car. But in reality anything that you can groove to on your iPhone or iPod Touch can be listened to - and transferred to - your PlayStation 3.

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

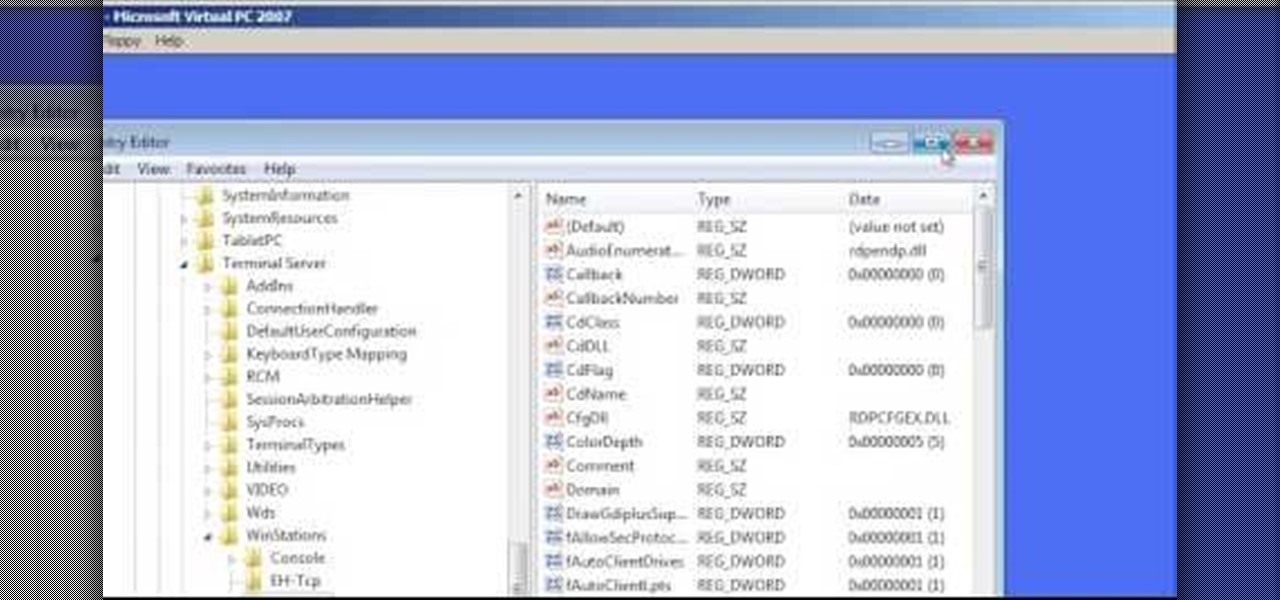
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...

Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

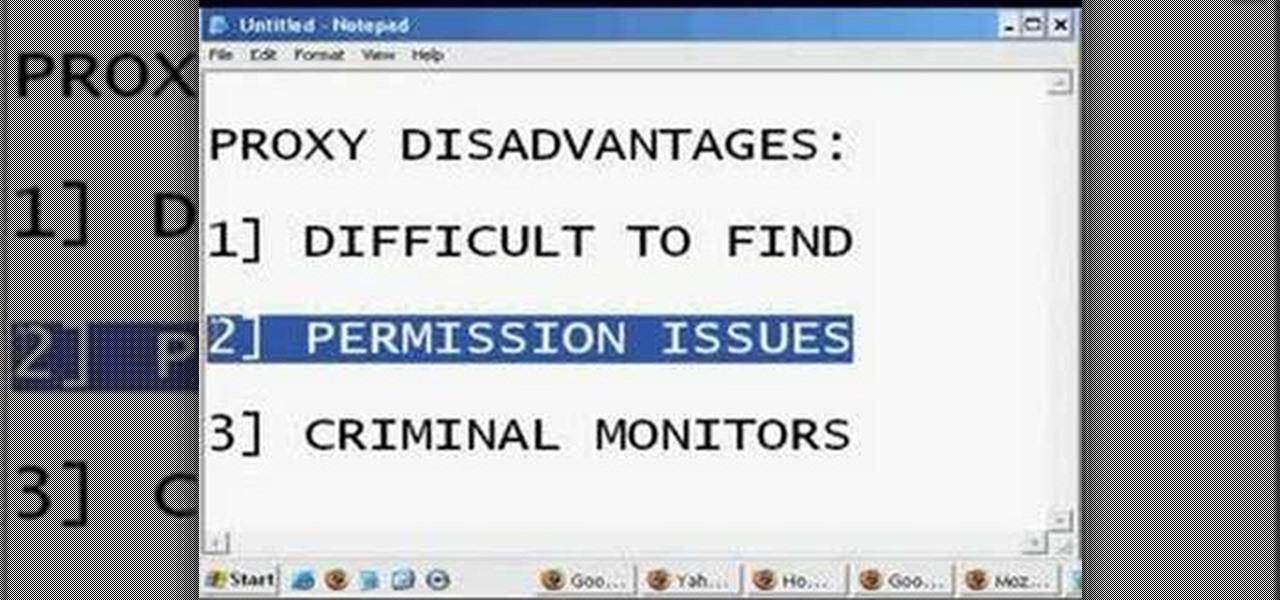
Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

In this tutorial, we learn how to configure Outlook 2007 to work with Gmail. First, go to the start menu and then open up Outlook. From here, go to tools and then options. After this, go to the mail setup tab and then click e-mail accounts. Then, click on "new" and then next. Enter in your information in the blank boxes on the screen. Then, enter in your e-mail address and make sure the server is not checked on this screen. From here, you will continue to go through the wizard until it's comp...

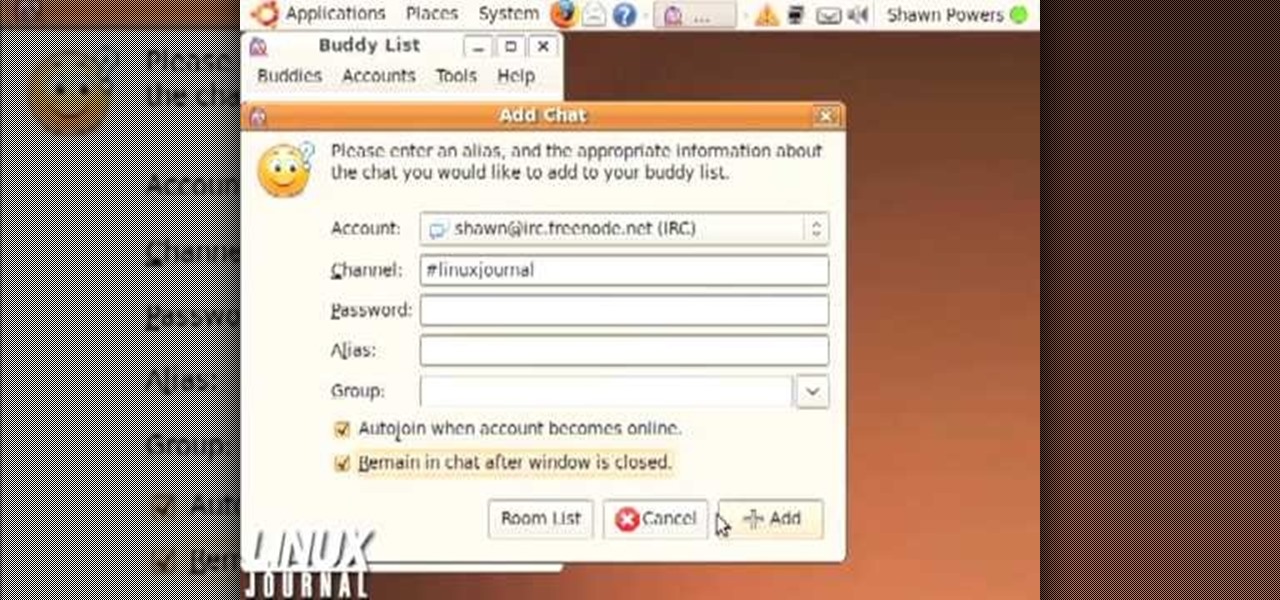
This video shows how to enter an IRC chat with a program called Pidgin, which is normally an instant messaging client. First, you should open Pidgin and open the protocol IRC, selecting or creating a username and changing the server to irc.freenode.net in order to connect to the Linuxjournal channel. After connecting to the channel, wait until you are connected. At this point, you should still not be able to see anything, so you have to go to "Add Chat" and join a channel, in this case #Linux...

In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

In this video, we learn how to bypass WebSense at school using an http tunnel. First, open up Internet Explorer, then type in http tunnel and go to the website. Download the first link to your computer. Next, start the program and click on "free service". Now, open up the browser again and go to "internet options". Once you are on this, go to "connection", then "lan setting". Check to use a proxy server, then click "advanced", then enter in "http 127.0.01 port 1080". Click "ok", then exit out...

In this tutorial, we learn how to use Microsoft SharePoint to view Acrobat 9 reviews. First, go to the comment bar and click "send for shared review". In this wizard, click internal and then click next. Then, click SharePoint workspace, then type in the URL to the server, then click "get workspaces" and you now may have to enter in your username and password. Now you will have to choose your workspace and document library. After this, click on next and click if you want to have it attached fo...

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.

Seems like everybody's blogging on the web these days. If you don't want to be the last one to the party, CNET shows you how you can get started with your own blog. If you know how to use a web browser, you should have no problem! Most bloggers use blogging services like Blogger or WordPress. Other sites like MySpace also let you blog. Or if you want, you can set up a blog on your own server. Learn all about getting started.

In this video, we learn how to control your Windows PC with an iPod Touch or iPhone. First, go online and search for 'Logitech touch mouse server', then download and install this software. Now, go into the software and launch it on your phone. You should now be able to use your computer and your phone simultaneously as long as you have a wireless connection. Now, you will be dragging the mouse on your phone and it will be working on your computer. You will have full functions while using your...

This video tutorial is in the Computers & Programming category where you will learn how to set up an FTP connection using Firezilla. Open up your filezilla program. On the top left, click on the file menu button, and select 'site manager'. In the window that opens up, select 'new folder' and give it a name. Now create a site to store in this new folder. Click on 'new site' and name it. Now on the right hand side, enter the host and the port. The default port is 21. Under server type, select F...

In this tutorial, we learn how to stream web content to your PS3. If you want to do this for free, you will go to PS3 Media Server. Once on this site, you will download their player, then you will be able to stream content from your computer straight to your PS3. This will give you real time audio and direct streaming of movies. You can do this one other way, which will cost you $49.99, the website you will visit is PlayOn. When you download this, you will be able to stream advanced content t...

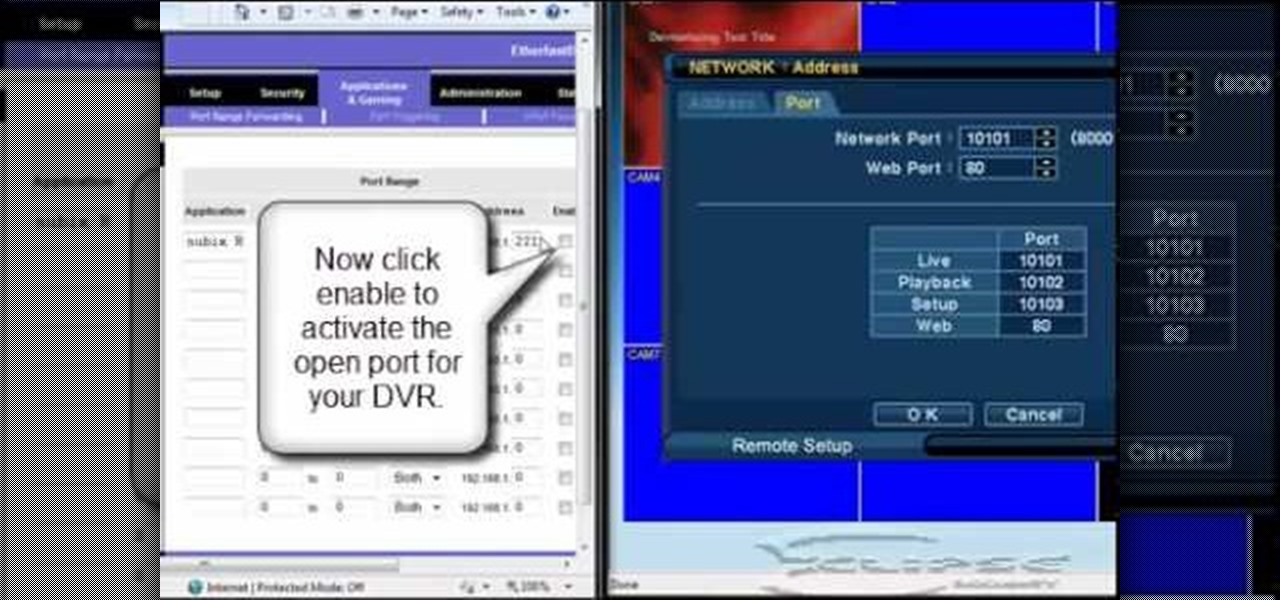
In this tutorial, we learn how to open ports on a Linksys router for your DVR. First, make sure your internet is connected and your DVR is connected to Linksys. Next, log into your Linksys router online and set up your DVR to the "DHCP" section. When you have the information from this, enter this information on your DVR so it has the correct server name. Make sure the IP and other information displayed on your Linksys page is the same as the setup on the DVR page. When finished, change your p...

In this video, we learn how to reset your wireless router. You can use this if you are getting the "server can't be found" error, and it will work most of the time. First, grab your router and unplug the electricity and DSL plugs that are in the router. They will be round and look like post, and shouldn't be hard to find. After you unplug it, plug it back in after about 30-45 seconds. This will reboot your router, so it will most likely fix the problem you are experiencing. You should be able...

In this tutorial above, you'll be finding out how to quickly set up IMAP in order for it to run with your Gmail account. Now first thing is first, IMAP has nothing to do with apps or anything else that is Apple. What it stands for is Internet Message Access Protocol. And what it does is that it's basically email but differs from the other email retrieval program, POP. It keeps email messages in the server while POP deletes them. So check out how to set it up with your Gmail account today! Goo...

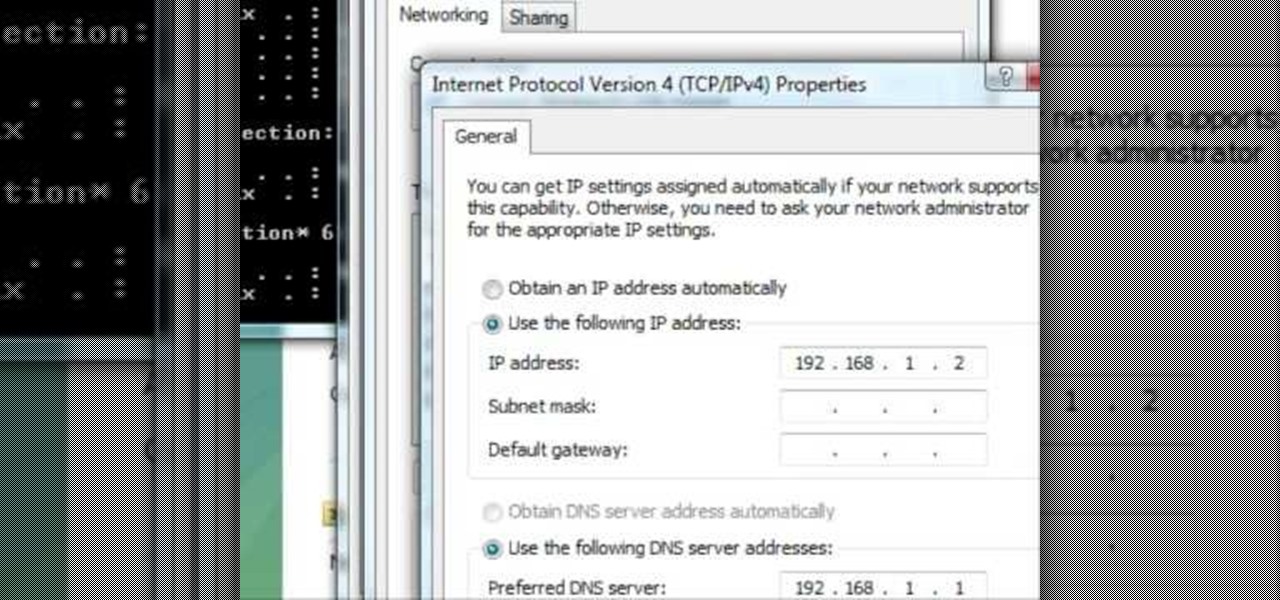
In this tutorial, we learn how to change an IP address in Windows Vista. First, open up cmd on your desktop and a new window will pop up. When the black window comes up, type in "ipconfig". You will now see your IP address, leave this window open and open up the control panel. Once in the control panel, click "view network status and tasks", then click on "view status". After this, click "properties" then click "internet protocal version 4" and click on "properties" again. Now, type your IP a...

In this Software video tutorial you will learn how to setup email in Microsoft Office Outlook 2007. Suppose you have a Yahoo email id and you want it in Outlook, go to tools > account settings > email > new and fill out the details. Then check the box next to ‘manually configure server settings’ and click ‘next’. In the next box, choose the 1st option and click ‘next’. To get the information for filling up in the next box, go to the Yahoo page shown in the video and copy and paste...

This video shows us the method to use iPad as a touchscreen monitor for your Mac. You have to use iDisplay available on app store. Start the application on your iPad and Mac. Tap the server on your iPad and on the Mac click 'Confirm' to connect it to iPad. Hit 'OK' on iPad. Now you can open a window on the Mac. You can drag the window out of the Mac screen on to the iPad. Now it will act as a touch screen. You can use all the touch screen features of iPad for this window. You can drag the win...

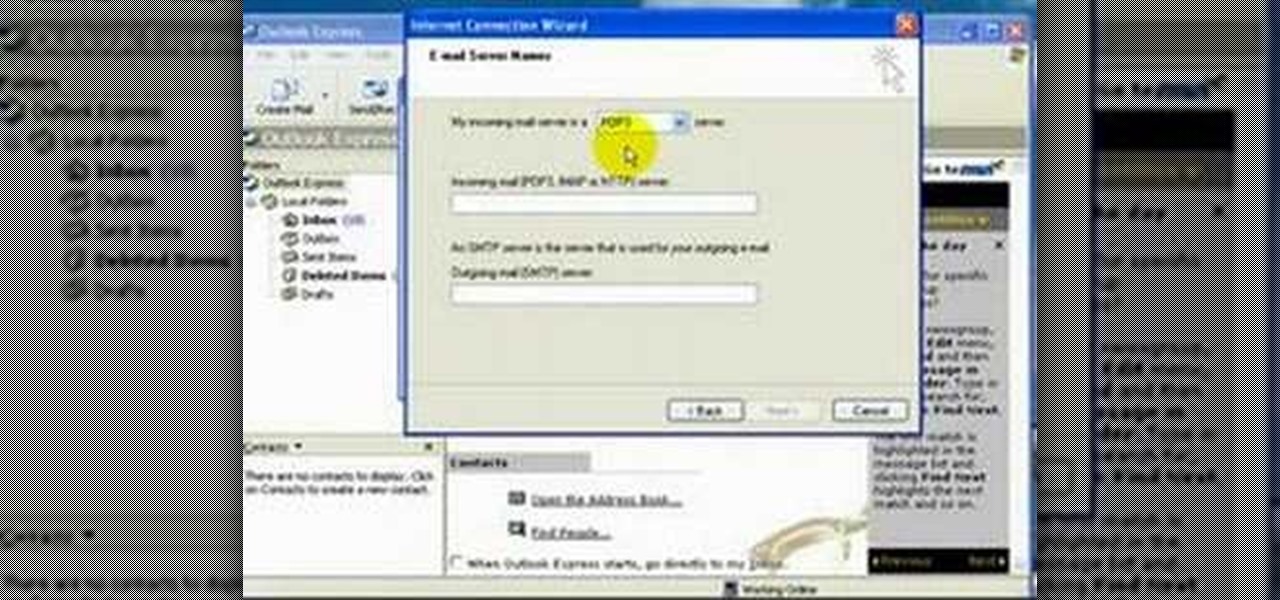
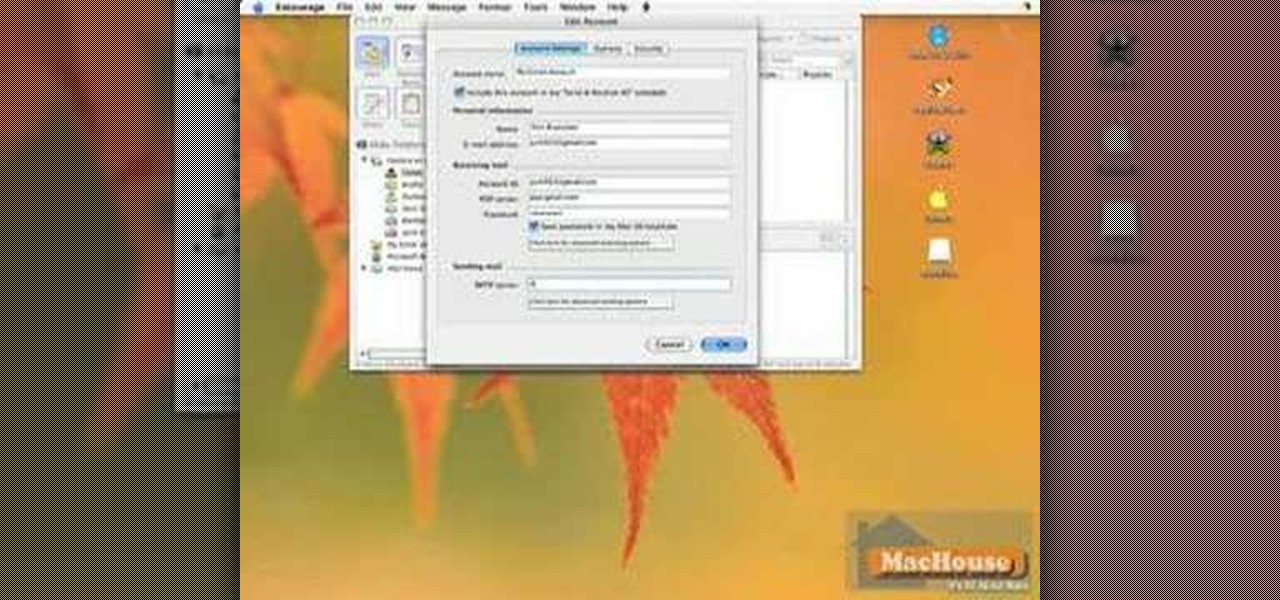
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...

In this video tutorial, viewers learn how to open ports on a Windows XP computer. Begin by clicking on the Start menu and open Control Panel. Double-click on Network Connections and select your network connection. Right-click on it and select Properties. Click on the Advanced tab and click on Settings. Select the Advanced tab again. Click on your internet connection and click on Settings. Click Add and fill in the port information. Click OK. T forward a port, users need to go to their router'...

Brad Garland guides us through the process of sharing our media files so that they can be stored on a single computer in our home, and played on any computer that is connected to this computer with iTunes 9. Using this technique, he and his wife can not only play the music that's stored on the central computer via their laptops, but also copy the desired music and videos over to their laptops much like they would for an iPod. Brad explains that he does not include Podcasts in this process, be...

Log in to your account. Go to settings, then go to Forwarding and POP. Then, check in the box for enable POP for all mail. Next, save the changes. Then go back to the settings page and check the first box (to include the mail that has already been downloaded). Save your changes again. Next, select tools>account. In the box that pops up, select POP for the account type and hit OK. Name the account and fill in your email address and POP address. For the SMTP server, put in smtp.gmail.com. Then,...

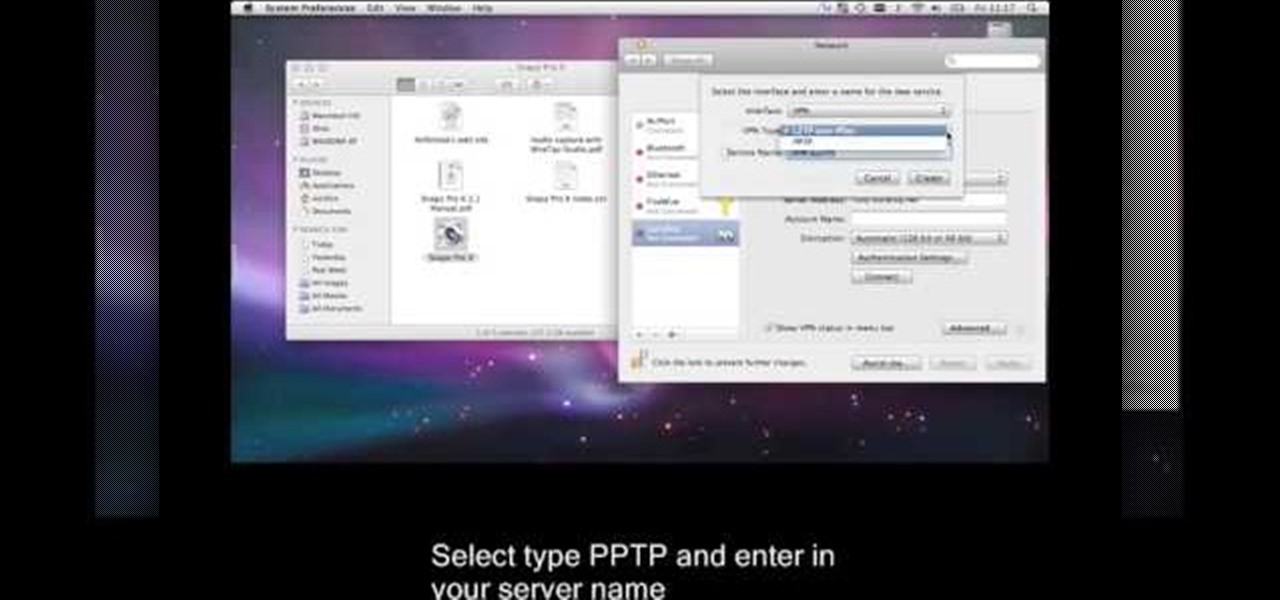
This is a video tutorial that is showing its audience how to set up your own VPN client on your Mac computer. The first step in setting up a VPN client is to go to your system preferences on your computer. Next select network and then select the plus button and type in that you will be making a VPN network. Next you should select the type PPTP and enter your server name. Then you can click on create and it will create a new network for you. Next you should enter your service address and your ...

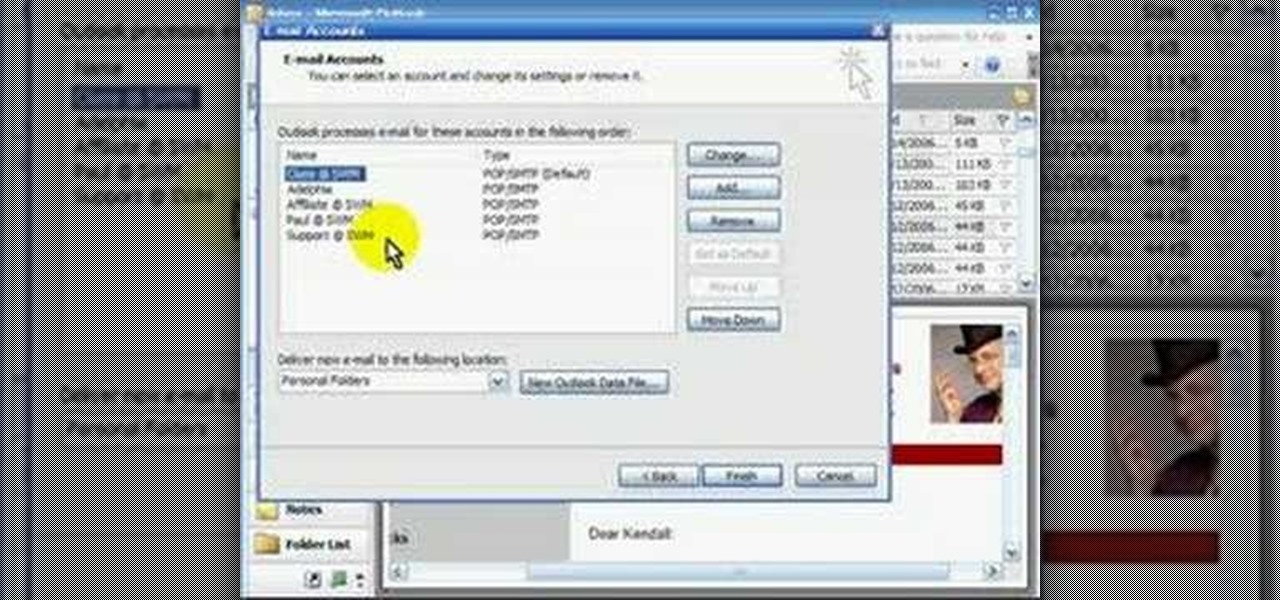
POP3 stands for Post Office Protocol, a way in which you receive mail on the internet, paralleling how mail is received in your mailbox. To set up your POP3 for Outlook, go to tools, click “view or change existing e-mail accounts’ and press next. You’ll be able to see a list of your current email accounts that you can change or remove. When you select an email and press change, you’ll be able to see the account in detail: the email address, the POP3 and SMTP server information, and th...

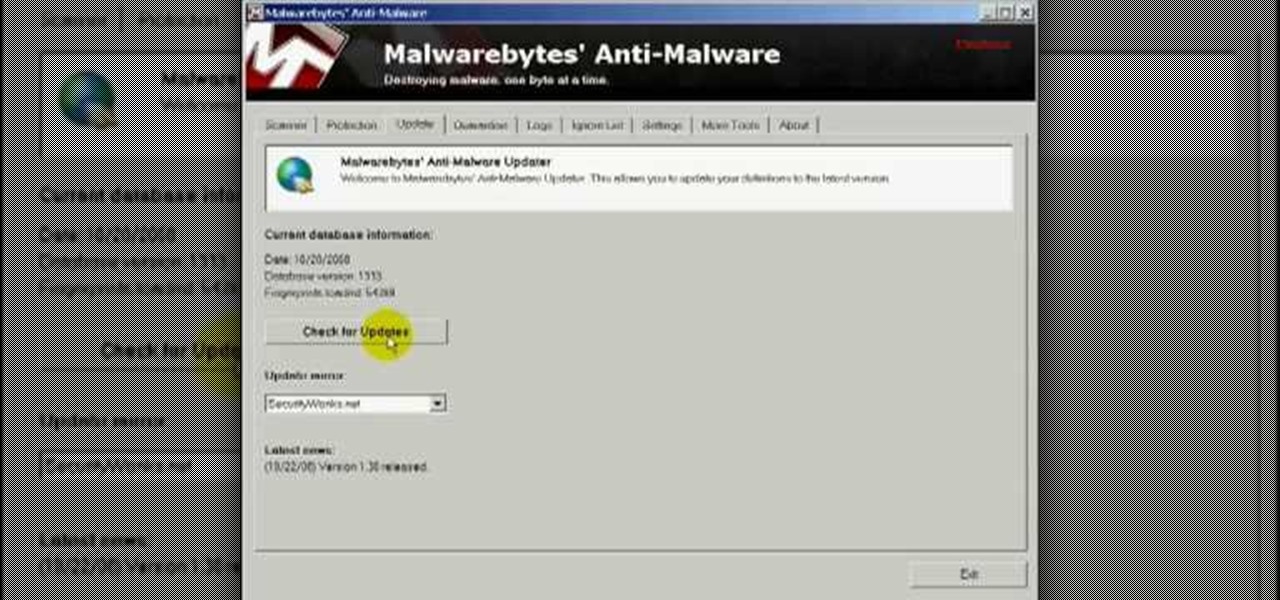
In this video you will learn how to remove the Trojan .dnschanger virus with Malwarebytes. To see if you got a Trojan .dnschanger virus go to your network connections right click on Local Area Connection, select proprieties, click ok internet protocol, click again proprieties and if you got an ip address at preferred DNS server that means that the Trojan entered a fake ip address. You can remove the Trojan. To do this first run the Malwarebytes application, click on the update tab, click on c...

Fetch is an FTP program for Macs (Smart FTP can be used if you don't have a Mac). These can be downloaded from Download.com