We all know the G-spot as that sensitive area that drives women crazy, but for auto enthusiasts, it has a whole new meaning. The G-Spot, designed by Daniel Davies, is a vehicle immobilizer, which keeps your vehicles safe from car thieves. And you don't need to pay a huge amount of money to get one, either! You can make on yourself, right at home, provided you have all the right materials.

Creating a modern video game is a mammoth undertaking, especially if you are working alone. Hopefully, this video will make it a little bit easier. It will teach you how to create a custom class for your game's hero character using Flash CS4 and Actionscript 3. Doing so will make your main character react in predetermined ways to a variety of actions, which is very useful if you want the character to react consistently throughout the game.

In this tutorial, learn how to do a variety of very cool tricks. In the first, you will appear to solve a jumbled Rubik's cube in less than two seconds by jumping up and magically moving the pieces into place. In the second, learn how to stack dice like in a video game. The third will show you how to turn an ordinary playing card (no gimmicks!) into a boomerang and finally you will train a disc to return to you when you throw it, as well.

Mr. O shows his audience in this video how to make oobleck, a slime-like substance which has a variety of unique properties. For this project, you will need a mixing bowl, food coloring, corn starch, a measuring cup, and water. First, color the water with food coloring to a color which is much darker than the color you would like. You will need the correct ratio of water to cornstarch, in a 1 to 2 ratio. Add some water to the bowl and add the cornstarch, then add the rest of the water. Finall...

This how-to video shows you how to make boiled wheat. To do this, take some wheat and put it in a pot. Pour some water into the pot and put it on a stove in order to boil it. After about 45 minutes to an hour, you will now have lovely boiled wheat grains. You can use this dish as a side dish. You can also use it with natural yogurt, fruit, and cinnamon for breakfast. Another alternative is using milk, peanut butter, and honey. You can also use it with a salad. Just add lintels, parsley, salt,...

This video demonstrates how to make a variety of ghillie suits. You can adapt your camouflage to many different environments to make yourself more invisible. Additionally, this series shows you how to make multiple types: rifle covers, partial suits, equipment covers, etc.

In this video tutorial, viewers learn how to read a micrometer. This tool allows the user to accurately measure components. They have the ability to measure dimensions accurately to within one hundredth of a millimeter. Micrometers are designed with a wide variety of styles and sizes for normal or specialized applications. Micrometers are able to measure the internal or external dimensions of a component. They are the most important basic measuring instrument used in the metal industry. There...

Are you interested in parties and cocktails? Let's make a Jagermonster cocktail. Start with a rock splash and ice it up a little bit. Next, get another glass for an ice mixture, one ounce of Jagermeister, and a little bit of grenadine. Then, add 4 ounces of orange juice. Shake it up well for a good mixture, get rid of the previous ice in the glass, and pour it in. This will provide a variety in your list of cocktails.

You can use the Canon EOS 7D to shoot digital video at a variety of frame rates and resolutions up to full HD. In this video, see the basics of movie mode and how to use it. This is the best digital SLR camera to film video with.

There is no better addition to a barbecue than a classic sangria. Rebecca shows an easy way of making this Spanish punch. There are various types of sangria which can be prepared easily by just changing the flavor through the use of a variety of fruits.

In this video tutorial, Creative Cow leader Michael Park shows you how to recreate the opening gun barrel sequence from the two newest James Bond movies in 3d Studio Max using the default scanline renderer, minimal modeling, and only standard materials.

Paste this code: shutdown -s -t 10 -c "Your Message Here" One of our viewers brought up that -s would simply shut down your PC, and not keep restarting it. To do so, substitute -s for -r and you should be set!

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to mod a USB flash drive.

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper.

In this Forehand Fundamentals video, we talked about how you need to take your racket back to complete your preparation. This video goes into more detail about the backswing and discusses the wide variety of backswings you see on the pro tennis tour.

No more do you have to buy additional equipment just to send a quick fax out. And no more going to the local copy store to pay for faxes. Windows 7 has a great feature built right in called Windows Fax and Scan. See how it works.

This video will show you an interesting trick which you can use to access Facebook or other web pages on a school server or other place where Facebook is normally blocked with the help of Google. You will need to first go to the Google homepage and find the button at the top of the toolbar which says "more" and go to the pull-down option of "even more" options. This will open up a new web page. You should then go down to the "translate a webpage" option on the right hand column of results and...

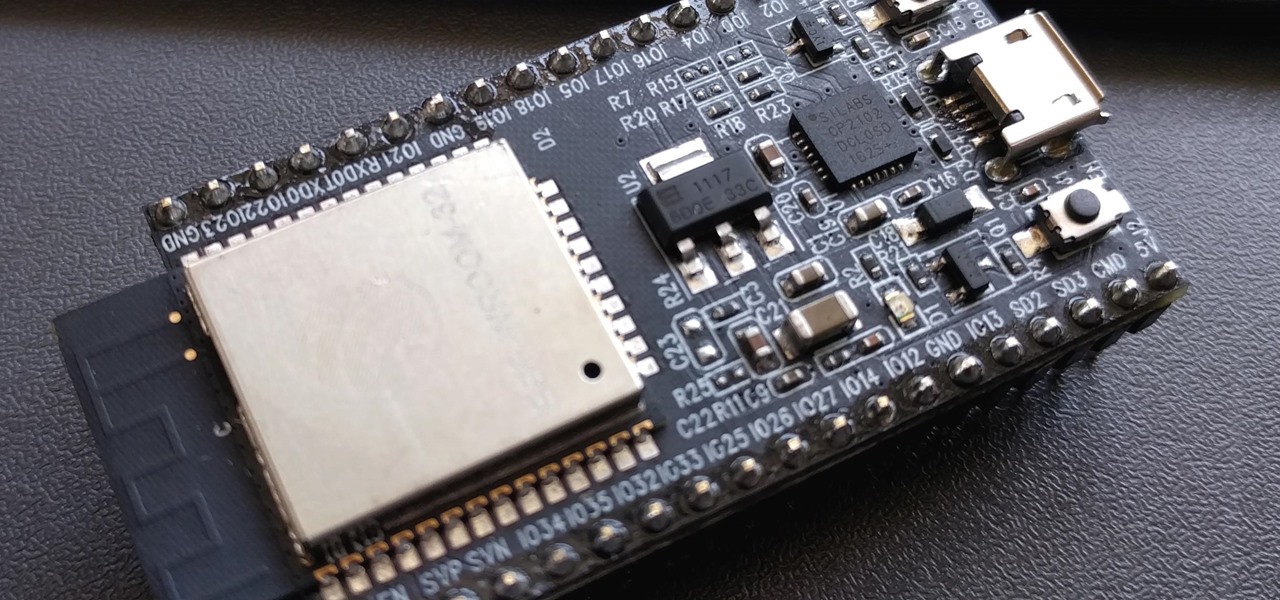
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

When you're on the go, Plex makes sure your media always stays with you. Just install the server app for Mac or PC and enable remote access, then you can stream movies and TV shows from your computer to your phone over the internet.

Many Android users woke up on January 10 to discover that their phone's performance took a nosedive overnight. Battery life is draining fast, overall performance has been sluggish, and devices seem to be overheating for no apparent reason. Not to worry, this isn't happening because of something you did.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

With the release of iOS 7, the entire Internet was abuzz with what's the exact opposite of excitement as Apple's servers were overloaded, causing many download fails of the new operating system. Since then, many other bugs and issues have arisen that are fairly common with new Apple software updates, like iMessage fails and wallpaper complaints (to only name a few).