This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

This is going to be guides on the Bukkit plugin and Minecraft Mod. WorldEdit is an in-game world editor for Minecraft, supporting both single player and multiplayer. It is easy to use, extremely flexible, and actively developed.

Are you bored with ordinary meals? Why not tap into your adventurous side and try Starfish? Yes, that's right, those cute little fish that you see on the sand - you can eat them! So, if you are interested, check out this video and master the techniques needed to eat these spiny sea creatures.

With Tim Burton's revival of Alice in Wonderland, throw one of the hottest parties in town with a "mad tea party" themed party. Recreating one of Alice in Wonderland's most famous adventures is a great theme for all kinds of celebrations. Set the scene with these suggestions.

Looking to make a nutritious change in your life? By choosing the right foods in the right amounts, you can reap rewards that will benefit you in all aspects of your life. In this tutorial, learn how to eat healthy and make positive changes in what you consume.

As most of you already know, the White House is the seat of the Executive branch of government in the United States. Constructed in 1792, it is one of the oldest buildings in the U.S. During the War of 1812, it was burned down and later rebuilt. The White House was inspired by a few foreign government buildings and is somewhat Greek in appearance.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Higher-fidelity 3D content and next-generation AR experiences take more computing power than most modern AR headsets and mobile devices can handle. But Nvidia is introducing a new cloud-based solution to address that need that will stream AR content to modern devices.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has no such solution, but Google's looking to fix that with a huge update to the Android Messages app.

Google updates the Play Store periodically, but the changes are usually subtle. A recent server-side update, however, is shaking things up quite a bit.

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some iPhones and iPads, is no exception.

Niantic has gotten themselves into a bit of a mess regarding their hit game Pokémon GO recently. The company hosted a fan fest in Chicago earlier this month that ended up being a complete disaster.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

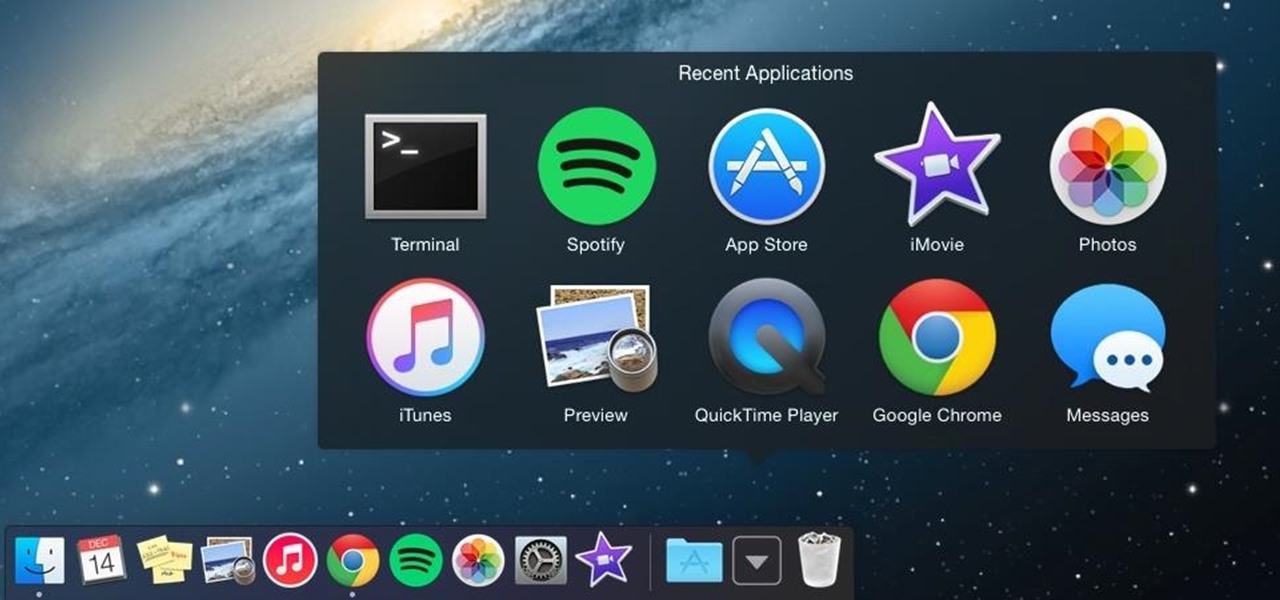
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.

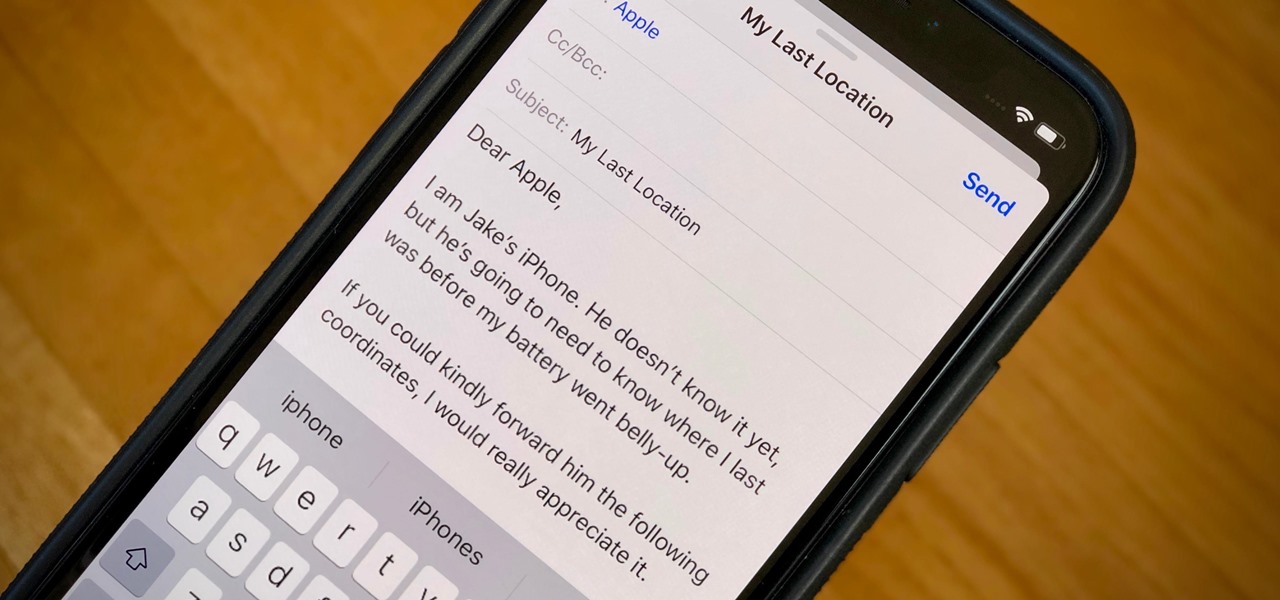
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Hello, freakje118 here, it is a while ago, but here are the winners of the easter builds! First place is this week for: Fedganac88
Hello, Freakje118 here! Today 13/04/2014 ends the Ice Castle Competition! What a shame only 3 people participated but okay, life goes on! Here are the winners and their prizes

Hey everyone, freakje118 here! This week, the first challenge ever will be to build an awesome and icy ice castle! It can be any size you want but please use the plots. Let your imagination work and make something great of it! you can use any blocks that you want! Ice, water, quartz, wool,.... But remember, it should be an ice castle!

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

The key to a successful indoor hydroponic garden is in both irrigation and lighting. This video can't help much with the irrigation, but if you want to decide what the best lighting systems are, this video is for you! There are a wide variety of bulbs and power sources that you can choose from when constructing your own hydroponic grow operation. The key is wattage, and the more wattage you can get out of your bulbs, the better your garden will be.

Yogurt has a variety of uses, some of which you may be unfamiliar with. For just $60 a cup you can whip up a (rather tasty) yogurt mask that combats acne as well as acne scarring. Yogurt contains lactic acid, which dissolves the top layer of skin to remove dead debris.

Entropy can be a tricky concept to wrap your head around, but this clear and detailed video helps make it easy. By using a variety of props as examples, you too can master the idea of entropy to amaze and impress your friends!

Gilder's Paste is what distinguishes a so-so piece of jewelry from a truly dazzling, memorable one. That's because Gilder's Paste, which comes in a wide variety of colors and tints, is a type of colorant for brass that can be mixed and applied for a unique look.

Remember when you were five and you had a blue crayon and a yellow crayon but all you really wanted was a green crayon? Just as you would mix colors in coloring and any other artistic medium, you sometimes need to mix icing colors in cake decorating.

Most people throw out the seeds and mushy innards of a pumpkin after they carve it, an act that is a sin against pumpkins everywhere. Yeah, the outer skin of the pumpkin is the only area you can actually carve, but that doesn't mean the insides can't be put to good use.

Caramel apples are sold in abundance at chocolate and candy stores during the Fall season, but why buy the store-bought variety (which has stayed on the shelves for an indeterminate amount of time) when you can make your own for cheap at home?

Saying that people have too much stress these days is an understatement. With Twitter, Facebook, and a variety of electronic gadgets occupying our time, there's hardly room to breathe or to relax. This means that more and more of us are finding it difficult to fall asleep.