I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Biting into a perfectly ripe mango is living proof of nature's goodness. The flesh is at once creamy, smooth, tart, and sweet. Plus they're incredibly good for you.
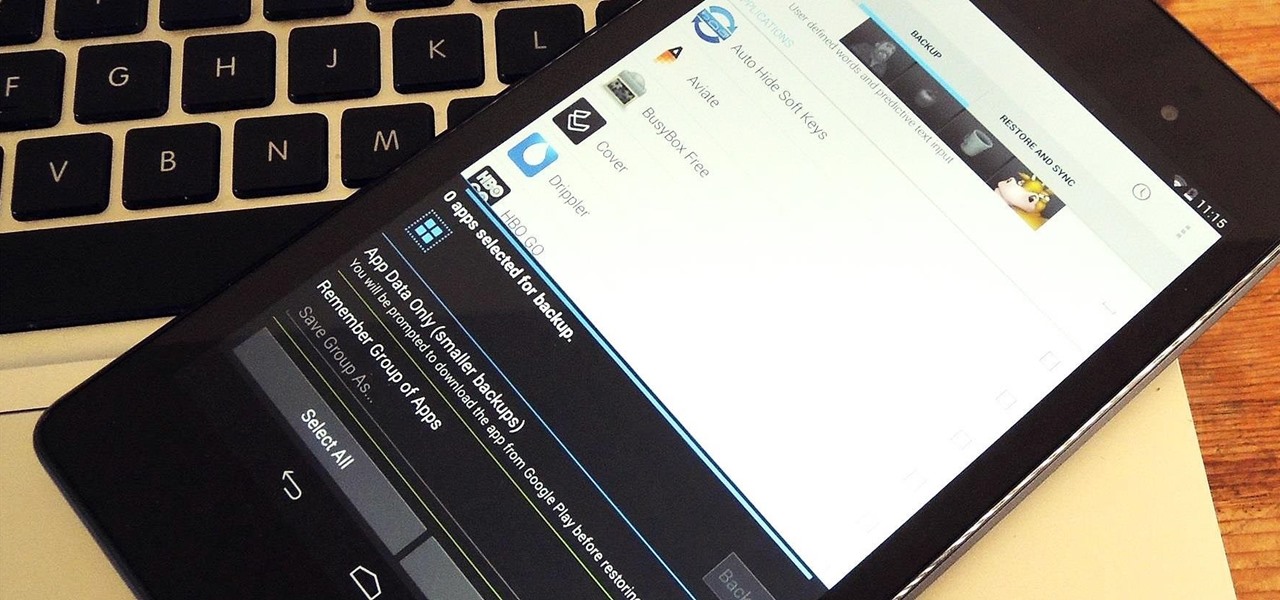
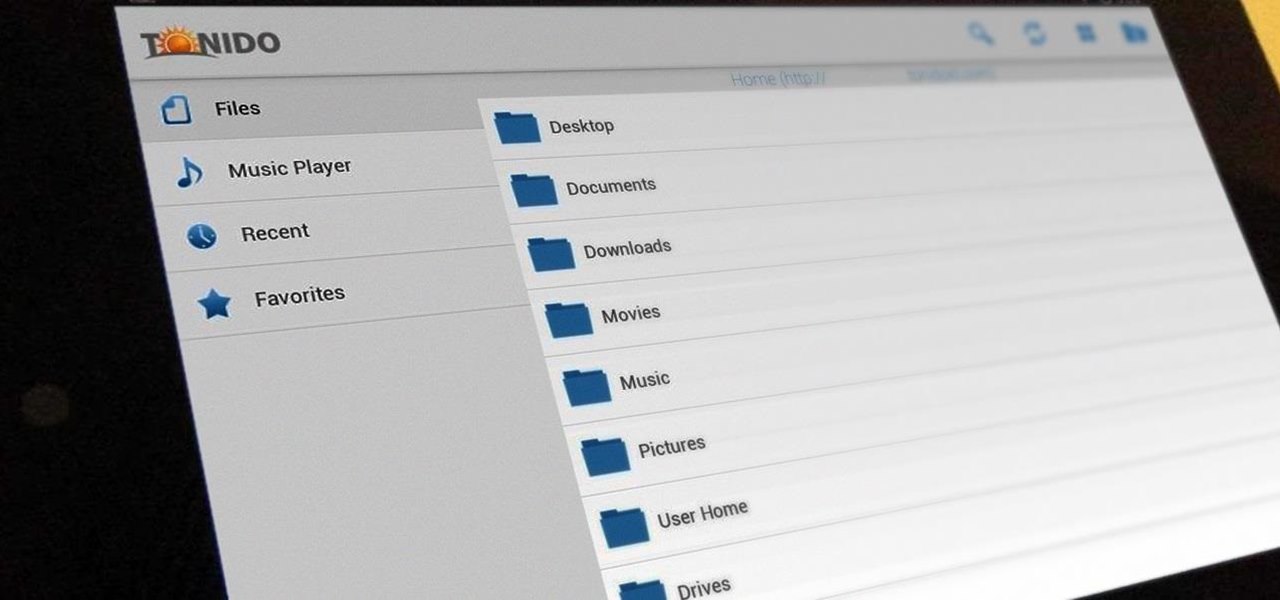
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily accessible on your tablet.

I'll be honest—I've never been a huge fan of camping. It's not that I have anything against nature, I'm just partial to showering and sleeping in my own bed. In fact, the only part of camping I've ever really enjoyed is sitting around a campfire. Outdoor fires are perfect for socializing and cooking hot dogs, but they're also great at helping remove one of camping's biggest annoyances.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

The next time a light bulb burns out in your house, don't throw it out. Believe it or not, burned out light bulbs aren't entirely useless. Besides creating an extra task on your to-do list, they can be hollowed out and used for a variety of different things from home decorations to miniature indoor gardens.

These lock picking tutorials cover some basics of single pin lock picking as well as the tools of a lock picking set. Watch the whole sequence of lock picking how-to videos.

Watch this demonstration on Spotlight on SQL Server Enterprise by Quest Software. Spotlight on SQL Server Enterprise is a part of the Quest Management Suite for SQL Server as well as standalone offering. This demonstration shows the use of Spotlight on SQL Server Enterprise within the Management Suite

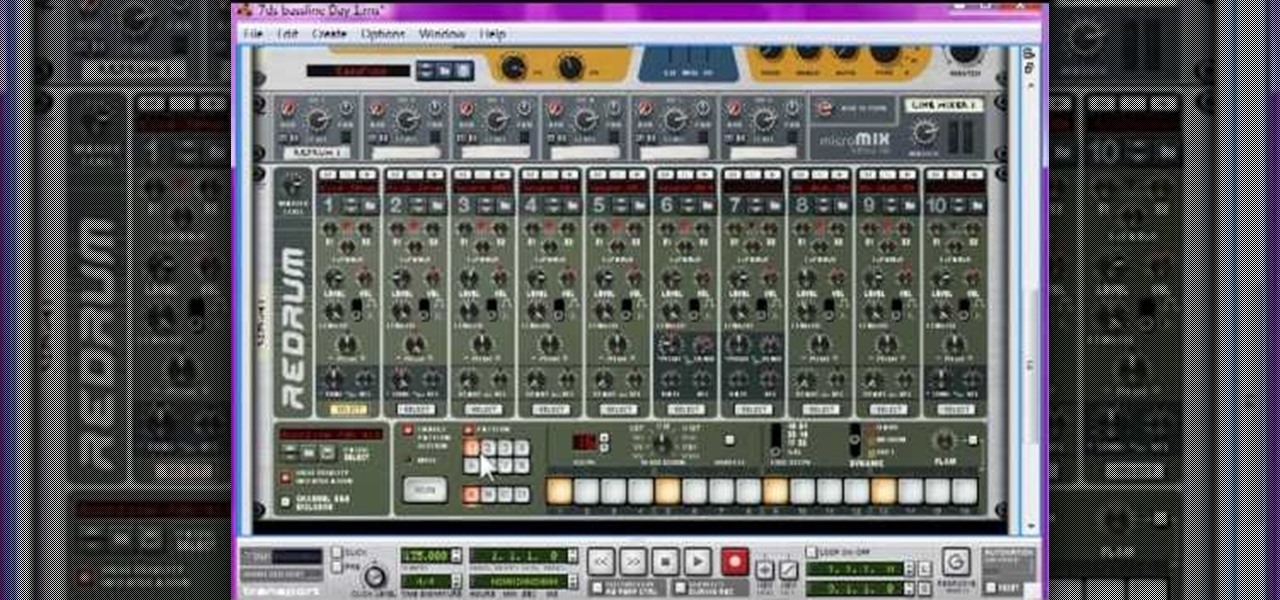
Bassline (otherwise known as 4x4 garage) is a popular bass laden variety of electronic music that has found it's way into mainstream pop production as well. If you want to start producing it, watch this video to learn, step-by-step, how to produce a 4x4 garage song from scratch in Reason 4.

Now that you're officially allowed to do it, jailbreaking your iPhone, iPod Touch, or iPad is a better idea than ever before! This video will show you everything you need to jailbreak a wide variety of Apple devices, including the iPhone 3G and 3GS, the iPod Touch 2G and 3G, and the iPad wifi or 3G model. All you need is a program called Spirit, iTunes version 9.2, and you device and you're good to go! This particular method is great because the jailbreak is untethered, meaning that you can t...

If you want to know the best way to get an accurate pH measurement, this shows the lab equipment needed and the processes used. When doing chemical reactions, sometimes the acidity or the basicity is important. This is usually defined as pH and measuring it can be very useful for getting the reaction right. There are a few ways to measure pH, and the simplest, cheapest, most reliable method is paper. But that's not all. See a whole lot of ways in this two-part video.

In this video from handmadetv we learn how to season and prepare chicken for grilling. You want to marinate your chicken before grilling. Marinades are made with a wide variety of seasonings. An Asian inspired one with ginger, garlic, red pepper flakes, sugar, sesame oil, and soy sauce, are mixed together to make a marinade. You don't have to worry about exact measurements. Change them up as you like. The container or bag can be left at room temperature for 30 minutes or 24 hours in the fridg...

Do you like adding garlic to every recipe you make. We'll you are definitely not alone. Learning how to mince garlic will take your love for garlic to the next level. This homemade solution will keep you away from the store bought variety, and will show how to create the perfect minced garlic effortlessly.

If you've never done it before, making a podcast can be tricky, with multiple programs to use and multiple file types to deal with. But, this video series helps you through the complete process of creating a podcast, everything including recording, editing, images, exporting, converting, uploading, and finally… sharing. Watch this whole series to learn how to make podcasts using GarageBand, iWeb, iTunes, and Fugu.

Aluminum nitrate nonahydrate is a crystalline hydrate - a salt of aluminum and nitric acid - Al(NO3)3·9H2O. It's used for a variety of things such as antiperspirants, corrosion inhibitors, and petroleum refining, or… glow-in-the-dark powder. Watch this science video tutorial from Nurd Rage on how to make aluminum nitrate nonahydrate with Dr. Lithium.

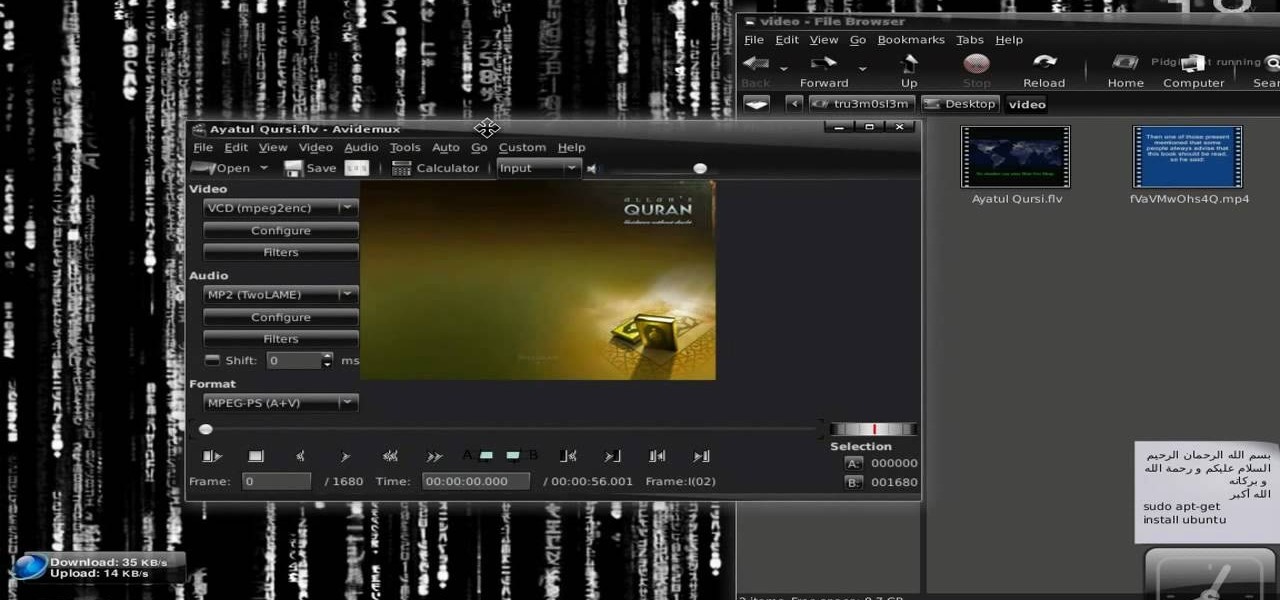
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to convert video formats with Avidemux on Ubuntu Linux.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to use color correction in Photoshop.

Learn how to build a remote controlled beer keg. Not only can you deliver beer to friends, but you can control the drinker's access to it. It's sort of like a remote control bartender!

Here is a step by step tutorial for making a swimmable mermaid tail. Check out Video #2 for a demonstration of the tail in use!

Are you aware of your water usage? Are you really doing all you can to conserve water, our most precious resource? Here are some simple ways you may not have thought of and some facts about the amount of water wasted on a daily basis in America.

This video tutorial teaches how to use molds with polymer clay to make a variety of different designs. Learn how to manipulate molds to make a variety of different polymer clay pieces out of the same mold.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

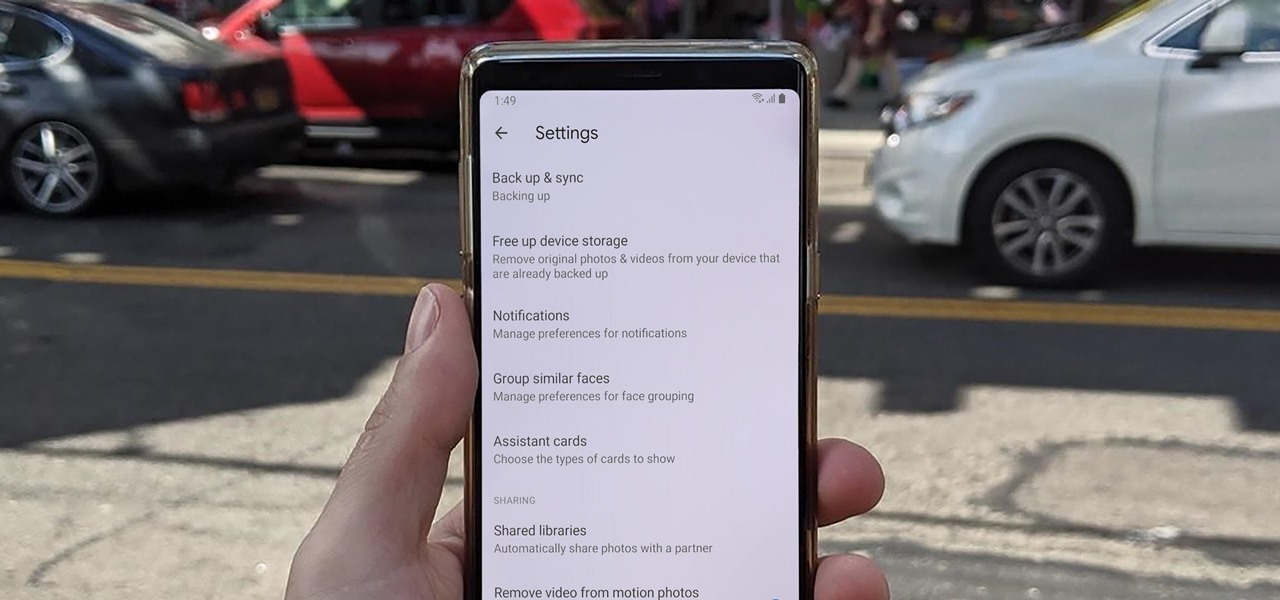
Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

The augmented reality cloud and multi-user experiences are shaping up to be one of the hotter areas of augmented reality, and now Google is the latest entity to back these emerging branches of AR.

Harry Potter fans can set down their wands for a spell, as the highly-anticipated augmented reality game from Niantic based on the franchise won't arrive until after July at the earliest.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

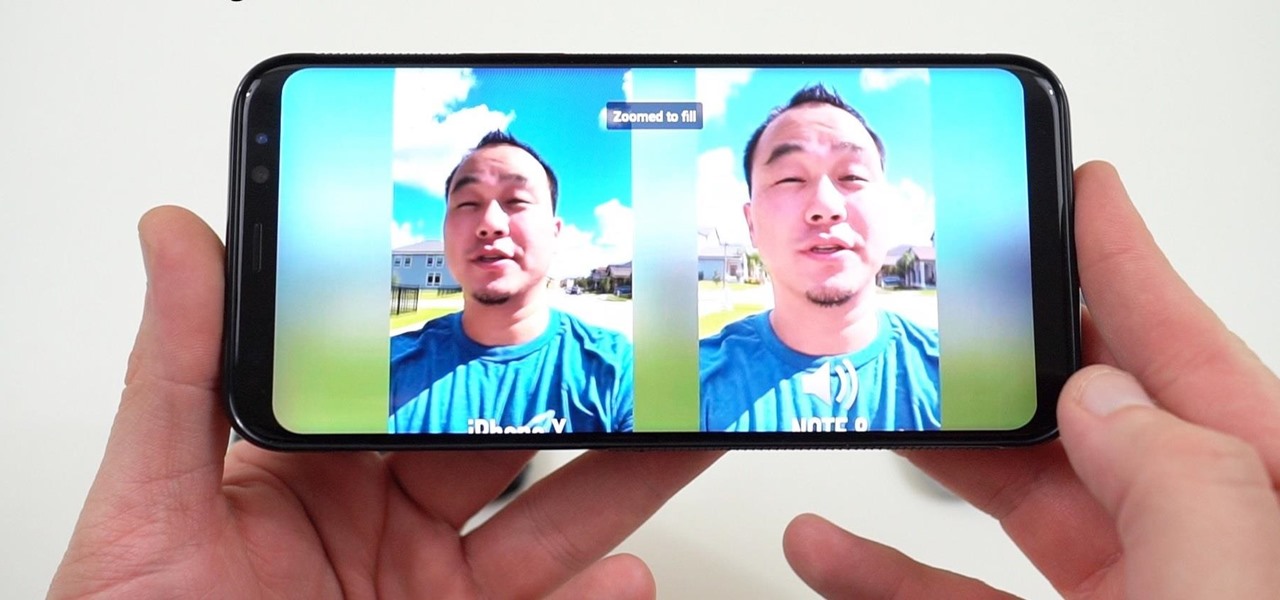
Google launched the Pixel 2 XL with a unique pinch-to-zoom feature in the YouTube app. The feature is pretty basic, allowing users to expand the video to full-screen on devices with 18:9 aspect ratios with a simple pinch gesture. Considering its simplicity, it was strange that the feature was limited to the Pixel 2 XL. Today that exclusivity has ended as the feature is rolling out to the Galaxy S8, Galaxy S8+, Note 8, LG V30, and LG G6.

A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.

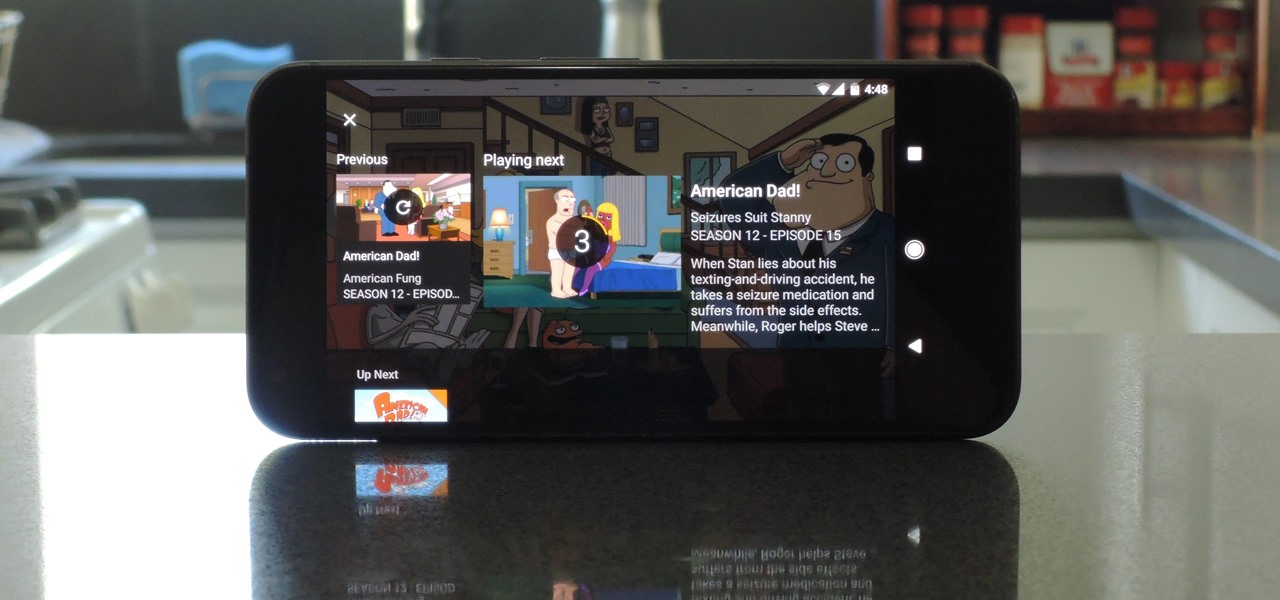
If you're new to Plex, there are a couple of things you should know up front. First is how to use it — simply install the Plex server app on your computer and point it to your media library, which you can then access anywhere using the Plex app for iOS or Android. All of this is free.