Blue corn is a special variety of corn which can be differentiated by the majority of the corn species by looking at the unusual top growth of the corn. It is a hybrid and grows very uniformly throughout. Now take a corn from the field and peel it off. You shall notice that it has a blue color corns. Blue color corns are hard from outside but they are very soft and tender in the middle. You can use these blue corns in making commercial products like blue corn chips, tortillas, and atole ’,‘ c...

There are a variety of substances that you can use to clean your LCD screen. The one thing you don't want to use is anything that has alcohol in it. Alcohol will damage your LCD. Any LCD cleaning liquid will work to safely clean your LCD. It is also good to use a microfiber cloth also so that they don't put any scratches in the screen. You should never use napkins, paper towels, or Kleenex. The primary ingredient in most LCD cleaners is water. The key is that they remove the impurities and ch...

As your home ages, so does your deck in the backyard, but there are ways to resolve this issue. If that wooden deck is looking weathered or worn, you can simply replace the components with composite materials without a complete rebuild. Composite doesn't splinter or have knots, and it's low maintenance. This two-part video, brought to you by Lowe's, will show you exactly how to renew your deck with composite decking.

Getting weird looks from the other dudes at the bar? Maybe because you're ordering a sex on the beach like the other women. Spit out that tropical drink or wine spritzer and throw away your stemware. It's time to put some hair on your chest, hoss.

Daniel Martin, a magician and escape artist, explains his technique for getting out of thumbcuffs. Disclaimer: We're pretty sure it's not illegal to know HOW to escape from thumbcuffs... but we're 100% sure it's illegal to actually escape when detained by law enforcement (just sayin').

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

The WordPress revolution has completely altered the way that people build and distribute websites. Instead of having to memorize endless lines of HTML and Java, both novice and professional web developers are now able to create incredibly detailed and responsive sites using a series of intuitive templates and plugins. And each new version of WordPress comes with an improved batch of features that make web-building even easier.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Often, the most frustrating part of crafting the perfect dinner is feeling like you have to clean every single pot and pan in your kitchen after cooking just one meal. With so many components, it can feel like each step of a single dish requires its very own pot.

We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around for a while and allow the pasta to essentially cook en casserole, this relatively new addition to the pasta scene includes elbow, penne, spaghetti, and rotini varieties that allow for usage in a greater variety of pasta ...

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

Simple Card Monday teaches viewers how to make a berry-themed card using Preserves Cricut! You'll want to use the Garden Variety Cricket Preserves paper for this berry-theme project. First, you should start off with an A-2 sized 5.5 inches by 4 inches sheet paper. Ink this using chamomile ink on all of the edges of the card. Next, add green onto the top of the card. It should leave a tiny border around. Now stick this strawberry paper with ribbon onto the polka dot paper. Cut your strawberry ...

Garden of Imagination demonstrates very simple method of how to make miniature doughnuts from polymer clay. There are three varieties of doughnuts made sprinkled, glace and chocolate covered. These are very simple round doughnut. For this we need a plastic clay measure which has balls of different size. We have to start off with a little piece of clay, put in size E of the clay measure. Always put some extra and slice it off. Take it out. Make it into the size of a ball with your hands. Now m...

A persimmon is not ready to eat until it has a soft consistency like jelly or pudding, though the fruit can be harvested and brought inside while still hard, so long as the branch the fruit hangs from is picked along with it. One way to be sure that a persimmon is ready to eat, is to press a finger against the skin of the fruit. If a fingerprint is left, the persimmon is ripe and delicious. Once they start getting soft they go bad very quickly, so it's good to prepare them so you can eat them...

Betty's at it again with a super-simple pot roast recipe that you can make in your crock pot. When's dinner?

Do your mussels not taste right? Beer can solve the problem. Irish beer to be exact. Spice up your mussels diablo with some good ol' Irish beer, like Guinness.

Hetal and Anuja from Show Me The Curry take us through the steps to make a tasty, fresh salsa which is an integral part of Mexican cuisine. You will need a food processor for this recipe, a blender would make the salsa to thin and soup like. First, add the following ingredients to your food processor. * 2 Large tomatoes or 4 Roma tomatoes, chopped * 1/4 of an onion, chopped * jalapeños - to taste (They used about 2 large jalapeños but you may want more or less according to your taste preferen...

Il Duomo's Secret: Super simple. The entrance is on the north end of the Basilica Santa Maria del Fiore. It's on street level, and really anyone could open it but only you're smart enough.

Get that extra oomph in your hair by teasing it! Teasing your hair will allow you to poof it up a little bit for styling purposes.

No ice cream? No problem! You probably have the ingredients at home to whip some up. Watch this video to learn how to make homemade ice cream in a plastic bag.

Learn how to weigh yourself correctly. Monitoring your weight is difficult when it can fluctuate three to five pounds in a single day. This system will help.

Everyone remarks upon the hands of the skilled pianist, but even the most dexterous keyboard artist couldn't pull off Schubert without using some fancy footwork.

Learn from our expert how to make a variety dinner party appetizer recipes that are sure to make your next party a hit in this free cooking video series on dinner party appetizer recipes.

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

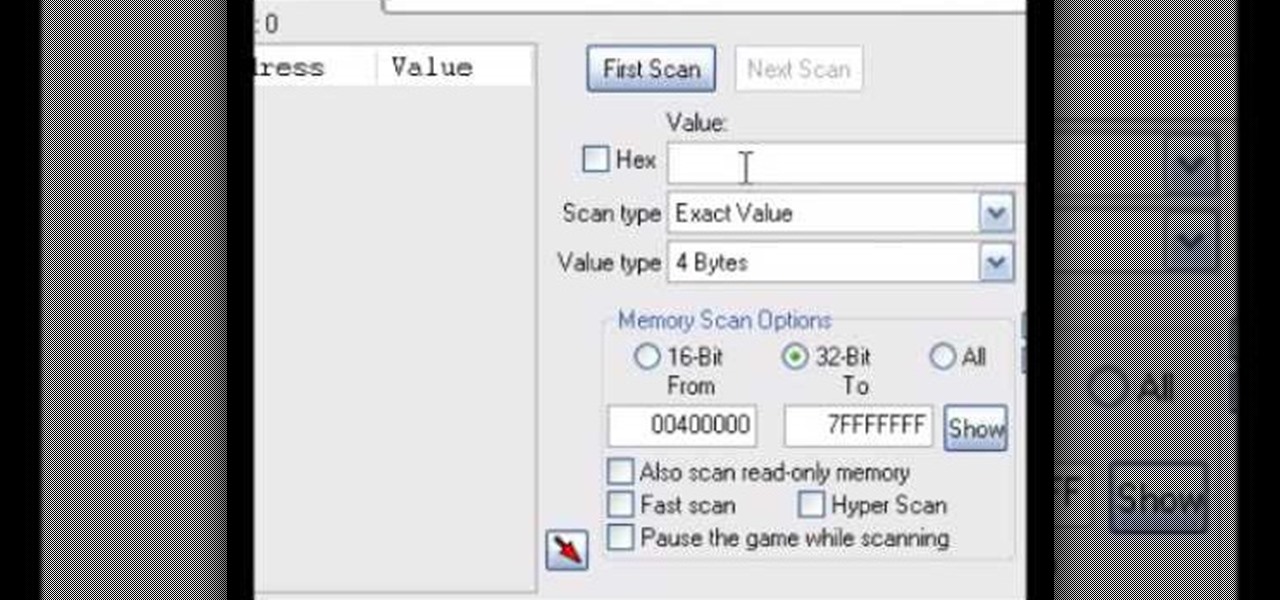
This tutorial shows you how you can use the free hacking program Cheat Engine to change both your speed and the stats for your weapons when playing World of Warcraft. The cheat works best when used on the live servers.

Freezing is a great way to preserve the nutrients and lengthen shelf-life of food. No need to waste extra apples from the fall. Freeze your apples to be used in a variety of ways at the date of your choosing.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.