Matteo Pisani, CTO and co-founder of Remoria VR, has managed to do something the folks over at Google said couldn't be done for at least a couple of years. With a little bit of tinkering, Pisani was able get his Google Daydream VR headset and remote to work on an iOS device.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

The human body is amazingly complex, and seeing inside one poses a variety of challenges whether you're dealing with an actual human or some kind of facsimile. Mixed reality offers the ability to get the best of both worlds by creating a holographic teaching tool for human anatomy.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Google first introduced Google Home, its latest smart product in the works, at the company's I/O conference in May 2016. It will directly compete against Amazon's Echo, which has so far been a success with over 3 million devices sold, and it was even featured as FBI Agent Dom's only real friend in the second season of Mr. Robot. Google may have their work cut out for them, but we're betting Home will knock Echo out of the water. Google Home is a personal assistant with a built-in speaker and ...

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

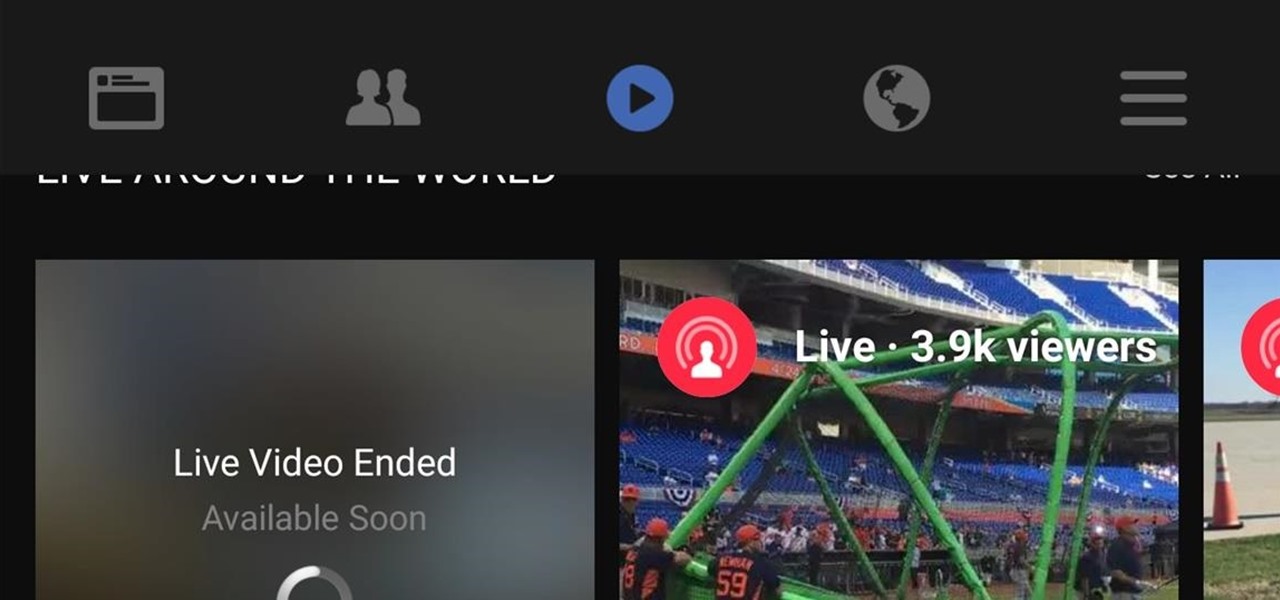
It looks like Facebook is adding a "Live" tab to the navigation bar for its Android app, and the feature has already been turned on for at least one user. A screenshot uploaded by Niko Steele shows the new feature, which lets you search for and watch live video directly on the Facebook app. Right now, you need to already be friends with a person who is streaming or be following a page or personality to receive a notification that live video has started. Some pages will post about an upcoming ...

Computer cables tangle and get in the way, but Mobile Accessory Project hopes to solve that with CONNEX, a flat cable shaped like a credit card which expands up to 1.5 feet.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

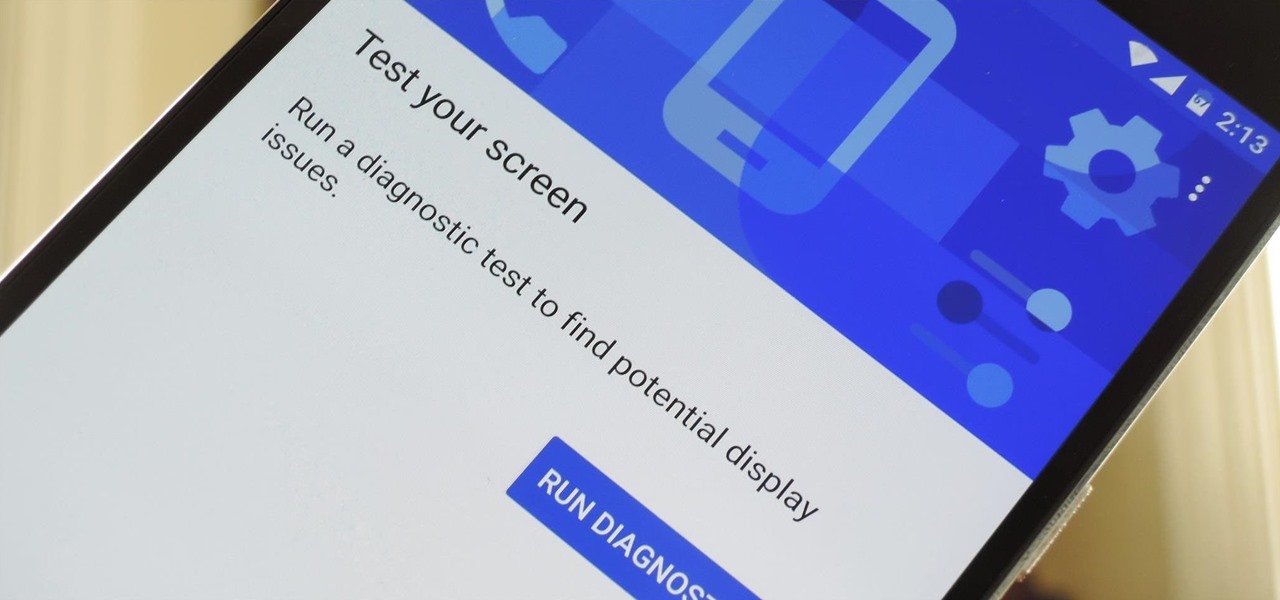
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Android TV devices have had those beautiful Chromecast background images as their screensaver for quite a while now. Envious of this feature, Apple copied the idea for a similarly-styled screensaver in their newest Apple TV, but with one big twist—they used videos instead of still photos.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

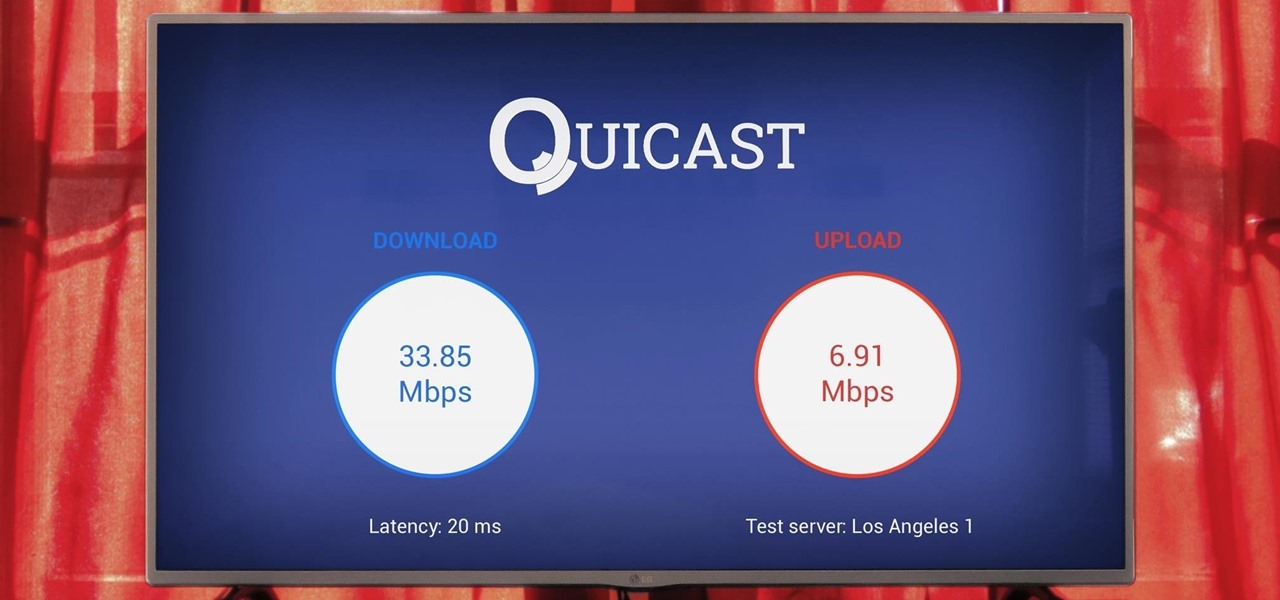
The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

I had the chance to play around with an iPhone 6s this past weekend, and I have to say, I found the new 3D Touch feature to be pretty intriguing. It's still only partially implemented, but when it does work, it works quite well—you simply press a bit harder on certain elements like image thumbnails, then instead of opening in a full-fledged view, you'll see a pop-up preview that fades away as soon as you let go of the screen.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

One of Android's biggest strengths relative to iOS was the ability to switch to a third-party keyboard. While Apple has finally included this feature in its latest OS and leveled the playing field a bit, the variety of options still pales in comparison to what's available on Android.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Peeling garlic is one kitchen task that every cook, from the newbie to the experienced, is always trying to make easier. Methods vary, from shaking heads of garlic inside a container to using the microwave to help peels slide right off.

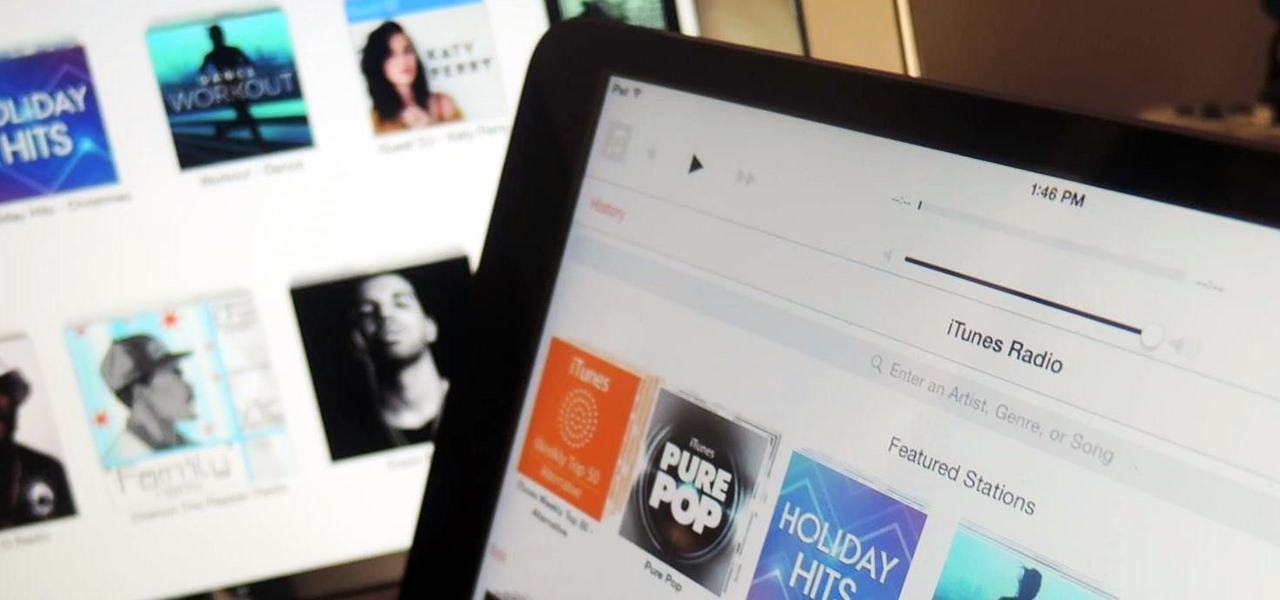
iTunes Radio, Apple's answer to Pandora, provides endless hours of free music streaming, but like other so-called "free" services, every now and then you're going to hear some ads. While you may not be bombarded with them, they can definitely kill the vibe when you're jamming to your favorite stations.

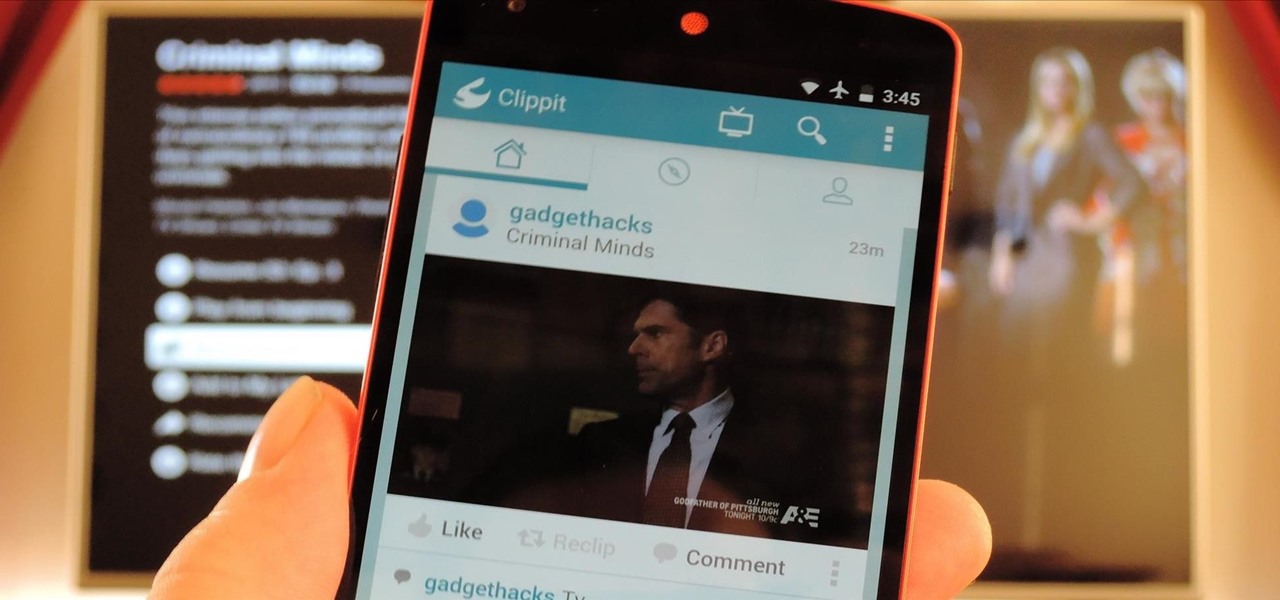
Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

We've already told you how the Japanese pioneered growing specially shaped watermelons (including square, heart, and Godzilla egg). Now it turns out an organic farmer just north of Los Angeles is doing them one better.

There's no TV show that stands out quite like American Horror Story. With its crazy characters and nightmarish storylines, there are countless costume ideas hiding in its episodes.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...