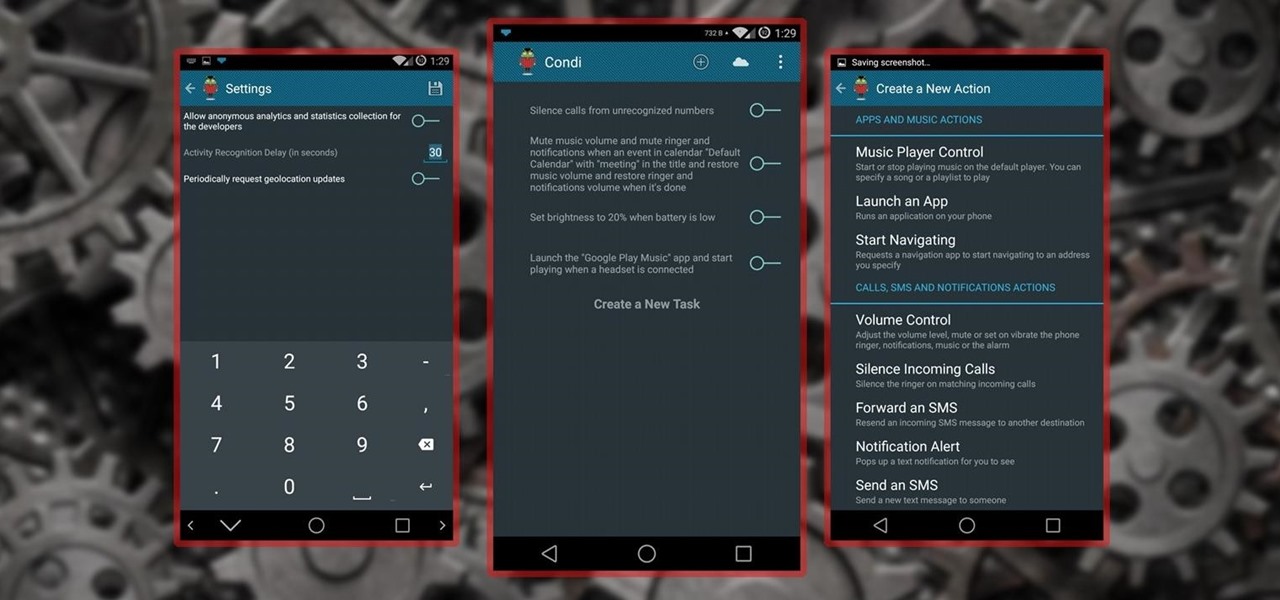
How To: Condi Is Like Tasker for Your Android, Only Easier
No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.


No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.
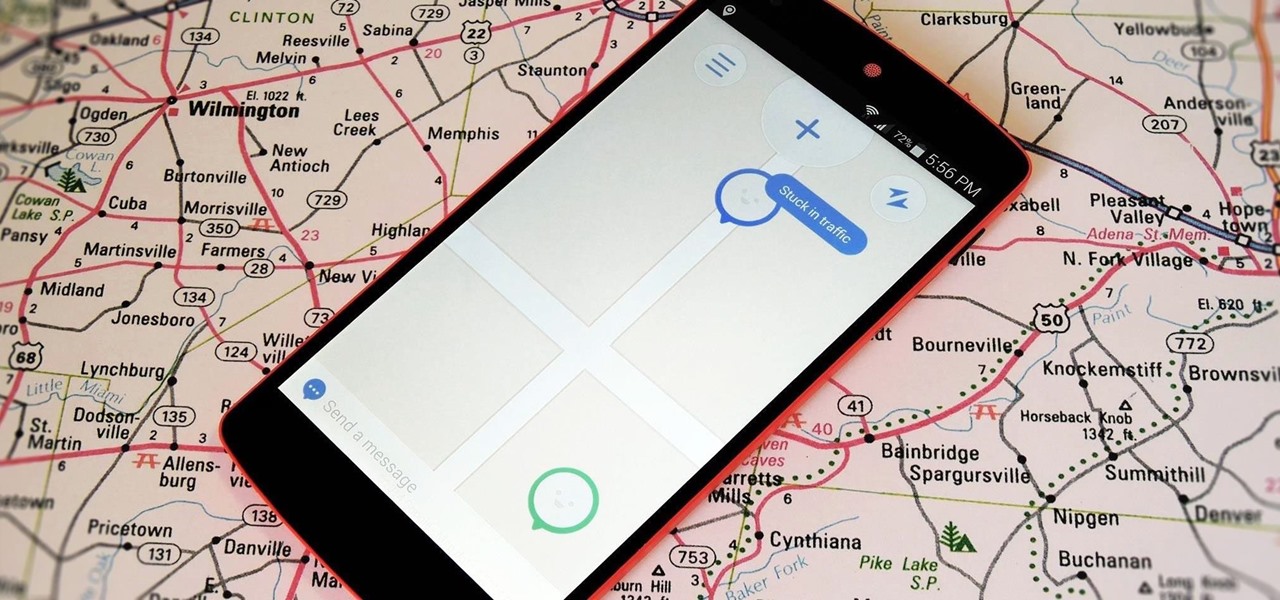
With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

Well folks, the dream is coming to life. While we still may be a ways away from mind control, the team over at Thalmic Labs has created the Myo, and with it, the power of the Force comes to motion control, so long as you use it wisely.
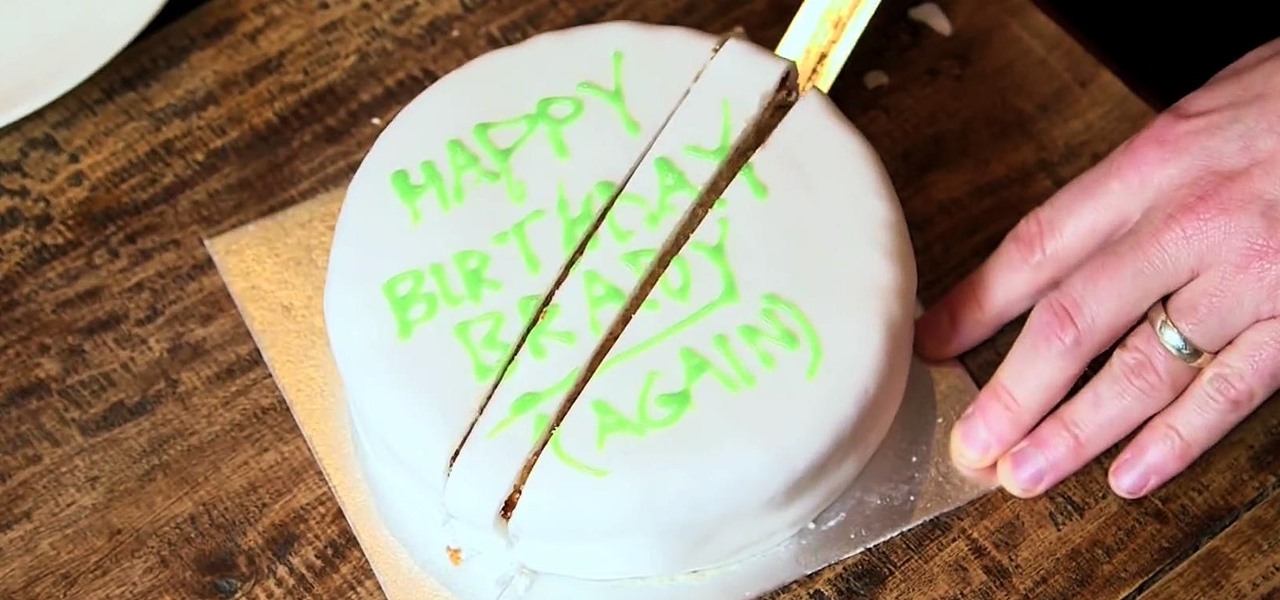
A dead British science nerd figured out the best way to cut a cake to preserve maximum freshness, and it's pure genius (well, sorta). His name? Sir Francis Galton, a polymath infamously known as the founder of eugenics, and apparently owner of a very big sweet tooth.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Let me begin this tutorial by reiterating how boring an iOS device can get, like my iPhone. It's extremely popular, yet extremely strict in terms of personalization.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Snapchat's self-destructing nature is the perfect way to send funny and potentially embarrassing photos and videos (something Anthony Weiner wishes he knew about). That's why there are currently 150 million Snapchats sent each day. While it may be used for fun, many fail to recognize that there's a dark side to every good thing. While Snapchat claims that the pictures and videos on their application are completely obliterated—not only from the phone, but from the Snapchat server—there are oth...
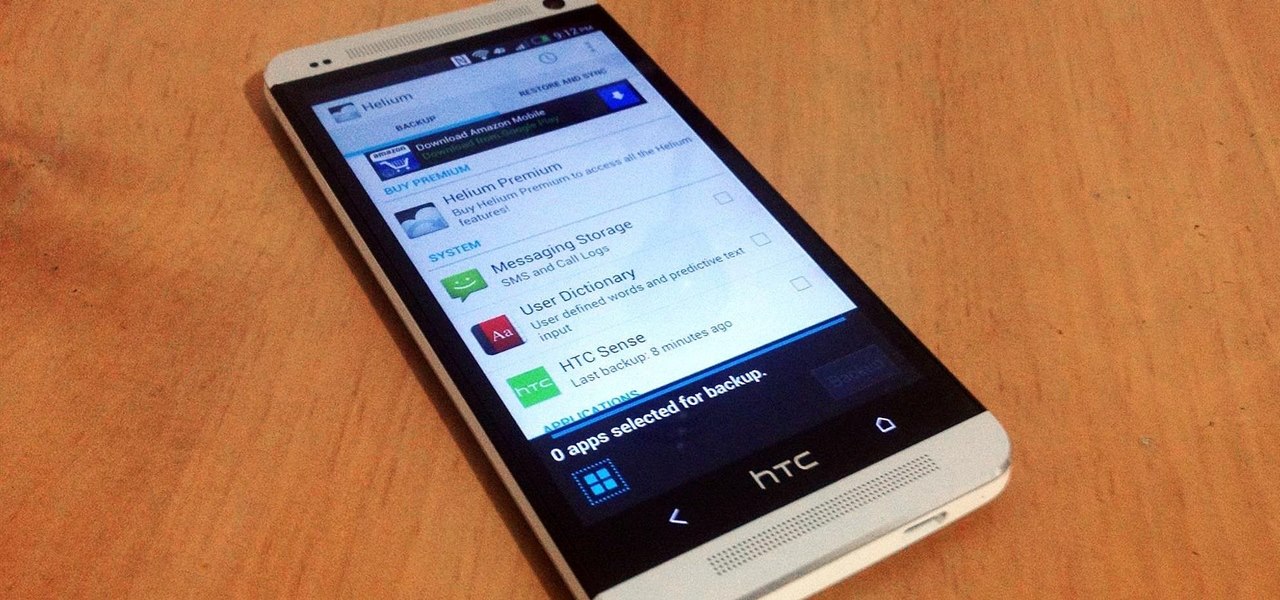
When you upgrade to a new Android smartphone like the HTC One, you can have browser bookmarks, Wi-Fi passwords, and other settings quickly transferred over from your old device using your Google Account backup. However, you'll still have to download apps individually from your Google Play list, and not all of your saved progress will be transferred over. Fortunately, there is a third-party app that will allow you to backup and restore your apps—with all their data.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

Every single year technology companies have a little bit of fun on April Fool's Day by releasing absurd, yet almost believable stories of some new product or feature. Yesterday, Google publicized the release of Google Nose—a new project in beta—that supposedly allowed users to sniff a variety of smells through their smartphone screens.

Humans are able to produce a wide variety of sounds in part because they have descended voice boxes that makes room for longer vocal tracts.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

Starting your own seedlings is a great way to save money, have a wider selection of varieties and gain personal satisfaction. Here are easy to follow tips on getting your seeds off to a great start.

I actually have a lot of shoes, and putting them on the floor in my closet just makes for a very large mess, and makes it harder to find a matching pair. So, this simple yet cool DIY shoe storage is actually something I could benefit from doing. This project shouldn't be too difficult to complete. You can get PVC pipe from your local hardware store and either have them cut it, or you can do it at home if you have a table saw. You can also opt to buy concrete forming tubes, which may be a litt...

You can take macro photos on a huge variety of devices, whether you're using a DSLR with expensive lenses or just your iPhone (or any smartphone, for that matter). One common issue, though, is that it can be hard to get the image as crisp as you want because the depth of field is so small.

The International Space Station is a habitable man-made satellite currently in orbit around the Earth. Launched in 1998, the ISS is used mainly as a microgravity and space environment research laboratory where astronauts perform experiments in large variety of fields, including biology and physics. In order to be hospitable for crew members and scientists, the ISS needs energy. To do this, the station uses its solar panels to capture rays of sun and power the station up. In order to garner th...

If you ask me, one of the best things about winter weather is drinking warm beverages to beat the cold. Coffee is my favorite, but hot chocolate is a close second. Whether it's the just-add-water mix from a pack or a spicy homemade Mexican variety, there's something comforting about sipping on warm, liquid chocolate. Looks delicious, doesn't it?
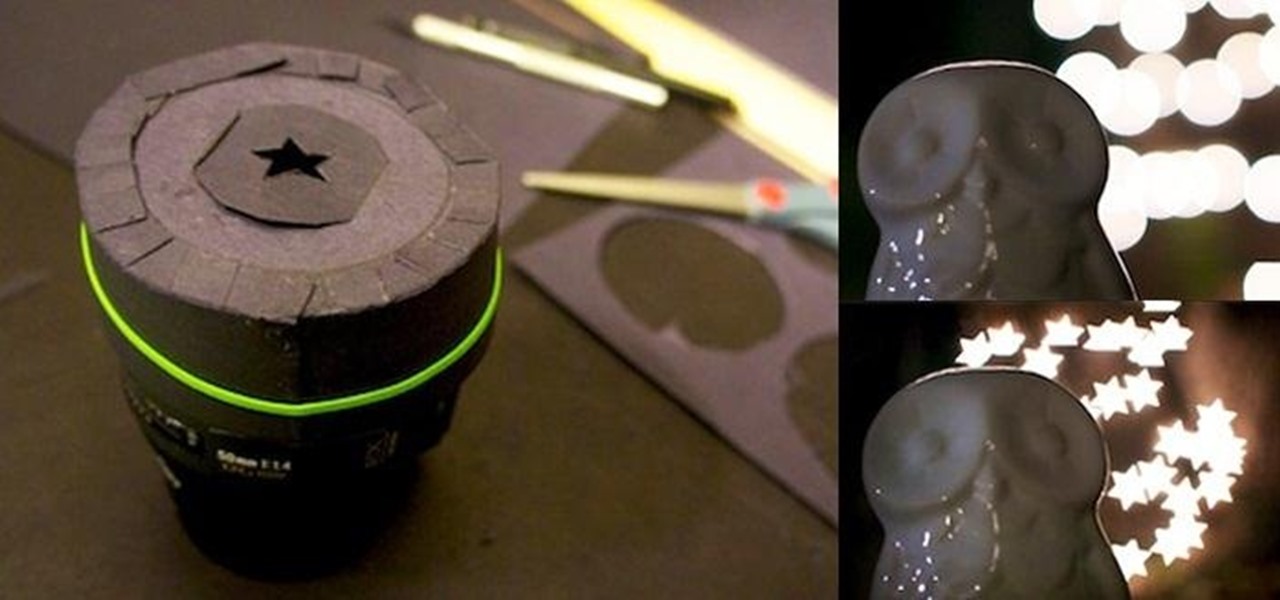
In photography, bokeh refers to the blurry or out-of-focus parts of a shot. Bokeh can be good or bad—it all depends on how you use it. There are tons of ways to create a bokeh effect, whether you go the traditional route with lens filters, digital with Photoshop, or even from your iPhone. With filters, you can use the blurred spaces to produce different shapes and colors. If you have a DSLR and want to experiment with bokeh, this tutorial by Chris Perez over on Apartment Therapy will show you...

The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to release its own real-time picture and video messaging application, aptly titled Poke. One of the biggest criticisms (besides the wave of recent security issues) of Snapchat is that even though the messages self destruct and ...

Apple's new iPhone 5 has enjoyed three weeks out in the public since its September 21st release. Millions of consumers have been shelling out big bucks and waiting in long lines just to get their hands on it. But sometimes users forget to actually keep their hands on their new phone, causing something like this... It only takes a second to drop your new iPhone 5, but the pain of picking up the phone and turning it over to reveal a cracked display lasts a lifetime. Well, not exactly a lifetime...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

I should start off by saying that this technique is of no real practical value, because this process is far more time-consuming than simply just manually trimming trees to meet your specifications. That said, it's an awful lot of fun to play with!

You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.
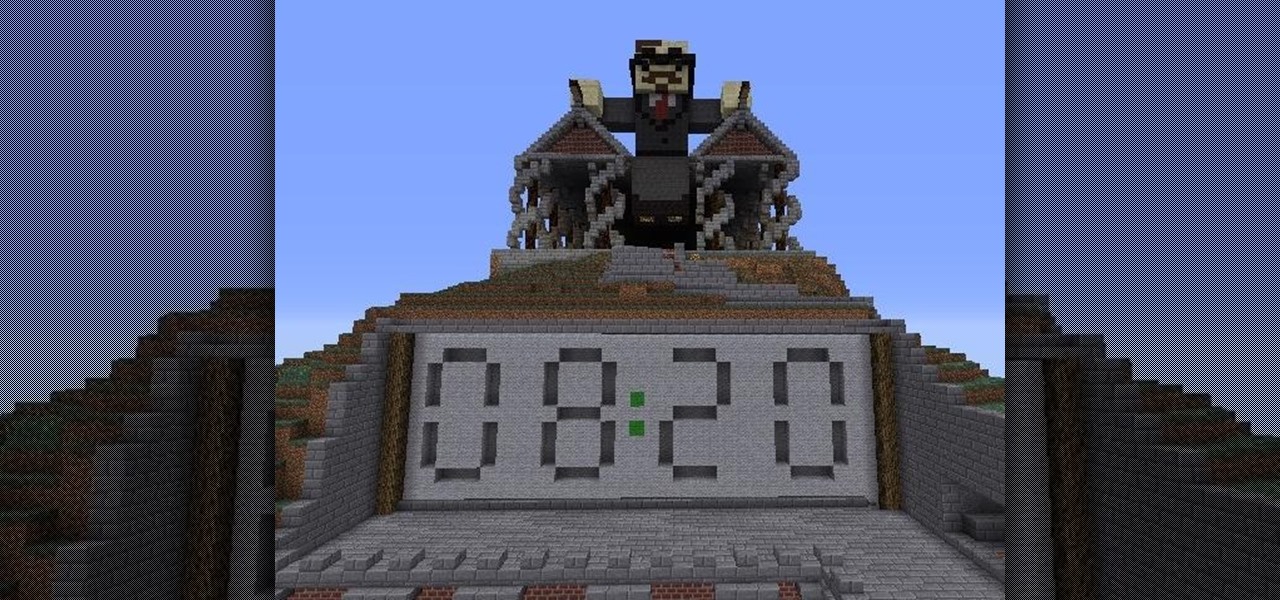
A redstone clock is a pretty easy mechanism to make. A digital readout for that redstone clock is a little harder, and that's what Lesnoydude has made that won him the staff choice award.

Video: . The Walls is a PvP survival map that takes back Minecraft to it's roots: crafting, surviving and creativity.
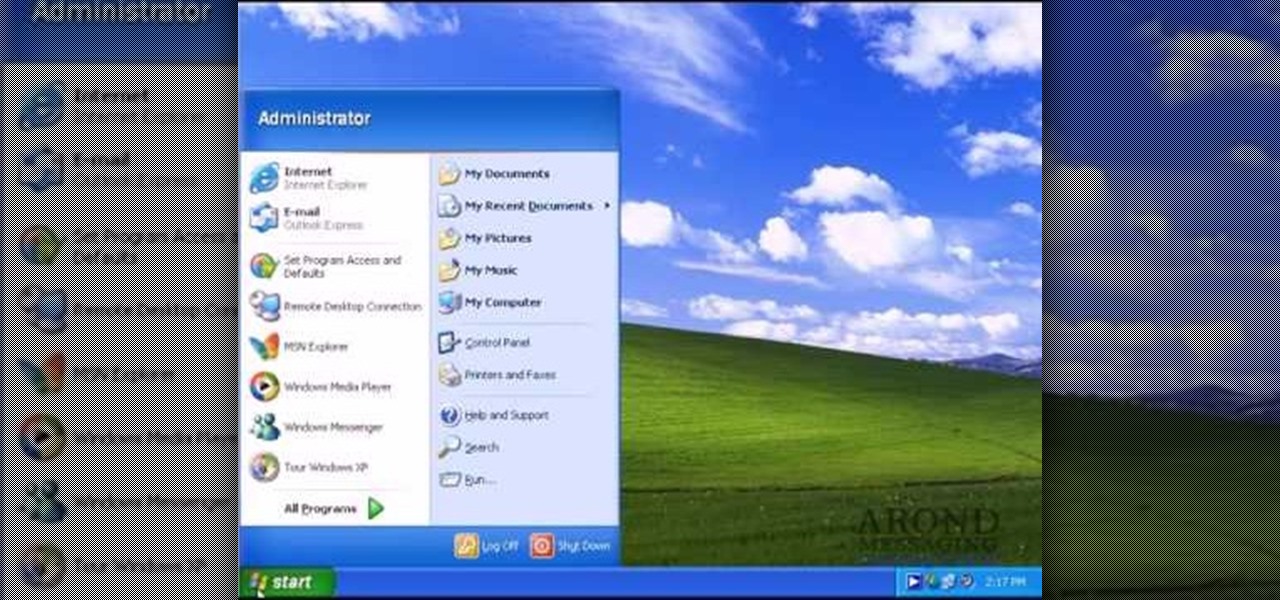
Remote desktop in windows is set up with these easy to follow steps. First go to your start menu this is in the bottom left corner of your desktop. In the start menu locate your control panel. In the control panel open up your systems folder. Once this is open click the remote tab at the top right of this folder. In this tab you will have the option to check “allow user to connect remotely to this computer.” From here press ok to exit out of the systems folder.Again click the start menu, navi...