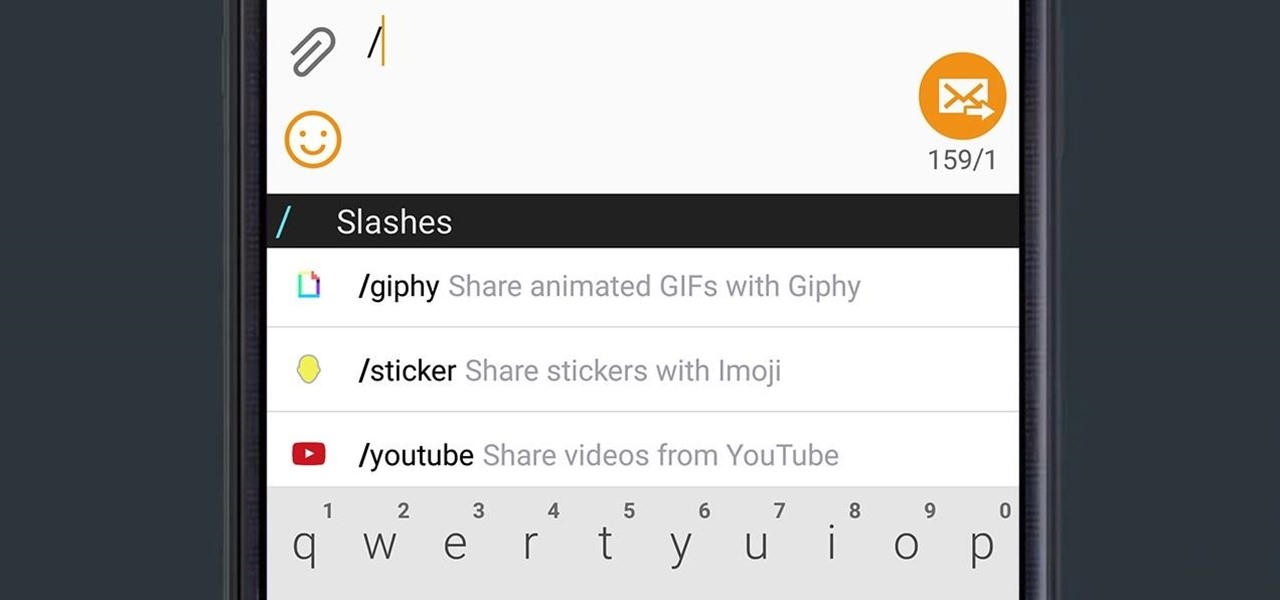
Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Walking while taking a video is always a pain. But it doesn't have to be, especially with Google's new Pixel smartphone and its new and improved Electronic Image Stabilization (EIS) feature. A new video, released on Reddit, pitted the Pixel's EIS against the Nexus 6P with some incredible results.

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.
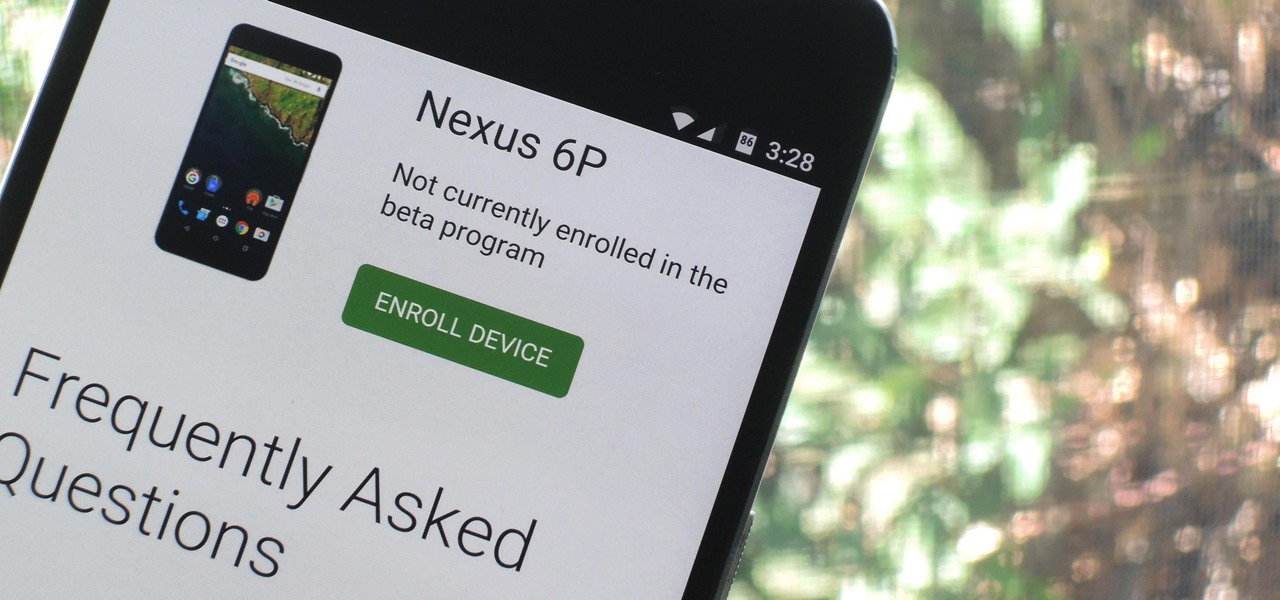
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

Most augmented/mixed reality hardware still exists in the development stage, whether that's one of the more robust headsets or a high-powered smartphone. Most everything else isn't widely used or monetized. Snapchat, however, snuck in under the radar and created the foundation for the first social network to focus on augmented reality.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.

Want to actually catch 'em all? Pokémon GO has long-teased the opportunity to hunt for Pokémon in the real world through augmented reality, but few have had the opportunity to actually see it in action.

Google released an amazing swipe keyboard a few months ago called Gboard that has Google Search built right into it; This makes adding pics, GIFs, videos, and links to articles, restaurants, and shops a breeze. It even helps you search for emojis! The only problem is that Gboard is for iOS devices only, meaning only an iPad, iPhone, or iPod touch can use its magical powers.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

It's no secret that the microwave is a modern-day wonder that, when used correctly, can cook a wide variety of food in a snap.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

Listen up, children, pregnant women, and lightweights: this particular KitKat variety is not for you. Well, with 0.8% alcoholic content per 2 KitKat bars, it's highly unlikely anyone will actually get drunk on these things. Still...

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Most wood furniture is long-lasting, durable, and resistant to great wear and tear over the years. However, set a single sweaty, wet cup or bottle on the surface of your favorite wood dining table, or your prominently placed wooden coffee table, and you'll end up with a round water ring stain that is difficult to get rid of.

Most people are familiar with the fact that vinegar adds sourness to a dish, in varying degrees from light acidity to puckering acid. However, vinegar can also be used in lieu of salt when seasoning the final touches to sauces, soups, and stews.

A few months ago, my friend Sarah appeared at a party bearing homemade liqueurs—amaretto, hazelnut (e.g. Frangelico), and vanilla liqueurs, to be exact. Her cool factor, which was already quite high, jumped up a few more notches—as did the overall energy of the party. (And that's why we call her 'Game Time.')

Back in August, Google unveiled a new YouTube Gaming service meant to compete with e-sports streaming sites like Twitch. At its launch, the service was capable of broadcasting desktop PC gameplay, but when it came to the mobile segment, users were only capable of viewing streams hosted by others.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

There are a lot of reasons for wanting to make sure your herbs last a long time. Maybe you know that your grocery store won't have decent parsley in the winter. Maybe you're taking a last-minute trip and don't want to throw away your perfect batch of basil. Or perhaps you're simply like me, and buy a dozen different herbs at the farmer's market, only to remember that you can't make it through all of them before they go bad.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?

Bringing lunch to work or school is a win-win situation. You save money, you eat better, and you create less waste. But while the virtues of brown-bagging it are undeniable, it also gets kind of boring after a while. How many times can you shove a container of salad or noodles into an insulated sack before you say screw it and buy a $12 burrito for lunch instead?