I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Many people are bored of the typical square-ish icons arranged in a uniform grid on their Android homescreen. I dislike looking at grids of buttons and sometimes I would like to have some really HUGE buttons for the applications that matter the most at any given time.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Have you ever heard the expression "Dress for Success" or "Clothes Make the Man"? When you're wearing a perfectly fitted designer shirt, something inside just shouts, "I look good" and when you genuinely think that, those feeling are radiated outward to all your come in contact with. That said, what kind of designer shirt are you interested in, a bargain basement discount, or one tailored made, outlining your best features?

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

One of the coolest features that Samsung built into the Galaxy S4 is the infrared (IR) blaster and WatchON software to control your television. I've been using my GS4 for the past few weeks to control my DirecTV setup and it works great. Smartphones are truly becoming all-in-one devices these days.

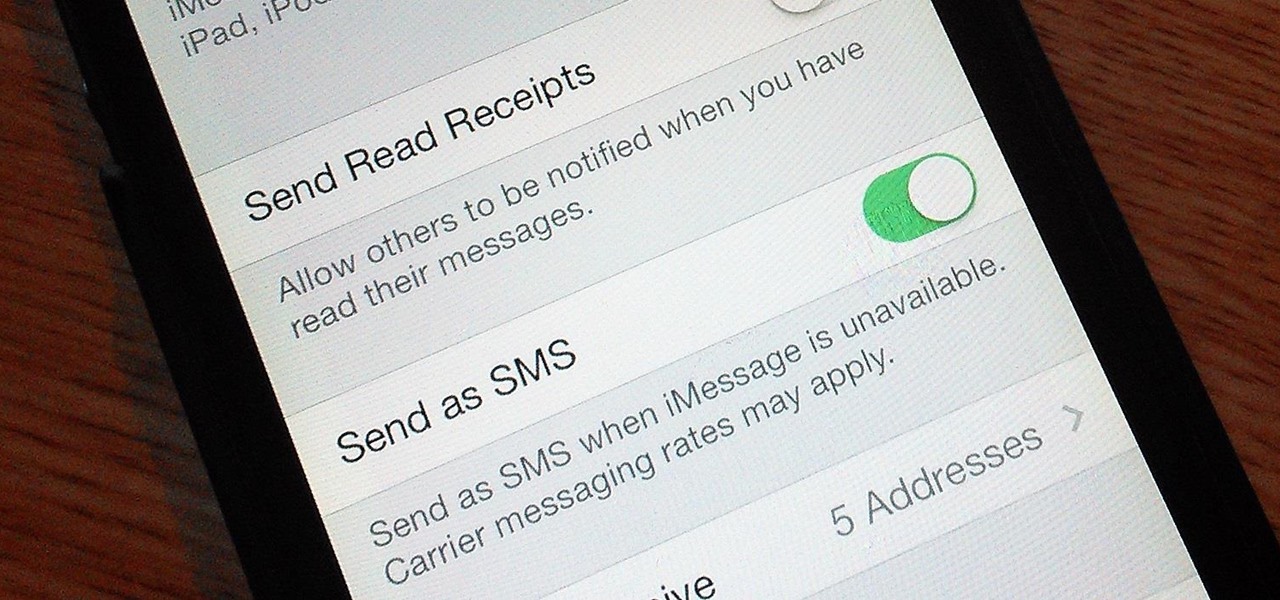
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.

Probably the most favorite custom ROM among softModders is CyanogenMod, a theme-friendly take on stock Android that not only makes it easier to customize your device, but also increases performance using a variety of system tweaks and enhancements.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

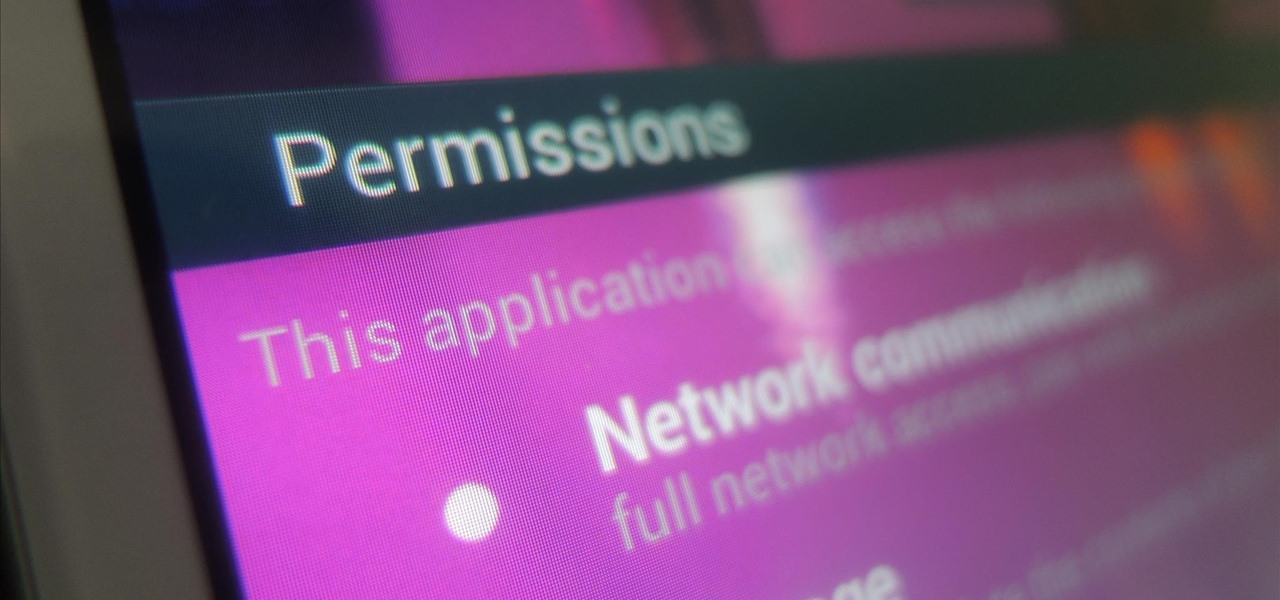
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

No matter what device you have, Android lag will get you down. It's our little green robot's only major downside, and you've probably noticed it quite a bit on your Nexus 7 tablet. Apps open slowly, actions stutter or pause, and loading files takes forever.

Driving in your car can cause a pretty spasmodic GPS connection on your Samsung Galaxy Note 2. Making a lot of turns, speeding past large buildings, and going underneath trees and highway underpasses can all disrupt your GPS signal, making it difficult for the satellites (in the sky) to get a good lock on your location. According to them, you're in that blue circle. Somewhere. Probably.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

Video: . How To Use a Tampon

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

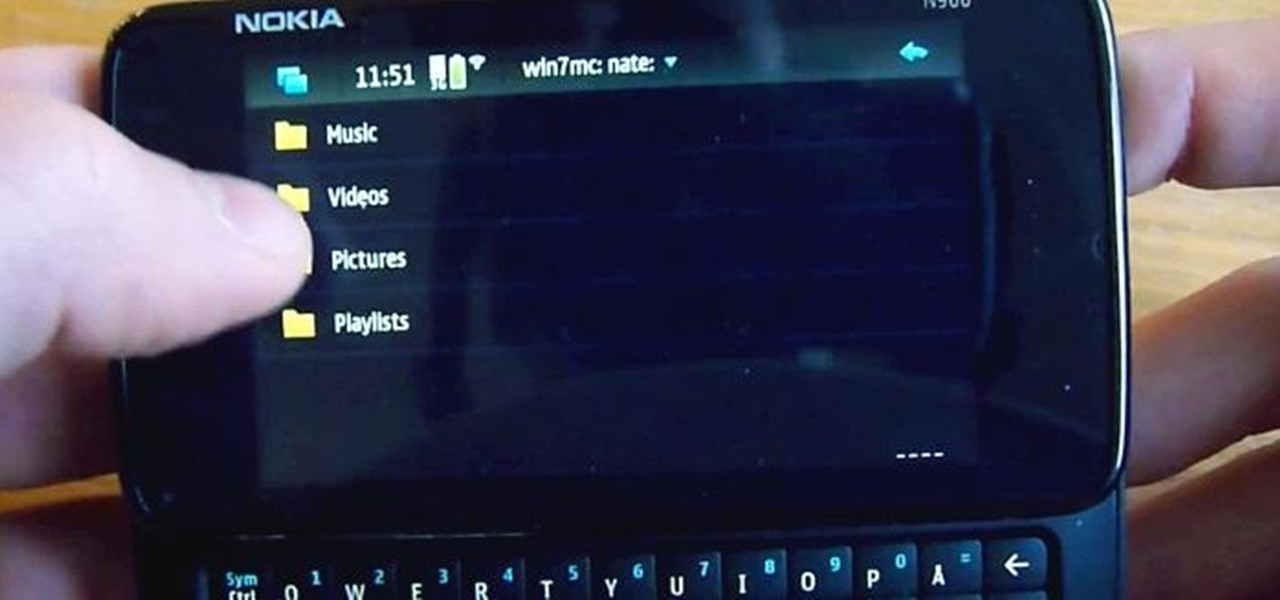
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

It wasn't that long ago that we started seeing a variety of beers catering to the Steampunk crowd, so why not some wine?

Those of you who have attended a Steampunk convention in the last year or two may have heard of something called "Tea Duelling" and been intrigued.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

People use search engines for a wide variety of subjects (just look at some of the results that pop up in autofill). The results you get with each different search engine are usually different, but almost all of them display the same number of results per page by default—ten. If you find what you're looking for at the top of the first page, great. But if you have to do a lot of digging, it can be a pain to load so many different pages to find it, especially if your connection is slow.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.
Are you scared that the RIAA is about to track you down for illegally downloading songs. Well, here is a method of obtaining many songs absolutely free that is virtually untrackable

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

Some would say that Turkish coffee is the best coffee in the world, and then some would go even further and state that Armenian Turkish coffee is the best coffee in the world. Well, that's exactly what this video is about, Armenian-style coffee, and you'll learn just how to make it.

Already an impressive gaming machine, the Xbox 360 can be modified to play a wider variety of games. This instructional video demonstrates how to flash your Xbox 360 to play downloadable games from the Internet. This method only works on the Hitachi v0078fk drive and will void your warranty, but think of how cool it would be to pull this off.

PGA golf professional Frank Ganley explains how to hit a golf ball with an iron. In golf, a player has a variety of clubs to choose from, but should only have one type of swing. Frank emphasizes that in order to learn how to hit a golf ball with an iron, the player needs to use the same swing that he uses when hitting the ball with a wooden club. The key to a successful hit is in the players ability to adjust for the difference in the lengths of shafts of the clubs. This because a wooden golf...

Ducttapestuff presents colored duct tape that he uses in making a variety of objects like wallets, book bags and flowers. He strongly recommends duct tape made by "Duck", which is the only kind of tape he uses and he considers it the best. He shows all the tape he has (some of which were freshly bought when the video was made): a wide range of colored tape, from beige to black, and also a few patterned tape like "tree camouflage" or "cosmic tie-dye". He says that he always gets his tape from ...

This video presents a system for automatically producing a wide variety of video enhancements and visual effects. Unlike traditional visual effects software (e.g., After Effects, Shake, Boujou, etc), the system is completely automatic and no manual labor is required from the user. The major limitation of the work is that it can currently handle only videos of static scenes (i.e., videos shot with a moving camera but containing no moving objects in the scene). Efforts are being made to lift th...

This video staff spinning tutorial series demonstrates a variety of different beginning spins: the basic spin, the figure eight spin, and the primary backspin. Staff spinning doesn't take anything but practice, and some good tips don't hurt. Watch these instructional videos and learn how to spin a staff like a pro.

The beehive is a woman's hairstyle that resembles a beehive. It is also known as the B-52, for its similarity to the bulbous nose of the B-52 Stratofortress bomber. It originated in the USA in 1958 as one of a variety of elaborately teased and lacquered versions of "big hair" that developed from earlier pageboy and bouffant styles. The peak of its popularity was in the 1960s, and it was especially popular in the United States and other Western countries. The beehive remains an enduring symbol...

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

With the success of Iron Man in 2008, a video game adaption quickly hit the market, so it's no surprise that when Iron Man 2 came out this year, that a video game would follow close behind. Sega released Iron Man 2 in a variety of gaming formats, including the Xbox 360, PlayStation 3, PlayStation Portable, Nintendo Wii, Nintendo DS, along with iPhone and other mobile devices. The story of the game takes place after the plot of the film, except the iPhone game, which mimics the movie's plot.