The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

If you own a Google Pixel, you'll soon have augmented reality versions of Iron Man, the Incredible Hulk, and Childish Gambino on your camera.

The arrival of Magic Leap One is tantalizingly close and, although the company has been saving the last details for launch day, a few of the more important details were found this week hiding deep in the code on Magic Leap's website.

On Tuesday, at the Unite Berlin developers conference, Unity unveiled new tools designed specifically for augmented reality that could literally raise the technology to the next level.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

In the wild world of Snapchat lenses, this week was an especially good one for cool effects. Lens-crafters (really hoping I can get that name to stick) have gotten a lot better at making non-gimmicky lenses that allow you to interact with them in new and unique ways.

On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

There was a huge Marvel movie that opened a week ago, and a popular TV show just finished its second episode of the current season. Both of these facts translate to more cool Snapchat lenses to try out on your iPhone or Android phone, thanks to Snapchat's Lens Studio — where anyone can make a sweet lens.

Google's been using their "Material Design" look in Android for years now, but a change is coming up with "Material Design 2," their updated version focusing on new colors, icons, and spacing. Whether it'll be called "Material Design 2" or not remains to be seen, but you can try it out right now in Google Chrome on your Android device right now.

While you were slaving away at work or school or whatever you were so busy doing over the last seven days, people have been hard at work creating a variety of new Snapchat lenses for your enjoyment. These lenses are hot off the presses, and I'm honestly really impressed with this week's crop.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

DxOMark, an independent camera reviewer, has become the go-to place where consumers and OEMs alike hope for good camera scores on major new smartphones. The Google Pixel 2 has topped the charts since Oct. 2017, when the score no doubt helped pull the phone out from its troubled launch, but it has just been dethroned by the Samsung Galaxy S9+, which received the highest DxOMark score yet.

Apple's Animoji on the iPhone X might allow you to use your own facial movements to control your favorite emoji, but Samsung is looking to make you the focus of the interactive icon with the introduction of AR Emoji. Instead of a dragon or an alien, Samsung wants your unique look to define your avatar.

We regret to inform you the former king of third-party keyboards, Swype, has officially retired on both Android and iOS. A few weeks ago, we noticed Swype's mysterious disappearance from the iOS App Store but had hoped it was just pulled temporarily, not gone forever. Unfortunately, Swype is no more, but there's something that's ready to take its place for you on your phone.

The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

If you're following the classic Halloween playbook closely, you've already got a costume or three picked out, you've binged-watched your favorite horror movies, and you've likely visited a haunted house. But it's 2017, so how about trying something new, like a haunted house that's not actually there?

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Anyone who knows me well is aware that I am a cyberpunk junkie. The conflict between lowlifes, corporations, and the government, flavored with dystopian future, high technology, transhumanism, artificial intelligence, and noir storytelling, just does something for me.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

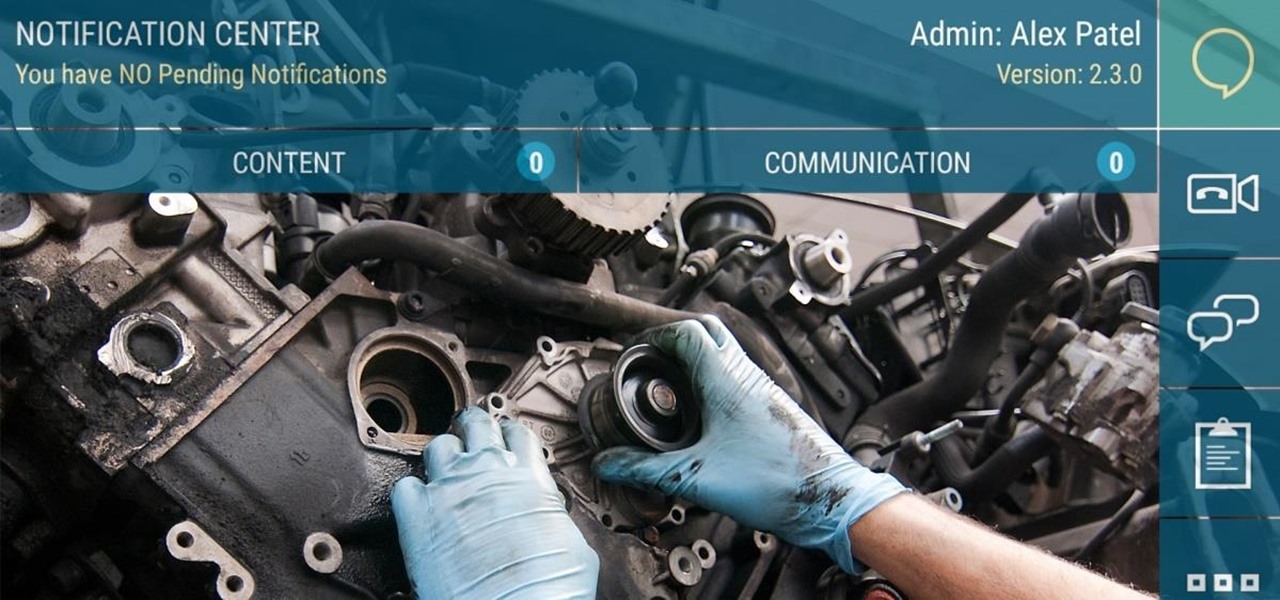
As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

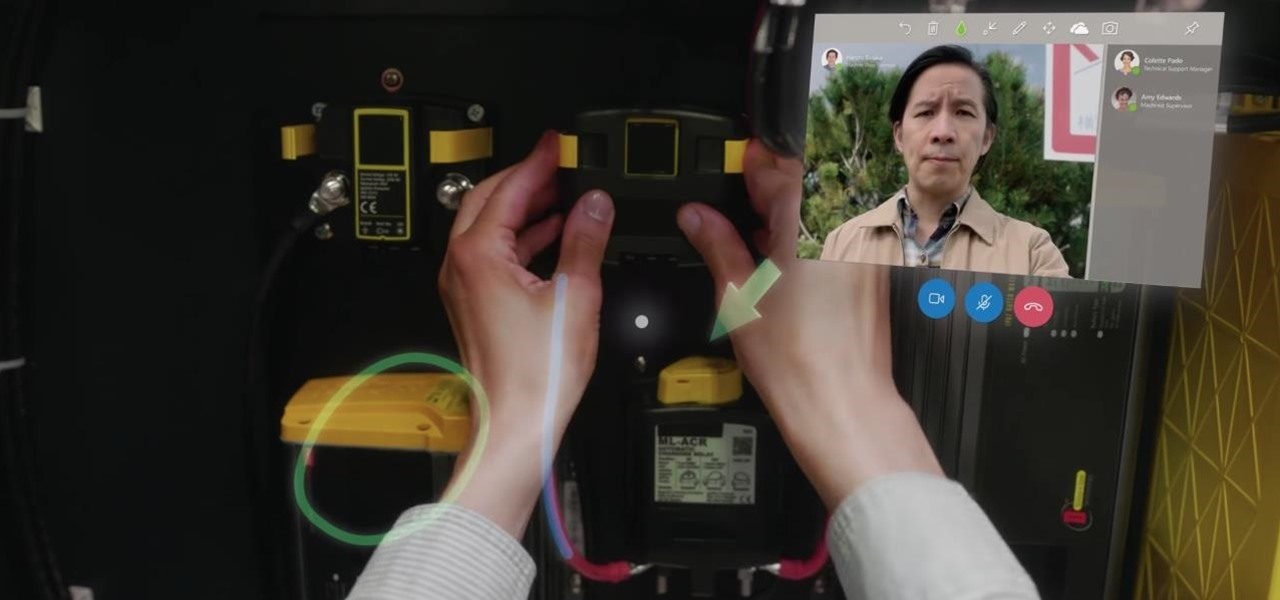
The augmented reality productivity app market for is a crowded space, so differentiation can be an advantage. Atheer is doing just that this week with their AiR Enterprise application.

Some types of bacterial infections are notoriously tough to treat — and it's not all due to antibiotic resistance. The bacteria themselves are rugged and hard to penetrate with drugs.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

A new Google Search update lets job-seekers streamline their search process. Searches like 'jobs near me' are now designed to show relevant opportunities from multiple sites.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.

Multistate outbreaks of Salmonella infection in humans have led the Centers for Disease Control to advise caution when interacting with poultry. A press release on June 1st mentioned eight multistate outbreaks connected to backyard flocks. As of May 25, 372 people in 47 states were reported infected with the outbreaks' Salmonella strains. That means this year could be as bad as 2016, a record year, for salmonella outbreaks with 895 people infected.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.