If you're like me, you've already spent a ton of money on your costumes, your badge, and your hotel room, and now you're looking for ways to cut costs. There are all kinds of ways to save money at DragonCon, but many of them involve violating the rules in some way, such as not buying a badge, sleeping on the floor in a hallway somewhere, etc. However, the one thing you can do that is totally not against the rules is eat for free. It requires a little self-discipline and a willingness to eat w...

Relays are simple redstone devices that allow you to switch between multiple outputs with only one input. They're incredibly useful in the right situation!

Sometimes the hardest part about getting your minecart rolling is the beginning takeoff. Have you ever started a minecart on a hill, and then tried to jump into it as it started moving, only to fail and watch it slowly dwindle into the distance?

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

As I said before in my earlier post on how to make a two-tone doorbell, sound is more than just music. Note blocks can create a wide variety of notes and sounds, and those can be used for more than just making a stirring rendition of "Still Alive" from Portal.

Builds in Minecraft aren't usually for your own personal enjoyment; most people want to show them off to others. So to some extent, builds need to be user-friendly. That is, they should automatically guide people to areas of interest or importance. One particularly stylish way to do that is by using guide lights. I have two different designs included here, which you can either use or adapt to your own purposes.

Everybody should have plants in their home. Not only do they give off oxygen, but they add a whole new level of decor and awesomeness to an otherwise drab room. So naturally, if you want to improve a room, just display a few plants.

We've already done a tutorial explaining why buttons are superior to levers, but now I want to show you a way to make them even more useful than they already are. You can't get this sort of functionality with levers!

Gardening is a great hobby for anyone looking to grow beautiful flowers, ferns or fruit bearing plants. Learn how to care for a variety of garden plants with gardening tips from a horticulturist in this free video series.

In this video series our expert will demonstrate how to make pottery cups and vases. Pottery cylinders can range in size and shape, but are quite useful and beautiful. Our expert will demonstrate how to wedge, center and form clay into cups and vases. You will also learn how to trim the foot and decorate your cup or vase using a variety of pottery techniques. Whether you are just a beginner on the pottery wheel, or a seasoned potter, let our expert give you some great tips and advice on makin...

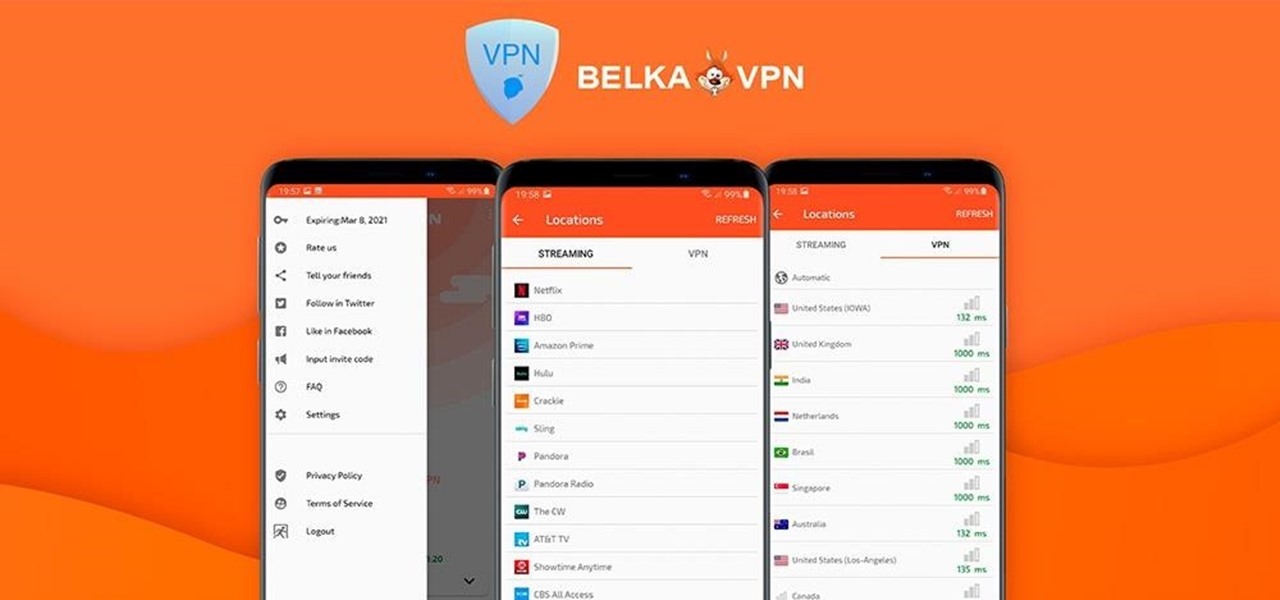
In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less safe for the people using it. If you want to watch something, you have to hope it was available in your country. If you want to keep your information safe, you have to take some extra steps to make sure that happens. The...

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

If you're concerned about your data ending up where you don't want it online, then a VPN is something you'll want to consider. A VPN can prevent your bank account information from leaking, your data from being taken directly from your device, and it doesn't come at the cost of any of the convenience we've grown to expect and require from the internet.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Django is a powerful Python-based framework that makes creating complex, database-driven websites easy to build and maintain. The free, open-source platform emphasizes reusability, the "pluggability" of components through APIs, rapid development, and less coding.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

If you're a regular Null Byte reader, you probably know your fair share of programming languages and have at least some experience with web or app development. But it's possible to apply your hard-earned coding and tech talents to other closely-related fields as well.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

Google recently started testing a new SafetyNet check that might spell trouble for rooted Android devices. It cross-checks your SafetyNet status with Google remote servers, making it impossible to fool by normal means. If Magisk shows you pass SafetyNet and you're still having issues, you might be affected by this change.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Mobile gaming has exploded, with roughly $70 billion in revenue in 2019. This gave rise to the so-called gaming phone, headlined by names like Razer and ASUS. While the Galaxy S20, S20+, and S20 Ultra are being marketed as everyman devices, make no mistake — these are unstoppable mobile gaming machines.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

There's no denying that native Dark Mode in iOS 13 is awesome. Stock apps that were blindingly white for over a decade can now be comfortably used in the middle of the night. You might find, however, that some of your third-party apps aren't taking the hint. Why won't YouTube switch to dark mode when iOS as a whole does? We put together a troubleshooting checklist to get your apps cooperating.

Starting Sept. 13, you can preorder the iPhone 11, 11 Pro, or 11 Pro Max from Apple, wireless carriers, and various e-commerce websites. However, unlike with Android smartphones, there is only one set of iOS phones that come out each year, so they're pretty hot items. That means being the first to get your hands on one could be a challenge, but we're here to help you out.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.