Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

You may know your onions but do you know your garlic? If not, you'll be well served by this gardener's guide, which presents an overview of the different varieties available for planting (including soft-neck, hard-neck and so-called elephant varieties) and provides tips on actually planting the stuff in your own garden.

Clinton Kelly, the lifestyle expert, shows the right way to ‘Set your Buffet Table’ for a buffet party, in this video. He suggests that all the serving dishes and utensils are laid on the buffet table, the night before the party. This will throw some light and give ideas as to how to place the dishes on the table. You could place the plates on one side of the table, the food at the center and the napkins to the other side. You should also decide the heights of the various serving platters, co...

You can eat Italian and still stick to your diet. Just follow these guidelines. Step 1: Skip the garlic

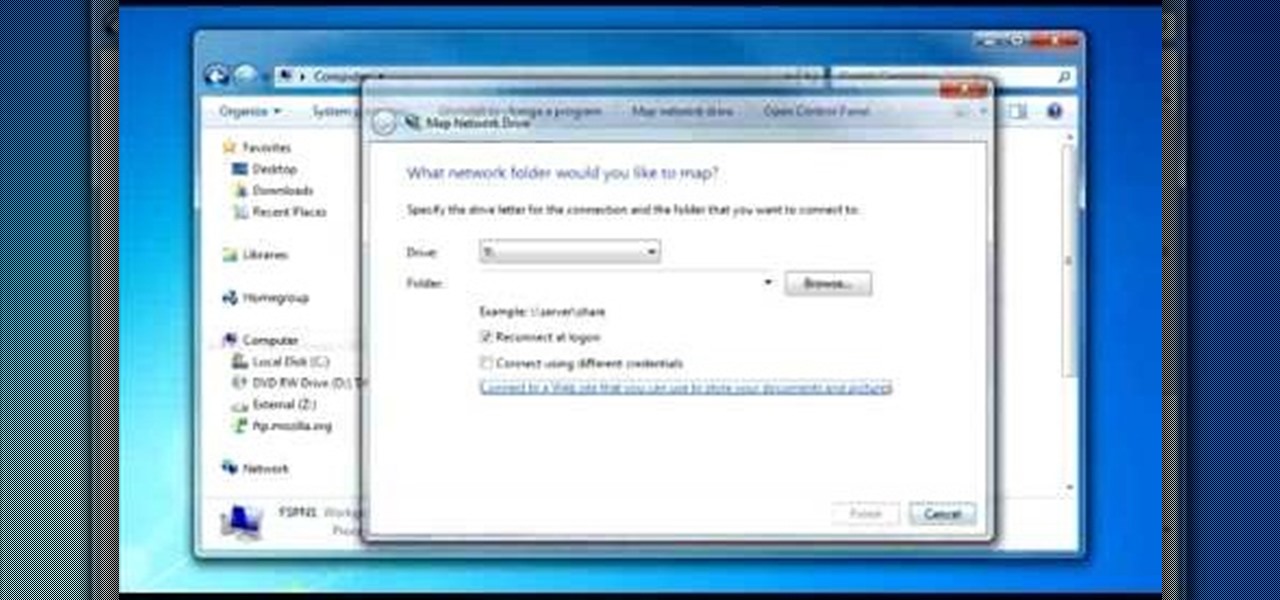
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

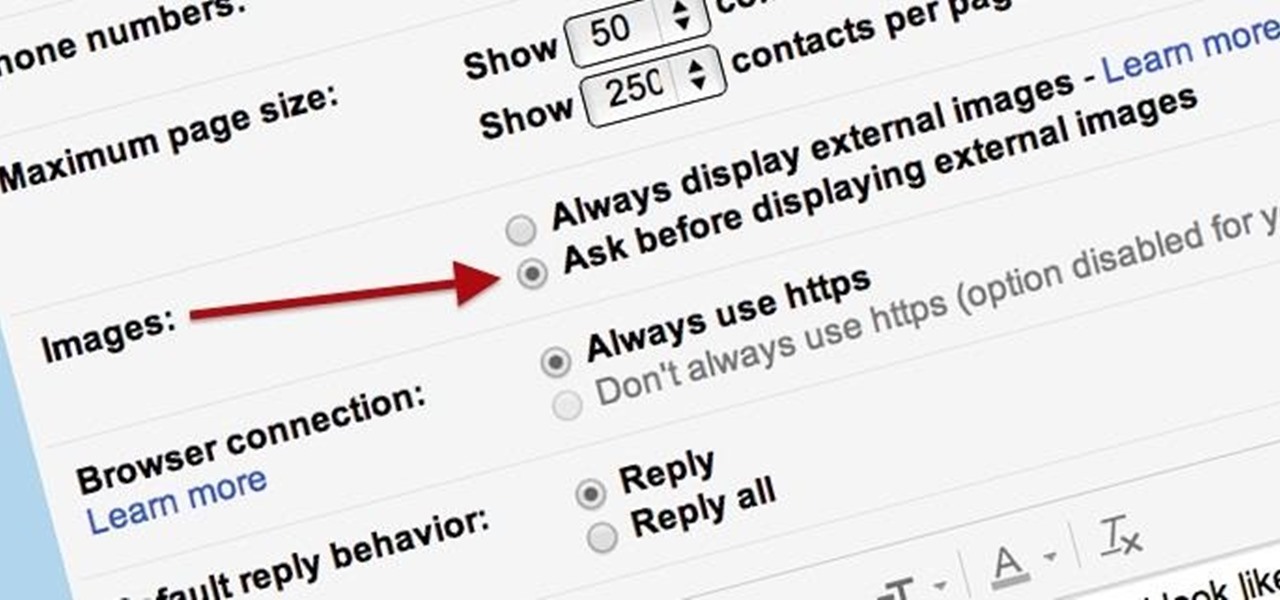
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

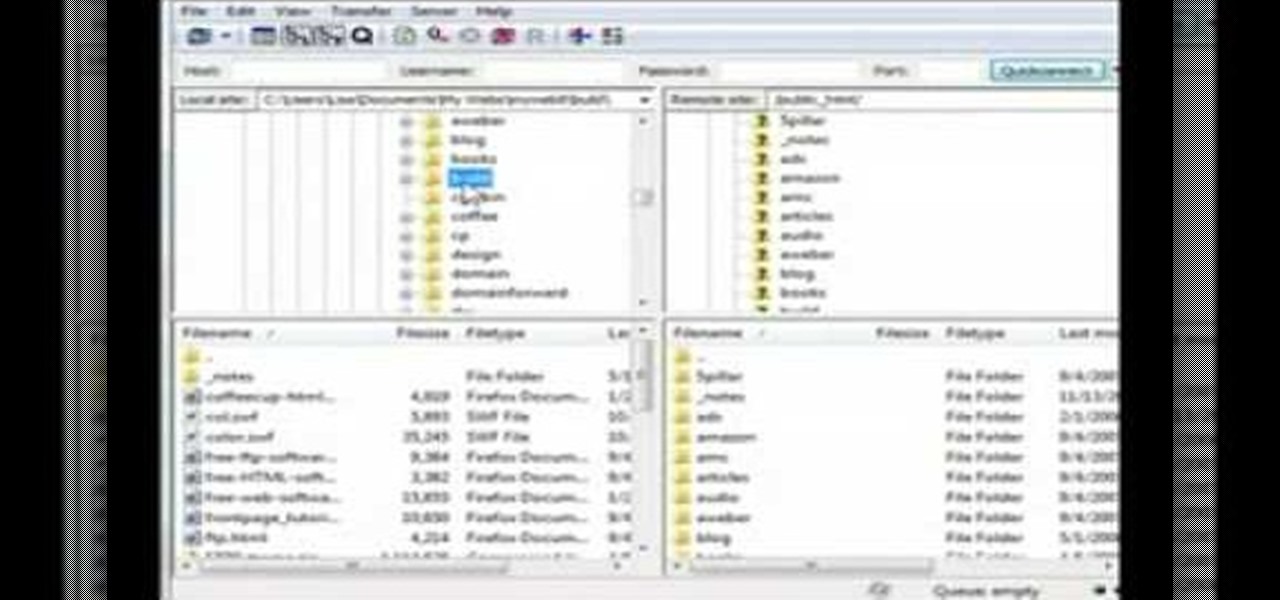
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.

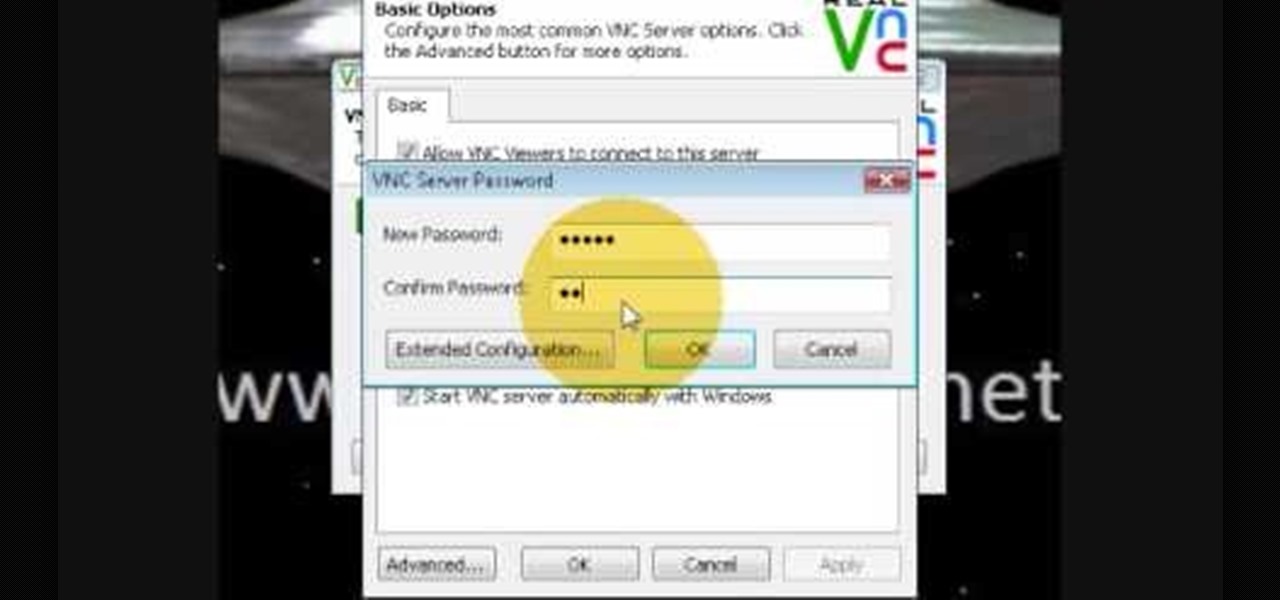
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

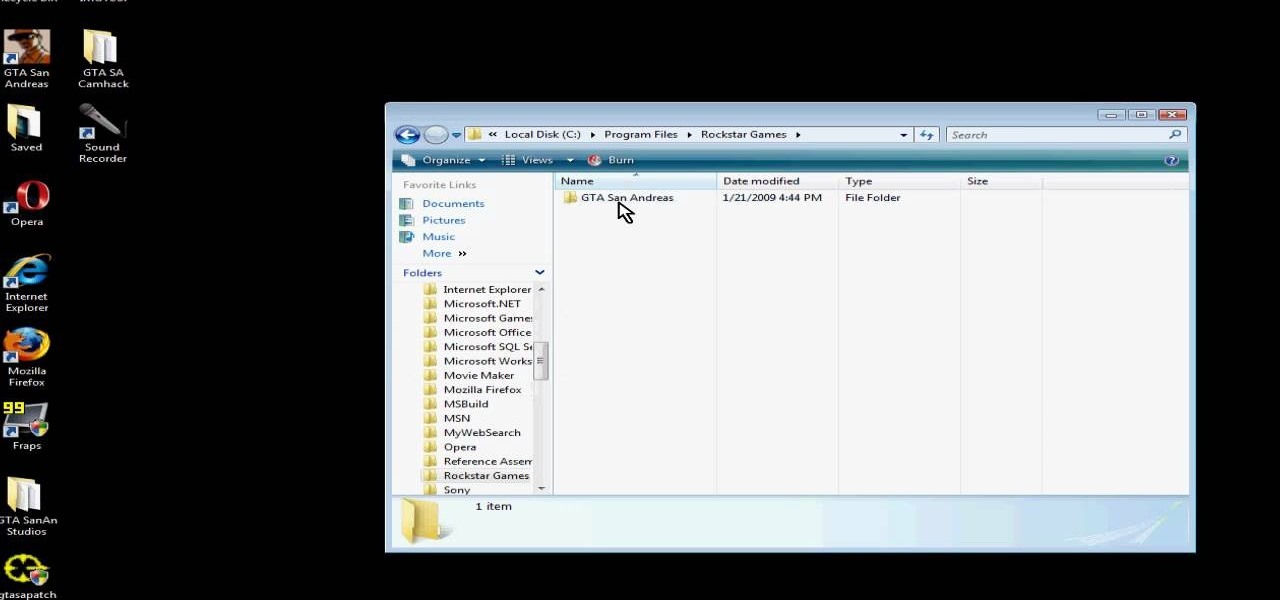
Although Grand Theft Auto 4 was released, many people are still going to want to play GTA San Andreas. Here's how to download and install GTA San Andreas Multiplayer. First, go to Google and search GTA San Andreas Multiplayer. Then, click on the first result that comes up. Go to that website and click on one of the download links that shows up. (Either one of them is fine.) Open the file and follow the Setup Wizard. The installation process takes a very short time and is very easy. Then navig...

Christina, from Brightling Beads shows you how to tie a variety of knots in this video demonstration. This allows you to make a variety of jewelry, using various forms of knot tying. She will show you how to do an overhand knot, double hand knot, square knot, lariat knot, figure eight knot, sliding knot, and surgeon knot. This video makes it easy to do the knot tying, because it uses demonstrations that highlight the sting, and arrows that point to the area that you're working on.

Learn when it’s appropriate to send your meal back in a restaurant, and how to do it without offending the chef.

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

Minecraft is such an incredible game that it allows players to create other games within their Minecraft servers. Here is one that is particularly fun. This is Blockey. Watch this video to learn how to build your own Blockey arena and get started playing.

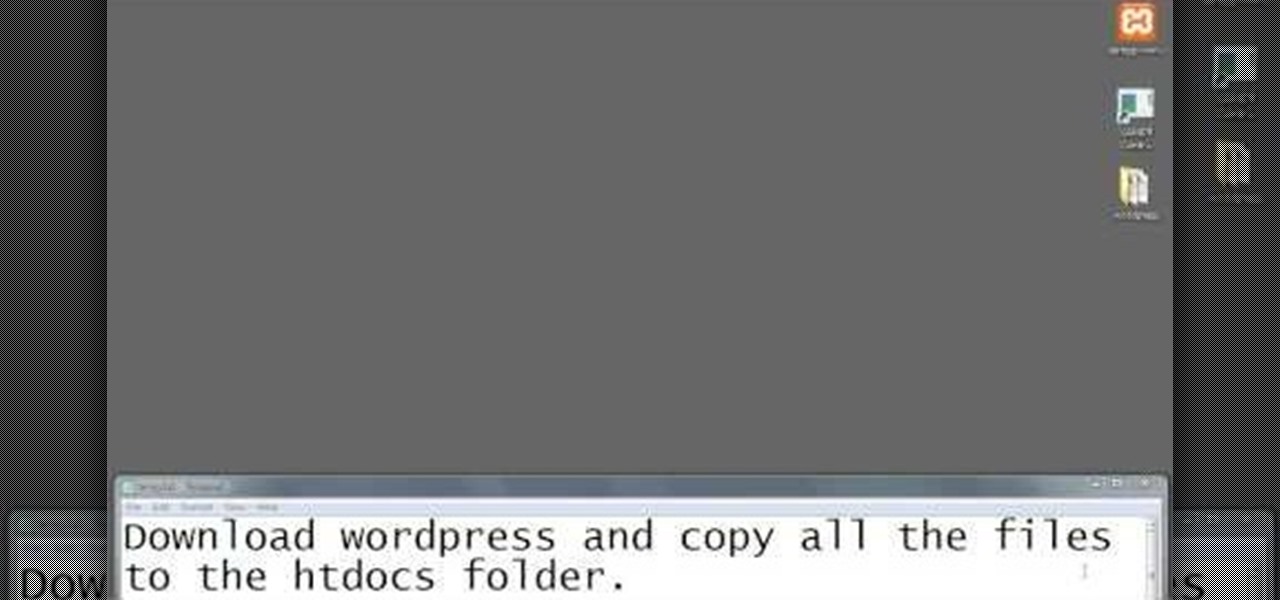
So you want to start your own website / blog / forum / web empire. Good, at least you aren't getting into financial services! This video will show you how to install three important programs that will help you get started: XAMPP, Wordpress, and MyBB. These programs will help you set up your web server, blog, and forum respectively, three important tool that you will need to use effectively to become a force on the web.

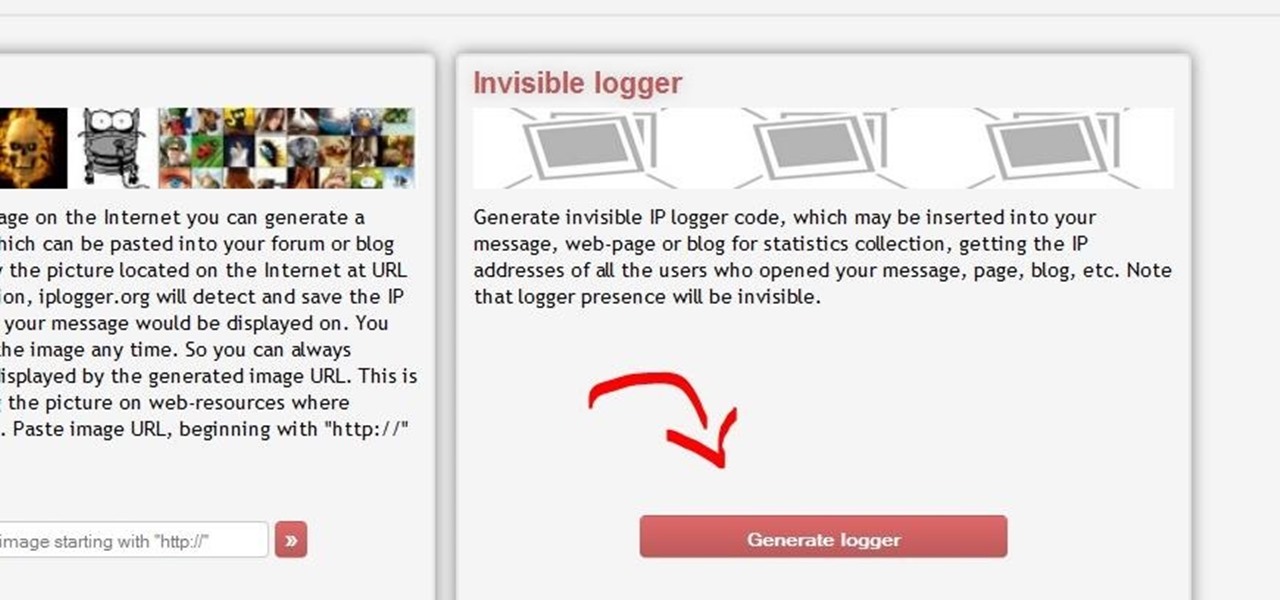
Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.