This video demonstrates how to install Webmin via SSH. Once you've downloaded the Webmin interface package, you'll want to install it onto your serve. In order to do that, you'll need to depackage it. If you're new to Linux or otherwise unclear about how to proceed, then watch this video for step-by-step instructions.
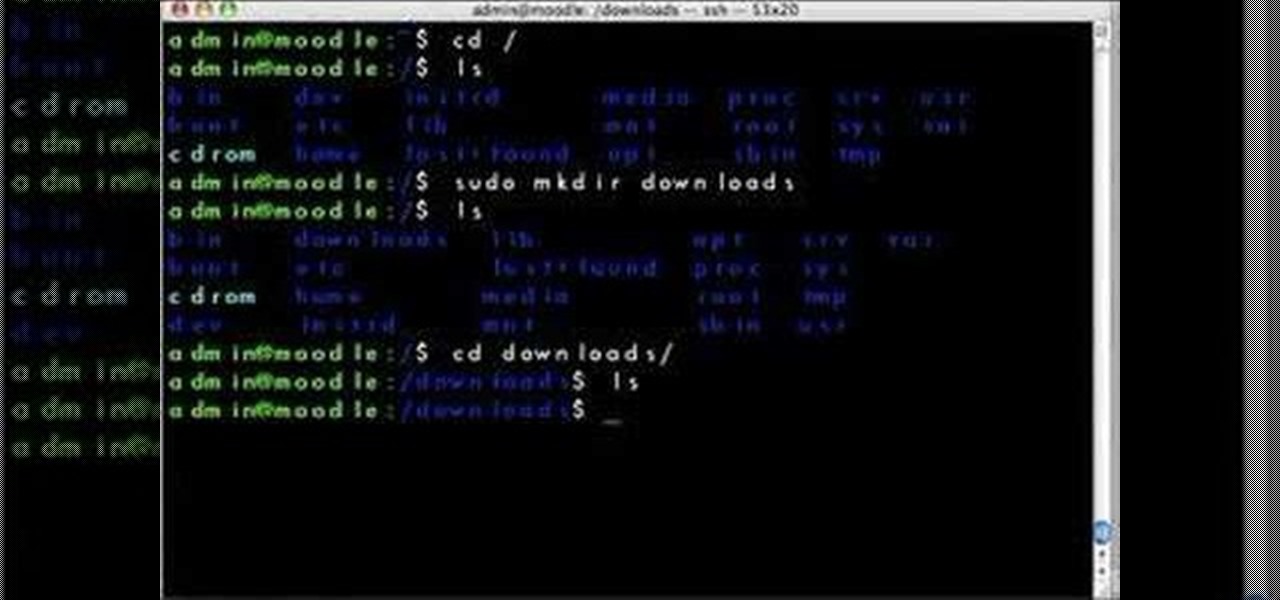
In this video you'll learn how to download Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. If you're interested in running the Webmin interface, then watch and follow along.
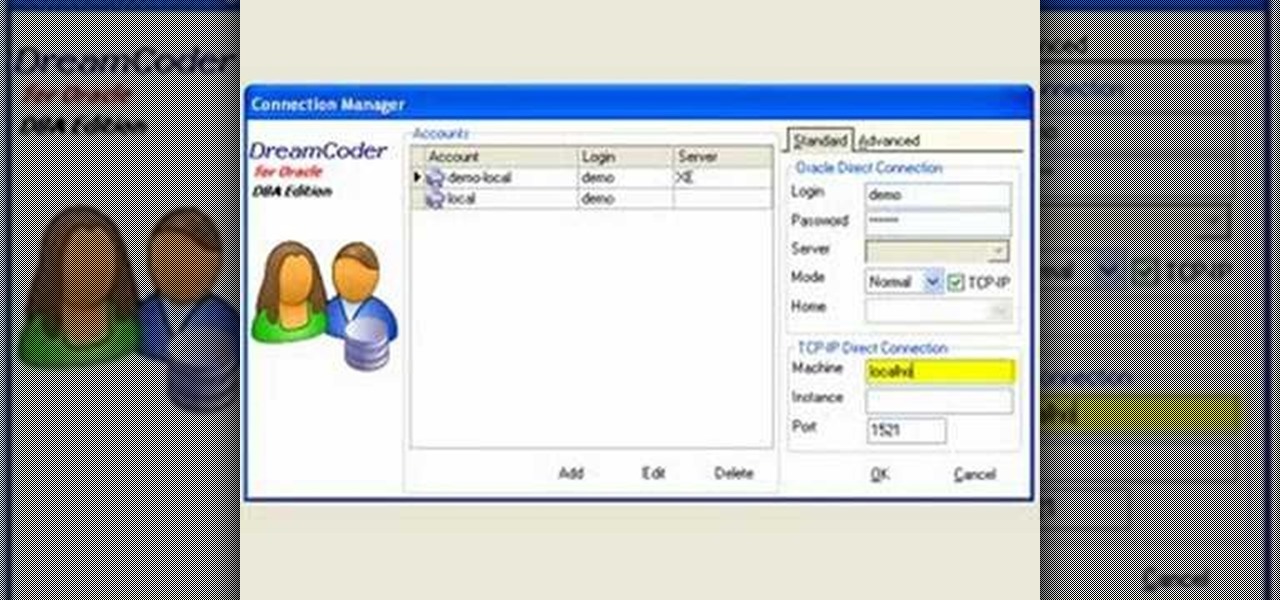
This tutorial will walk you, step by step, through, the process of establishing a connection between Oracle database server and DreamCoder for Oracle using the TCP-IP Direct connection option. To learn more about connecting to an Oracle database without an OCI client, press play!
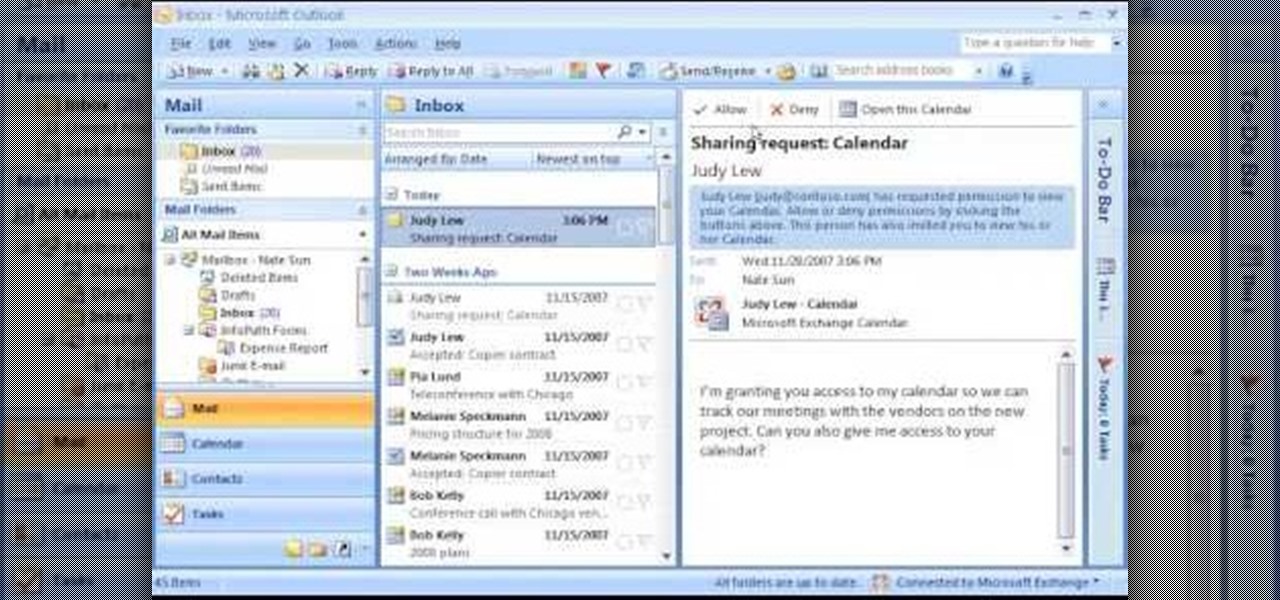
This tutorial shows you how to share your calendar three ways in Microsoft Office Outlook 2007. If your company uses Microsoft Exchange Server, you can share your calendar within the organization by using that feature. You can also send a snapshot of your calendar in e-mail to people outside your company. And you can publish your calendar on the Microsoft Office Online Web site and restrict how much detail is shown and who can access it.
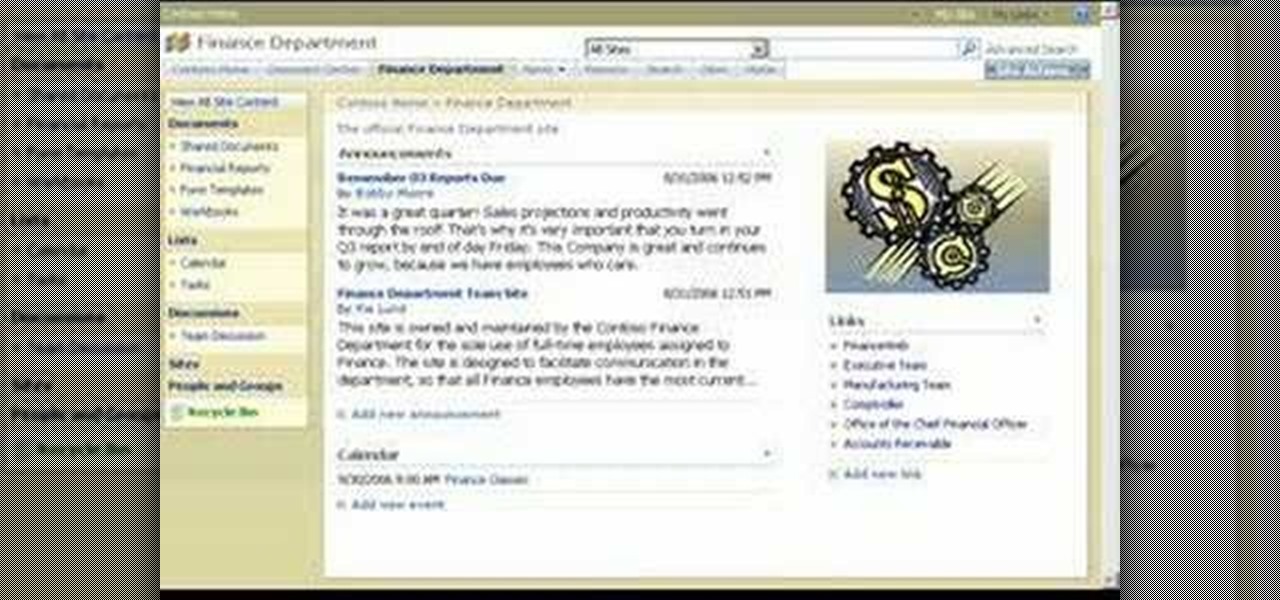
Check out this tutorial and learn how to use Excel Calculation Services to handle processor-intensive calculations from your Microsoft Office SharePoint Server 2007 team site and to control access to external data.
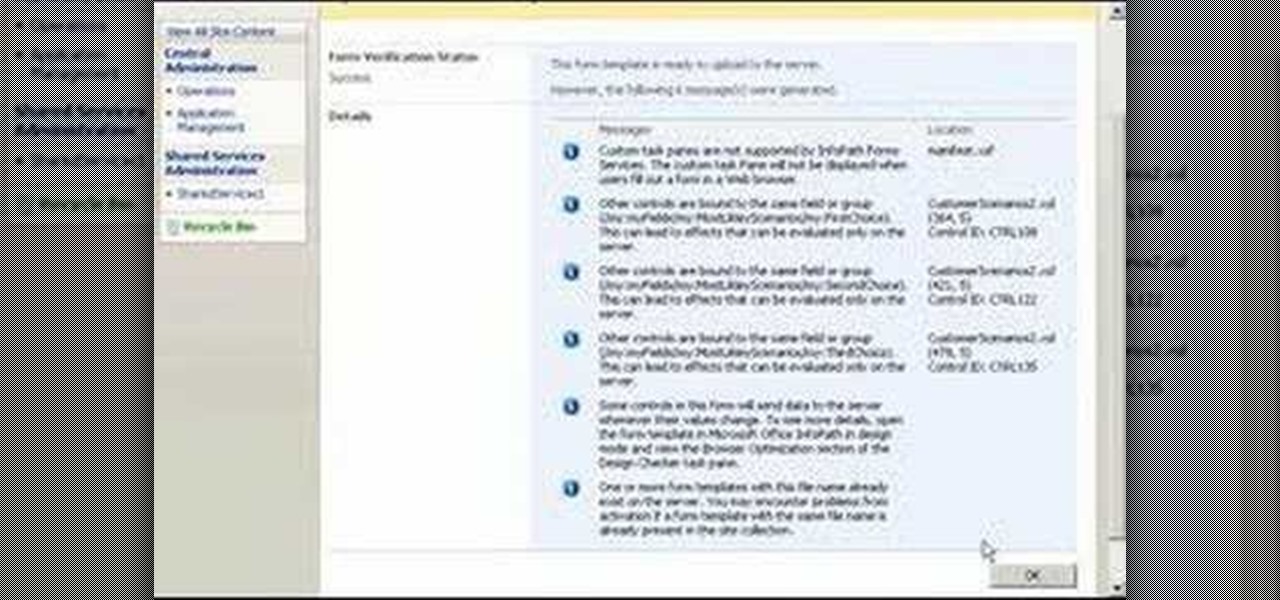
Now you can enable users to fill out Microsoft Office InfoPath 2007 forms by using a Web browser, which makes your forms more accessible to a wider audience. This instructional video shows you how to go through the process an IT Administrator can use to verify, upload, and activate an administrator-approved form template on a Microsoft Office SharePoint Server 2007 site.

This how-to shows how to make gold in World of Warcraft. With this technique you can easily make 500-1000g a day in your spare time. This completely depends on the economy of your server, but it is amazing how you can make so much money.

See how simple it is to create data-driven web sites using ASP.NET 2.0, Visual Web Developer 2005 Express Edition, and SQL Server 2005 Express Edition. Watch this video tutorial to learn how to create a database, add its data, and display that data on a web page.

In this video tutorial, Chris Pels will show how to persist and restore information in the ViewState of a custom user control. First, learn how to persist simple values containing .NET primitive types such as String, Int32, Boolean, etc. Then see how to persist complex types such as Class which contain properties storing information. The sequence of processing View State information during the lifecycle of an ASP.NET page is also discussed.

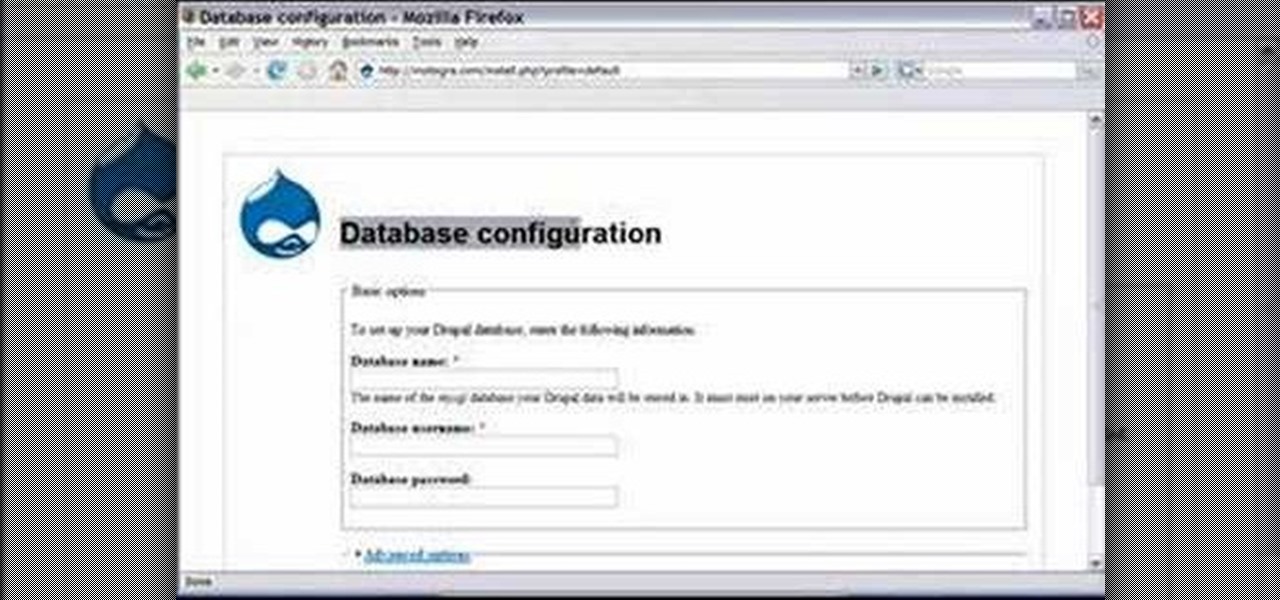
Basic installation of Drupal on a web server from start to finish with good explanations of Drupal's framework. Tutorial assumes viewer knows basic FTP and database configuration.

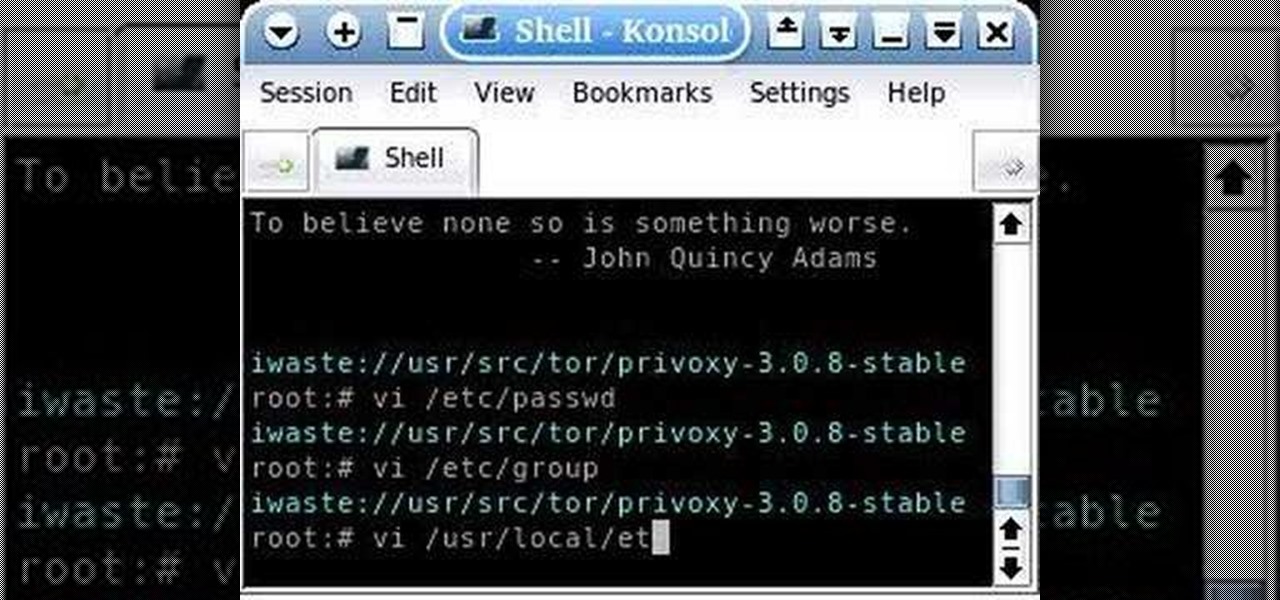
This is a tutorial about how to browse the web anonymously on a Linux server. Requires some knowledge of Linux. Be sure to note that information sent through this system is ever MORE open to hackers than the normal Internet. Don't send any personal information this way.

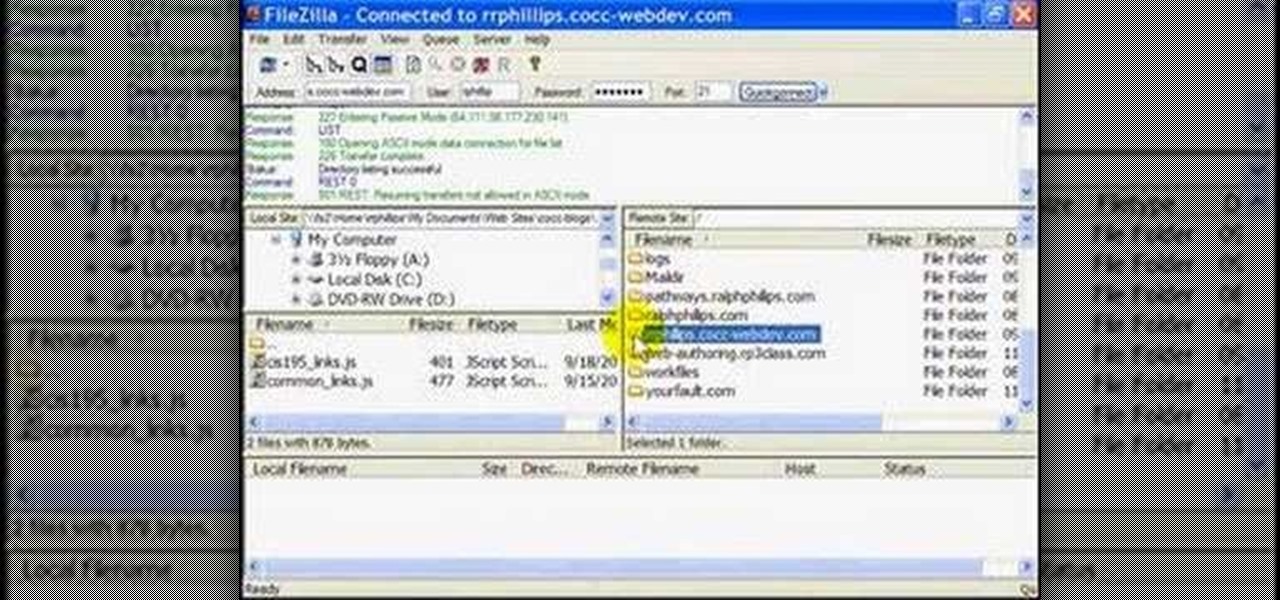
Use the Filezilla FTP client to publish files to your web server.

This video shows a cut and paste illustration of the tools Google offers in it's documents programs. Sharing a document can either occur by transmitting the doc from your home server to another person's home OR you can upload a doc to Google and browse from anywhere-- not just your home computer.

In this tutorial, we learn how to open a variety of coconuts. These fruits can be extremely difficult to open up, but it can be done. First, you will need to have a very large and sharp knife and all of your types of coconuts. To open them up, you will need to first crack the skin of the coconut with the sharp knife. On other coconuts, you can simply use the knife to cut the outer skin off to get to the milk that is in the middle. Whichever way you choose, just make sure you have a very sharp...

Ilysa Bierer and Kira Slye with Polymer Clay TV demonstrate how to embellish wall decals with polymer clay. Wall decals come in a variety of styles. You can embellish wall decals in a variety of ways to make them your own. Take transfer paper and use parts of the design to incorporate into your polymer clay figures. Cookie cutters are handy ways to cut out polymer clay shapes. After you cut out your shapes with the cookie cutter, you can use the piece of clay with the negative space and place...

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Our server is primarily a fun server, so we don't often get huge, epic builds of amazingness. And yet that's exactly what we've got with Mgabrys's build, the Portland. Or, more specifically, Zeppelin City OR-2019 "Portland".

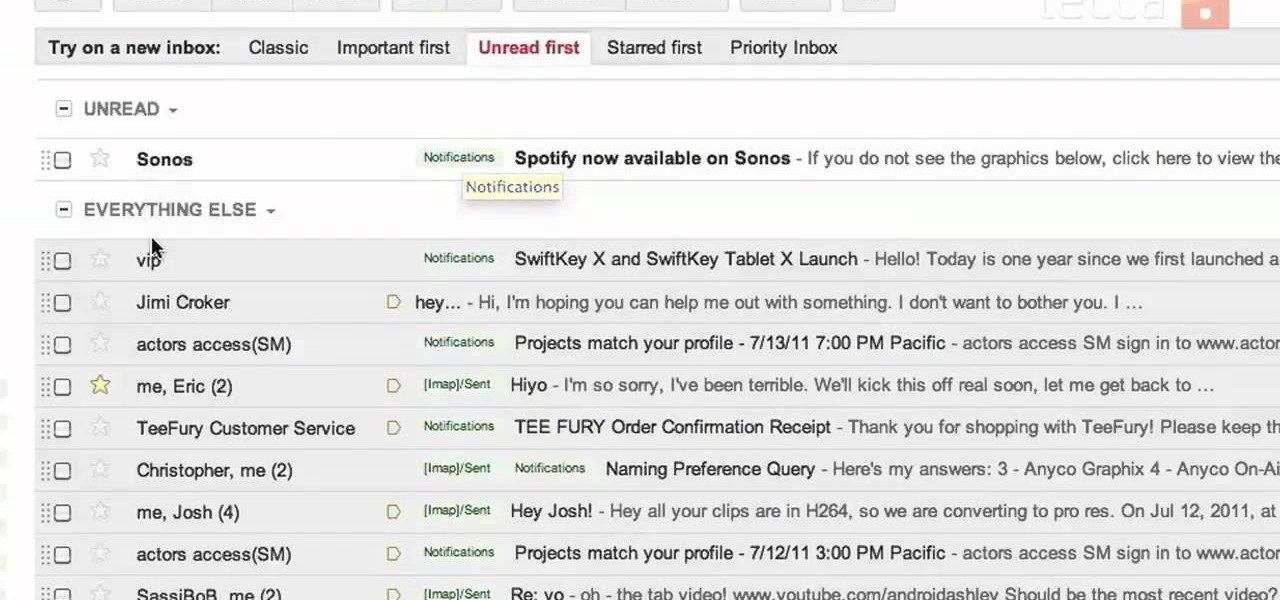
The Gmail interface is highly customizable, allowing you to organize your email messages in a variety of ways. One of the best ways to organize the email is by changing your inbox view. By trying a different inbox view mode, you can prioritize your email messages by importance, unread order, starred emails, and more. So give the different inbox views a spin and see if it helps you better manage your Gmail messages.

When you remove the multifunction switch from your Saturn S-series car, be sure to disconnect the battery and remove the airbag fuse so that you can safely interact with the switch.

The Trapcode suite is a set of plug-ins for After Effects that allow video artists to create a variety of effects for inclusion in video and film productions. This particular guide demonstrates the power of Trapcode Particular and Trapcode 3D Stroke. Specifically, Wes Ball from OddBall Animation reveals how Trapcode was used in the creation of 'Eye of the Storm' - a music video by Lovett which can be seen here.

Most recipes usually don't call for whole vegetables, which means that if you're learning to cook, you'll eventually have to learn how to cut vegetables.

In a survival situation, one of the most vital pieces of gear you can have is a fire starting kit. If you aren't adept at starting fire and want to be prepared for a disaster, watch this video for a guide to assembling a basic waterproof fire starting kit that will start a fire for you in a wide variety of survival situations.

There are a variety of sensors on the market for your digital SLR camera - but which one is the right for you? This tutorial gives you a good run down of each sensor with their strengths and weaknesses so you can easily pick the best one for you.

Don't you just love / hate those Mario levels that use the elements to add variety to the platforming? World 2-4 in New Super Mario Bros Wii is a classic Mario wind level, and this video will teach you how and where to find and get all of the Star Coins in the level.

The Moog is the original and arguably still the king of the analog synthesizers. It looks like an old phone switchboard, and can create a dizzying variety of unique, warm sounds. This video will show you some advanced features of the Moog, including how to use the sequencer to add filters to your tones.

The variety of tutting combos you can learn and create is limited only by your creativity. If you've already got some good moves and you're looking for an advanced combo to add to your repertoire, watch this video. It will teach you step-by-step how to do a really hot tutting combo.

Angle grinders are very powerful and useful tools, but like many such power tools they are extremely dangerous if you don't know how to use them. This video goes over a variety of must-know safety precautions that you should take before using an angle grinder to grind for your own construction projects. It covers proper eyewear, fire protection, and setting up the device for use.

Reading people's minds is something that most inquisitive and sensitive people have wished that they could do at some point. Well, what if you could? This video will show you a great multipurpose bar trick that will allow you to appear to read the mind or body of people in a variety of situations. It's really remarkable how easy this is and how well it works.

Tying knots can be fun and a great way to help pass the time. They can be used to decorate a variety of different things. For this video tutorial, you'll be finding out how to tie a dragonfly knot easily. It's a decorative Chinese knot and is one of the more popular ones searched for online. So check out the video above, pay attention, and enjoy!

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to play WoW on your iPod.