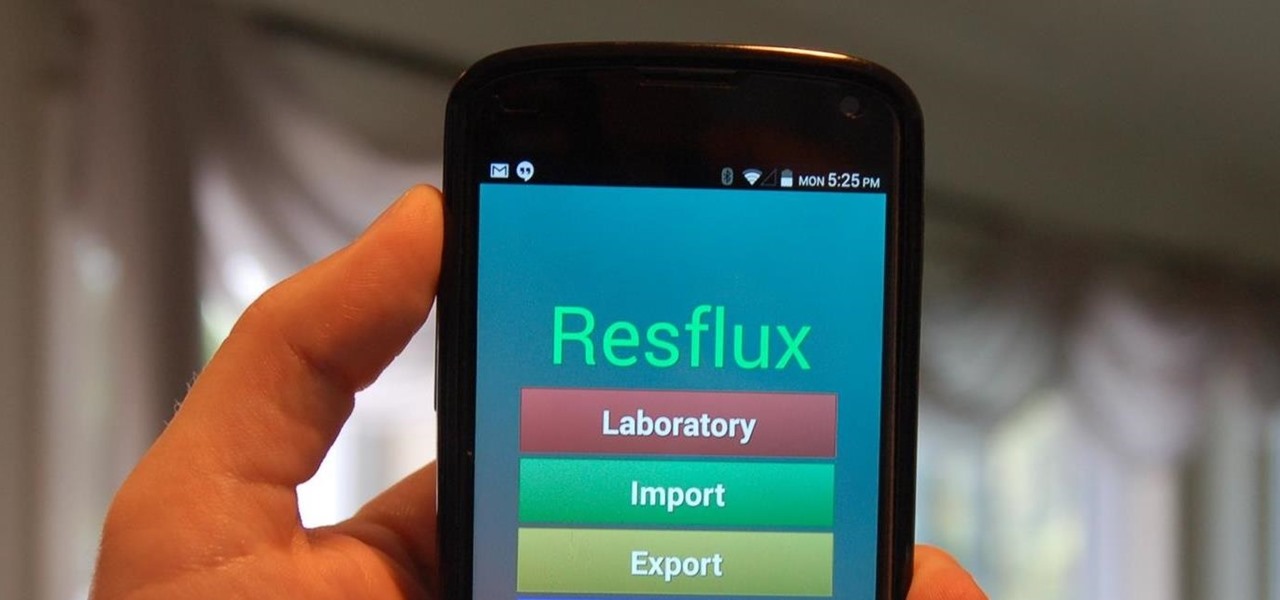
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.
One of the best aspects of Android is its customization options. You can change launchers and icons, add widgets, and replace standard apps with others that allow full customization. Android allows your device to really take on your personality, from the inside and out.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

Religion is one of the most-ignored topics when it comes to Steampunk, which is surprising given how important religion was in Victorian England. Even the hot-button issues of race and gender are confronted with a greater awareness than religion.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Since the start of the COVID-19 pandemic, Google has packed new functionality into Google Meet to compete with Zoom, Microsoft Teams, and other video conferencing platforms.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for an app that will work well for the task at hand, two million is a lot to sort through.

Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

The latest immersive production from Magic Leap Studios finally got its debut on Monday at Siggraph, during which the company also released the app to the general public, so we took it for a spin.

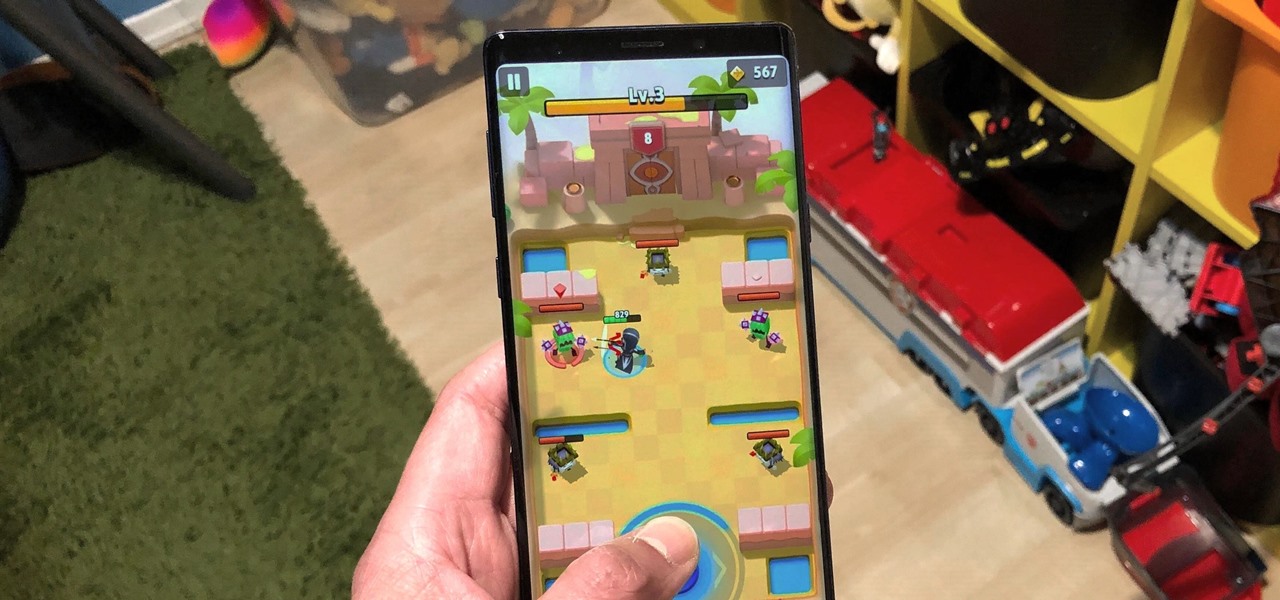
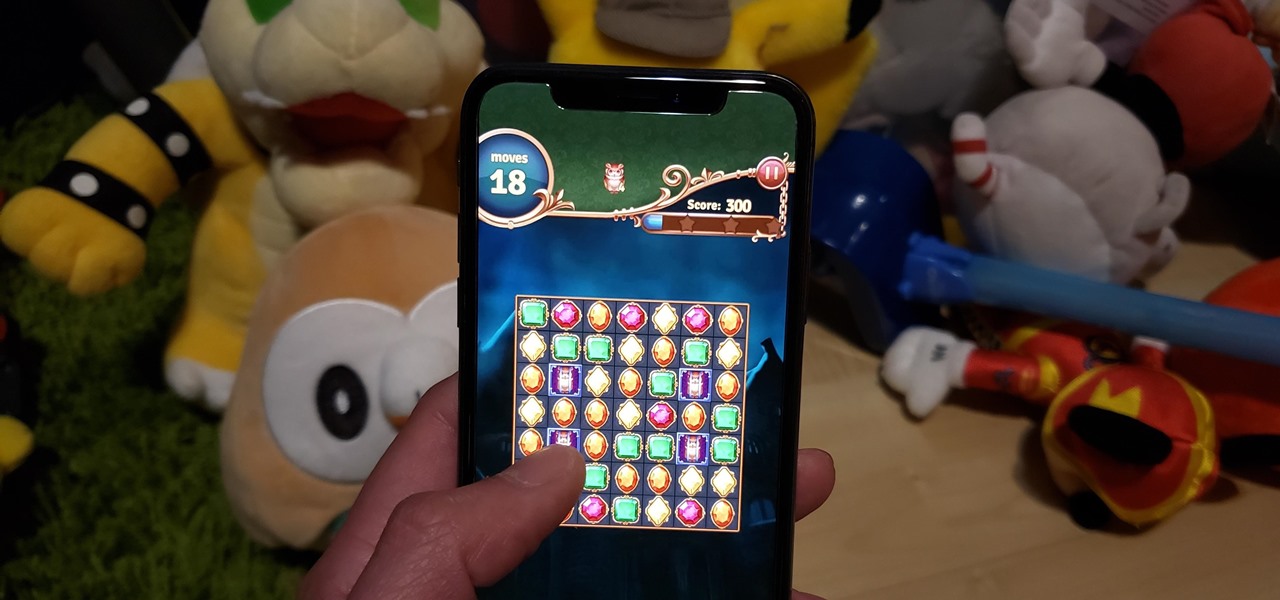
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Creating doodles on an iPhone is made easy thanks to the "Draw" tool in Notes and "Digital Touch" for iMessages, but these are limited in scope. Drawing in Notes has no animated effects, and while Digital Touch does, its drawing tools are lacking and the animations can only live within iMessages. If it's animations you want, Apple has another app that can help you create them.

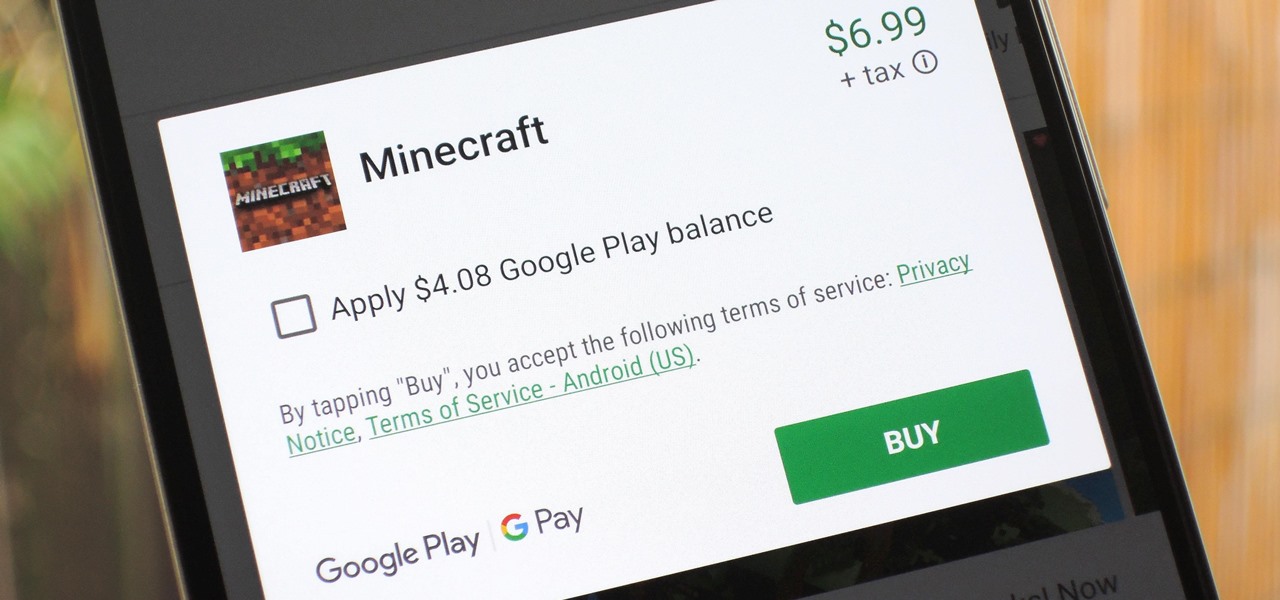
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

When it's all said and done, it doesn't really matter who did it first — the more important question is who did it best. Still, it's nice to know who's really responsible for groundbreaking innovations in the smartphone space.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

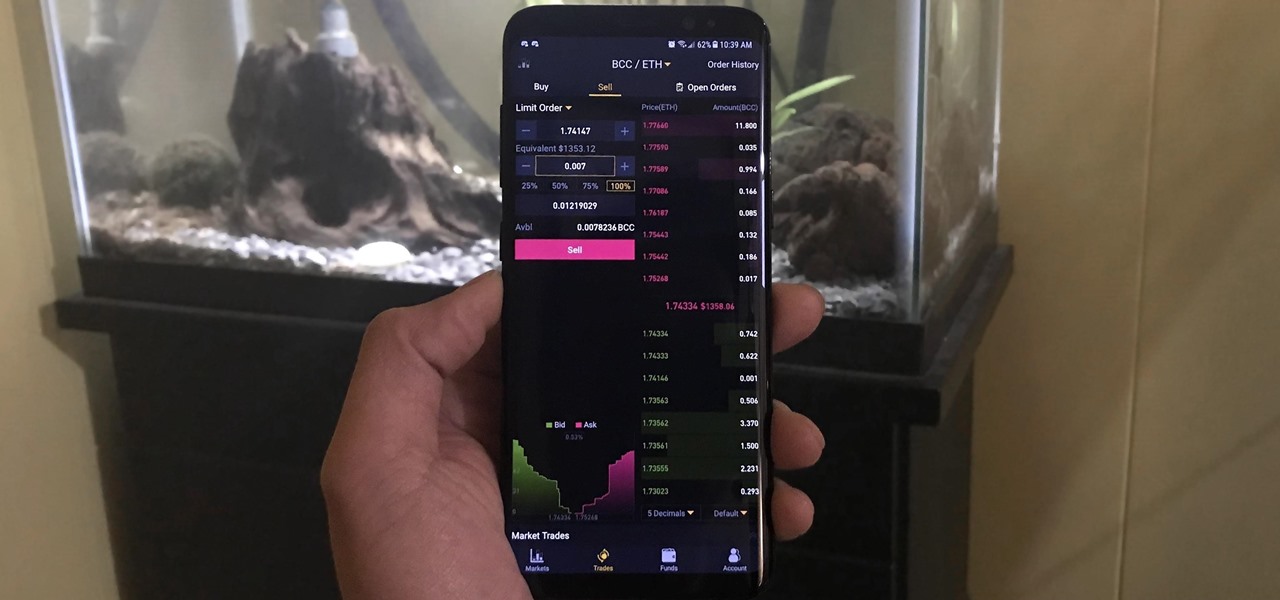
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

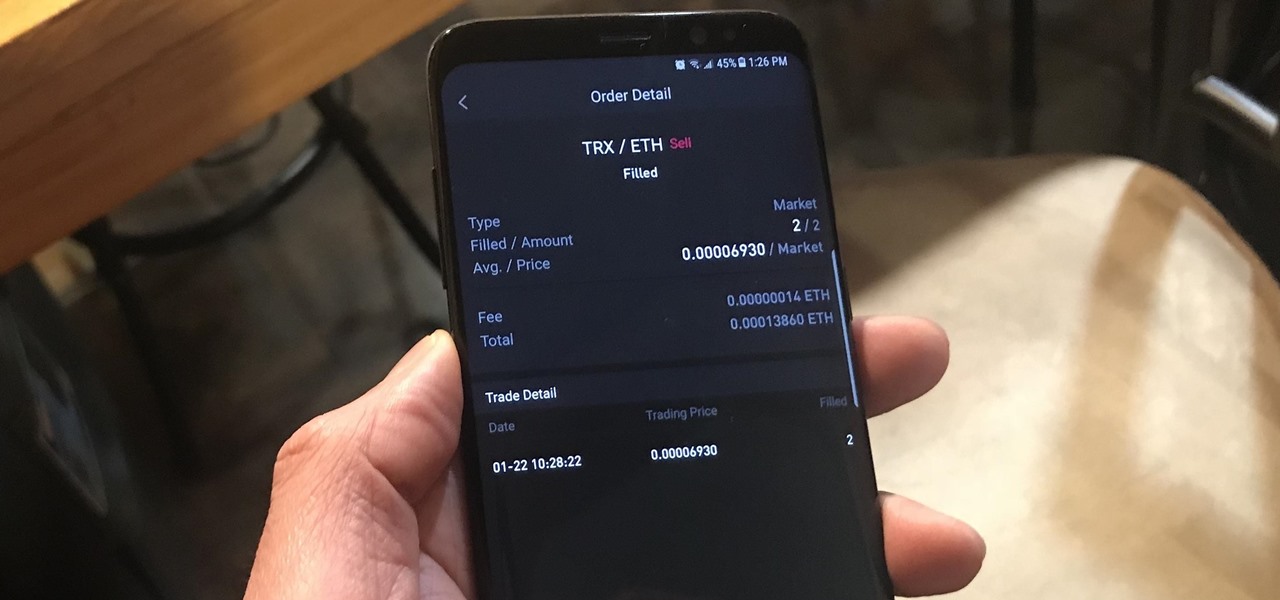
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.