You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Cuffs can make or break a fashion design, and illustrating cuffs well helps a designer sell a collection. Learn how to draw cuffs for fashion design from a pro designer in this free fashion illustration video series.

Seventy-five years ago, a St. Louis widow named Irma Rombauer took her life savings and self-published a book called The Joy of Cooking. Her daughter Marion tested recipes and made the illustrations, and they sold their mother-daughter project from Irma's apartment. Today, nine revisions later, the Joy of Cooking--selected by The New York Public Library as one of the 150 most important and influential books of the twentieth century--has taught tens of millions of people to cook, helped feed a...

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

As one of the household brands in creative software, Adobe is now ready to lay its claim to the artistic side of augmented reality.

Magic Leap and AT&T have lifted the lid on multiple parts of their mysterious relationship today. According to AT&T Communications CEO John Donovan, the company is planning to launch a beta version of DirectTV Now for the Magic Leap One in 2019.

Less than 20 days after the launch of Magic Leap One, Mapbox has jumped at the chance to provide its map services to Magic Leap developers through its Maps SDK for Unity.

In the latest example of life imitating art, IBM has applied for a patent for a video censoring system that looks a lot like the "Arkangel" child monitoring system from the latest collection of modern sci-fi fables from Black Mirror on Netflix.

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

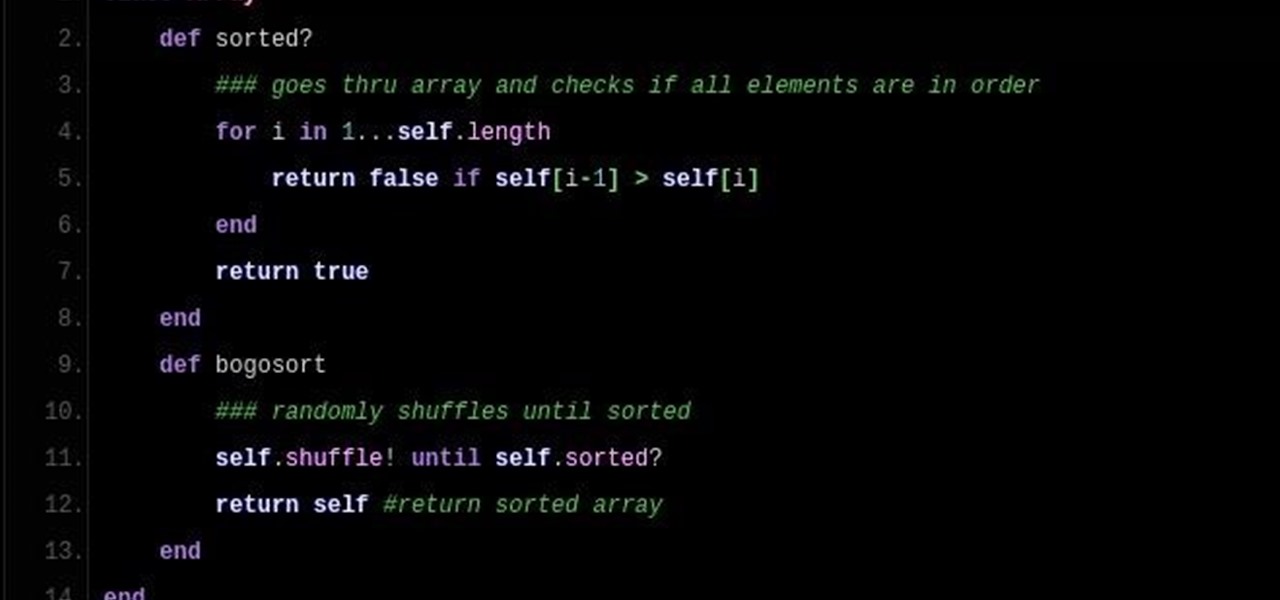
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

Illustrator/Character designer Joe Bluhm talks about his process and philosophy as he paints a caricature of Bill Murray (as Steve Zissou from the Wes Anderson film "The Life Aquatic...") as part of an illustration for a Canadian Pop Culture Magazine called the Naked Eye (available in USA, as well). Using Adobe Photoshop, Joe renders the face in very little time to demonstrate his approach to an entirely digital painting, with a cartoony and loose feel to the art.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

Occasionally, a not-so-great movie also does something so right that you have to forgive some of its sins and give it a little love. Such is the case with the latest film from Keanu Reeves, Replicas, which takes a HoloLens-style device and gives us a look at how future research labs might use that kind of augmented reality device, sort of.

Snapchat is one of the best ways for people to communicate with pictures, but it has a ton of other features baked into it. From the Memories feature to My Story, there are many ways to save save and share snaps among friends. Sometimes though, you want to add a little more pizzaz to your snaps. Luckily, Snapchat gives users a myriad of ways to interact with snaps before they're sent.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Whether your holidays are cause for celebration or exhaustion from over-celebrating, alcohol is more often than not involved in the merrymaking. We at Food Hacks are very fond of enjoying this particular indulgence in lots of different ways.

There are many apps and features on your iPhone that you may never use, and therefore don't need. A great illustration of this is the Apple Watch app. You might have no interest in ever getting an expensive smartwatch, yet you're stuck with the Apple Watch app on your home screen.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

Recipes are invaluable to cooks who are just starting out, but what if you want to get to the next level? Then it's time you learn how to apply simple math to food. In other words, learn how to cook using ratios, not recipes.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra hardware, like on the new HTC One M8. The camera does this by utilizing a depth map through the processing of multiple images. Frame your photo, move the camera (phone) in an upward tilt or motion, and the software capture...

This video clip shows you how to hit a straight tee shot in golf. There are two parts to this shot. There is the swing path and the face direction. Using a line of golf balls as illustration the demonstrator shows you the path that the head of the club should take as it approaches the ball. Just before impact the head will square up and look in the direction of the target impact. This is called the face direction. There are thus two aspects to a straight shot. The path must be in the correct ...

Snapchat offers a rich experience for anyone looking to communicate with pictures in addition to (or instead of) words. There are many ways to share your snaps, from Memories to My Story. You can even draw all over your snaps, creating a unique experience that hinges on your own illustrations. Sometimes, though, you want to customize your snaps in a different way. In a more collage-y sort of way.

Just when you thought Google Glass was dead, it turns out there may be a second life for the often ridiculed device that won't relegate it to the staid confines of factories and repair jobs.