Everyone talks about how great sliced bread is, but there's nothing better than the taste of a just-baked loaf of crusty French bread. Like most beautiful things in life, however, the beauty of the baguette doesn't last. The next day, it's rock-hard, and good for very little except for croutons or breadcrumbs. But there is a trick to make it like fresh again.

Love the beauty and fresh fruit of trees but have limited space? Try your hand at dwarfing a tree. You can enjoy all the benefits of a tree without any worry of the tree outgrowing the area or roots damaging side walks and property. Plus, they just look adorable.

A bouquet of fresh roses is wonderful but real roses soon fade and die. Make a rose that will last forever, or at least a lot longer that a freshly cut one. Give your rose to someone special or use it as a decoration.

Whenever a new hard drive is purchased for a computer, it needs to be formatted to work with that computer. Formatting a hard drive on a Macintosh computer is a fairly easy process.

In this series of home laundry videos, you will find out the best way to iron your sheets from an ironing expert. Joyce Danielson shares her insider tips on when to leave out the starch and how to tame fitted sheets as well as those heavily creased new sheets fresh out of the package. She also discusses folding tips, how to iron and fold pillowcases, and shares her insights on how to pass the time while ironing.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

It is important to have healthy teeth not only for your appearance but for your overall health as well. You can keep your teeth white by avoiding foods that stain your teeth and having a good cleaning routine including fluoride

Marinate your pork chops before grilling to really make them tender and flavorful. Your family won’t be disappointed when they sit down to a dinner of hot chops just off the grill, so fire up the grill and get started.

Remove all those dust mites and pet dander from your pillows on a regular basis with a good wash in hot water. Pillows can be a little trickier to wash than other linens so keep you pillows fresh and new by following proper washing instructions.

In this video series, learn how to apply mineral makeup. Our expert, Kelli LaBar, shows you everything you need to know to create a fresh makeup look. Learn how to use brushes and powders.

In this DIY project on video, learn how to paint the roof eaves and fascia of your home. Our expert will show you everything you need to know to get the job done. Get tips on preparing the eaves with a pressure washer, scraping off old paint, caulking, spackle, priming, and more. Learn the proper paint mixing techniques to get an even, professional result. Watch these videos carefully, and turn a potentially disastrous endeavor, both for you and your home, into a simple painting project. When...

In this do it yourself video guide to refinishing and restoring wood furniture, learn tips and techniques for how to refinish your old, well-loved wood furniture, including everything from wood stain removal to applying a fresh, new furniture stain. Our expert, Jennifer Ware, will walk you through a refinishing project step by step, with safety tips before you begin, what types of sanders you’ll want to use, and how to choose and apply the right stain for your piece of wood furniture.

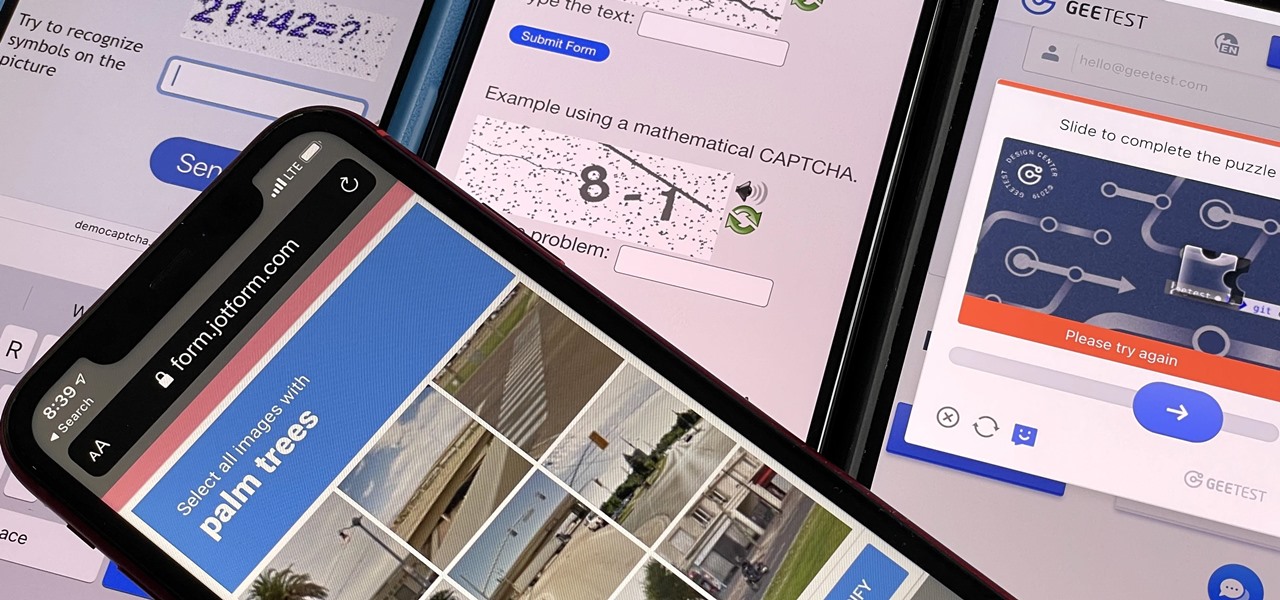
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

Those of you lucky enough to snag a PlayStation 5 can pair your DualSense controller to Sony's PS Remote Play mobile app to stream and play your PS5 games from anywhere you want. DualSense support for Remote Play has been available on iOS since May 2021, and it's just now arrived on Android.

Thanks to the Snapdragon X55 modem, the Galaxy S20 and Galaxy Note 20 are among the most compatible 5G phones on the market. There are few bands they don't cover, as the modem supports both Sub-6 GHz and mmWave. But even with such broad support, the Galaxy S20 doesn't get the best 5G reception.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

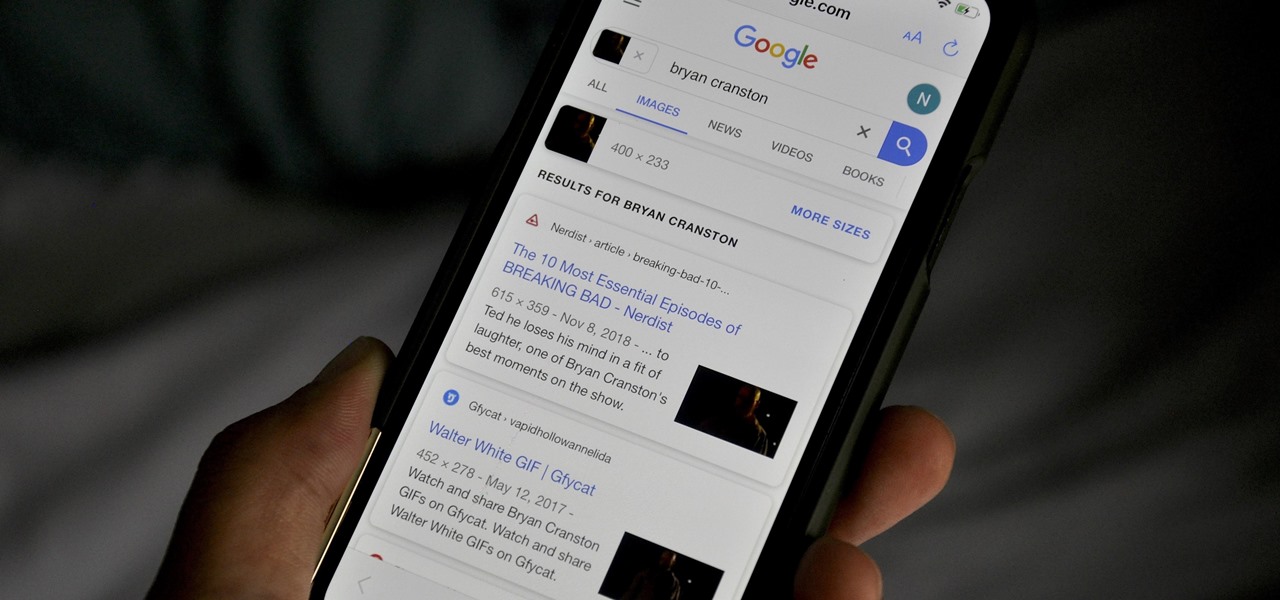
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

I've been using the Galaxy Note 10+ as my daily driver for a while now. I love it, but as with any phone, it loses its pizzazz after a while. But since it's an Android phone, there's always a way to add fresh features and functionality to the UI.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Apple's update for iOS 13 is not without bugs and other issues, and if those problems become annoying or impede your ability to use your iPhone like usual, you may want to downgrade. Hundreds of new features may not matter if you can't use your iPhone like it's meant to be.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.