Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

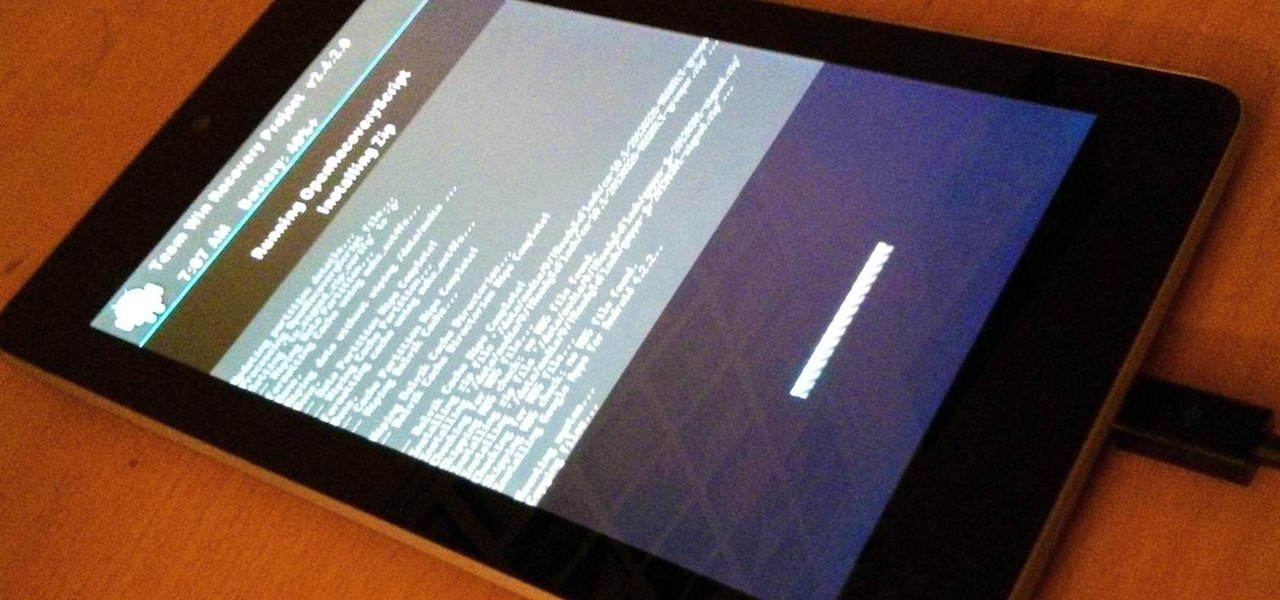
Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

Any pizza lover knows that a quality crust is crucial to the whole experience. Good pizza crust should be delicious on its own, for once you get to the edge, it will be without any toppings, sauce, or cheese to disguise a bad character. It should be redolent of fresh, good wheat and taste full-bodied, rather than flat, flabby, or metallic, the way so many big chain and frozen pizza crusts do. The exterior should be crisp, while the interior contains an airy crumb as well as having a tender, s...

The Moto X introduced tons of cool features that have slowly been ported over to other phones, like Peek notifications and always listening "OK, Google" detection. Another such feature allows you to twist your wrist to bring up the camera app from any screen—even with the display turned off.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.

I own two aprons—a cute one for company, and another for the hard-core cooking duties, like cutting up chicken and making stock. The sad truth is that I almost never remember to wear either of them. So, much of my clothing ends up spattered with grease, liquid, and bits of fruit and vegetable. While stain-removing sprays, sticks, and pens are all effective to a certain extent, they have two drawbacks—they're expensive and sometimes I need to use them in large quantity, like when a piece of eg...

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

Cleaning a blender thoroughly is a pain in the ass, especially when you try and get all the goop out from underneath the sharp blades without nicking your knuckles. Alas, it is a necessary chore, otherwise you end up with disgusting dried gunk that ends up in your next batch of pureed foods. Fortunately, there's an easier way to get your blender sparkling clean besides using easier-to-clean mason jars as you main jar, and the best part is that the appliance literally does all the work for you.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

We've already taught you a few tricks for getting chilled, rock-hard butter to spread easily on toast, and some of you probably bypass that issue entirely by purchasing spreadable butter from the supermarket. But why waste your money when you can make a healthier, tastier version at home for a fraction of the cost?

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

About ten years ago, Western research figured out that green tea was a nutritional powerhouse. After all, in Asian countries where green tea is consumed throughout the day, cancer rates tend to be much lower, although there are probably other factors contributing to that fact, like less processed food and red meat in the standard Asian diet.

Though nobody's going to hide the fact that they're getting sloshed on major holidays, you might want to be more discreet when it comes to your morning pick-me-up or lunchtime tipple during the rest of the year. It used to be that having four martinis at lunch was acceptable and even desirable, but that's really not the case anymore.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

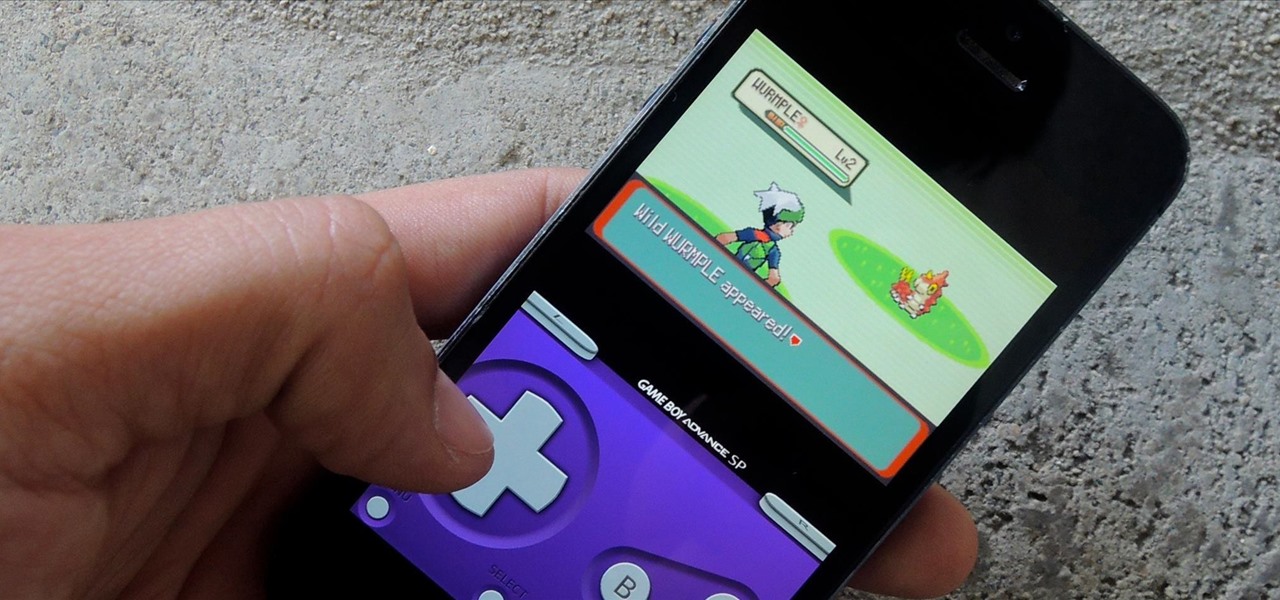
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

The launch of Android 4.4 KitKat alongside the Nexus 5 was met with much fanfare from Android enthusiasts. Unfortunately, if you don't have a Nexus device or are still awaiting the 4.4 update, you may feel a bit left behind.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

When life gets boring, you change it up. A little tweak in your schedule goes a long way in making your existence fresh again, and it could be anything from putting on deodorant to seeing a movie with someone you don't know. The more flexible you are in life, the more dynamic it should be.

Just because a problem is small or superficial doesn't mean it can't annoy the living crap out of you. Others may think you're overreacting, or even have the audacity to roll their eyes, but you're in your own personal hell.

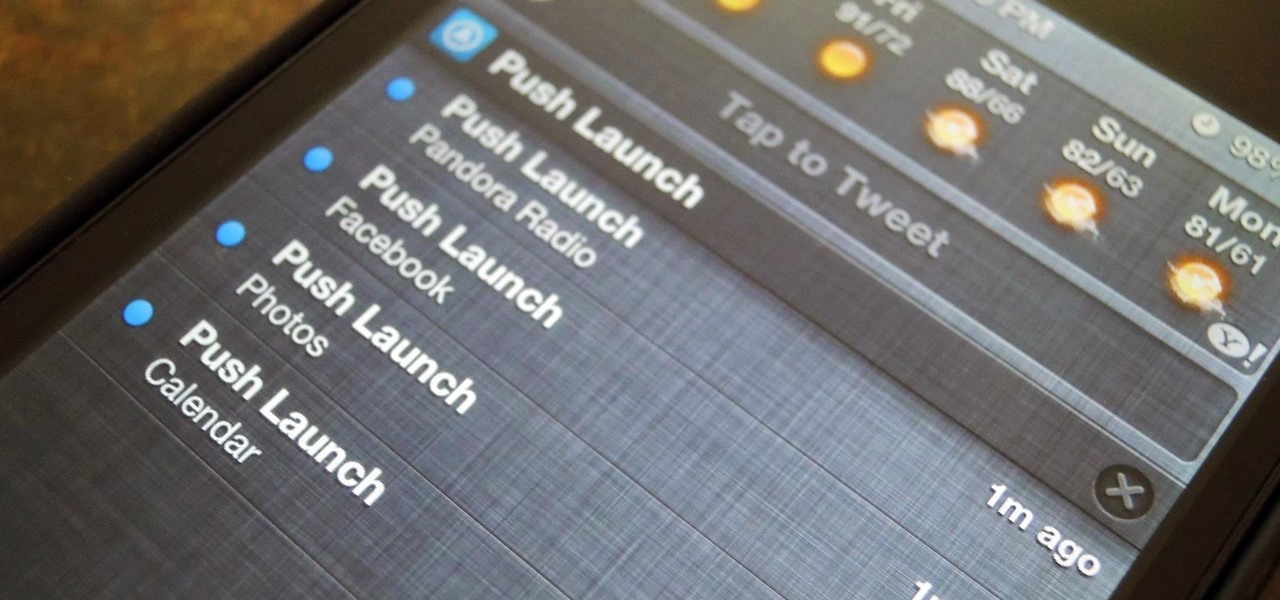
The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

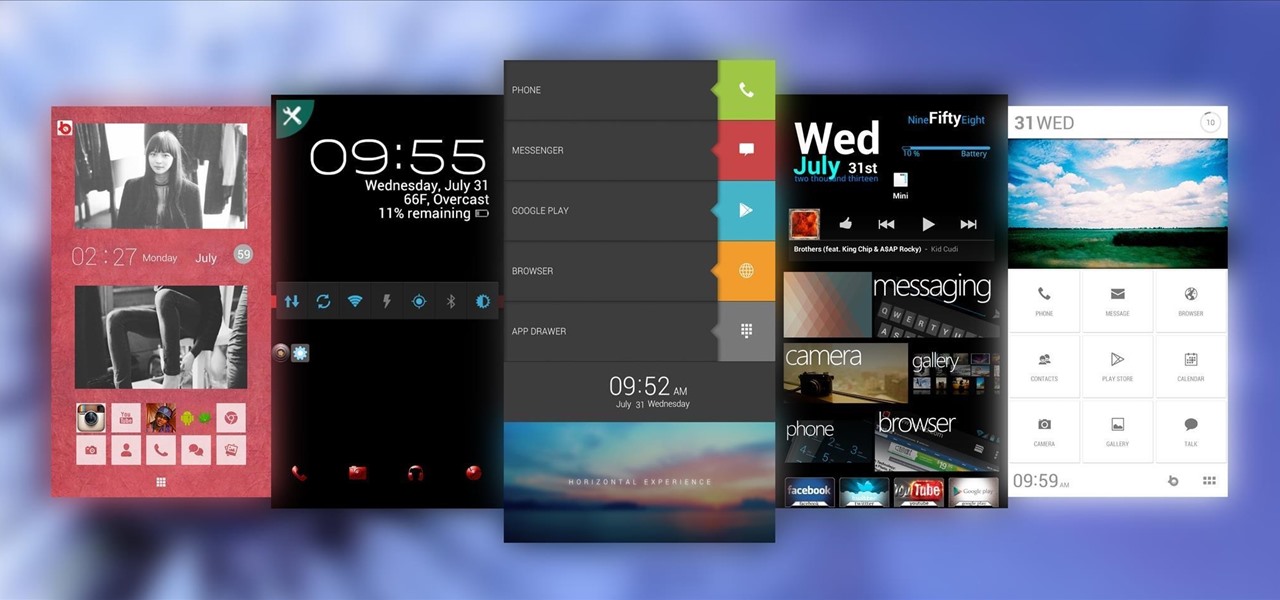
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Other than sticking your crayon drawings onto your refrigerator door, magnets have a variety of unexpected and sometimes surprisingly practical uses, ranging from keeping your chip bags sealed to creating weird patterns on your nail beds using magnetic nail polish.

Welcome to Minecraft World! Check out our full tutorials and make sure to post to the community forum if you have any questions or cool builds you want to share.

Not everything that Facebook does is in the best interest of its users. Just look at past examples such as social ads, facial recognition, and instant personalization. Users were perfectly fine without these, and they still are. And now there's another annoying problem that Facebook users have to deal with—the ticker.

Eat wonderful peaches all year long. Freezing fruit is easy and a great ways to preserve and retain nutrients. Freeze your peaches now and thaw them when you are ready to make a peach pie or smoothies. This is the perfect way to make the most out of your fruit.

Forget the takeout food tonight, watch this how to video and learn how to cook a delicious Korean cod fish recipe. Make a cook "Jeon," a traditional Korean food breaded with flour and eggs. There are many kinds of Jeon, but this one is made with cod fish.

Everyone loves pasta recipes because they are so simple and quick to prepare. This how to video will show you how to make a delicious red pepper and sausage pasta dish. Watch and impress your family by making it for dinner.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.