This video pet grooming tutorial series shows the steps for drying and brushing out the coat of a bichon frise dog. This breed of dog has a particularly fluffy coat which might seem unruly and hard to groom. Regular washings and trimmings keep the fur looking fresh and clean. Watch these instructional videos and learn how to keep a bichon frise dog looking beautiful.

In this video series, Louis Ortiz shows you how to prepare common seafood items. He shows you how to clean and skin a fish. He also illustrates how to pan fry and sear fish. Learn how to clean and crack crab legs. Louis illustrates an important step in eating fresh shrimp. He teaches you how to peel and devein shrimp. So, with these simple preparation tips, you can learn the beginning steps of preparing a tasty seafood meal.

Make a fantastic brisket for your next holiday meal. Brisket can be dry and bland when not done correctly so remind everyone just how delicious and oven-roasted beef brisket can be with this flavor popping recipe.

The egg is an incredible compact, nutrition, protein and fat all in one prepackaged unit. This video will show you how to boil an egg using a strainer basket in your boiling water to heat steam your eggs as an alternative to regular boiling.

Our expert, David Postada, shows you everything you need to know to prepare the stuffing with fresh vegetables, corn bread, and chicken stock for stuffed pork chops. Also, learn how to stuff the pork chops. Finally, everything taste better wrapped in bacon.

In these cooking videos, learn how to make a fried coconut shrimp recipe. Our expert will walk you through the process step-by-step, with tips on how to buy fresh shrimp, what ingredients and utensils are needed, how to devein the shrimp, how to add flour, make a beer batter, and dip the shrimp, how to make an orange marmalade dipping sauce, how to fry the shrimp, and how to serve the dish with a little bit of flair.

Our expert will give you some of those key tips to get started; then learn how to make a basic fresh fruit smoothie. Other recipes include a vegetable smoothie, a detox smoothie, an energy smoothie, an immune booster, smoothies for dessert and more. Click on a recipe that seems tasty and go for it.

In this easy dessert video recipe, learn how to make lemon mousse from expert chef Karen Weisman. Karen will teach what supplies and ingredients you will need to make a delicious lemon mousse. She will also demonstrate how to juice lemons for lemon mousse, how to separate egg whites from egg yolks, how to use dried egg whites as an alternative to fresh egg whites, how to combine gelatin and lemon juice for lemon mousse, how to prepare a trifle dish for lemon mousse, how to prepare lemon souff...

In this DIY project on video, learn how to paint the exterior of your home. Our expert will show you everything you need to know to get the job done. Get tips on preparing the wall with a pressure washer, scraping off old paint, caulking, spackle, priming, and more. Learn the proper paint rolling techniques to get an even, professional result. Watch these videos carefully, and turn a potentially disastrous endeavor, both for you and your home, into a simple painting project. When you’re done,...

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

There are now more emoji on your iPhone's keyboard that you can send as reactions or stickers or insert wherever else you use emoji — and it's about time. It's been nearly a year since the last emoji update for iOS, and we only received support for 31 new ones then. The new iOS 17 software update brings almost four times as many.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

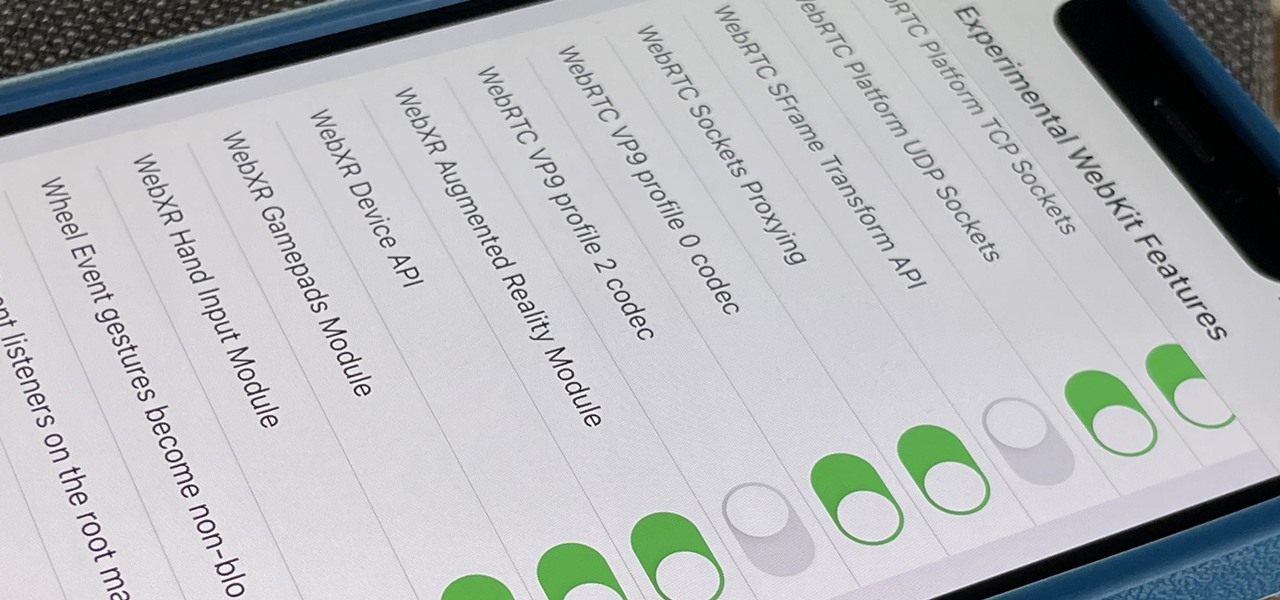
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for an app that will work well for the task at hand, two million is a lot to sort through.

Apple's iOS 14.5 is the biggest update since iOS 14.0 came out, with over 50 confirmed features and more being discovered every day. There are new emoji, support for AirTags, more privacy controls, and exciting upgrades to Siri, Maps, Reminders, Podcasts, Music, and even Shortcuts. So it wouldn't surprise us if you want to get this on your iPhone ASAP.

For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.

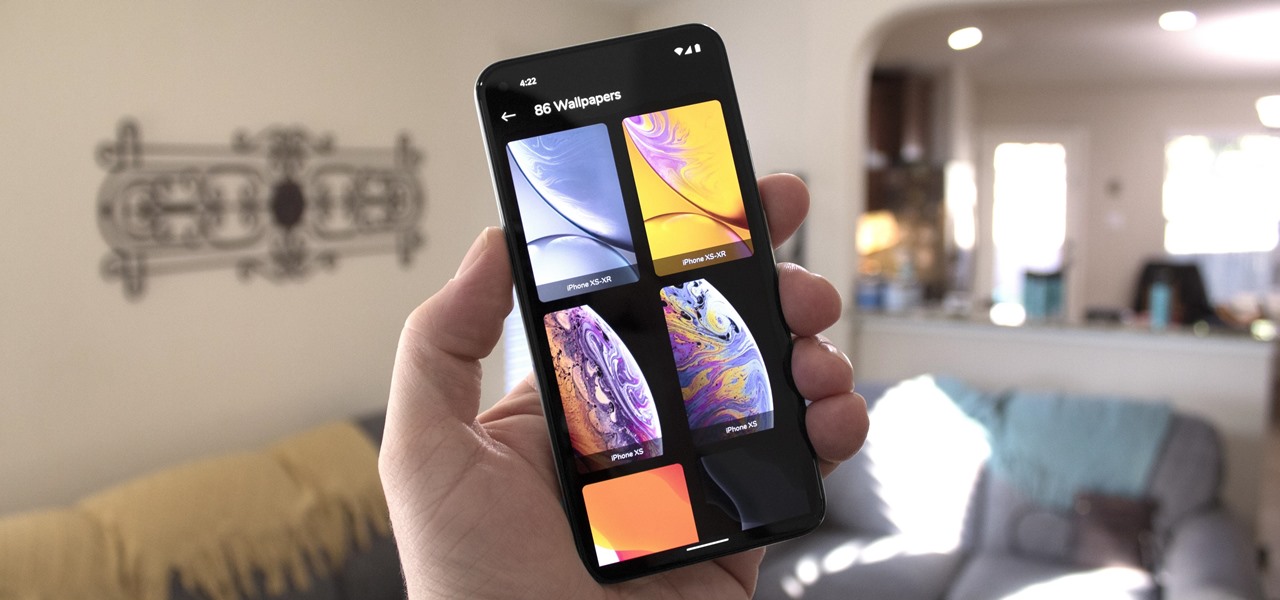
These days, the only thing your eyes view more than your phone's home screen is the backside of your eyelids. So it goes without saying that whatever picture you have as your background gets old pretty fast.

Every mainstream Android home screen app looks and behaves almost exactly like Google's Pixel Launcher. It's the trendsetter, like the Nexus Launcher before it. But when all your options are modeled after the same thing, that really takes the "custom" out of "custom launcher."

Your phone tracks your every move to some extent, and I'm not just talking about Google services. Smartphone manufacturers use telemetry services that run in the background to track how you use the device, mostly for ads or to improve their future products. You don't usually have a say in the matter, but if you have a rooted OnePlus, there's a way you can take control over it.

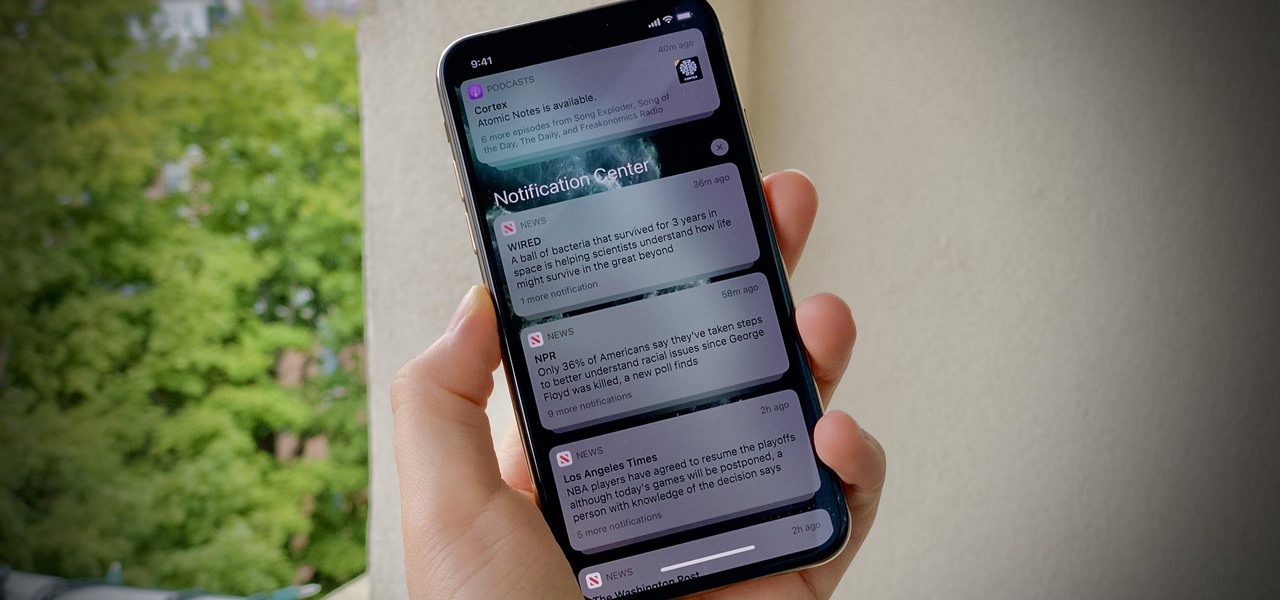
If you're like me, no matter how hard you try, your iPhone's notifications are a mess. There's just too many of them. That's when it becomes helpful just to get rid of the whole bunch and start fresh. However, deleting alerts one at a time is as tedious as it is unnecessary since you can clear all of your notifications at once.

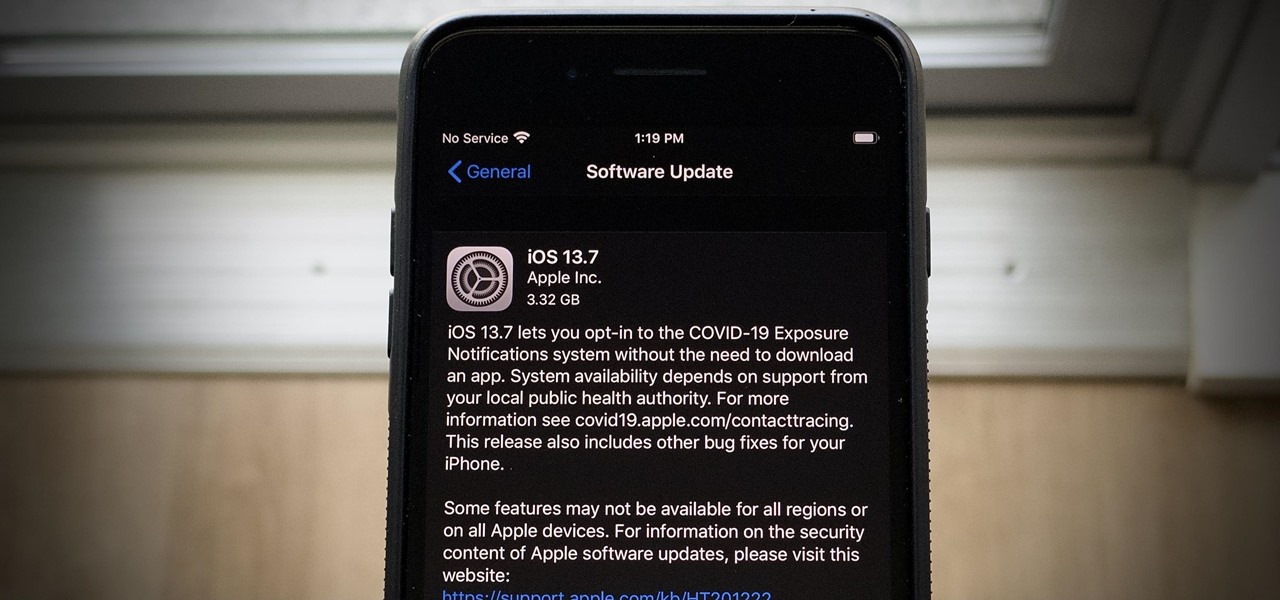
The iOS 14 beta may be picking up steam, but the iOS 13 beta program isn't out for the count. With the release of the iOS 13.7 beta, build 17H33, Apple has included API changes for the COVID-19 Exposure Notifications setting. The update makes it possible for public health authorities to let iPhone users get coronavirus exposure alerts without installing their state's app.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

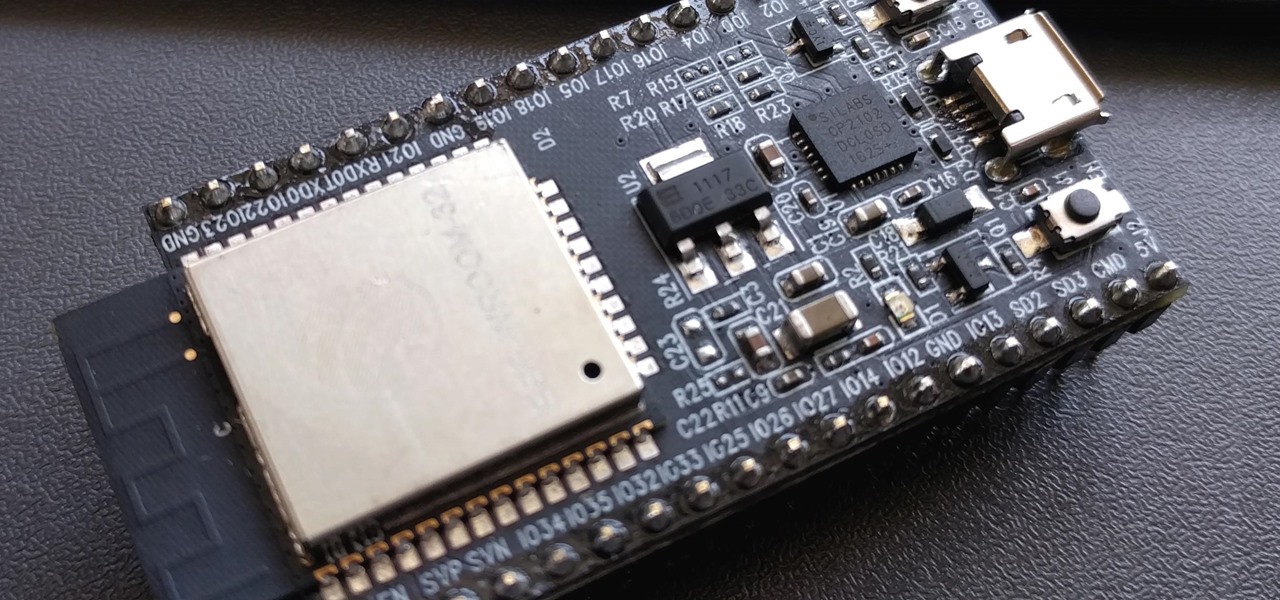
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

The iPhone 11, 11 Pro, and 11 Pro Max introduced a new rear camera system to the iOS ecosystem. Each model has a new ultra-wide lens in addition to the wide one, and the Pros have a telephoto lens. Both have improved selfie cams too. With so many lenses, it can be challenging to choose which to film with, but why pick when you could shoot with two at once?

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

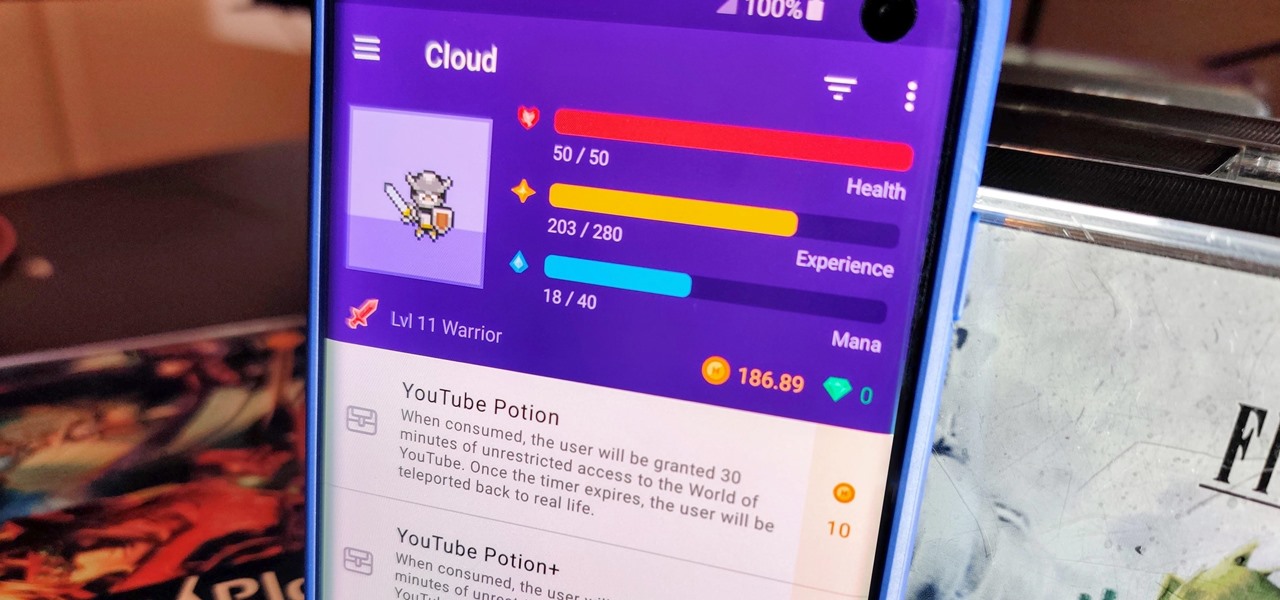
When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

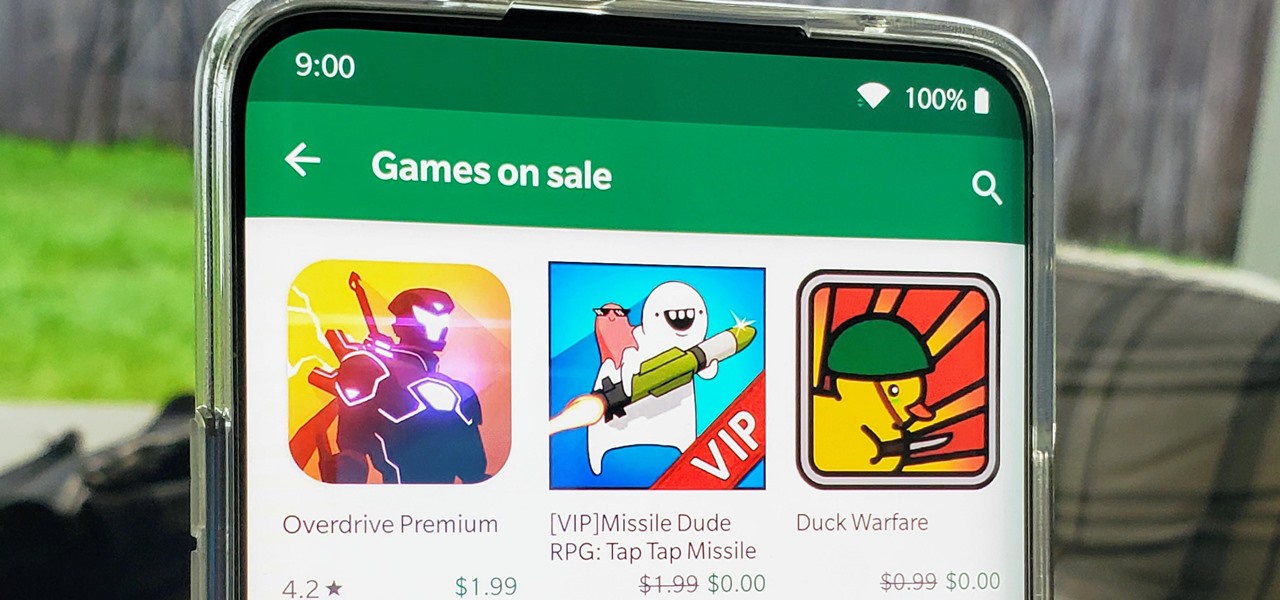
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.