When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Throughout Thursday's virtual Snap Partner Summit, Snapchat's parent company made a profound statement: If you use Snapchat, you're a creator.

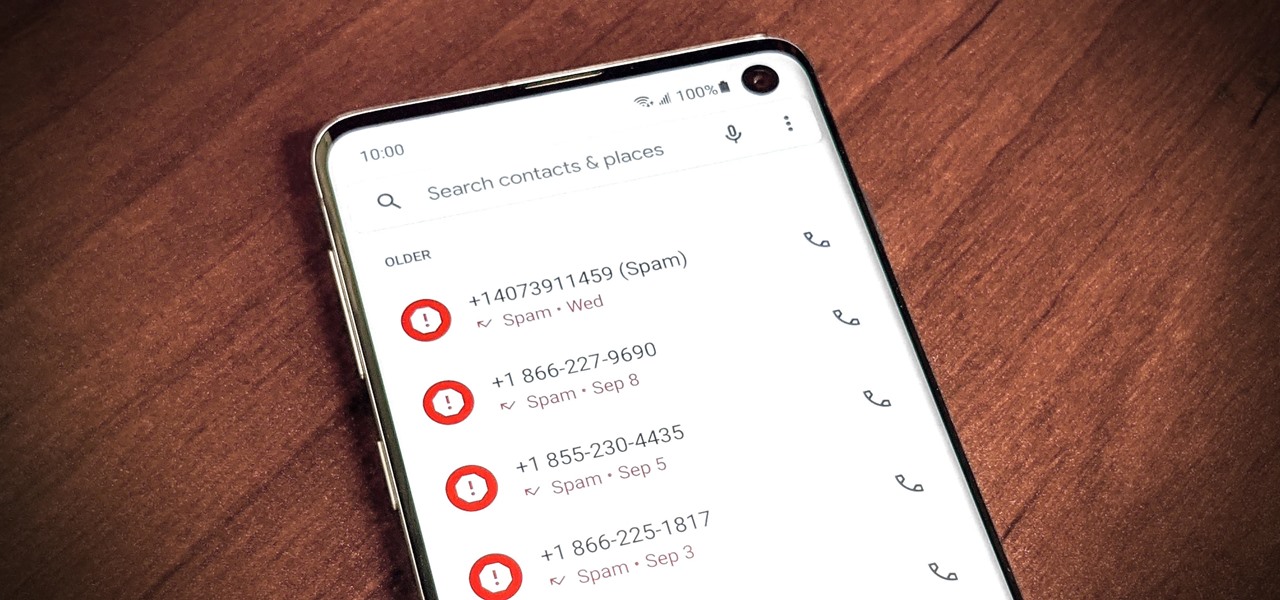
As if telemarketers weren't bad enough, now we have robocalls and spoofed numbers to deal with. Many of us get a least one spam call per day, if not much more than that. Google's Phone app has always been great at managing these calls, but it's been exclusive to their Pixel phones — until recently, that is.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

Buckle up, iPhone users, because it's update time! Apple just released its latest iPhone OS to the public, iOS 14.4. This new edition isn't the company's most ground-breaking, but it doesn't come up short, either — you'll find support for smaller QR codes in Camera, a new "Device Type" setting in Bluetooth, support for a new Apple Watch face, and a major privacy feature, among other new changes.

Apple has finally seeded the release candidate for iOS 14.4 to iPhone developers and public beta users, build 18D52. The update adds scanning support for smaller QR codes in Camera, the ability to classify Bluetooth devices to improve audio notifications, and alerts on the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max for if the camera is detected not to be genuine. There's also a short list of bug fixes.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

Android 12 comes with new features and upgrades that any mobile gamer can appreciate, including Instant Play, which lets you play games instantly without downloading them first. Even better, there's Game Dashboard, which adds shortcuts for screenshots, screen recordings, and more in whatever game you play. The only problems are that it's not enabled by default, and it's a little hard to find.

Whether it becomes mandatory or not to show your COVID-19 vaccination card at events, restaurants, bars, hotels, airports, and other public places, it's a good idea to digitize the paper card on your smartphone so that it's always with you. It's also wise to give yourself quick, convenient access to it, so you're not holding up lines while trying to locate the file, and there are a few ways to do that on your iPhone.

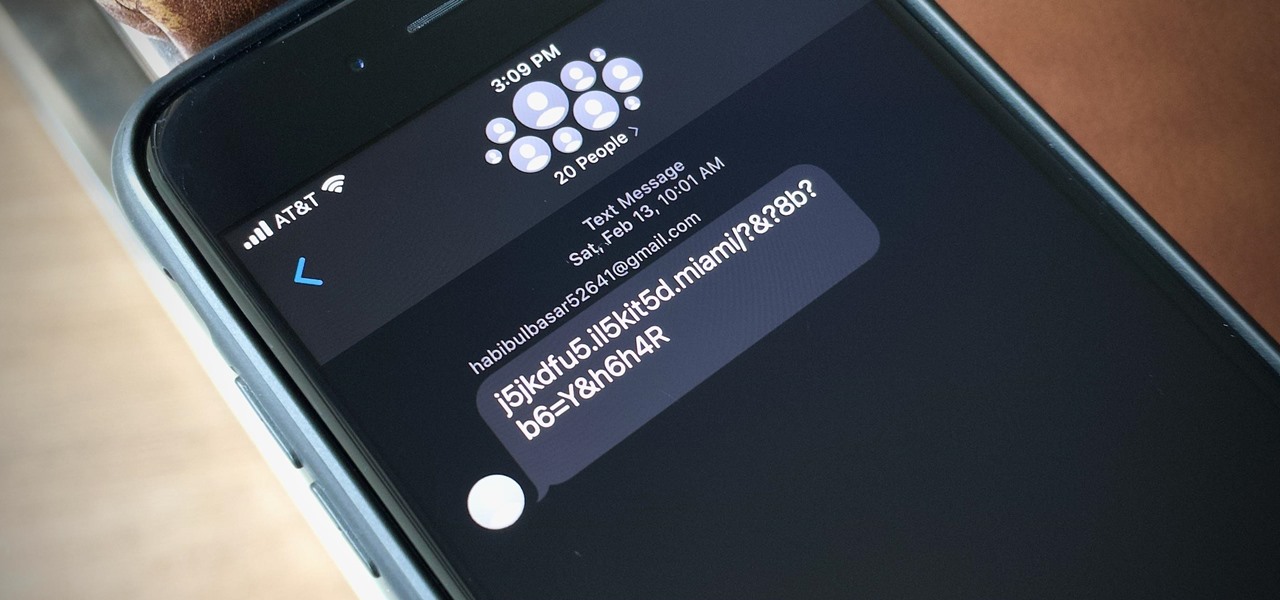
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Most packages sent to you via delivery services include a tracking number that allows you to track it from the creation of the shipping label all the way to your doorstep. The U.S. Postal Service includes tracking information with many of its mailing services, but not for first-class mail or periodicals. Luckily, there's a workaround to that limitation that you can set up pretty quickly.

One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

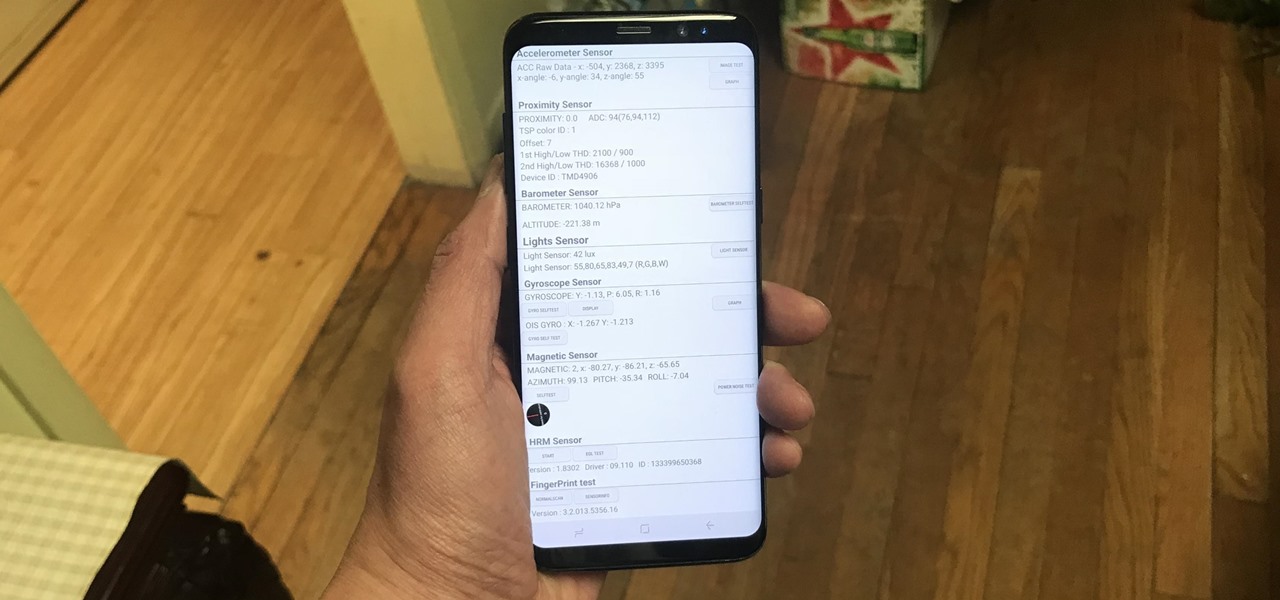
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

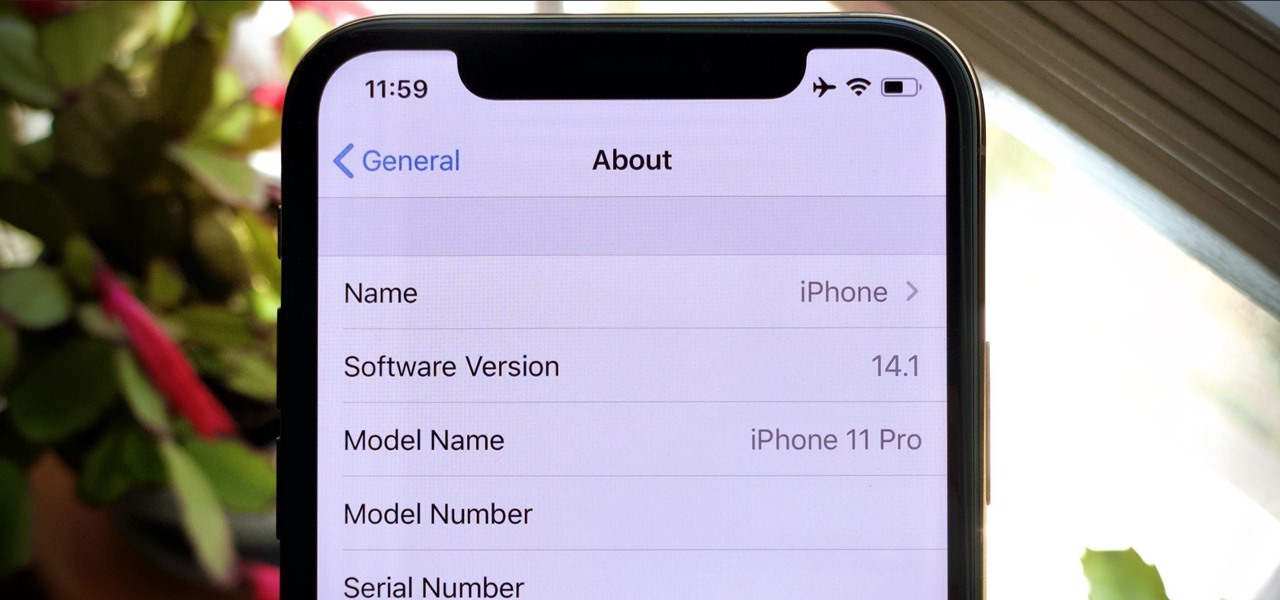
Apple's iOS 14.0 update has come and gone, and now we're sitting on iOS 14.2, the latest version of the iPhone's operating system. While it may be too late for you to revert to the last iOS 13 version, if the iOS 14.2 firmware is giving you problems or you're not just digging it, you can downgrade to iOS 14.1.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

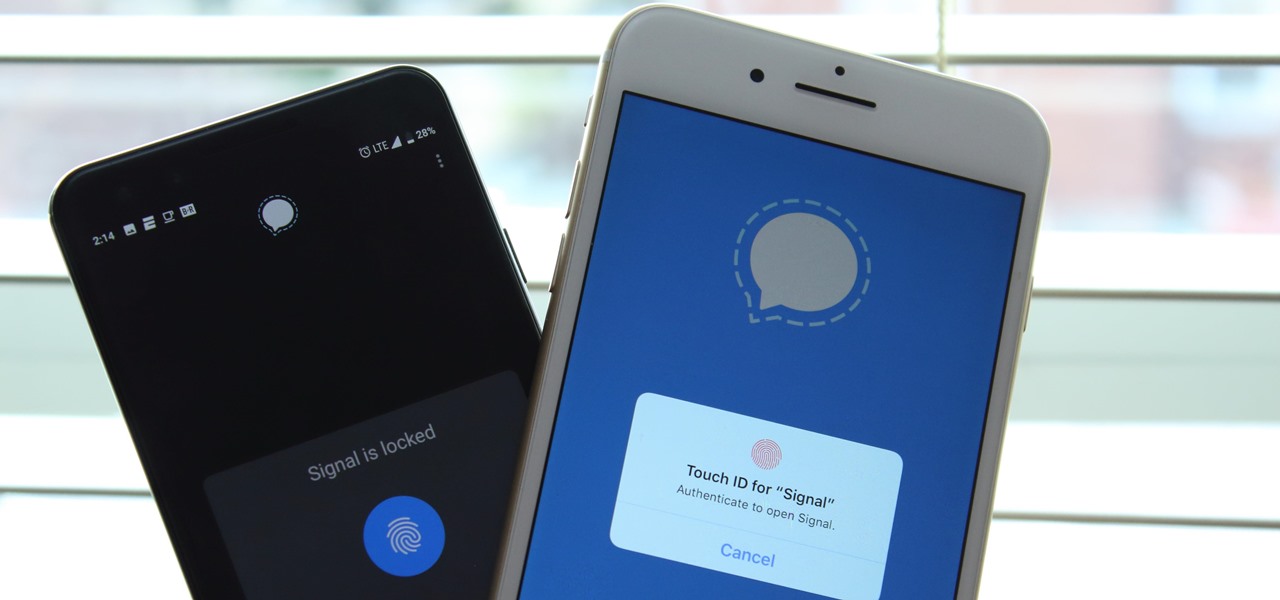
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

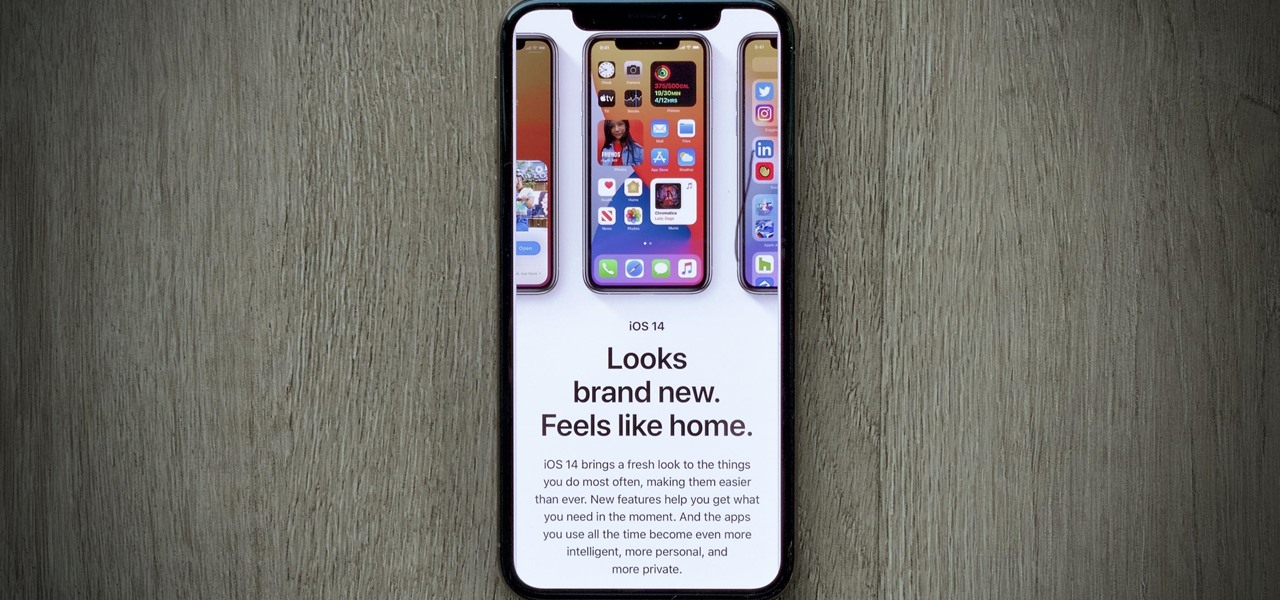
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update.