With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.
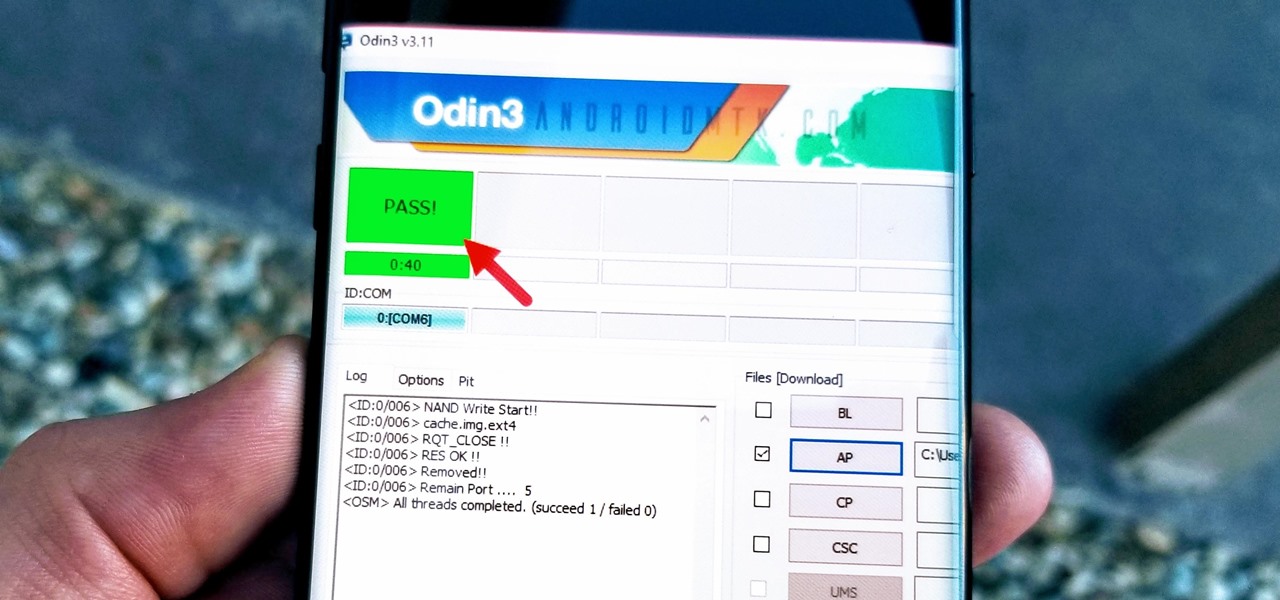
With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.
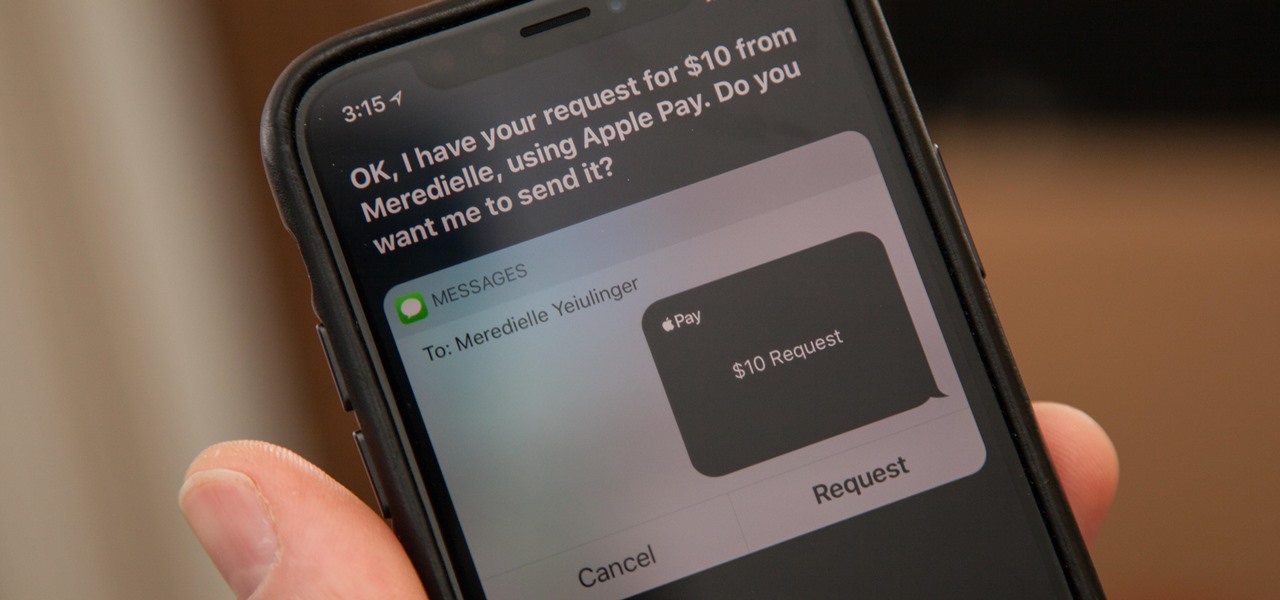
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

So you're thinking about downloading the Galaxy S8 Oreo beta, but you're not sure if it's stable enough to use. It is a beta, of course, so you might want to wait for others to give it a try. Over the past ten days I've used the Galaxy S8+ running Android Oreo as my daily driver, running down the best new features. Let's take a look at the bugs, the performance, and the battery life.

Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Most Android launchers limit you to three choices: Icons, widgets, and folders. It's better than nothing, but it's still pretty hard to find the best look without overcrowding your home screen. You could fill everything up with icons, but then you'd have an iPhone. You could toss everything into folders, but that would always require an extra tap. You could mix in some widgets, but that would take up valuable space. So what do you do? Action Launcher has the answer.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

We're all looking to meet someone, and in this day and age the easiest way to do that is through one of the various dating apps out there. But we can all admit it can get disheartening swiping through all of those people for the frustration of someone not answering your messages after matching. The fact is, we could be missing out on great people just because they don't have time in their busy lives to answer their dating apps every day. Not to mention the fact that we as a society are becomi...

I haven't bought into Apple Pay just yet, but I do love the idea of having quick access to passes like loyalty programs, boarding passes, and my Starbucks card. However, for some users, it's impossible to open these passes stored in Apple Wallet on the iPhone's lock screen. While it's not totally obvious, or even ideal, there is a way to get those Wallet passes back on your lock screen in iOS 9 or iOS 10.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.

The Autobots and Decepticons are back as Transformers: Forged to Fight has soft-launched for both iOS and Android. Help Optimus Prime fight corrupted Transformers one on one to save them from their ruthless overlords, and have them join your cause, regardless of which side they're on. Collect, control, and level up unique robots from the entire Transformers universe, including the classic TV animated series, movies, comics, and toys.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

If you really want to play Gran Turismo or Castlevania on the go, Sony's PlayStation Portable is a great way to do it. But it gets harder and harder to justify carrying around a PSP handheld gaming console when you've got an equally powerful Android phone in your pocket already. The PSP had a good 10 years before being discontinued, and your Android can pick up the slack now.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

As iOS 10 makes its worldwide debut, many users are noticing that the promised iMessage effects feature in Messages is not working properly. Instead of seeing the actual effects, messages will come through like normal, but with text describing the effect they were sent with. On top of that, you can't send your own message effects if you're one of the affected users.

We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgraded your firmware to keep jailbreak compatibility.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step in with a Tasker alternative.

Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Microsoft did a wonderful thing in 2015: for the first time, it was offering a free upgrade to Windows 10 for all current Windows 7 and 8.1 users. And, if you were lucky, the upgrade process was relatively simple and painless. There were, however, some questions after the everything was said and done.

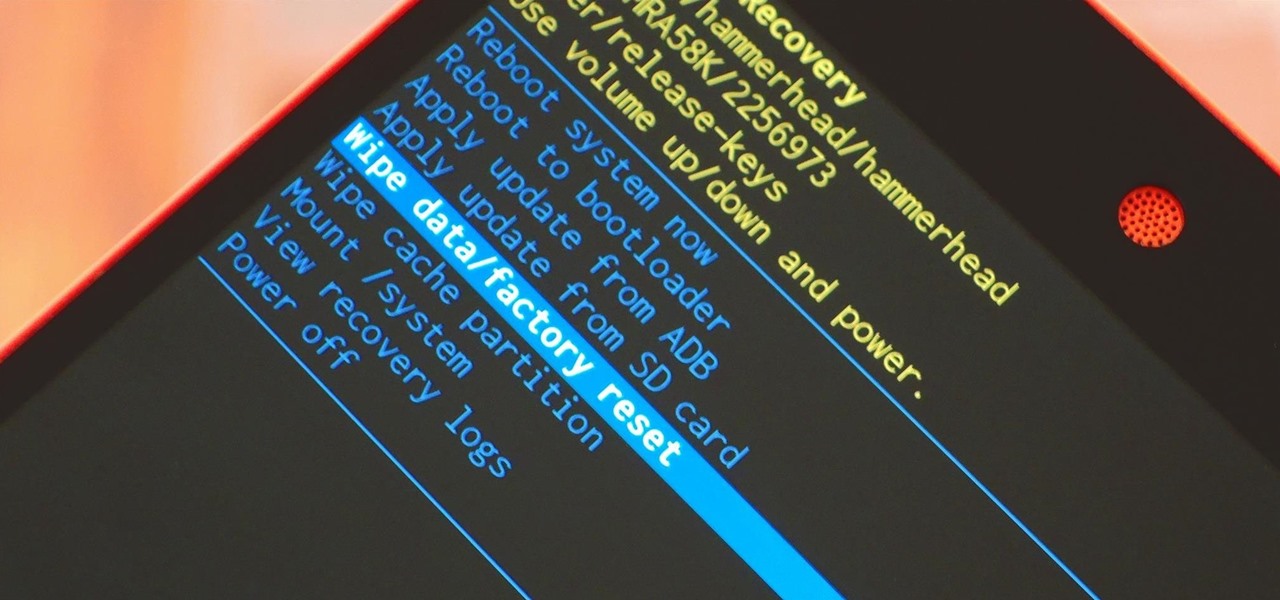
When it comes time to sell your smartphone or trade it in for your annual upgrade, you'll have to make sure that all of the sensitive data the device accumulated while you owned it is properly erased so that no one else can access it. This process is referred to as a "Factory Reset," and regardless of if you own an iPhone or Android device, like a Samsung Galaxy model, HTC One, or Nexus, I'll show you how to do it below.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right call.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.