Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

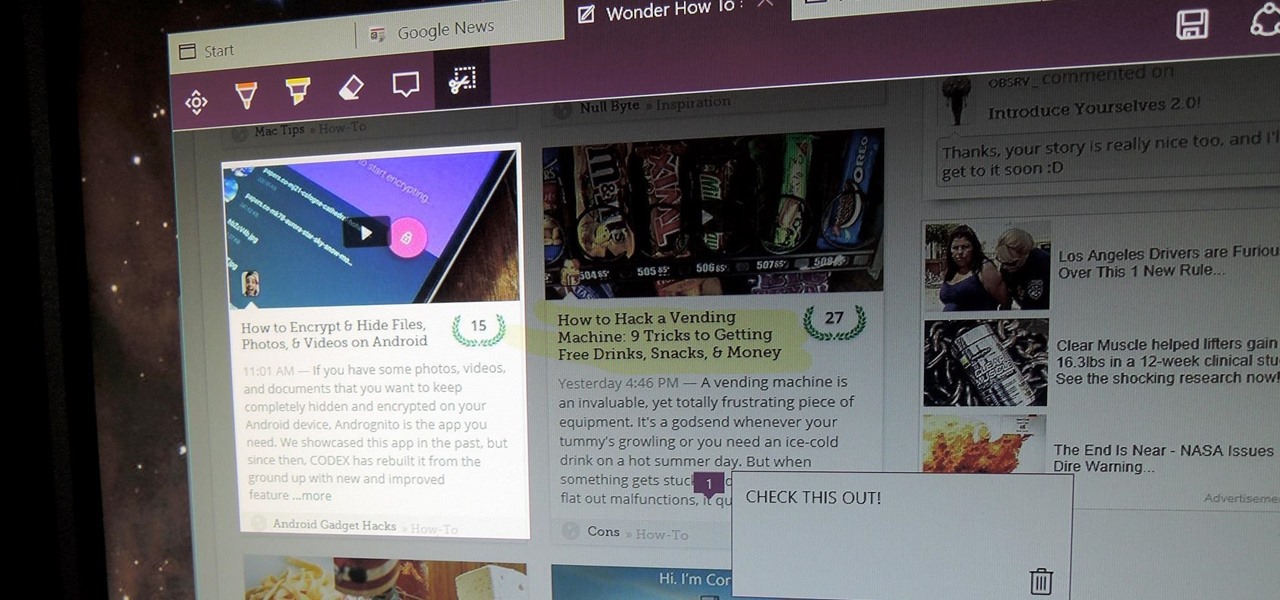
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

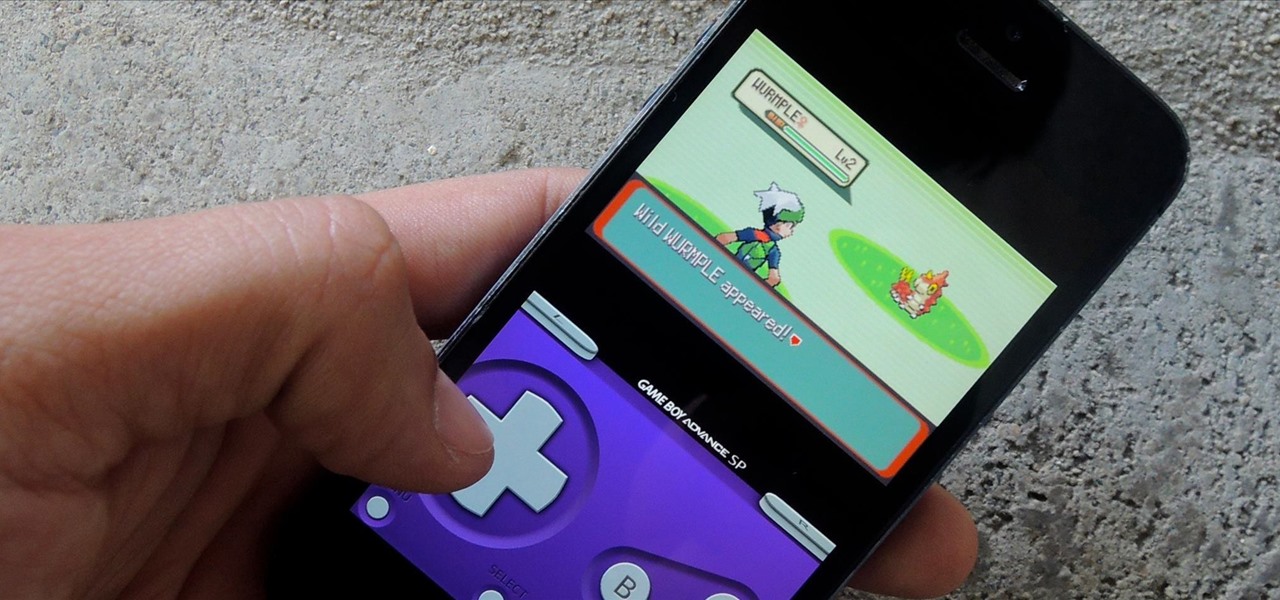
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

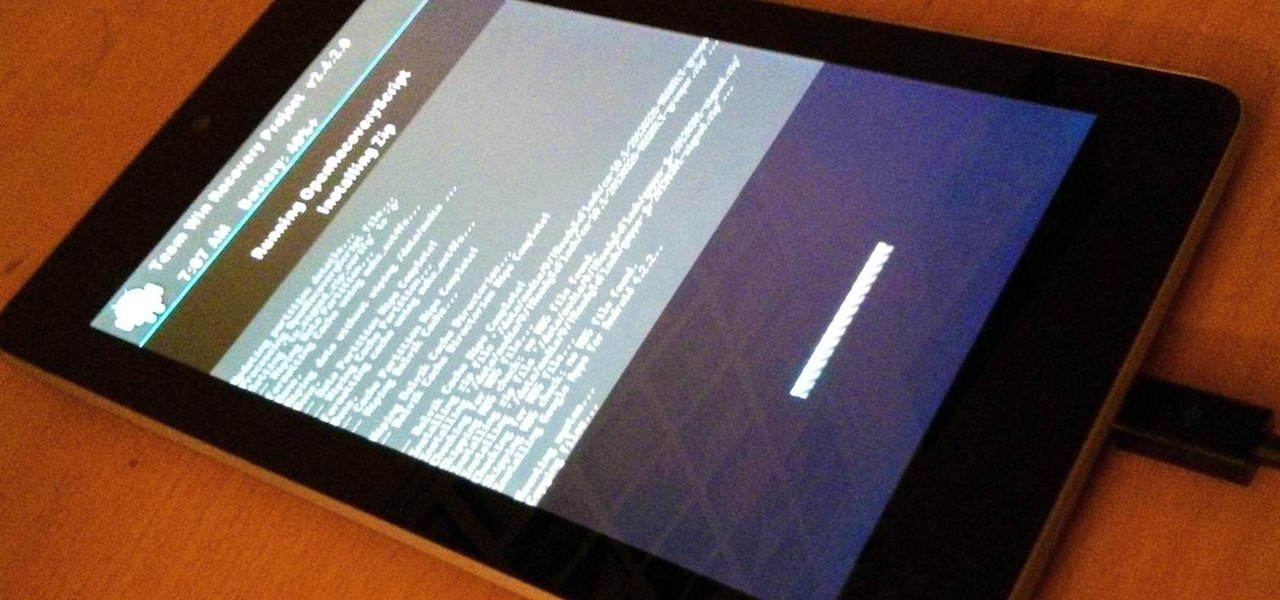
Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Other than sticking your crayon drawings onto your refrigerator door, magnets have a variety of unexpected and sometimes surprisingly practical uses, ranging from keeping your chip bags sealed to creating weird patterns on your nail beds using magnetic nail polish.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

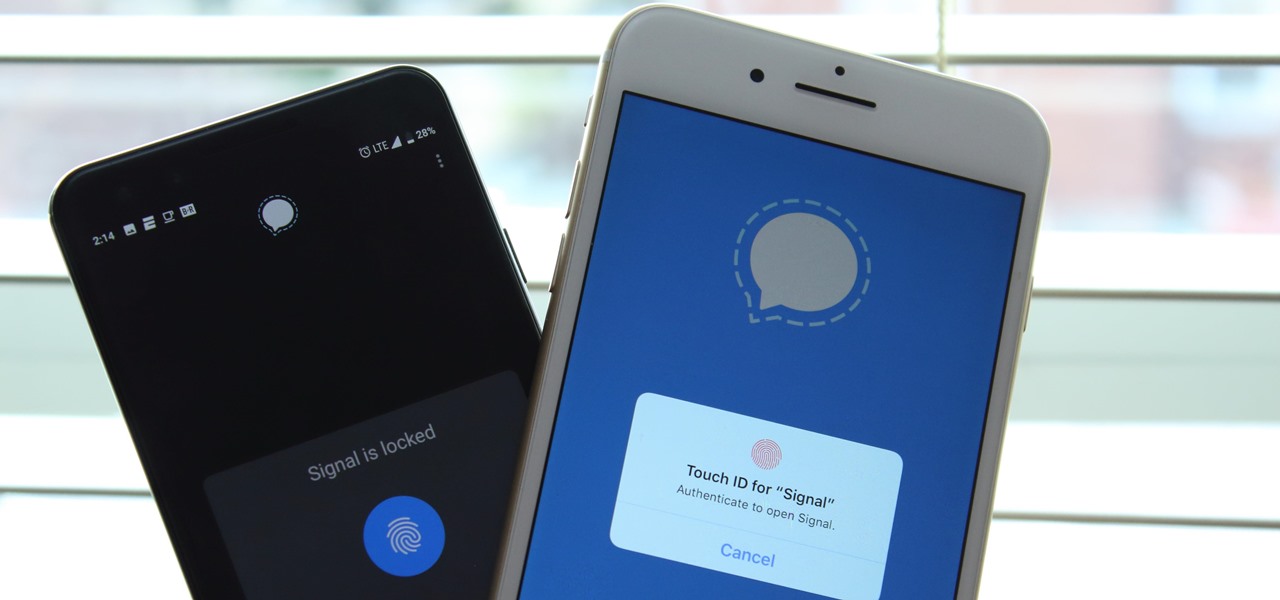
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.

Your phone tracks your every move to some extent, and I'm not just talking about Google services. Smartphone manufacturers use telemetry services that run in the background to track how you use the device, mostly for ads or to improve their future products. You don't usually have a say in the matter, but if you have a rooted OnePlus, there's a way you can take control over it.

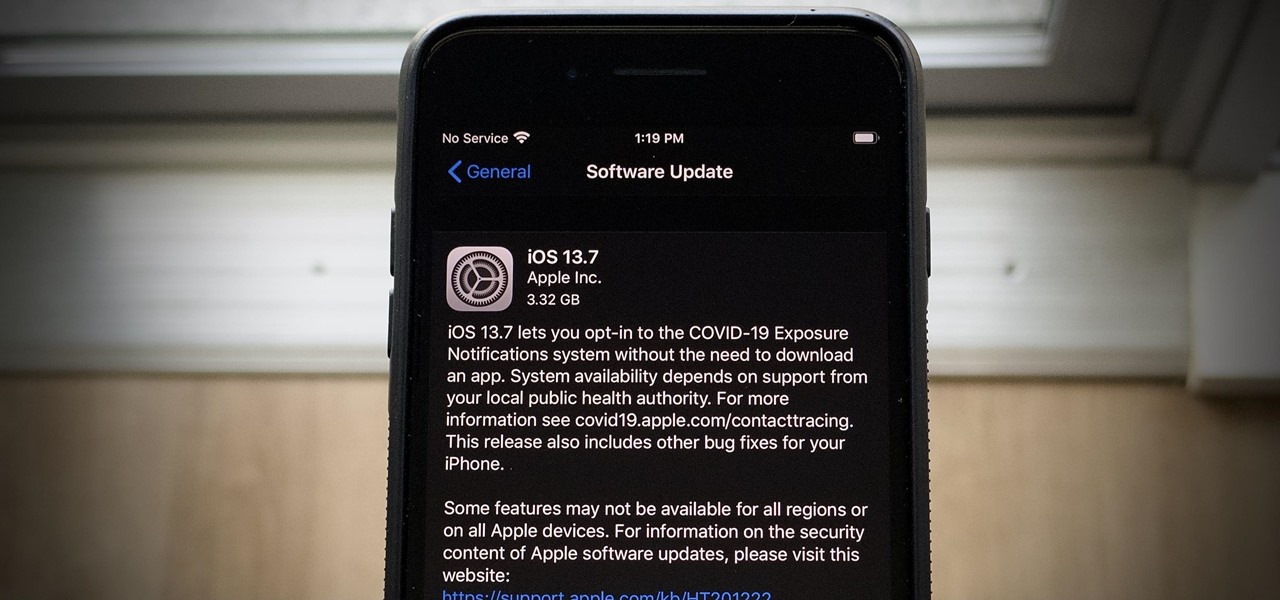
The iOS 14 beta may be picking up steam, but the iOS 13 beta program isn't out for the count. With the release of the iOS 13.7 beta, build 17H33, Apple has included API changes for the COVID-19 Exposure Notifications setting. The update makes it possible for public health authorities to let iPhone users get coronavirus exposure alerts without installing their state's app.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.