There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

I remember the first time I used coconut oil; the whole kitchen was filled with a fragrant aroma that reminded me of the tropics. After learning it was a healthier alternative to traditional cooking oil—not to mention a great source of the good-for-you saturated fat—I was hooked.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

The first time I encountered a deviled egg, the name freaked me out. Why was it called a deviled egg? Was it the spawn of some demonic chicken? If I ate it, would my soul be at risk?

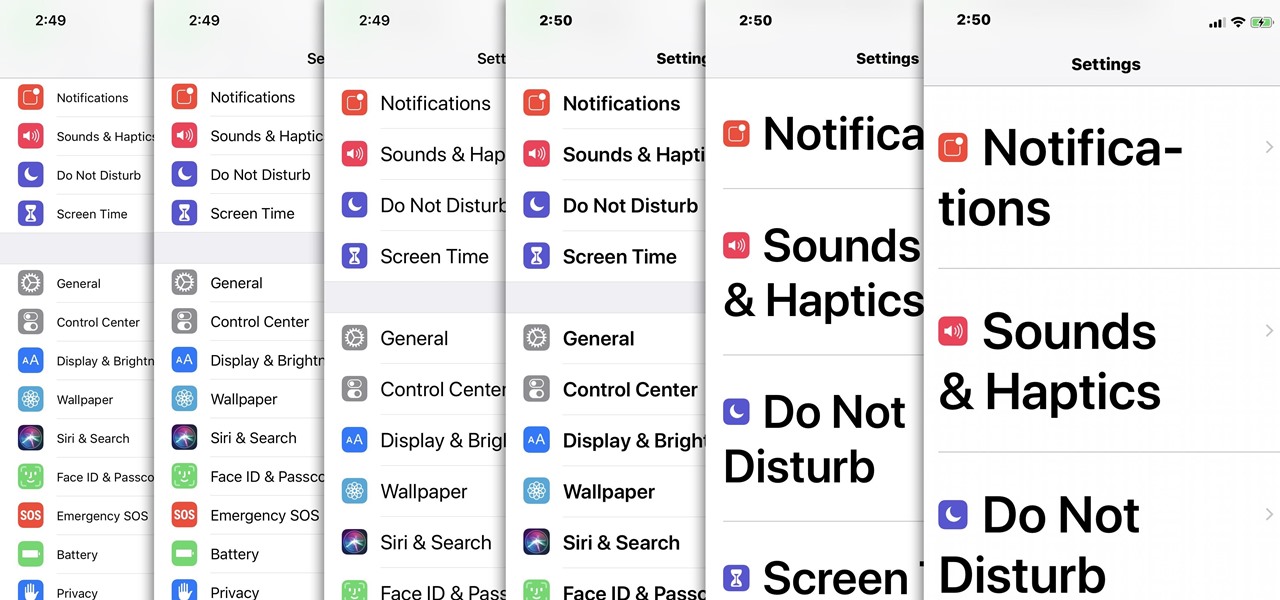
With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

For most people, the font that Apple uses in iOS is just perfect, but some of you may think it's too big while others with poor vision may have a hard time reading it. Whether you're having a hard time seeing text on your iPhone or just want something different, there are actually three things you can do to adjust how text is viewed.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

Regardless of your culture or your age, eating with your hands is fun. Flouting social convention and just digging in with your fingers provides a whole other level of epicurean enjoyment. And one of the most entertaining hands-on foods is monkey bread. Food historian Tori Avey provides a comprehensive history of the origins of this pull-apart treat, including the important detail that no actual monkeys are involved in the making of monkey bread. Originally a savory culinary creation from Sou...

We've all been there before. Preheated the oven, popped in the cake, and then became distracted by this, that, or the other... until we either smelled burning or had the smoke detector pierce our eardrums.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

In my opinion, spices are the key to a successful kitchen. With a healthy array of spices and spice mixes, you have the foundation for nearly any dish that you want to make; the culinary world is your oyster. With a depleted cupboard of spices, however, nearly every recipe looks intimidating and unattainable.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

Single-serve yogurt cartons are so much fun. They're delicious, convenient, and the perfect size; no wonder it's so fun to open a new container of yogurt every morning. Yet as awesome as single-serve yogurt cartons are, there's something you really need to do: stop buying them!

Catching up with Windows 8, Apple has finally included a way in Mac OS X to use two apps side by side in full screen view. In the 10.11 El Capitan update, it's called Split View, and it works fairly well for the most part. It's not quite as intuitive as it should be, but easy enough once you get the hang of it.

In the realm of Android mods, none is more powerful than a custom recovery. This is installed in place of the stock offering, and it lets you back up your entire system, flash mods, and install custom ROMs.

HTC's Sense UI is generally regarded as one of the best manufacturer-skinned versions of Android. This is mainly due to the subtle and classy styling of the interface, as well as some unique features that are added in here and there.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Among the many gifts that Italy has bestowed upon the world, culinary and otherwise, pesto stands alone. The exact birthplace of pesto, that herby sauce made of pine nuts and olive oil, is an area of Italy called Liguria, whose microclimate is particularly kind to basil, one of pesto's key ingredients.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Christmas is just around the corner, which means holiday wreaths are decorating many doors across the nation. While we're always fans of a practical DIY, we especially love the edible kind, which are great for last-minute decorations.

Tagine is both the name of a cooking vessel and also the dish that is cooked within it. In fact, some might say tagines are the national dish of Morocco. These slow-cooked stews and braises, often combining meat, vegetables, spices, and dried fruits, have a character unlike anything I've ever eaten.

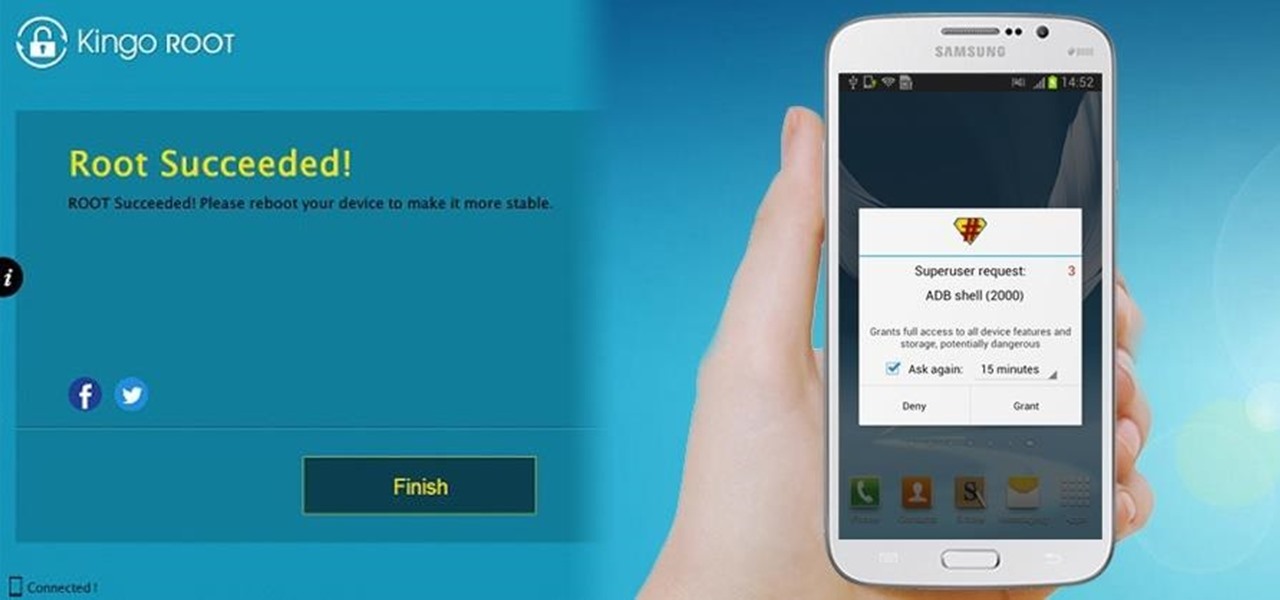
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

The new Nexus 6 and Nexus 9 models will be shipping with Android 5.0 Lollipop preinstalled, and the Nexus 4, 5, 7, and 10 will be getting the new OS update from Google very soon. But where does that leave the rest of us?

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.