Rooting has a long and storied history in the Android community. As OEMs push out more refined software, the need to root has diminished — still, the number of incredible things you can do with a rooted phone is enough to tempt many enthusiasts. Luckily, some manufacturers are still putting out root-friendly devices.

Whether inappropriate or unimportant, some emails don't need to be viewed at a certain times of the day. For example, you might not want to see any personal emails during work hours. By default, Gmail will notify you of all emails that hit your inbox, but fortunately, there's a feature that can automatically hide certain emails and prevent distracting notifications.

While Black Friday shoppers found countless deals on all kinds of smartphones, one device was overtly left out of the price cuts — the iPhone X. Walmart was the only store to offer a promotion on the newest Apple device, and even then, it was difficult to find. Cyber Week appears to have repeated recent history, with only one store offering a special on the iPhone X, but it's not Walmart this time.

The first wave of iPhone X preorders, the ones with a delivery date of Nov. 3, sold out in ten minutes. You can still preorder one and skip the lines next week at Apple Stores across the country, but if you want that bezel-less beauty in your hands ASAP, brick and mortar might be the way to go.

Now that the cutting-edge iPhone X is up for preorder, everyone is excited to see how the new device will compare to offerings from Apple's competitors. Namely the Galaxy Note 8, which is a beast of a phone in its own right.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

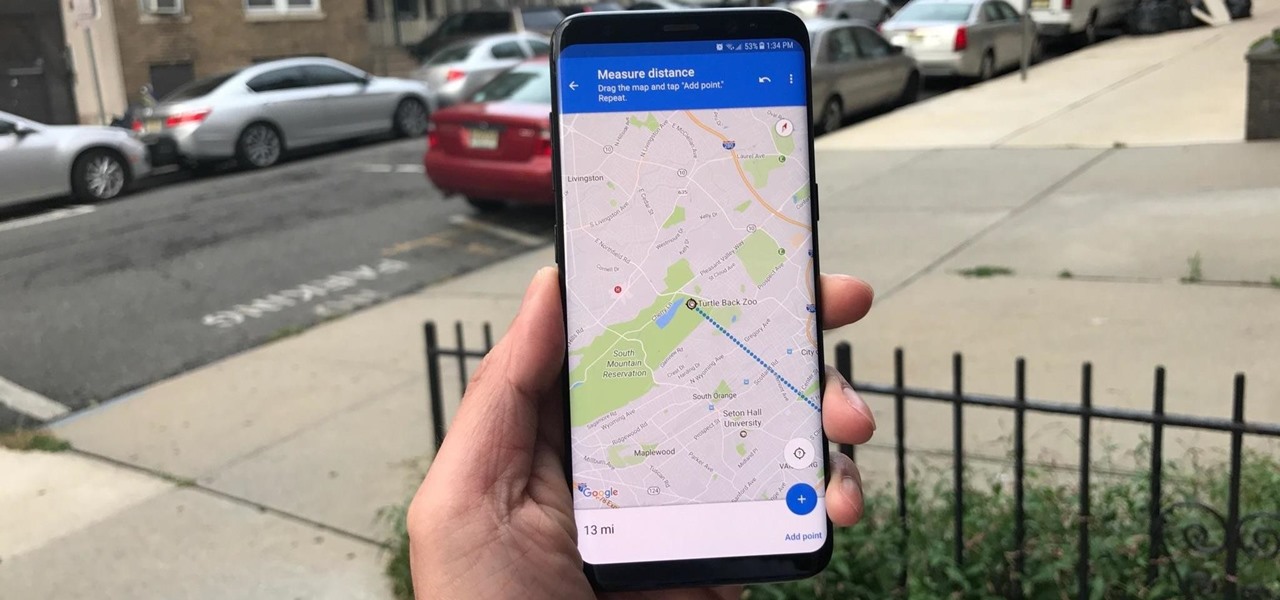
If you want to find out the linear distance between your hotel and a landmark or restaurant you want to visit, Google Maps has a great feature that lets you quickly measure the distance between two or more points. It's perfect for getting an idea of how far places are in relation to each other, which can help you plan trips more efficiently.

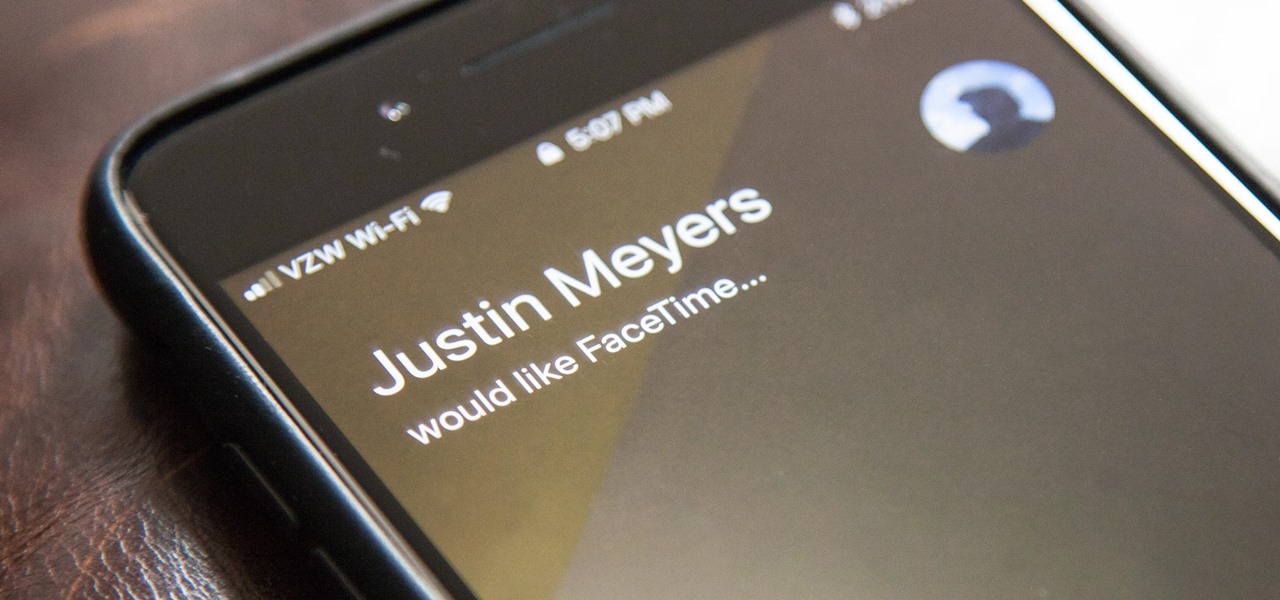
Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

I wanted to post a Live Photo to Instagram of me in front of that donut that got eaten next to the CVS on Houston St. in New York, between Mott and Mulberry. The only problem is that Live Photos aren't supported on Instagram, so I couldn't just tap and post it to my feed without it becoming a regular still image. Luckily, there is an awesome workaround.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

In this episode of Have You Seen This?, we will look at Oriental Museum by 247 Technology Limited, a free application in the Windows Store for HoloLens. Museum exhibits seem to be a popular theme amongst the demonstrations going up, so let's see how this one looks.

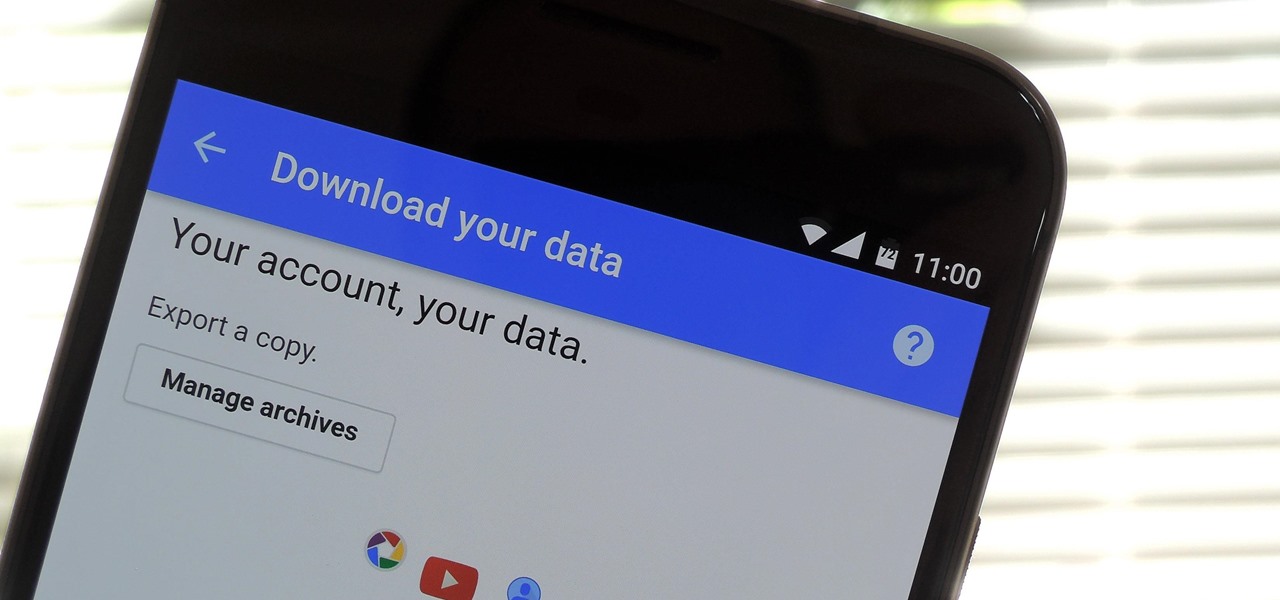
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.

When we talk about augmenting our reality, we often first think about vision instead of our other senses—but there's more to an immersive experience than what you see. One inventor figured out how to utilize sound and touch to create a simple, upgraded version of laser tag that you can play with your smartphone.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

One of our favorite kitchen items, hands down, is a good old-fashioned wooden spoon. It's practical, versatile, and can last for decades if cared for properly. There are specific ways to nurture wooden utensils in order to keep them from cracking and to help them maintain their glossy sheen.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.