Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

OnePlus changed the way we think about high-end phones. Their "Never Settle" motto led me to ditch my high-cost smartphone for their flagship One, which not only packs some pretty impressive hardware, but won't break the bank. Now that OnePlus has made a name for themselves with the One, they're trying their hands at ROMs, too.

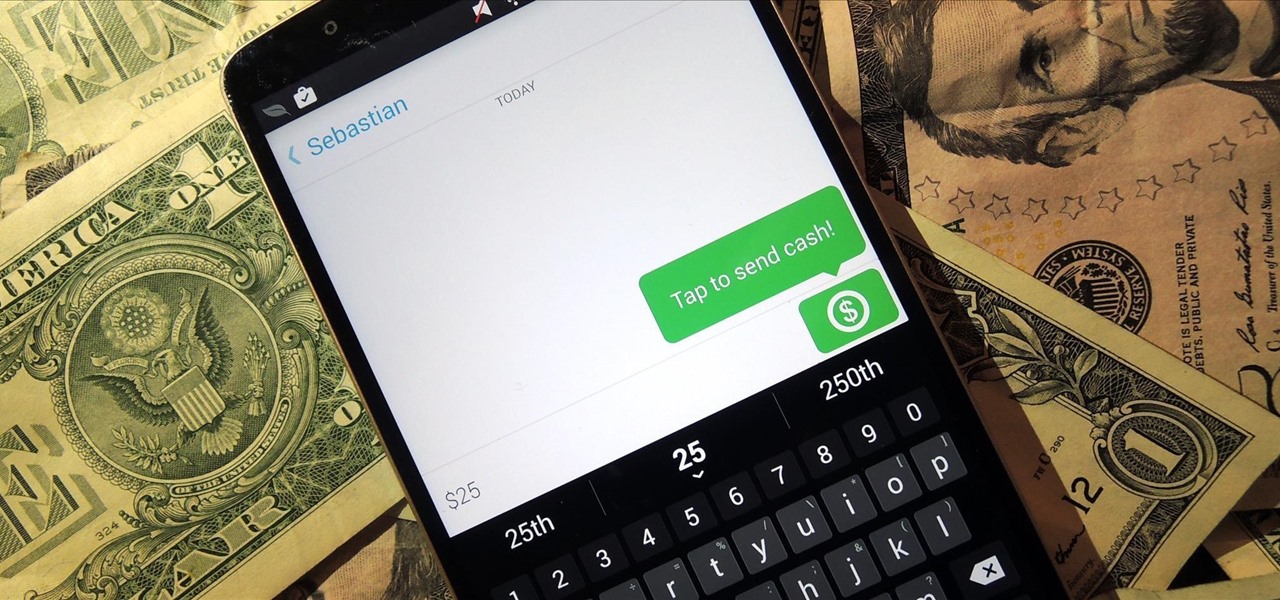
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

If you're breaking a sweat in the summer heat, but not trying to break the bank, this dead simple trick will show you how to make your own air conditioner for under ten bucks.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

Poor alignment of cabinet doors will cause a kitchen to look run-down and may be embarrassing to the homeowner. Luckily, with a single screw driver and a little ambition, the door alignment can look brand new.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

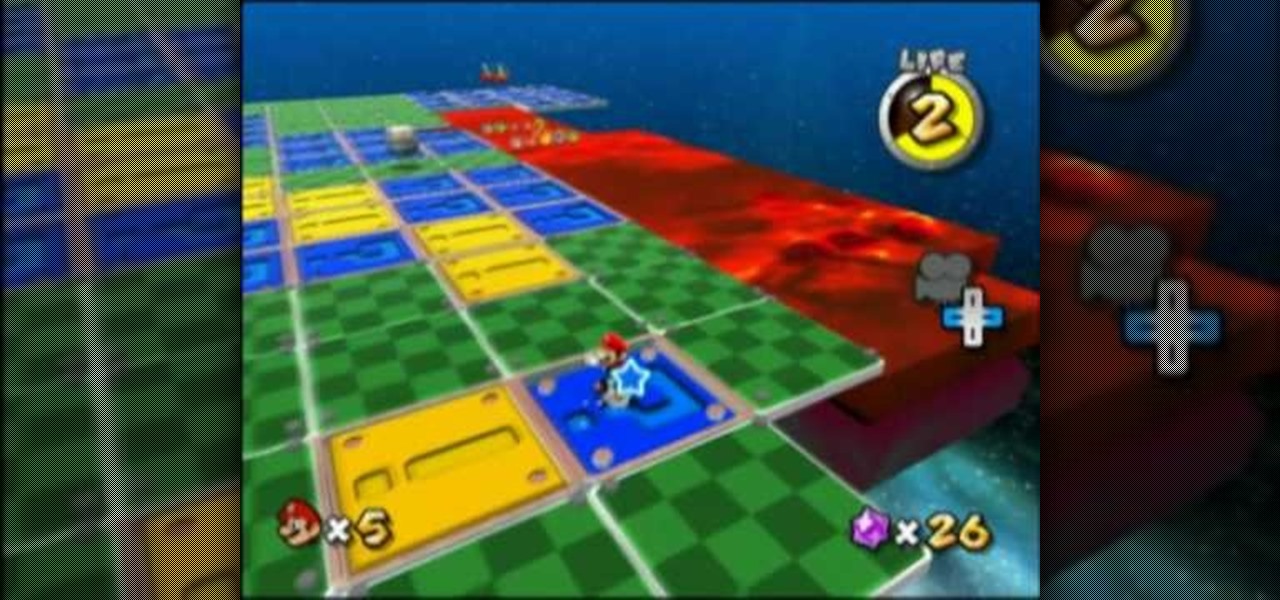
On your mission to collect all 242 stars in Super Mario Galaxy 2 on the Nintendo Wii, this is your last World before moving on to the 120 green stars and bonus stars. World S is the key to get the rest!

You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Horseback riding can be a peaceful outdoor recreation that puts you on the back of a powerful, yet simple creature. Instead of using gas or pushing pedals, you're able to give direction to something while you enjoy the open air. When it comes to horseback riding, there are many things that people need to know. One is how to leave a horse unattended.So, this video demonstrates how to tie your horse to a rail using the safe, easy, quick-release knot known as the "Bank Robber Knot." Enjoy!

In this math lesson you will learn about simple interest and compound interest. Whenever you want to borrow money from a bank, you have to pay interest at a certain percent rate. The main difference between compound and simple interest is the fact that the simple interest is paid only on the principal, while the compound interest is paid on both the principal and the accumulated interest The simple interest is given by the following formula:

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

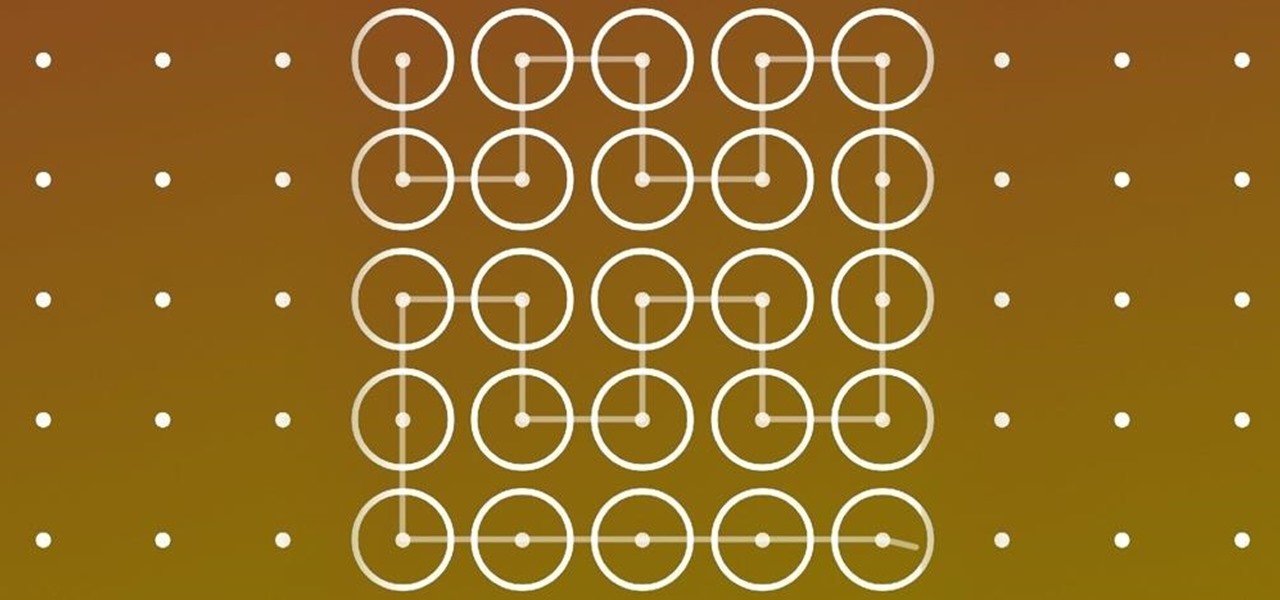
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

Accuracy and skill, not speed wins the game of pool. Learn to use precision in a pool bank shot. It could mean the pool game. This quick little billiards clip will help you succeed as the pool shark you want to be.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

It's a sad fact, but the Galaxy Note 10+ is the only phone in Samsung's 2019 Note 10 lineup to include microSD support. It comes with either 256 GB or 512 GB of storage, but you can more than double that if you slap a memory card in it. So if you're in the market, here are some of your best options.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

The augmented reality space is brutal, and that means shifting directions quickly to meet whatever need the market demands.