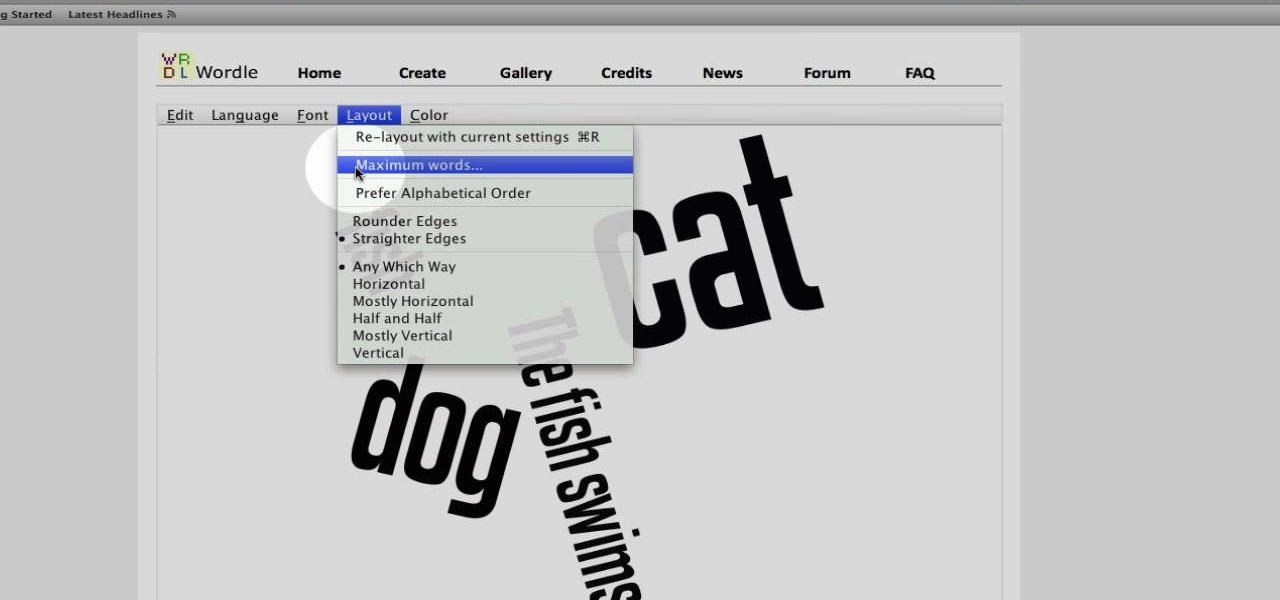
This video tutorial belongs to the Computers & Programming category which is going to show you how to use Wordle to create word clouds. Go to Wordle and click on the 'create your own' link. In the first box, type in your text, and in the second box enter the URL of any blog, blog feed or any other web page that has an Atom or RSS feed. In the 3rd box enter your del.icio.us username, if you have one. After typing in, hit 'go' and you get your Wordle file with the words written in different sty...
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.
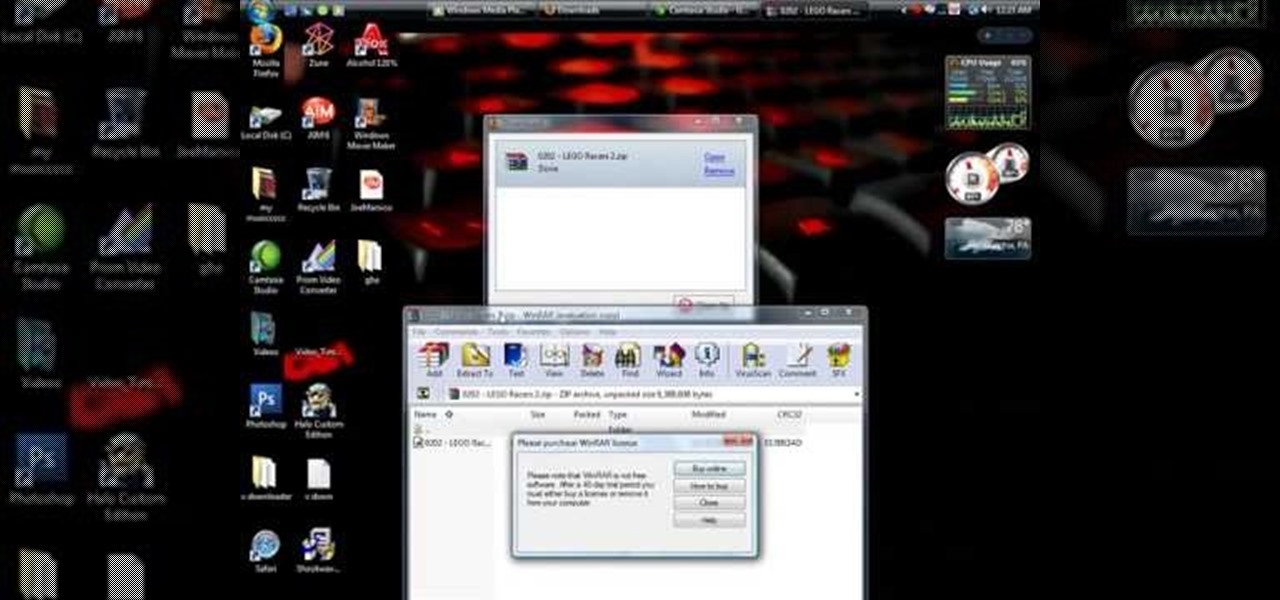
This video tutorial from shrederjoe shows how to easily extract .rar file's content using WinRar application.

In this video tutorial, viewers learn how to rip audio and video from You Tube to an i-Pod or computer. Users will need to download the Free Studio program from located the video description. Once the file is saved, double-click the file and follow the instructions to install the program. Now find a video or audio from You Tube and copy the URL. Now open the program, paste in the URL and download the file. This video will benefit those viewers who enjoy watching or listening to videos on You ...
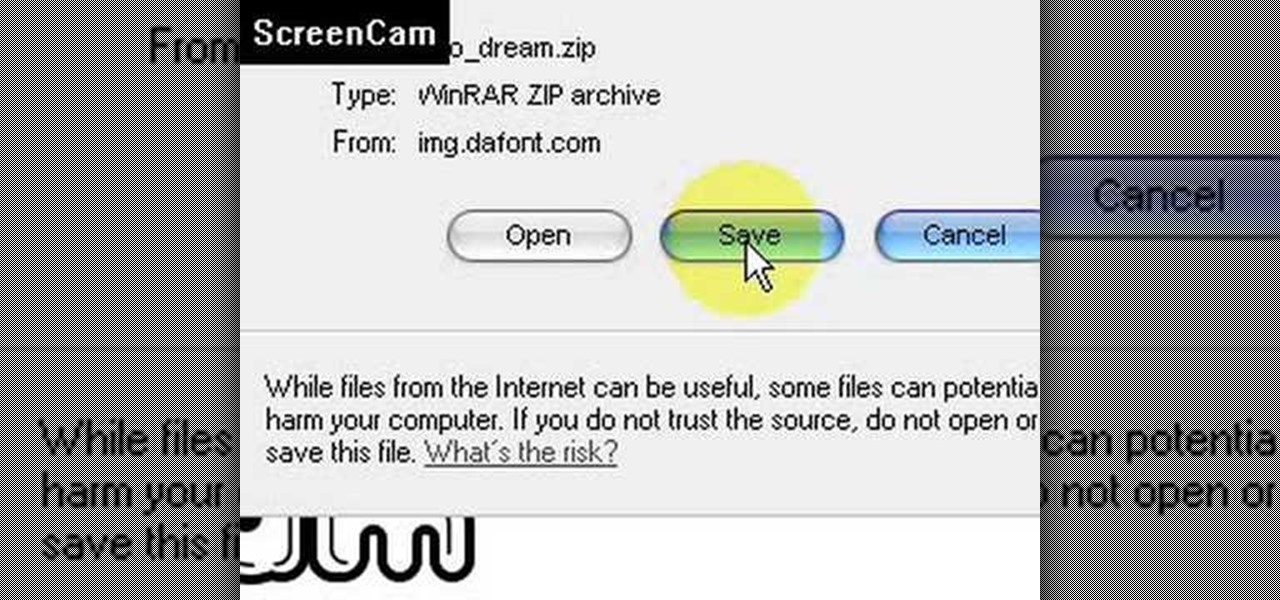
This video is about how to install new fonts in Windows XP. The first step that you will need to do is open your web browser then search for fonts. If you have found the site, just simply click on it. Then the next step is have a browse and look for the font you like. Once you have found the font that suits you best, just simply click the button "download" then save the file in your computer. Once you have saved the file in your computer, simply right-click the file and click on the "extract ...
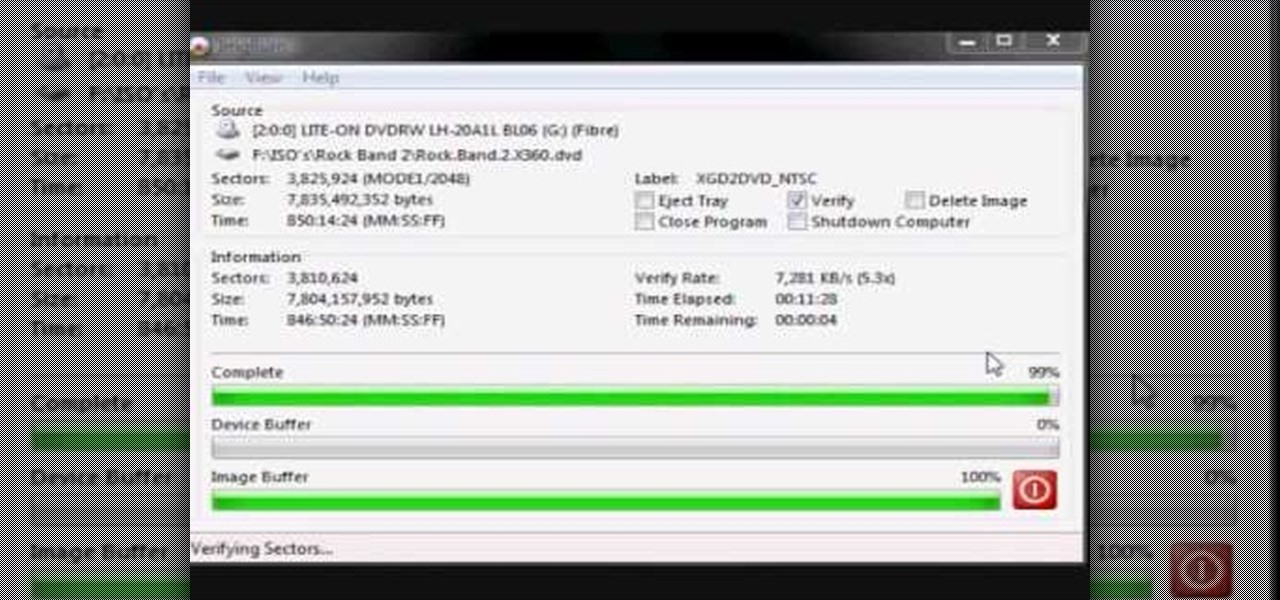
In this how-to video, you will learn how to burn game ISO's for the Xbox 360. It is important that it is only legal to back up the games that you already own. You will need the Image Burn program. Open it and click Write Image File to Disk. Next, click browse for file and look for the .DVD file. Go to tools and settings. Click the Write tab and go to sectors and make sure the number is 1913760. Check the ISO file and open it with notepad to check if the layer break number is also that number....

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

It's easy to find yourself drowning in a pile of papers and nick-nacks if you're not armed with a good organization system. By taking the time to set up a system where everything is condensed and has a place you'll find it much easier to keep it that way.

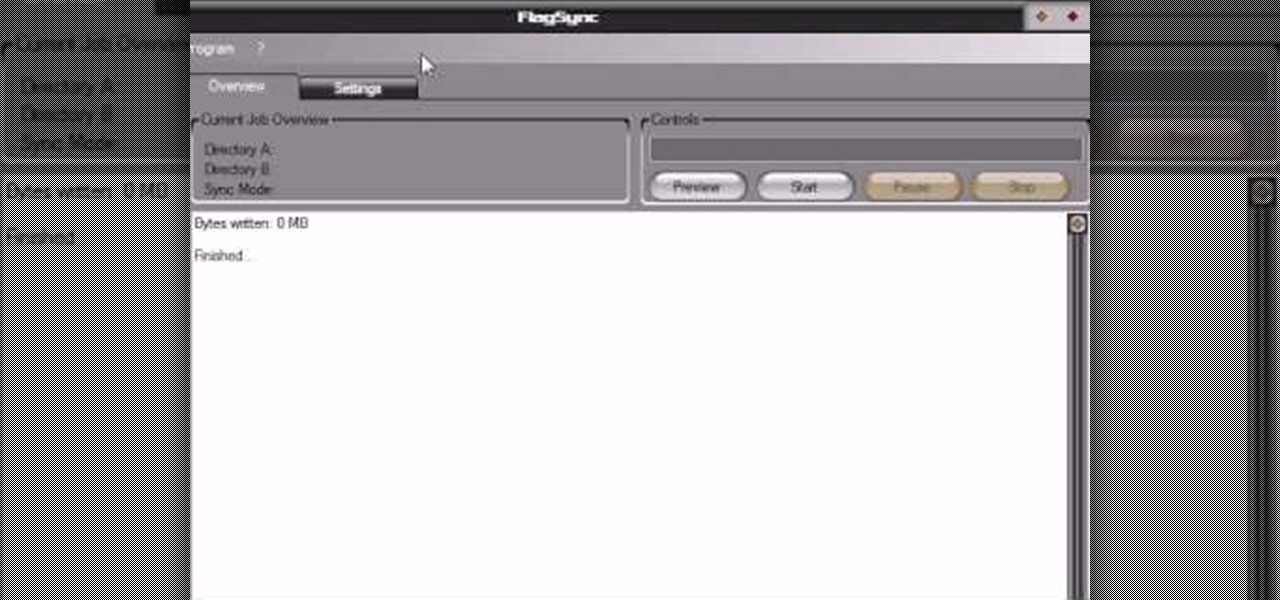
Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud o mount -o loop -t iso9660 and then the name of your image file, followed by CD/. This will create a new disk drive, which can be seen on the desktop. You can explore that disc like a real one. To unmounted your image, s...

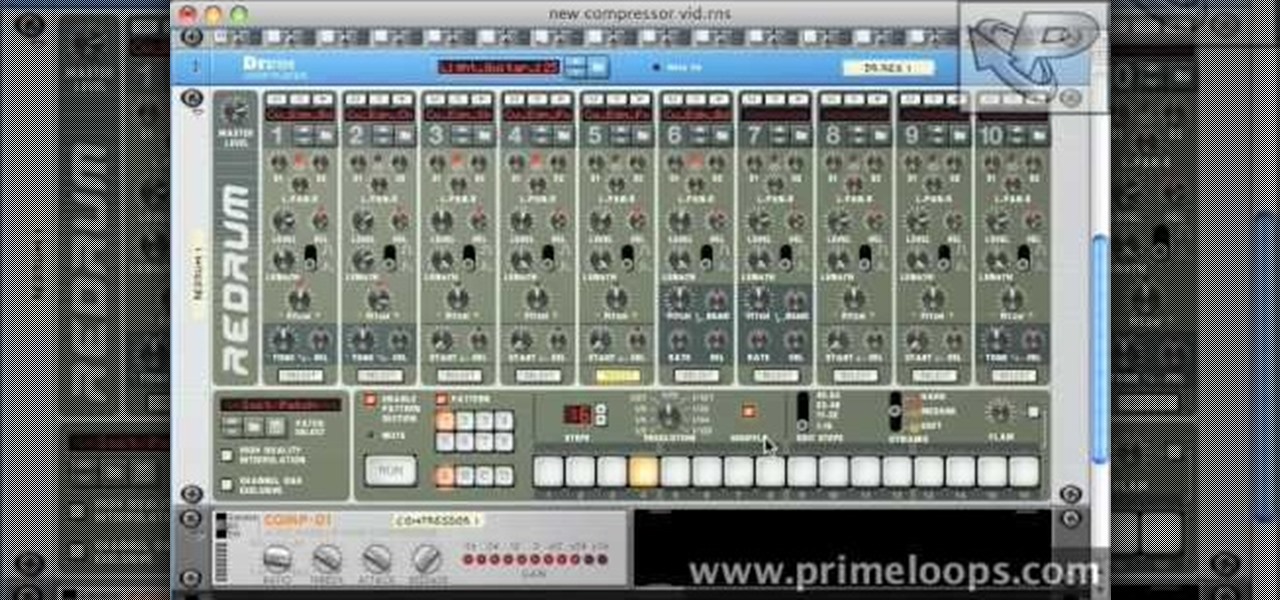
This tutorial video will show you what the purpose of compression is and how compression works through its parameters. Your instructor illustrates a drum beat and a plucked guitar line. Beginning with how to compress the drum beat, take (download) a drum sound pack without compression and to add compression using the software right click on the drum machine, choose create, and then choose combo on compressor. The virtual compressor has all the dials and adjusters found on any basic compressor...

This video teaches the secrets of downloading and using uTorrent in your computer. First download the software from the link shown in the video and open it. Now to download any file search some popular torrent websites. Make sure you select a torrent file with more SEEDS but less LEECHERS and download it. Now open the downloaded torrent, select the required files if there are many and start downloading. After downloading stop the torrent and use the files.

This how-to video is about how to make PS3 controller work on the computer that have either Windows XP, or Vista or 7 as their operating system.

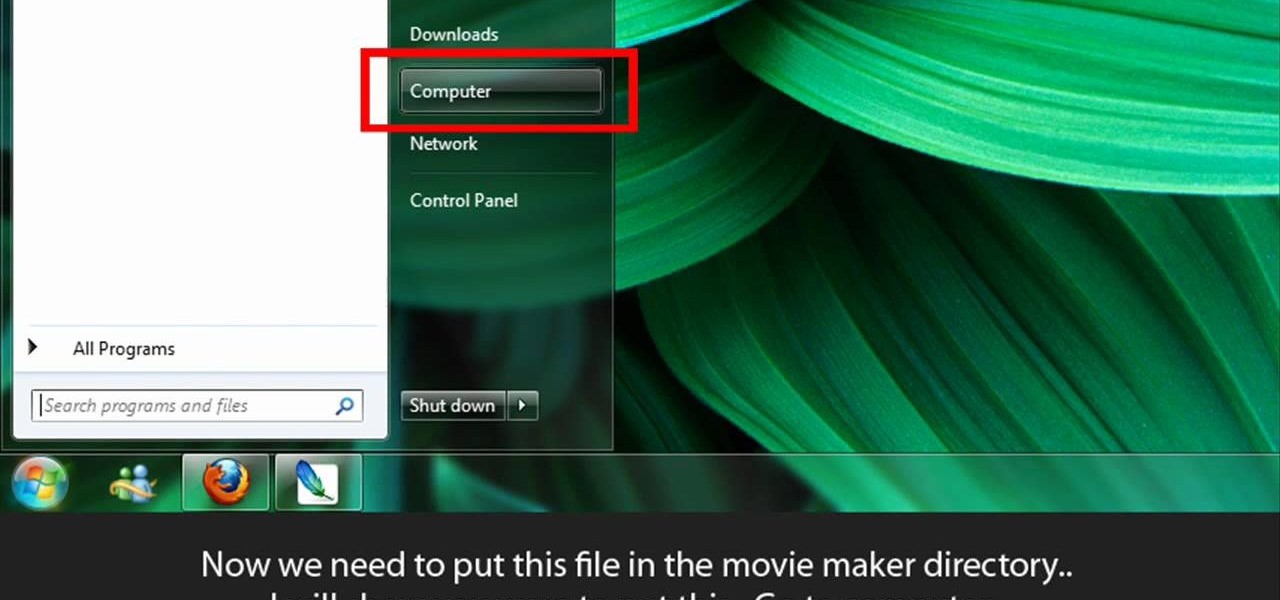
Learn to make HD Video With Windows XP's Movie Maker with this video tutorial. First, go to PapaJohn, there is WMV-HD at the left hand side of the screen. Expand that and click on the Introduction, then 1280*720 link. Download begins, save file on you hard drive. It has to be in the movie maker directory. It is in Program Files - Movie Maker - Shared Link. File must be added in the folder Profiles. Put it there, and if you don`t have such folder, create it. OK, we can start movie maker and ma...

Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.

There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Before you attempt this firmware install, if you have already installed custom firmware on your PSP this measure might brick it. Don't double install if you have already hacked your PSP.

File collaboration is one of the best integration features between Office 2003/Office 2007 and SharePoint. These task panes allow you to access and modify content in a SharePoint site from within Office without having to navigate to the site using your browser. The feature is available in the following Office 2003 and Office 2007 applications: Word, Excel, Microsoft Project, OneNote, PowerPoint, and Visio.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

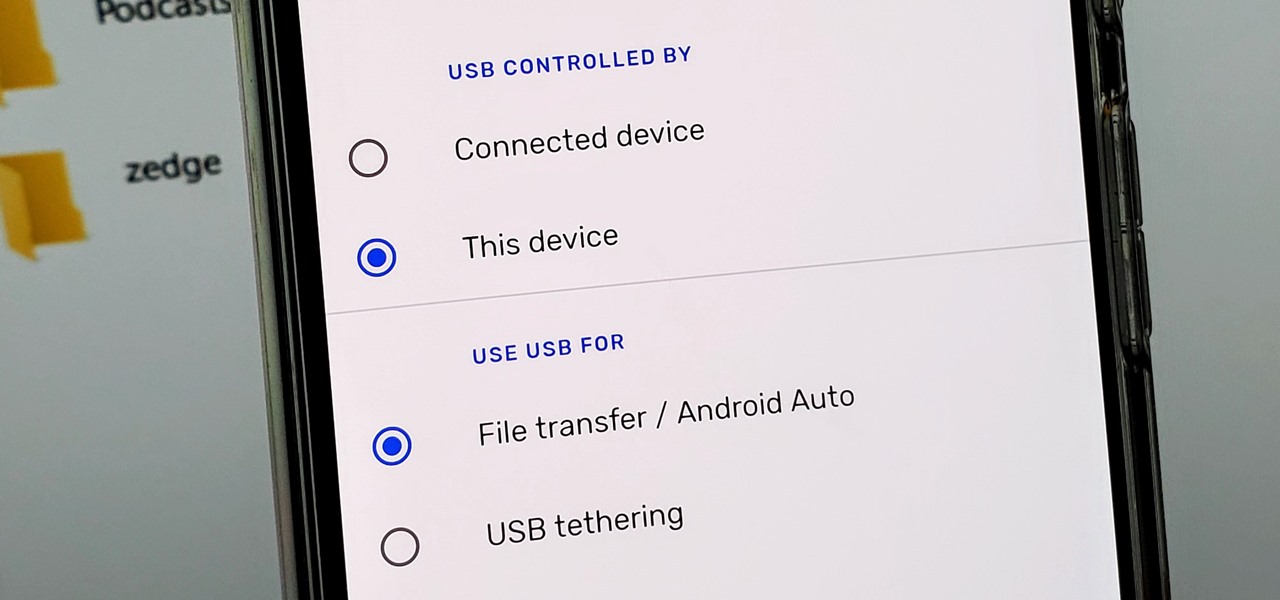
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

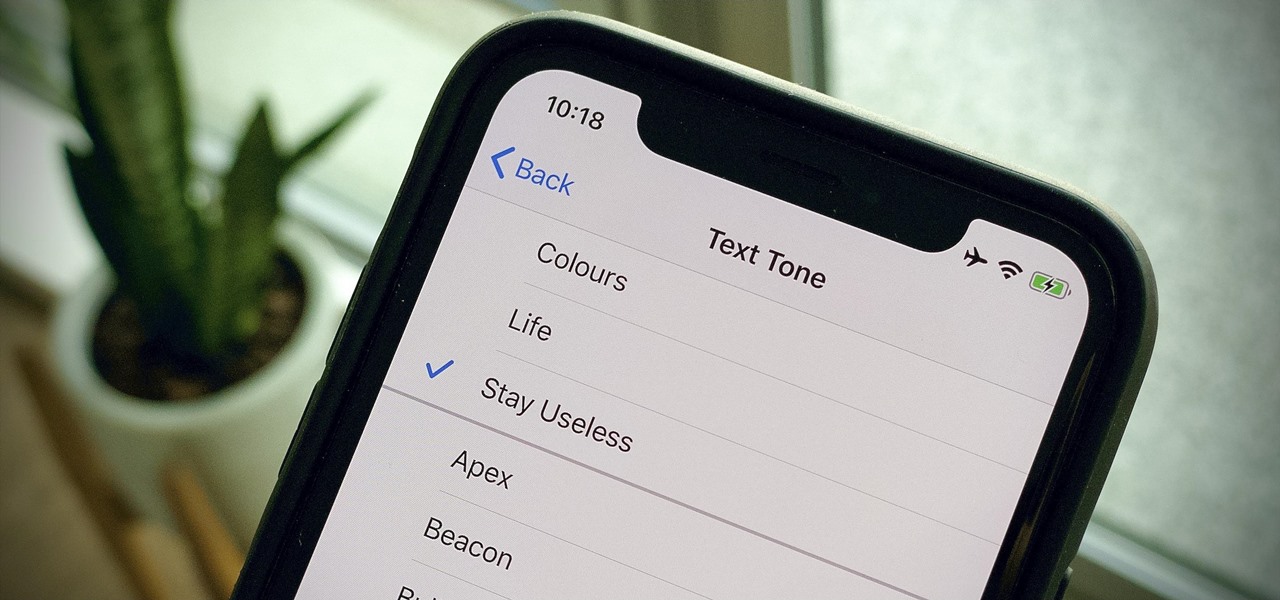
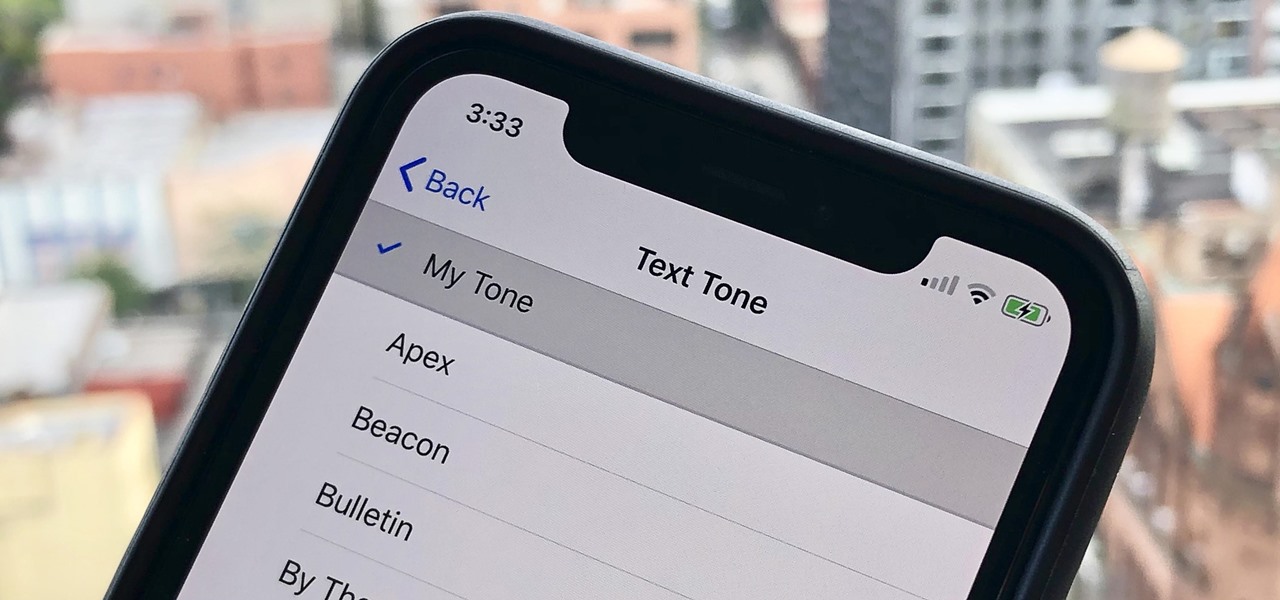
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.

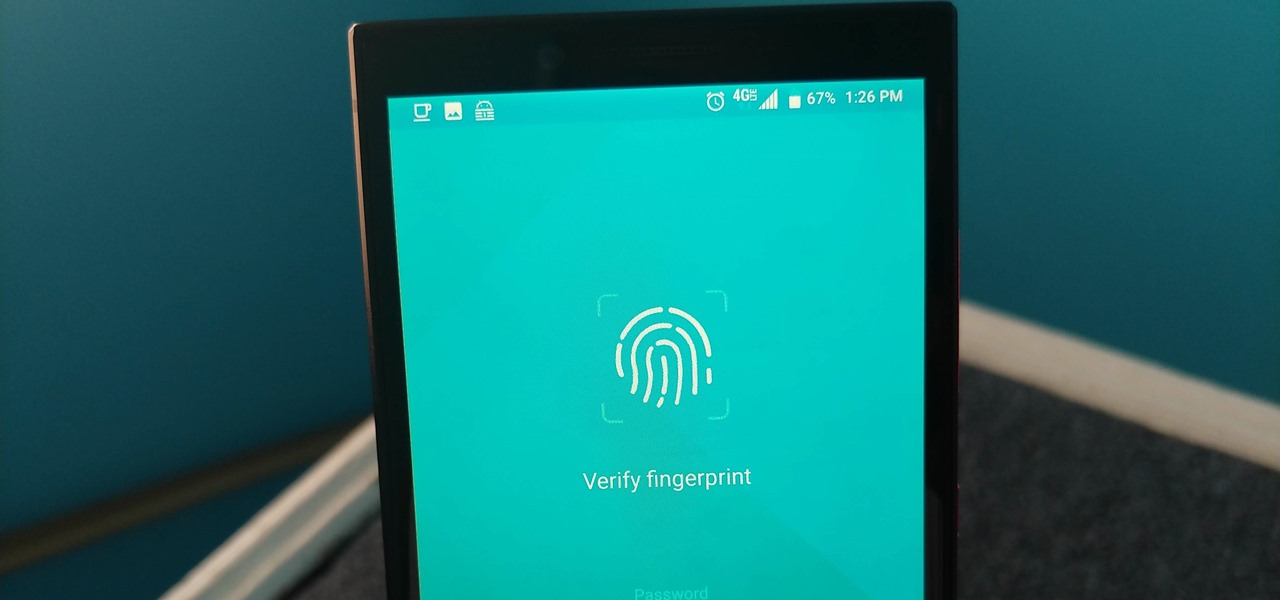
If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

As part of the iOS 11 update, Apple added a document scanner function that creates high-quality digital copies of physical documents, but it was only available inside the Notes app. With iOS 13, Apple has built its scanner right into the Files app, enabling you to quickly create PDFs with your iPhone and do more with them.

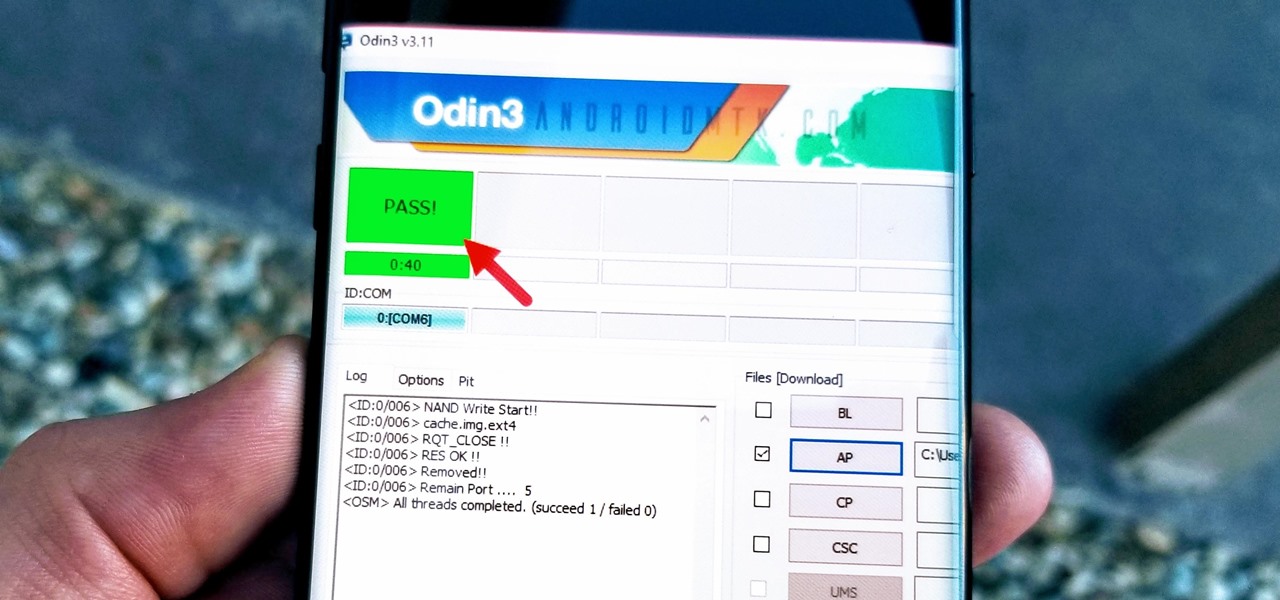
TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Your iPhone comes packed with a long list of excellent text tones to choose from. Bamboo anyone? Of course, for some of us, stock sounds from 2013 don't cut it anymore. We want customizability, something that's found more on Android than iOS. However, you can add your very own text tones to your iPhone right now, so long as you have a sound file in mind and a computer running iTunes.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

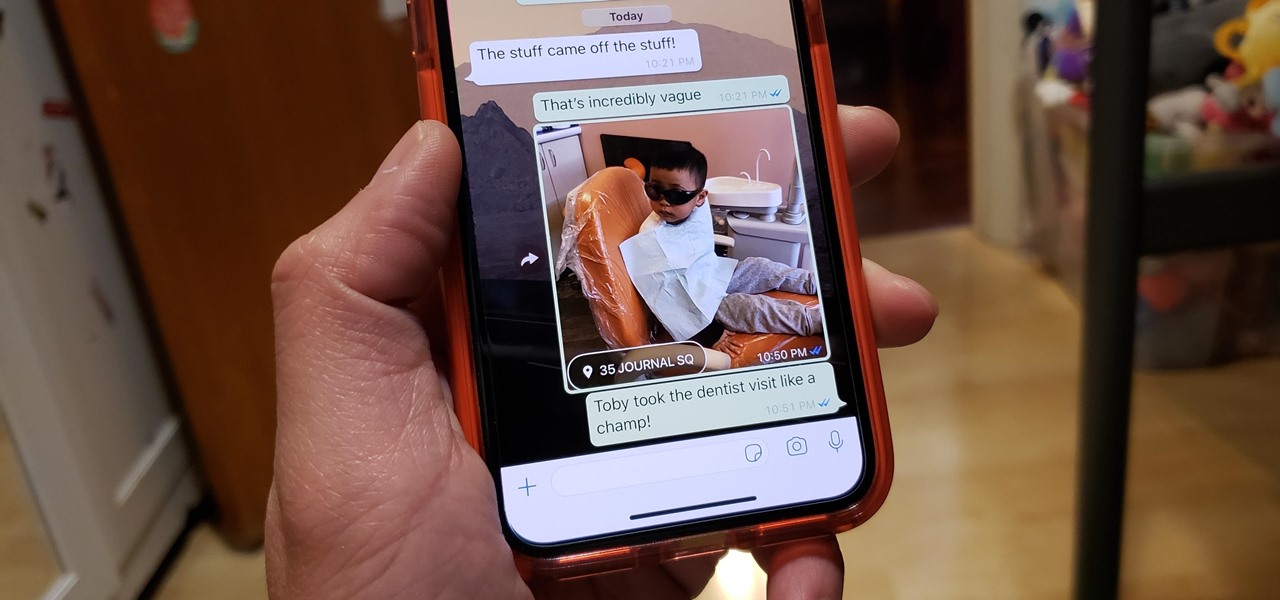
For quite some time, popular messaging apps like Snapchat have had features that let you place stickers on photos and videos to add time and location-based information. To catch up, WhatsApp has now added the same functionality to its messaging platform in an effort to remain among the most well-rounded messaging apps available.

With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

Over the past month, we've spent significant time covering Samsung's Oreo Beta program, and the detailed list of features in Oreo is extensive for the Galaxy S8 and S8+. Many of you were upset when the Galaxy Note 8 was left out of the official Oreo beta program entirely, but we found a method to install a beta Oreo build right now on the unlocked and US variants if you'd like to give it a try.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

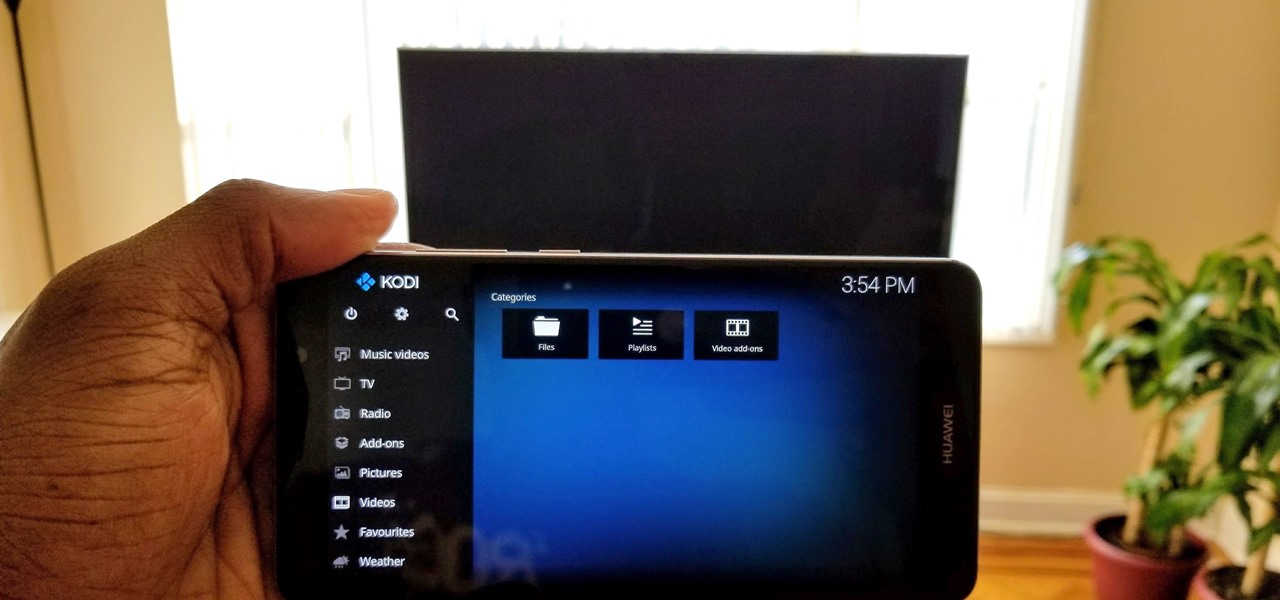
Over the years, Kodi (formerly XBMC) has become one of the most popular media players. It provides all the essential functionality needed for any home theater setup while remaining open source and free. However, Kodi is not limited to just your living room. With the Kodi app for iOS or Android, you get a streaming media player that can act as a video player, music player, picture gallery, and so much more.