New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to convert video formats with Avidemux on Ubuntu Linux.
If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.

Android has not had the best reputation for privacy and security, though Google has made strides in those departments in recent years.

Lossless quality isn't for everyone. If you can't distinguish between lossless audio and other formats, you probably but don't need it. But if you're a musician who's sharing ideas with bandmates or a journalist interviewing people for a video, you might want the best possible quality, which is what lossless offers. And you might not know it, but the Voice Memos app on your iPhone supports it.

Samsung uses their own SamsungOne font for their Galaxy lineup. But if you're coming from an iPhone or another Android device, you might not love it. With the help of this mod, however, you're sure to find a font that's right for you.

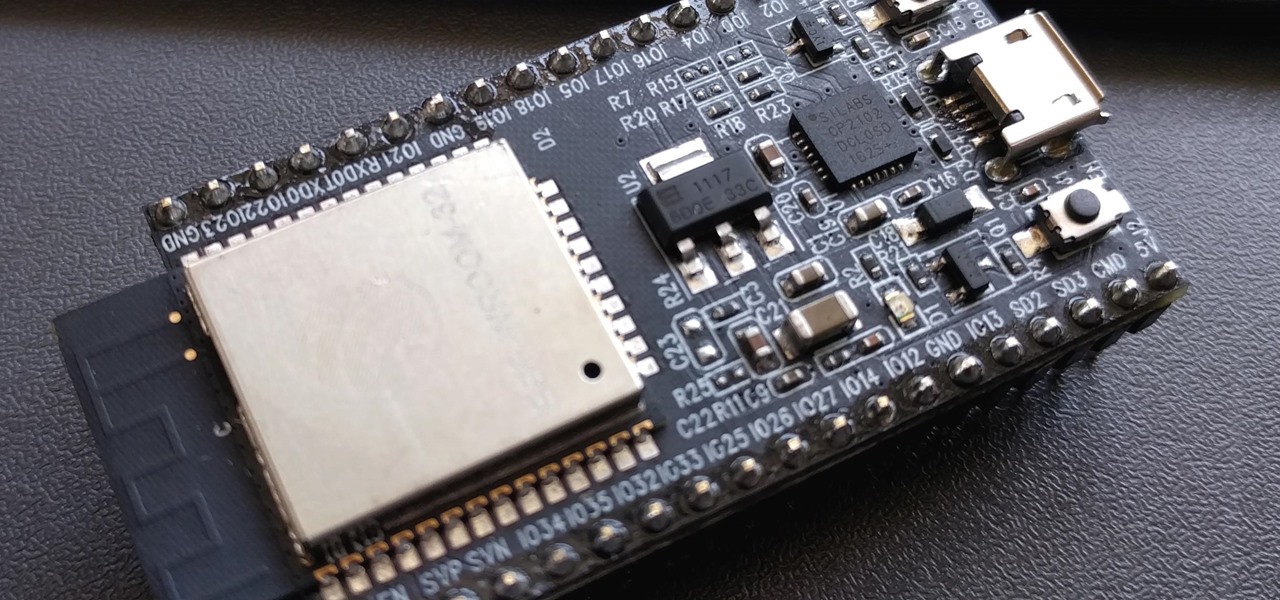
The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

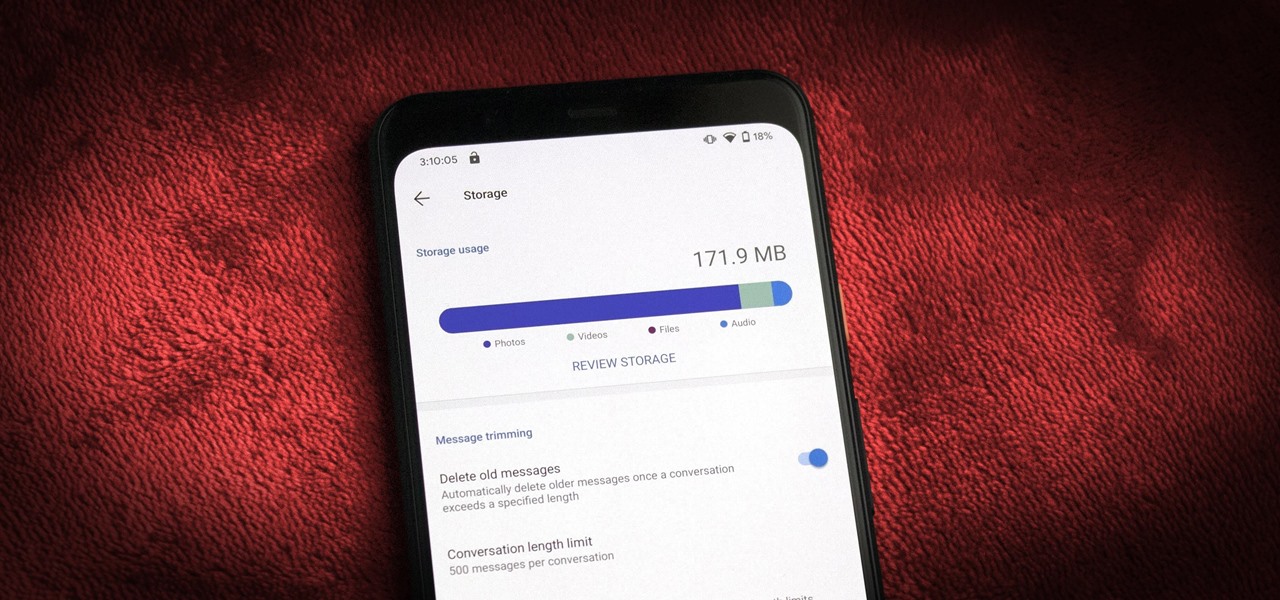
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Lenovo has done a great job preventing leaks of their new Moto RAZR. We've seen a few images here and there, but for the most part, we knew very little about the long-rumored phone. But with the announcement date just around the corner, an FCC filing has given us a look at the new RAZR from almost every angle.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

In the latest update to the ongoing Meta Company patent infringement case, the court has responded to a request from the defendants, and the answer isn't good news.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

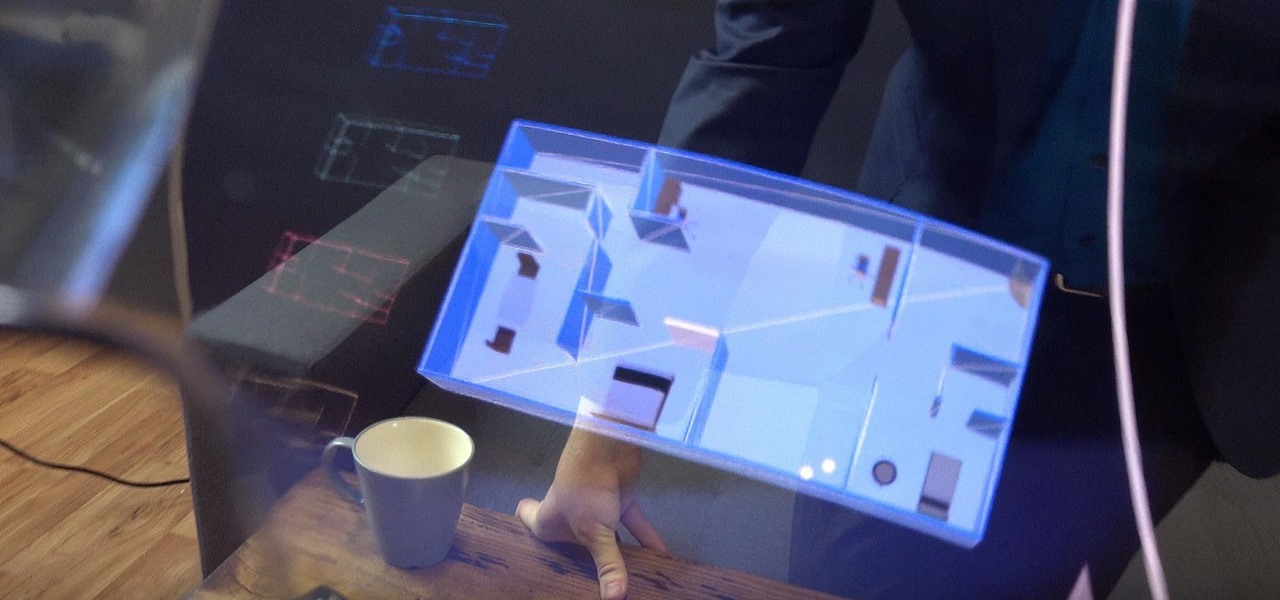
Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

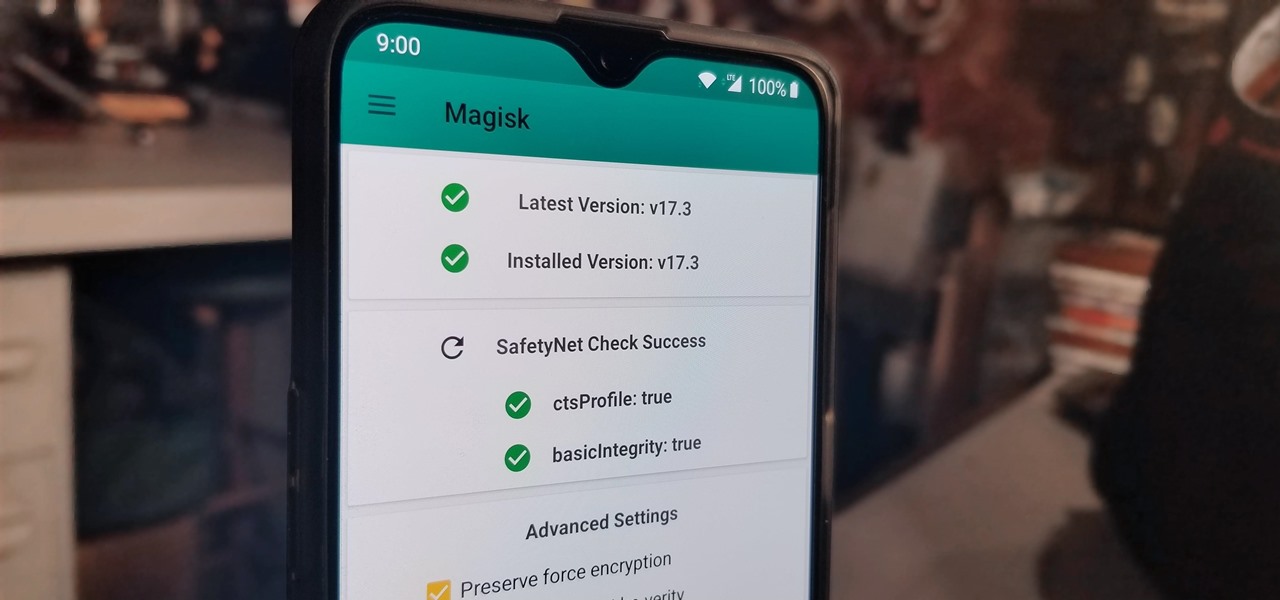
Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

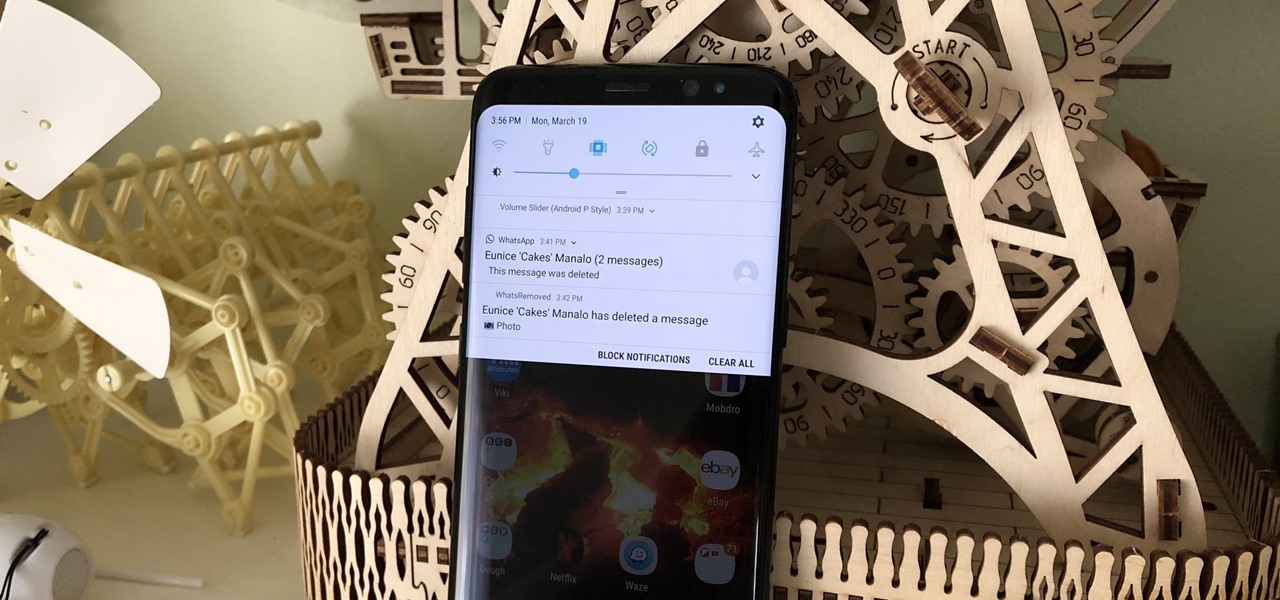
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

Android 9.0 Pie has officially rolled out, but for the time being, it's only available to Google's own Pixel phones and a select few others. Thankfully, you can get a taste of the Android Pie experience on any phone right now.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

It looks like Magic Leap is getting its ducks in a row to launch its Magic Leap One: Creator Edition as the company's name is once again showing up in US Patent and Trademark Office (USPTO) filings.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

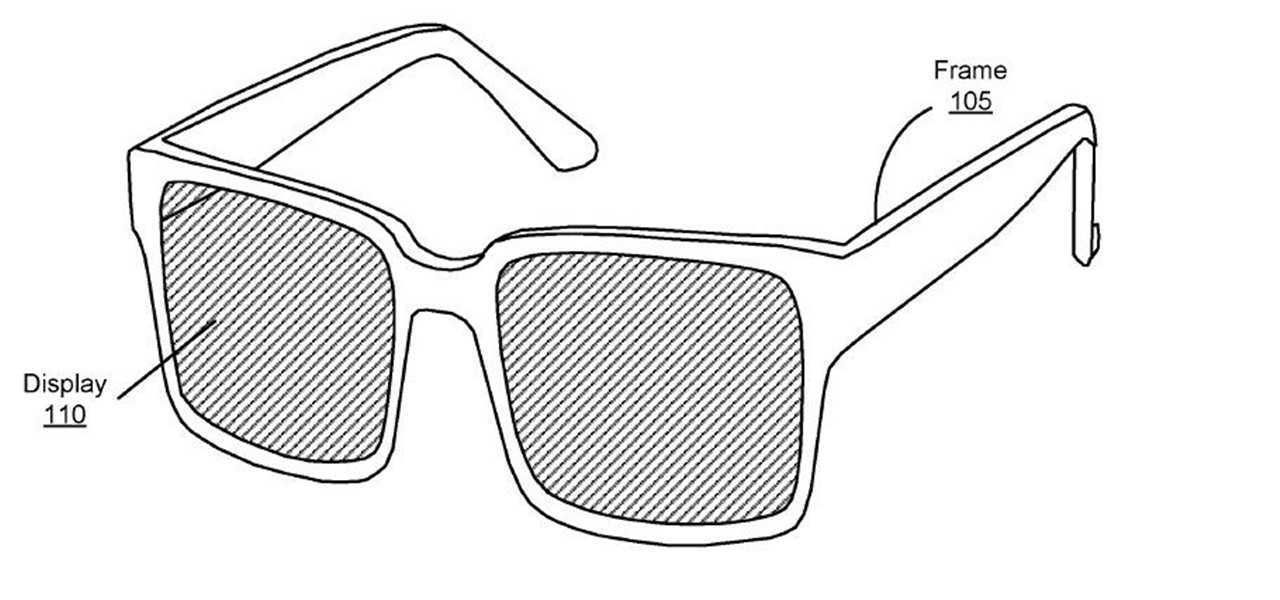
A patent application for waveguide-based smart glasses submitted by way of their subsidiary Oculus sheds light on Facebook's plans to escalate their augmented reality efforts.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.