Here’s a video on how to process your panos in Lightroom. Learn how to take those raw files and process them with a panorama in mind (it’s really a lot like processing a regular photo with just a small change at the end). We’ll process them in Lightroom and then take it through the Photomerge feature in Photoshop to finish things off.

This tutorial teaches you how to save your photos after you've edited them in Photoshop! Tutorial taught using Photoshop CS3 and recorded with Camtasia Studio v5.
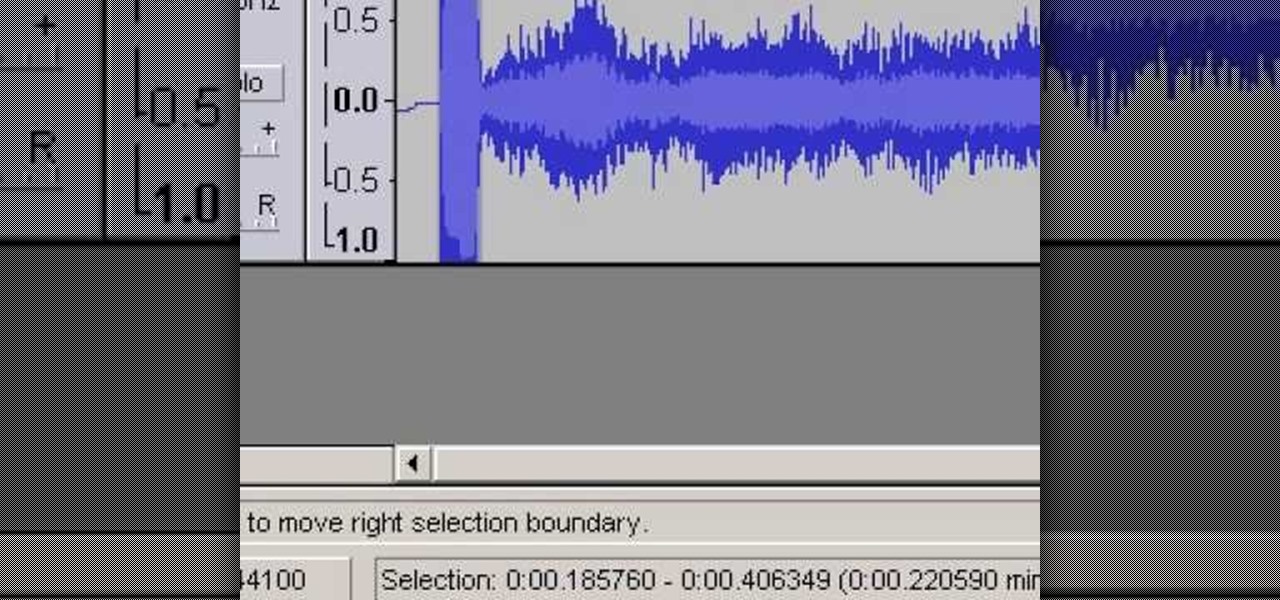
This Sony Vegas 7 tutorial talks up about many topics such as: -Explorer
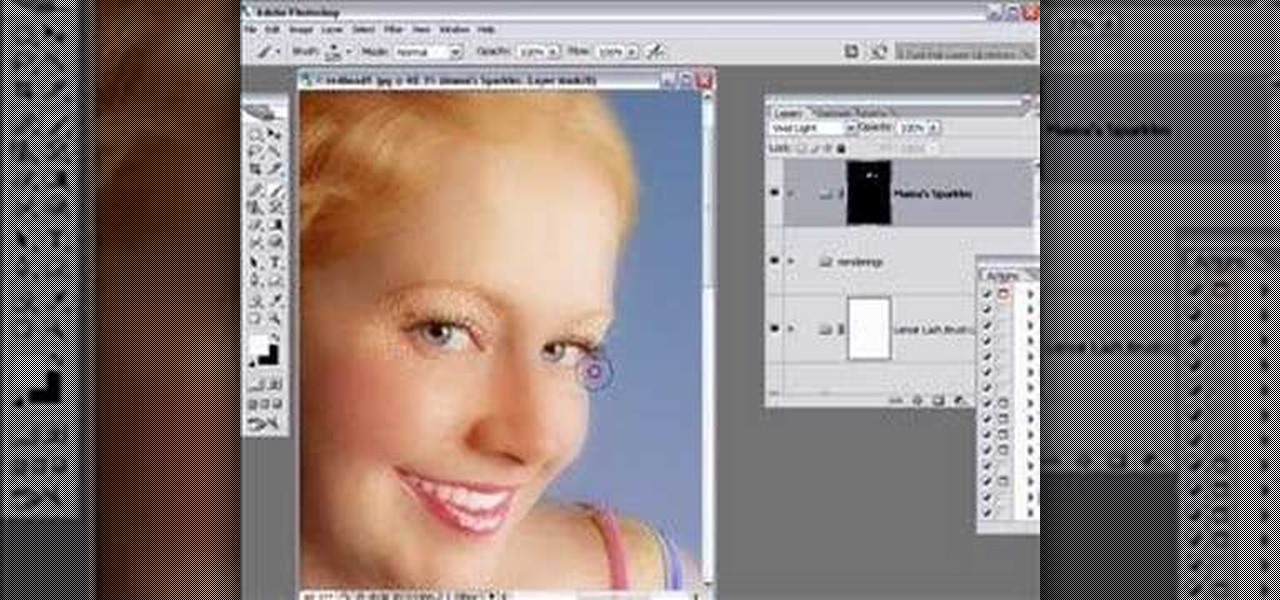
This video shows how to modify Mama's Sparkles Action for Photoshop to accommodate sparkle size to a smaller resolution file or smaller area of the image.
Chad west covers some basic masking concepts to add a pre-made border file to a photograph.
This video shows you how to download and play TV and movie files on your computer using two programs: Joost and Miro.

Learn how to change the default action that the Firefox web browser takes when opening a type of file including .mp3, .midi, and others.

PDFs are the industry standard for document sharing. However, sometimes PDFs generated by non-Adobe apps can tend to be larger than they need to be. In this video you’ll learn how to make your PDF files smaller even if they were not generated by an Adobe product.

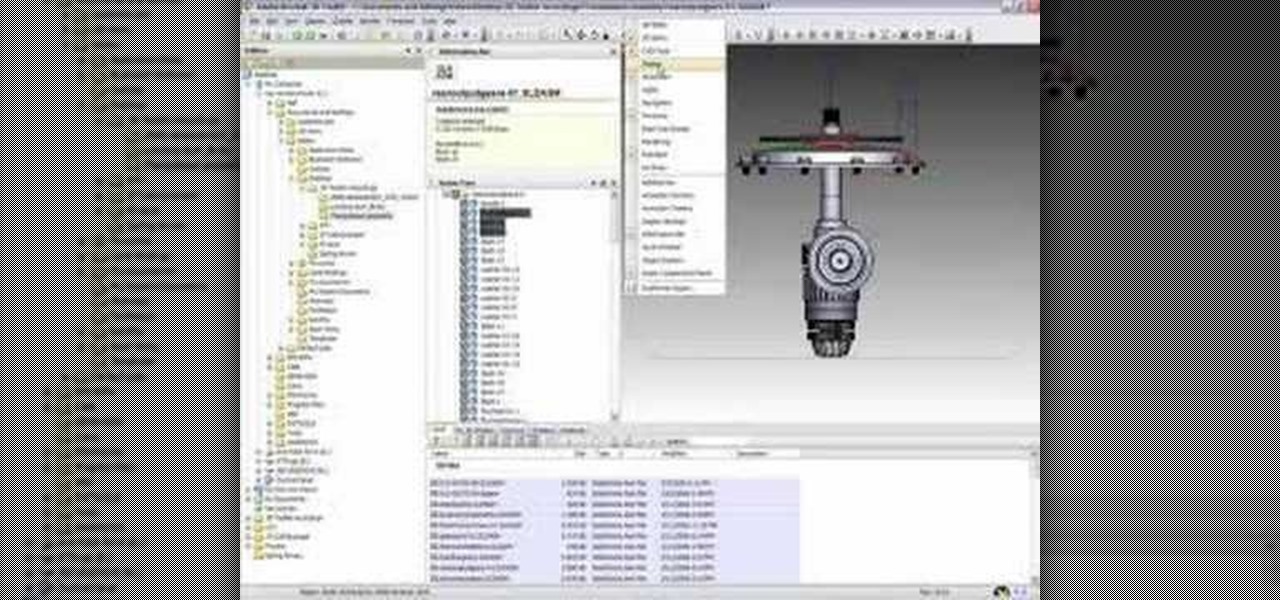
The application Acrobat 3D comes with an associated utility called Acrobat 3D Toolkit, which allows the 3D content in the PDF file to be enhanced by editing lighting, adding textures and materials, and creating animations. In this video tutorial you will learn to set up the Acrobat 3D Toolkit environment for technical illustration. Learn about the shortcuts and quick keys to quicken your workflow!

In After Effects 6.5, Adobe introduced Incremental saves. Rather than waiting for the auto-save to catch the latest revision to your project, incremental save allows you to manually save a new file, incrementing the name of your project in numeric integers. CINEMA 4D does the same. And with a little configuration, you can make it act exactly the same as in After Effects.

R4DS is a cartridge-based system that fits right into SLOT-! on a NIntedo DS. Here's how to install R4DS and be able to support ROMS, multimedia files, and homebrew games on your Nintendo DS.

Learn how to use Virtualdub - a free video editing program available online. Learn how to use Virutualdub to edit videos and convert video file formats.

Lillian Garcia demonstrates how to remove the polish from you nails and how to file your nails. The video explains how to apply nail polish remover and how to shape you nails with an Emory board.

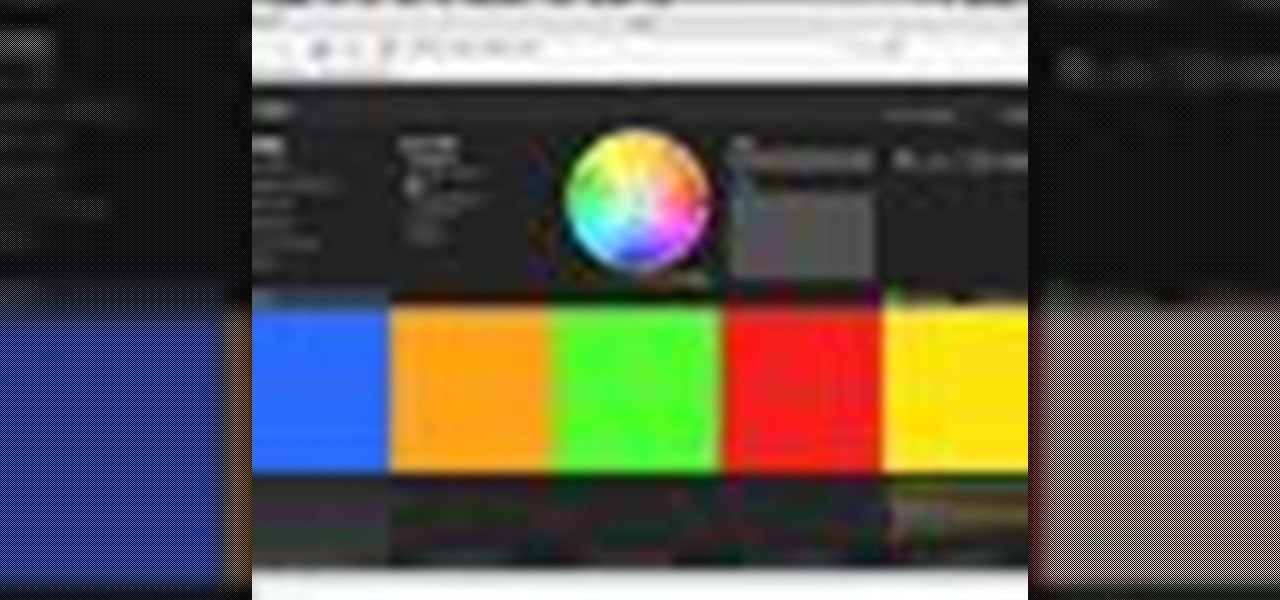
Kuler is a beta Adobe application at labs.adobe.com. It allows you to choose color schemes using rules or completely at random, then export the colors as an Adobe Swatch Exchange file for use in all of the Creative Suite applications. In this video tutorial you will learn how to create color schemes using Kuler.

In this Podcast you’ll see how to make a form using Adobe InDesign CS2 and then export it as a PDF file. After your form is in PDF form, you can open it in Acrobat 7 Professional and create fields on top of the PDF. This enables users to fill out the form right inside their web browsers with the Free Adobe Reader. Check out this video and learn how to do it now!

Need to move your my documents folder in windows xp because you have 2 drives for video editing and want to keep files on one drive and the operating system on the other, or maybe you just have an older computer to which you've added a new drive? Find out how to use Tweak UI to change some the hidden settings to move your my documents folder.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

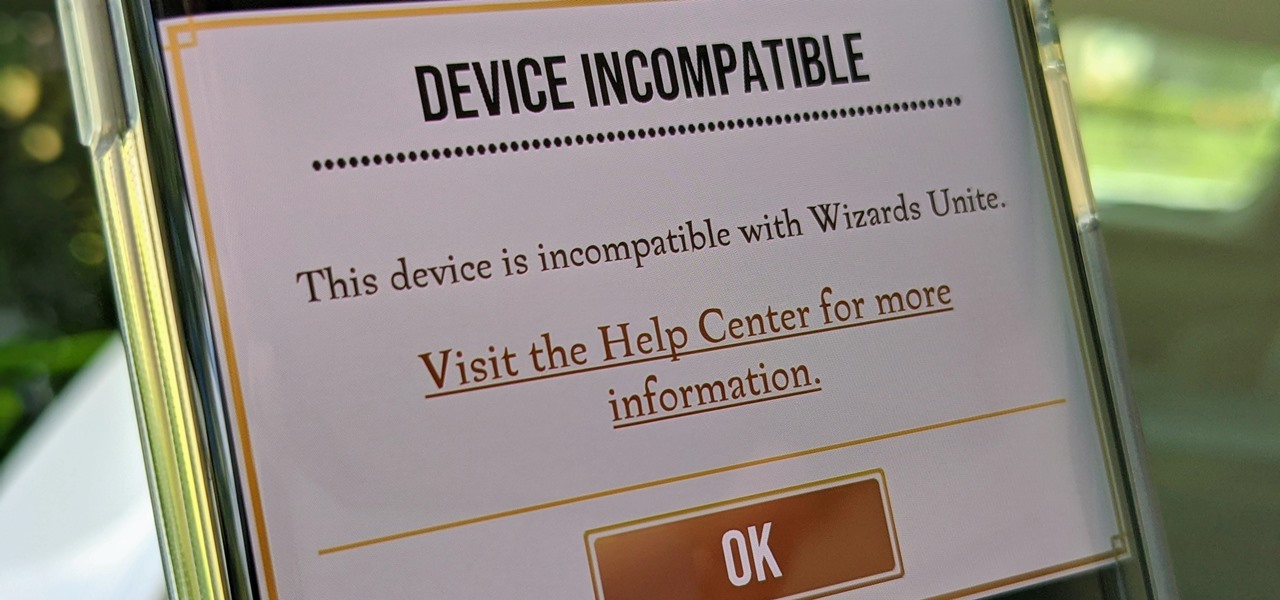
Harry Potter: Wizards Unite has gained quite the fan base since its launch, but not without a few bumps along the way. Niantic, the game's developer, has a long-running history with trying to block all root users on Android. The methods will vary for each game, but this time around with Wizards Unite, they appear to have a new detection feature at play from the recent 2.9.0 update. Let's find out what's going on.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

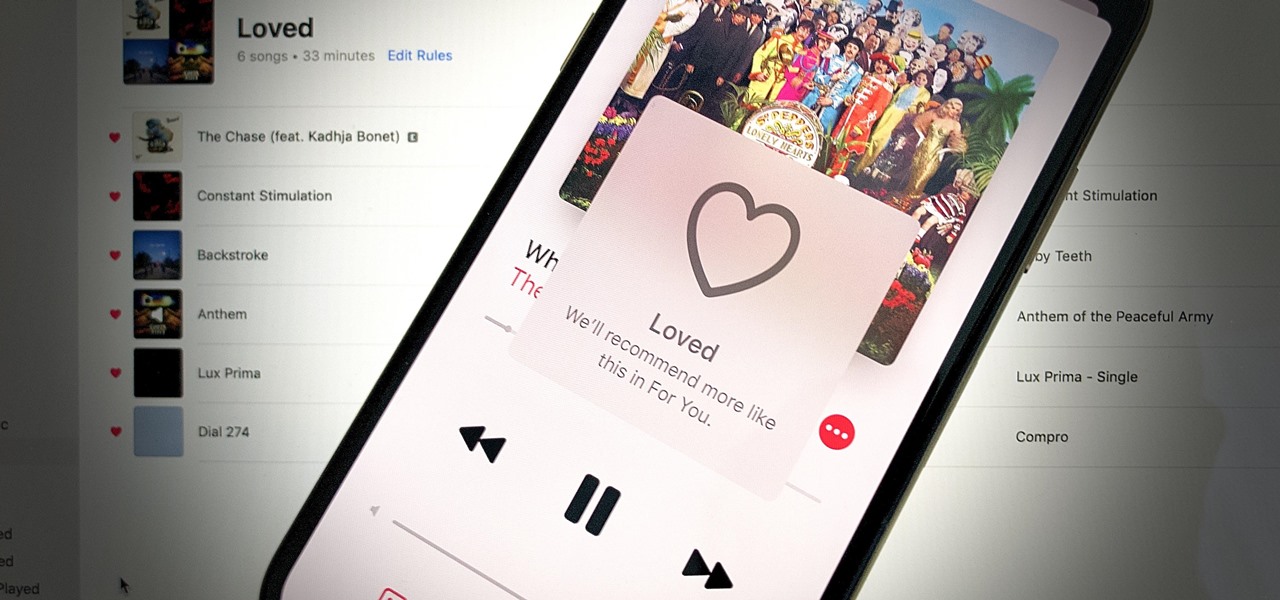
In Apple Music, loving and disliking songs is a great way to teach Apple's subscription service what type of tunes you like and which you don't. While it also seems like it should be an excellent way to keep track of songs you enjoy in the wild, there's no clear way to view all of your loved tracks in one convenient list. There is a way, however, but easy it is not.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!