
How To: Apologize, the Japanese way
1. Shallow Bow You bump into someone in passing


1. Shallow Bow You bump into someone in passing

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

I am a graphic designer, so I have to collect massive pics from webpages to provide me with inspiration. But sometimes I need to use them everywhere, even if I've no access to computers or laptops, so I have to resort to mobile devices.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Spotify lets you customize some aspects of your experience, whether on the desktop, web, Android, or iOS app. And one of the simplest yet coolest customizations you can perform is changing your playlist cover images. However, it doesn't work on all playlists.
Unlike the realm of virtual reality, augmented reality is less about losing yourself in some fantasy environment, and more about getting things done in the real world. So while we've seen some great games that capture the imagination on devices like the Magic Leap One and the HoloLens, when it comes to real-world usage, the biggest developments coming for AR apps that are the more practical ones.
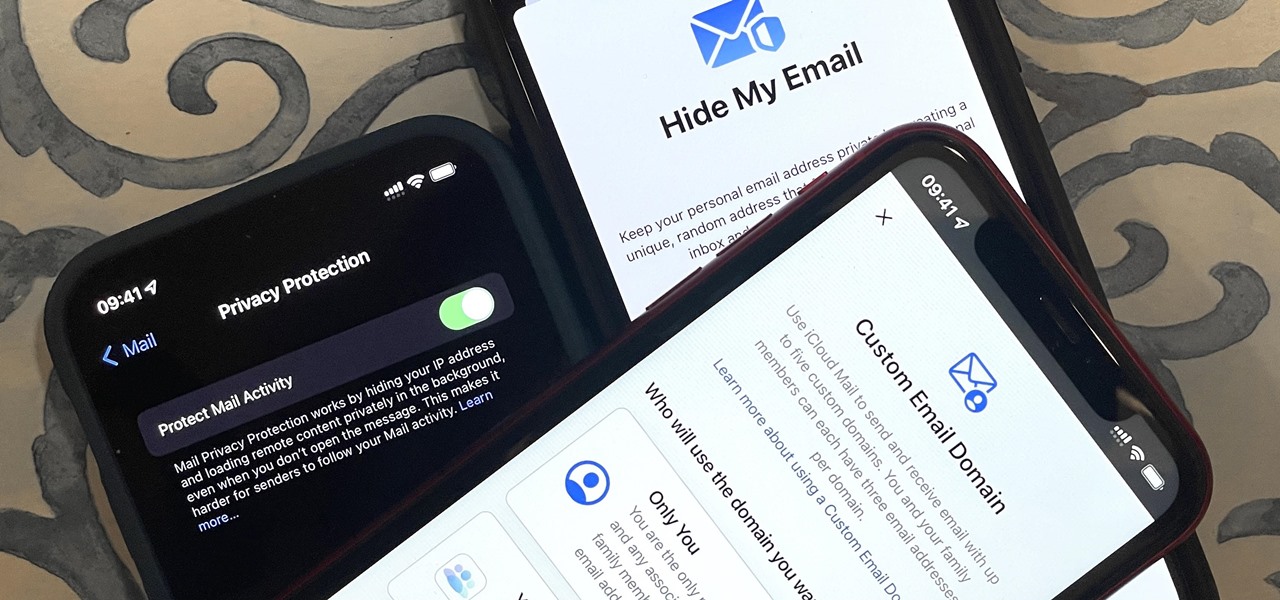
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

The popularity of breakdancing waned by the late 1980s, but has been recently rediscovered by a new generation of dancers who perform in professional competitions. While taking breakdance lessons might seem to violate the very ethos of the “streets” movement which spawned the genre, no one will ever know you learned the basics of breakdancing in a free online video course. Our expert dance instructor demonstrates the foundations of up-rocking, popping, locking, the six step, and power moves l...

While taking Breakdance lessons might seem to violate the very ethos of the “streets” movement which spawned the genre, no one will ever know you learned the basics of Breakdancing in a online video course. Expert dance instructor Julie Urich demonstrates the foundation of toprock, downrock, and power move steps you’ll need to ensure you don’t “get served” during your next battle.
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

I like to grow vegetables all year round, and I couldn't afford the big gas bulbs, or the power to run them. The big gas bulbs:

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.
New York (CNN) -- New York City police didn't violate New Jersey state laws when they carried out surveillance programs of Muslim-owned business, mosques and university student groups, according to a Thursday statement from the New Jersey attorney general's office.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

If you live in an urban environment, chances are that you've seen this: It's a program started by the FBI to prevent terrorism and general thievery in peaceful and innocent communities all around America. I myself have seen a lot of these, and my previous apartment community was part of this 'program'.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.
I’m seeing a flood of posts on youth football forums and even getting a few e-mails from youth football coaches complaining about “player agents” also known as parents. Most of these unhappy coaches are dealing with parents that have non-issues, have an agenda, are misinformed, don’t know much about the game of youth football or are just people that gain great pleasure from complaining. The 80/20 rule is more like 95/5 in youth football, 95 percent of the problems are caused by 5 percent of t...

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)