News: Samsung Keyboard Vulnerability Exposes 600M Mobile Devices!
Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.


Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image as intended.

It's late and dark, I'm playing Dying Light, and, admittedly, I'm a little creeped out. Working as a grown man's night-light, this is one instance where I actually appreciate the light bar on my PlayStation 4's DualShock controller. But outside of a few particular instances, I generally find it to be quite a nuisance.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

Samsung's Gear VR headset is a thing of beauty; unfortunately, it only works with the Samsung Galaxy Note 4. That's where ImmersiON-VRelia's Head-Mounted Displays come in to play. With four different HMD models, we got a hands-on look at "The Go," which is not only affordable (at $125), but also compatible with the majority of Android and iOS devices.

Minecraft is a simple game with a huge following, and is a great inspiration for easy, DIY Halloween costumes. We've already shown you guys how to make a Simple Steve costume and a Creeper costume—now it's time for a new Minecraft-inspired one.

Mobile gaming, in case you haven't noticed, is huge. From the astronomical popularity of Candy Crush Saga, to the ease of using old school emulators, we love gaming on our mobile devices. The future is also bright, just take a look at the Oculus Rift, an immersive virtual world that just might change the way we view and play games.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

I've had this idea in my head for almost a year now. I knew what I wanted to do, but wasn't sure if it would work. After a long time of armchair-engineering, I decided that the best way to test my idea was with a soldering iron and a screwdriver.

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.
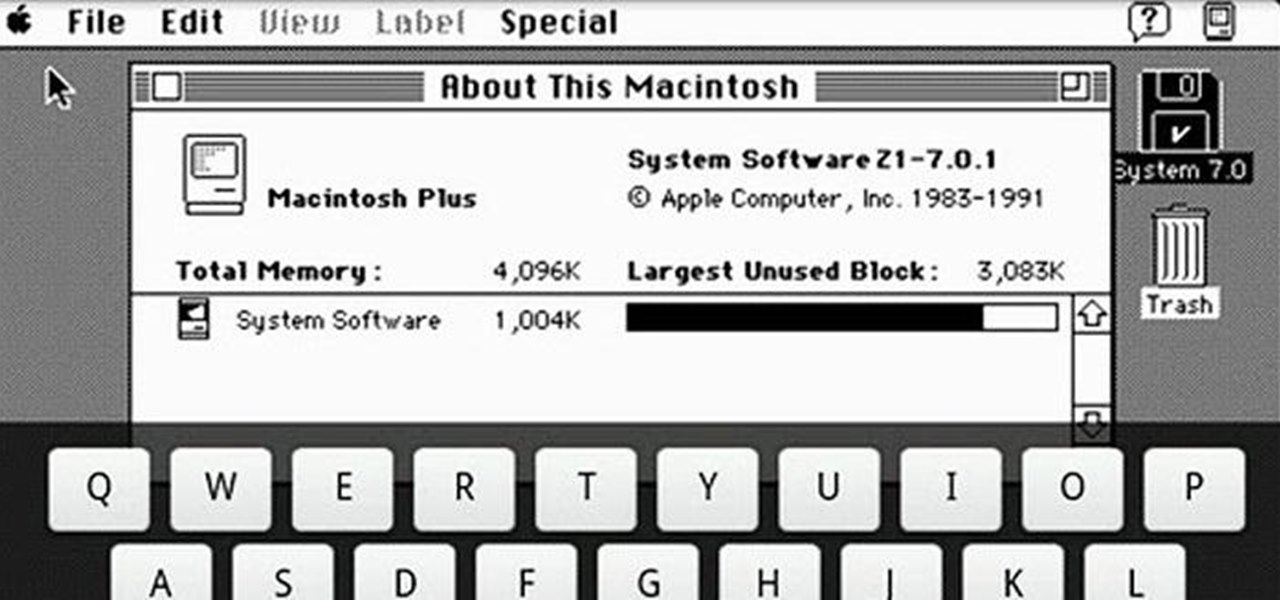
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

Google has just launched a new revolutionary augmented reality game for Android called Ingress. Their new mobile game centers around the fight for control of the minds of everyone here on Earth. It's a freaking worldwide fight—from your smartphone! While augmented reality in is nothing new in the smartphone gaming world, it has never seen the likes of this. With an almost Halo-like storytelling, Ingress seeks to bring out gamers all across the globe to perform physical activities by transform...

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania
Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

Drums Overkill is a new virtual instrument from Best Service that features 1,200 drum kits and a total of 27,000 samples. Never before has such a huge collection of samples been formatted into "ready-to-play drum kits" that can be loaded into the included Kontakt 2 interface which you can then play on your keyboard. Learn the basics of using the Best Service Drums Overkill kit in this Kontakt 2 tutorial.

Ian Ozsvald shows how the powerful, interactive python shell IPython can be combined with the Python debugger to provide a powerful debugging environment.
If you're looking to try your hand at a virtual existence, IMVU is the world to go to. Start out by creating your very first account on IMVU. See about building your avatar.
Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

Thirteen isn't an unlucky number for this Limbo walkthrough; it's the number of videos in this series, a series which shows you the complete process, through trial and error, life and death, and as least amount of edits as possible.
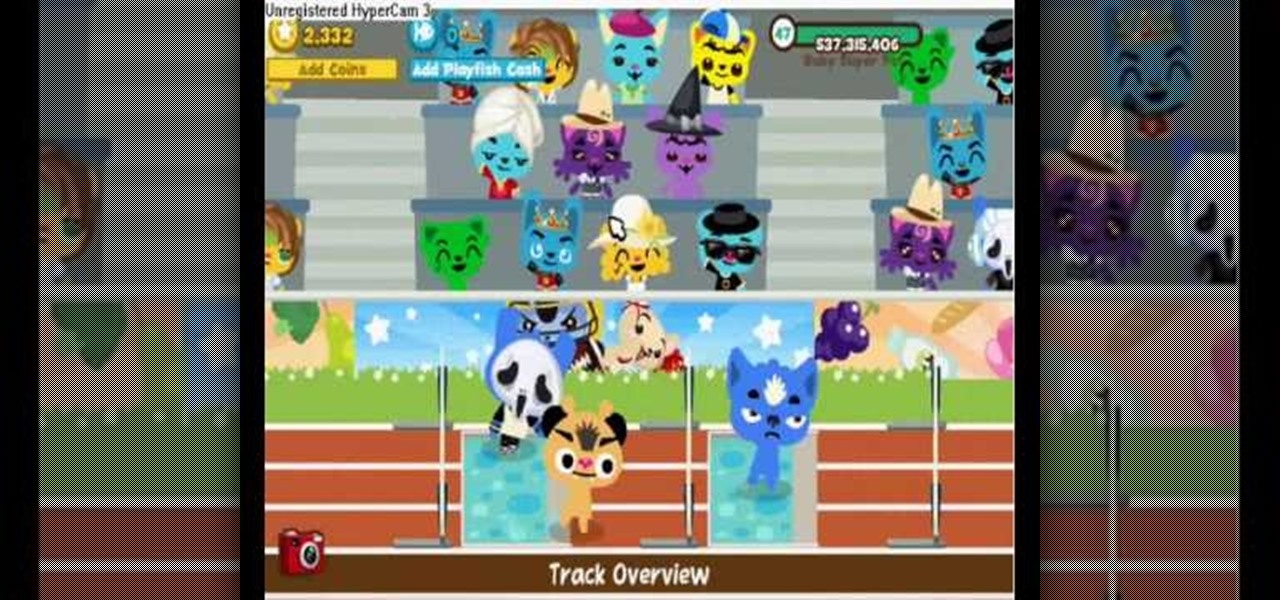
Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.
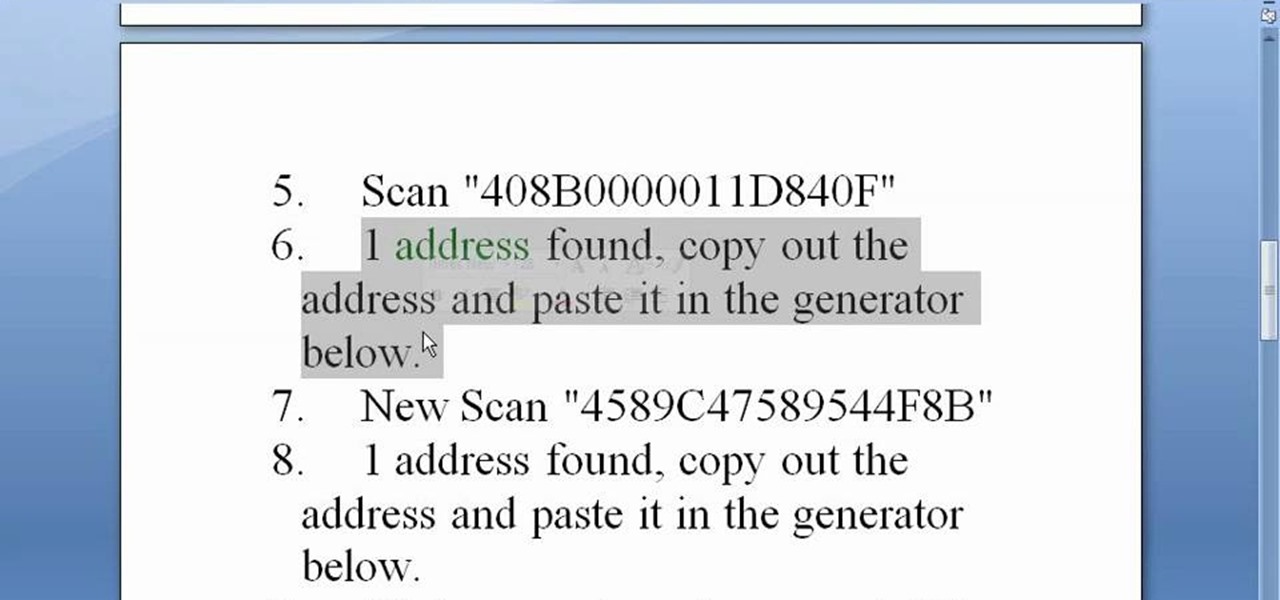
This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

Learn how to make your videos well under the 100mb limit using virtual dub and learn to break the video into pieces if the video is much too long. Learn from the master of humdrum tutorials!

Here's another video from the Tees2Greens Virtual Golf Pro, Stuart Smith; this time on how to stop hooking the ball. He offers a few checkpoints to follow that should get you hitting the ball straight again.

Part of the mainstreaming of augmented reality is learning to adopt new habits around the hardware delivering these groundbreaking next-gen interface experiences.

After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product.

There's already some fierce competition between Snap and Facebook in the AR space, but it's about to heat up even more, with Snap snatching up a 3D mapping startup that could add some new AR capabilities to its arsenal.

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.
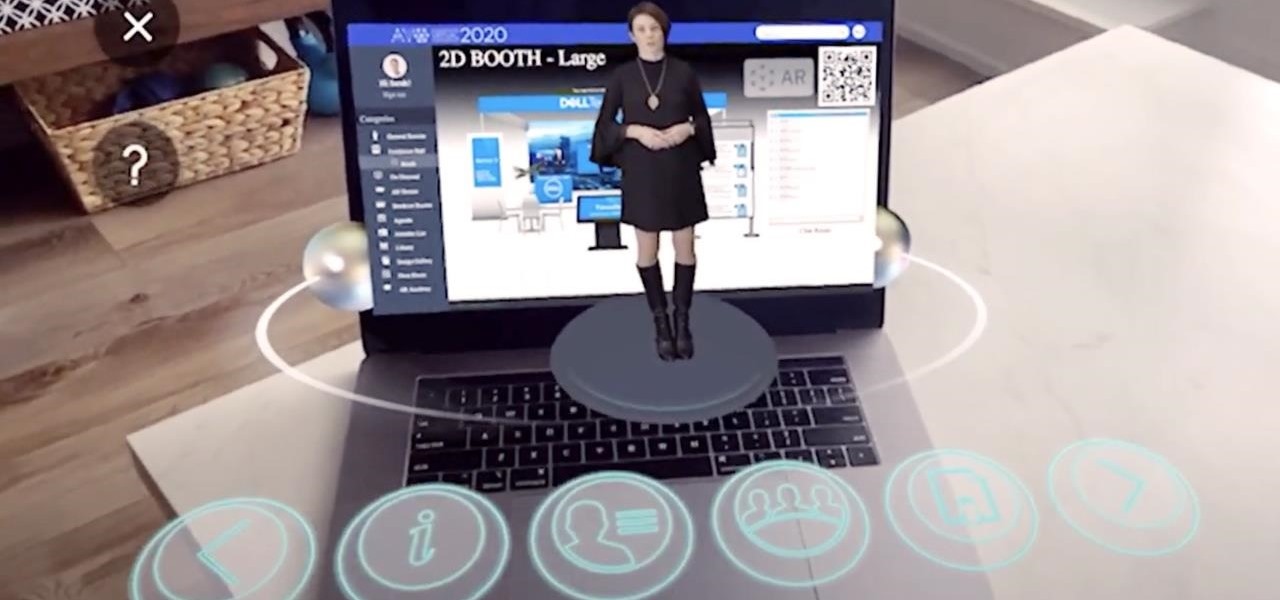
As augmented reality space continues to move into the mainstream, the competition to offer immersive services is ramping up as well.

February is the shortest month, but it's marked by the celebration of Black history and the celebration of romantic love.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.