You probably don't give much thought to buying yogurt in the store. You have your favorite brand, or maybe you like trying new varieties each week; either way, you just grab it and go.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

There are so many great apps in the Google Play Store that it's become the number one app marketplace in the world.

One of the best qualities about fresh bread (such as sourdough) is a thick, crispy crust—which is easy to create in a commercial oven, but can be tricky for home cooks to replicate. Luckily, the the trick to baking a professional-style crust is a simple one—just bake your loaf with steam using one of these three methods to achieve the perfect, crispy crust.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

Samsung trademarked the name Gear 360 a few weeks ago, and today it has been confirmed that the Gear 360 is a spherical virtual reality camera that will accompany the much-anticipated Galaxy S7.

There are a million (okay, slight exaggeration) ways to peel an egg, and countless numbers of tips, tricks, and hacks that are supposed to make that deviled egg appetizer you agreed to make for the party an absolute snap. More often than not, though, experiences vary... and pock-marked, greyish-yolked boiled eggs find their way into your collection whether you like it or not.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

At night, no matter how dim my Android's screen gets, it never seems to be enough—especially when I'm in bed. In fact, in pure darkness, the lowest brightness setting on my Android devices end up giving me a headache that keeps me up for hours.

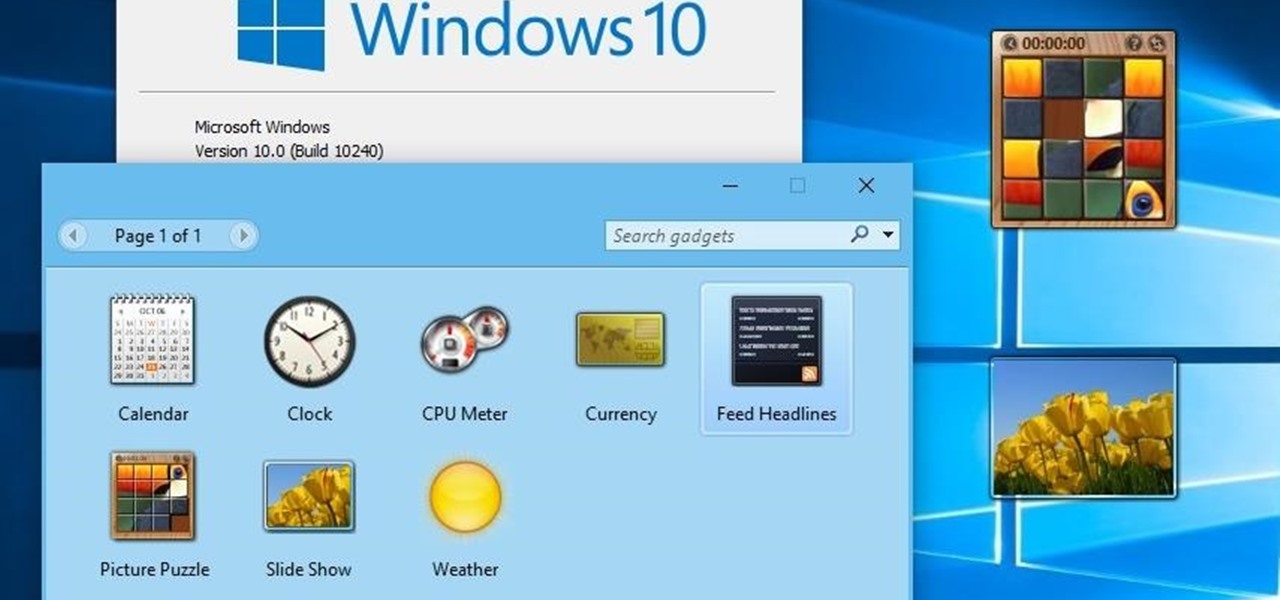
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

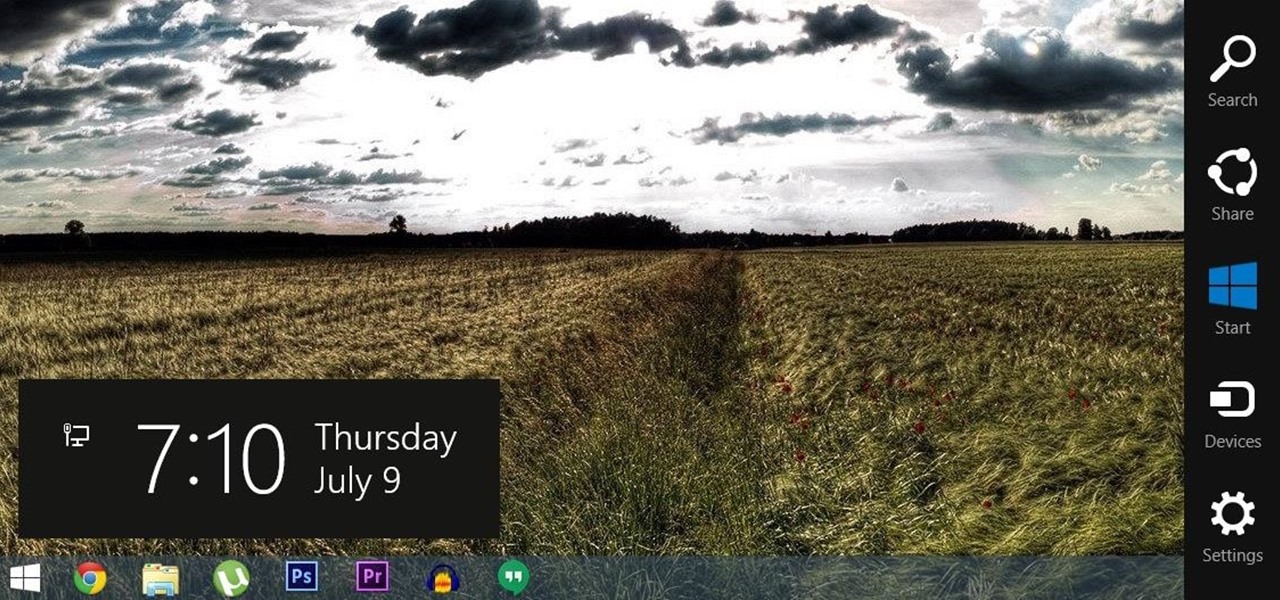
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

Summer cookouts and barbecues come with a lot of delicious foods, but to me, there's nothing better than dishes heaped with avocados. From guacamole to simply eating an avocado right out of its skin, I devour this fruit constantly—but it's one that can be tricky to find perfectly ripe.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

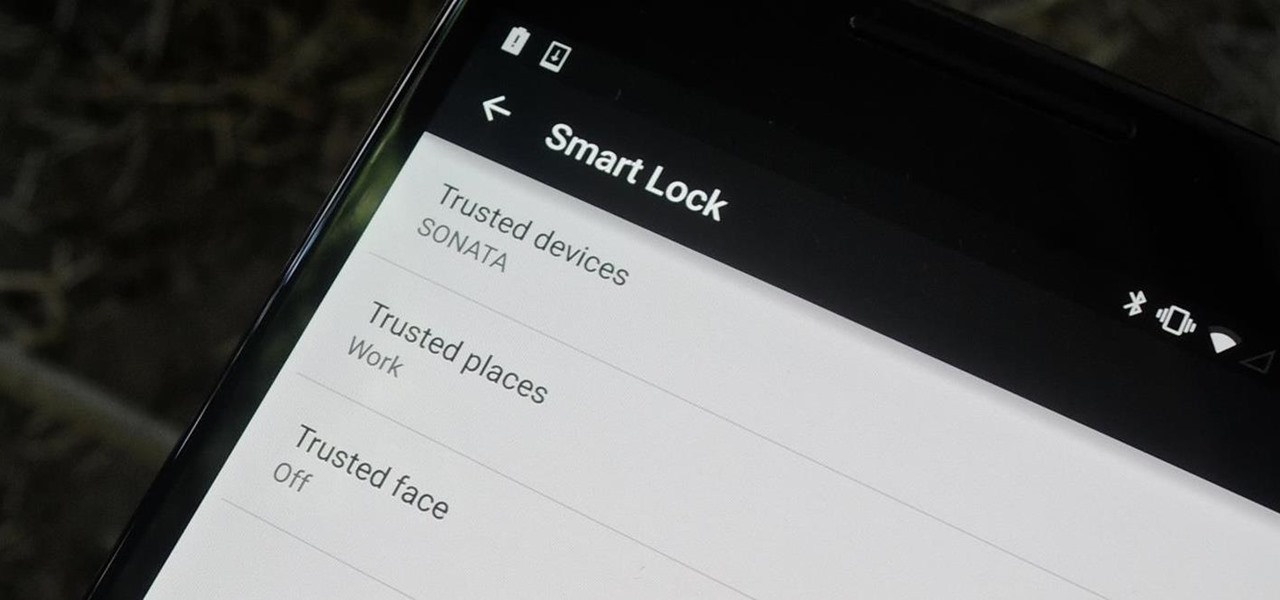
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

On-screen navigation buttons offer many distinct advantages over physical buttons—they can change orientation along with your device, they're capable of visually morphing to indicate secondary functionality, and the user experience is more consistent when buttons and app elements require the same amount of force to press. Add to that the fact that they're far less likely to fail and can be themed or even switched out altogether, and it's hard to come up with an argument in favor of physical b...

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Keeping your OnePlus One running smoothly can be taxing, especially if you spend most of your day looking for ways to tweak performance settings like me. Sometimes I get lucky and end up with a faster phone, but because I experiment so much, I often end up restoring it back to stock. This process can get old really quick, but when I started using the Bacon Root Toolkit from WugFresh, it became exponentially easier.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

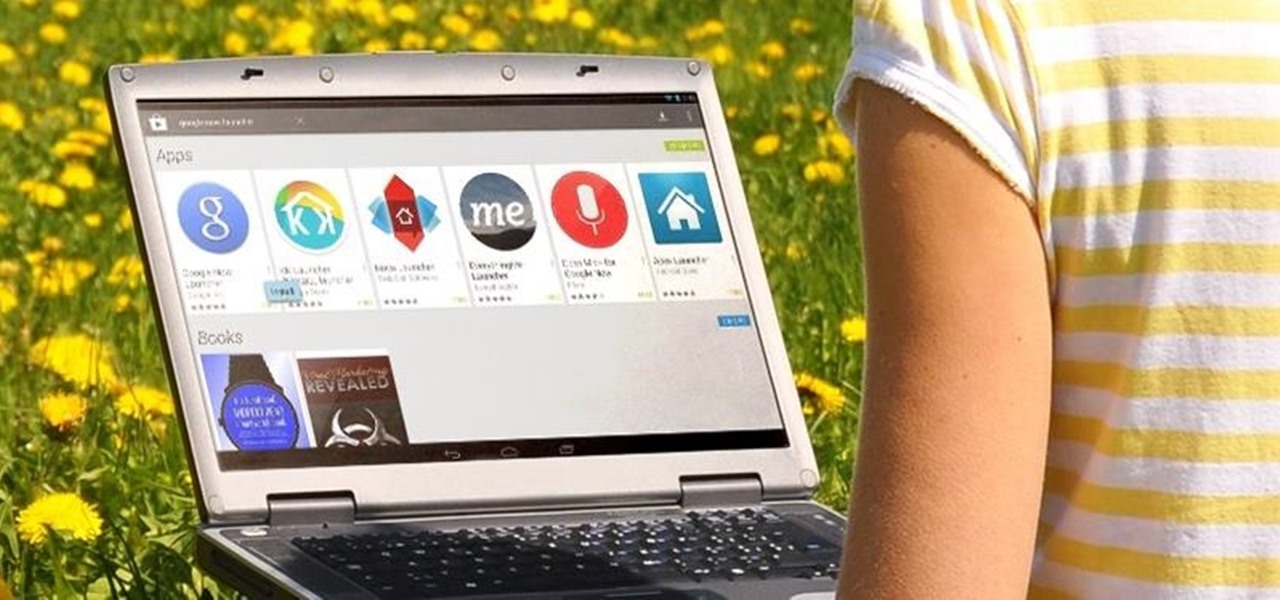
There are tons of good reasons that you might want to use Android on your desktop. Perhaps your favorite game is only available on Android, or maybe you use a messaging service that doesn't have a Windows companion app.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

One of the most feature-packed camera suites out there resides on the Sony Xperia Z2. Along with the regular camera and video modes, it comes with Motiongraph, AR Effect, and Social Live.

Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

Loving parents can suffer bouts of insomnia when their children leave the house. Not just when they move out, but when hanging out with friends or during out-of-town weekends. Others may worry about their significant other who has to work late all week and their only option for getting home is that sketchy nighttime bus.

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

Your new HTC One M8 has a ton of really cool features, some of which relate to waking the device up. A swipe up to unlock to your last active screen, a swipe down to access the voice dialer, and a double-tap (or knock) to wake the device and bypass the lock screen.

The outstretched arm, the perfectly positioned angle, the shot and the subsequent array of tinkered saturation, contrast and shadows. In almost every car, changing room, or Starbucks, these string of events happen—you might know it as the selfie.

Microwave popcorn promises so much—a tasty, relatively healthy snack that's ready in minutes—yet it rarely delivers. Most of the time you'll end up with a scorched bagful or a bunch of stubborn un-popped kernels, but it doesn't have to be that way. With a few simple tricks, it's easy to get perfectly fluffy, tender-crisp popcorn every time.