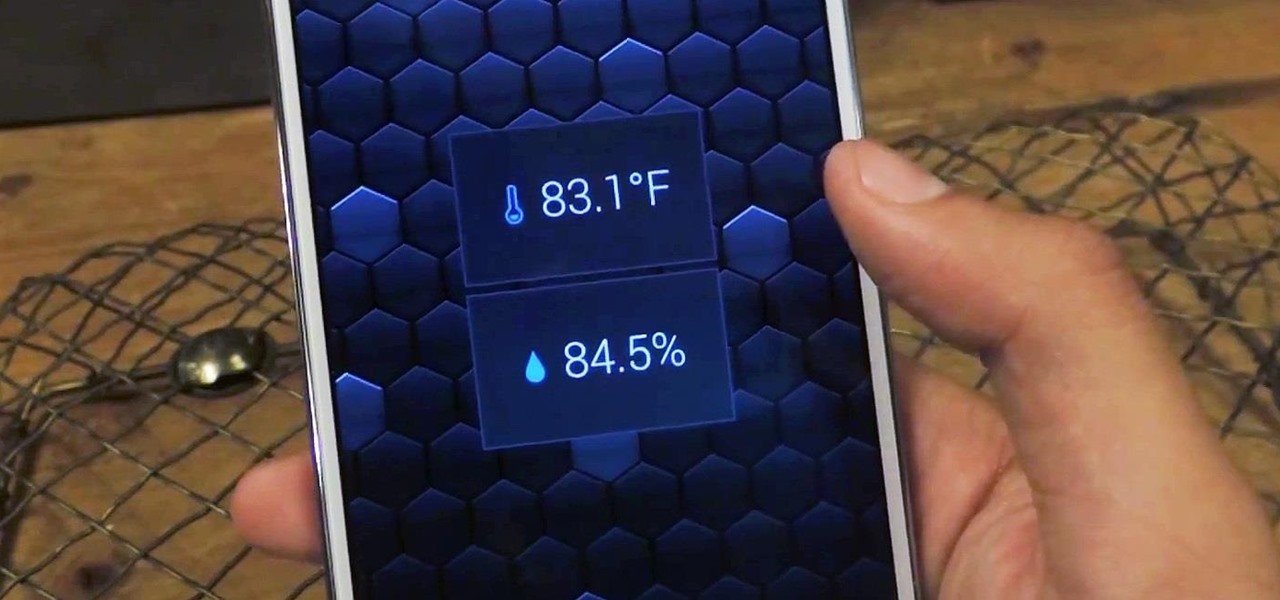
The majority of Android devices have built-in sensors underneath the hood that measure motion, position, and several environmental parameters that provide data needed to monitor your movements and adjust accordingly.

My favorite type of video game is first-person shooters, and the one that started it all for me was GoldenEye 007. There was just something about the controls, fast-paced action, and free-roaming environment that got me hooked.
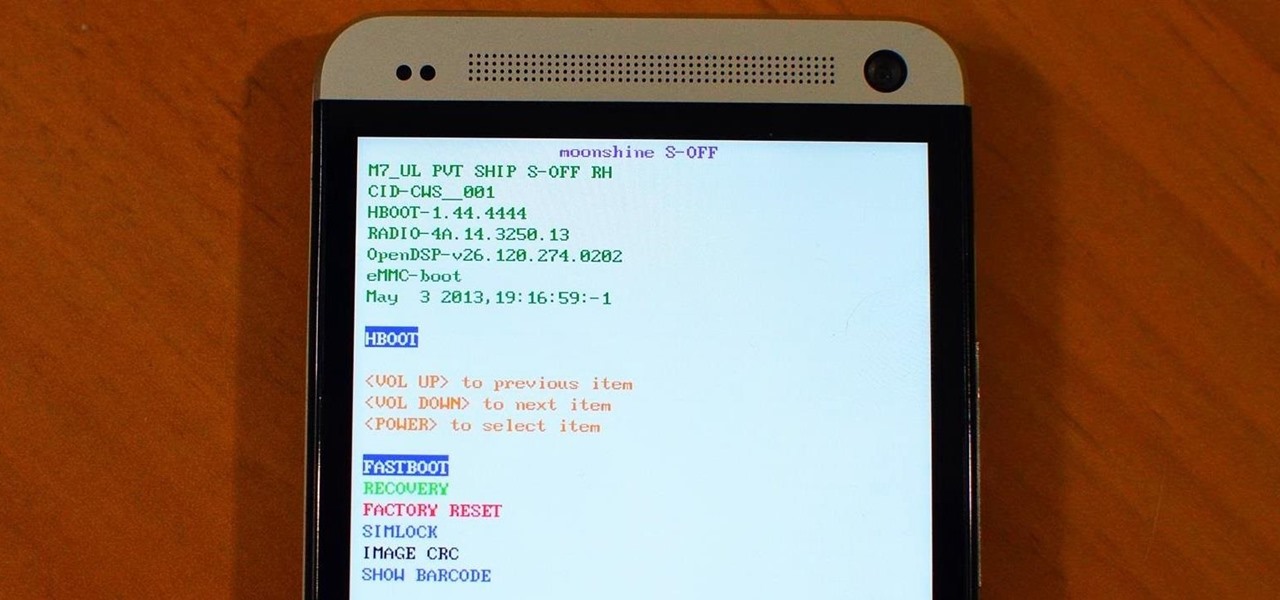
If you still have time left on your warranty, taking your HTC One in for repairs can be a serious pain if you've modified it in any way. To avoid the chance that they'll reject your phone because it's been tampered with, you'll have to return it to stock condition.

You can find a ton of live wallpapers for your Android device on Google Play, but the more alluring interactive ones are a harder to come by, which can bring your home screen to life using a few finger swipes and taps.

A mustachioed Italian plumber collects coins and battles bullets, plants, fish, mushrooms, and turtles in strange environments to save a princess held captive by a crazy, spiked-shell, bipedal tortoise.

Every time Apple releases a new version of their mobile operating system, it comes packed with an assortment of bugs, issues, and other hindrances.

A blue hedgehog runs at high-speed through fantasy environments collecting rings. Sounds a bit loony, but I’m of course taking about the Sonic adventure series that was made popular on the Sega Genesis. The days of cartridge 16-bit gaming has long been eclipsed, but nostalgia can get the better of the old generation of gamers. Many of you probably don’t even own a working Genesis anymore, but don’t hop on eBay for a used console just yet!

Approximately 380 billion plastic bags are used in the United States every year. That’s more than 1,200 bags per U.S. resident and more than 54 times the number of people who live on the planet. That's why here in Santa Monica, thanks to a city-wide plastic bag ban, you won't find a plastic bag at any of the major retail stores.

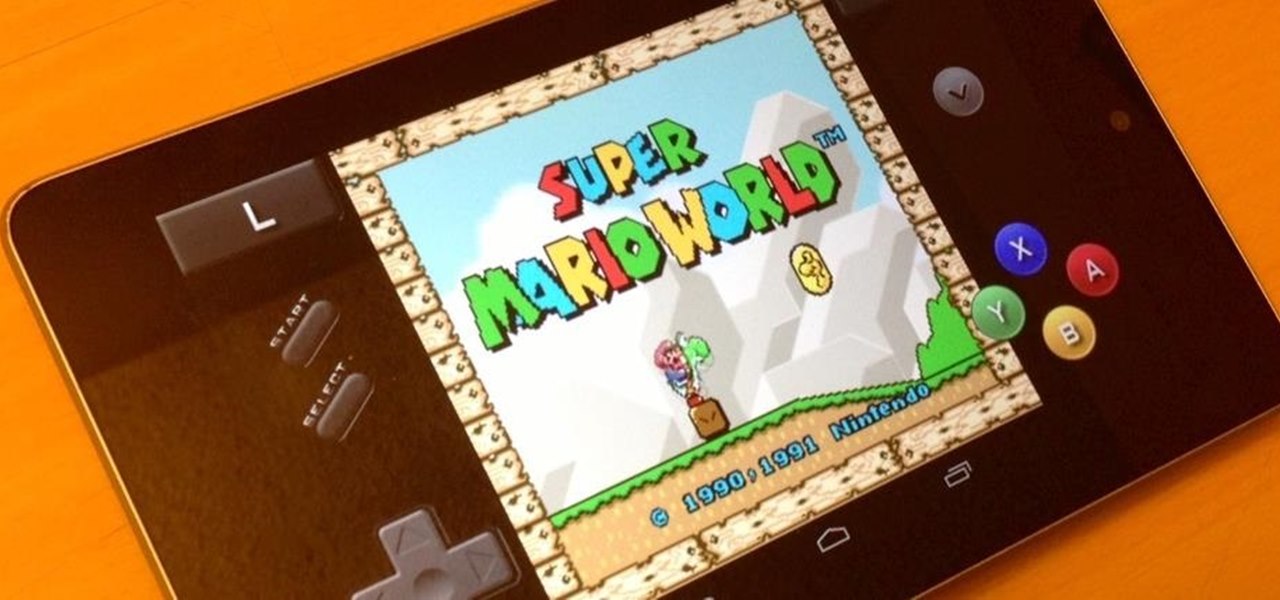
Arcades, Nintendo, Sega, and 16-bit graphics ushered in a new level of gaming that was leaps and bounds ahead of the early Pong days. I remember loading quarters into the machines and playing 2D fighting games until all my money ran out. When I wasn’t in school, you could usually find me at the arcade playing Street Fighter, The King of Fighters and Marvel vs. Capcom. At home, I had my Super Nintendo and Super Mario World keeping me glued to the television until the next boss stage.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Earlier today, a meteorite flew over the Chelyabinsk region of Russia, triggering a shock wave that injured hundreds of people and caused damage to buildings and vehicles in the area. Witnesses describe seeing a bright ball of light streak through the sky followed by a loud boom as the 10-ton meteorite entered the Earth's atmosphere and exploded.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

"Cheating is for losers" is only something that losers like to say. If you want to smash your friends and fly up the leaderboards, though, sometimes you have to go that extra mile.

This may seem like an odd subject, because what do Steampunks and iPhones even have to do with each other? Actually, more than you might think!

Here's how to build a sexy looking water-fuel generator that will convert your tap water into an extremely powerful, clean burning gas!

With how quickly technology evolves in this day and age, it's only natural that people replace their computers every couple years—even sooner. It seems that right when you get a new desktop, there's always a faster model with more features released the following week.

Fairs and festivals are awesome, and one of the best parts about them is the food. Sure, it's all deep-fried and terrible for you, but it's so delicious. It's also always on a stick, which makes eating fried food even easier for us fat Americans.

In this video the tutor shows how to mount ISO's using Power ISO software. To do this follow the simple procedure shown in this video. Download the Power ISO program from the link given in this video and install it. You need to purchase the key to install the software or you can use the key provided in this video. Now restart your computer. After restarting open the software and go to mount ISO at the top right corner. Select the image that you want to be loaded. Finally run the virtual CD dr...

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

At the opening of its virtual Lens Fest, taking place Dec. 8-10 and open to the public, Snap is furthering its facilitation of AR development with new tools for Lens Studio version 3.3 and a planned investment into its AR creator community.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

With a little bit of planning, you can avoid a lot of blood-pressure-raising traffic messes. You Will Need

Take a look at this instructional video and learn how to cause Link to seemingly float around the map in Zelda: A Link to the Past. This effect also allows Link to interact with the environment while he's floating around (slashing monsters, etc. ) The easier way to keep yourself in glitch form without the use of spells is be near the tree so when you are inside the Like Like, talk to the tree and when you are free you get bounced back by the angry tree and during that stun you can let go all ...

Water is an important resource and it needs preservation. Older toilets suck up way more water than necessary, causing both high water bills and pain for the environment. Follow this tutorial, and learn how turn your old toilet into a newer low-flow model.

You don’t need a camera to recreate a picture you see. Choose and object and with only a pen and pencil you can recreate that object as a sketch. Take your time, and choose somewhere quite where you can focus on your creation.

When you start to run out of space in FarmVille, you may want to delete plots to free up some room. It is a simple and quick process that will allow you to better organize your farm down the line.

Want unlimited Tiki power on Island Paradise? Just use Cheat Engine to hack your way to more power. This is only for 1 use only.

Get more money and experience in Fish World with this simple Facebook Fish World cheat using Cheat Engine 5.5. Easy to perform.

Cheat your way up the ladder, higher and higher, with more levels than anyone on Fish World. Using Cheat Engine, this Facebook Fish World cheat will outperform your expectations on leveling up.