Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

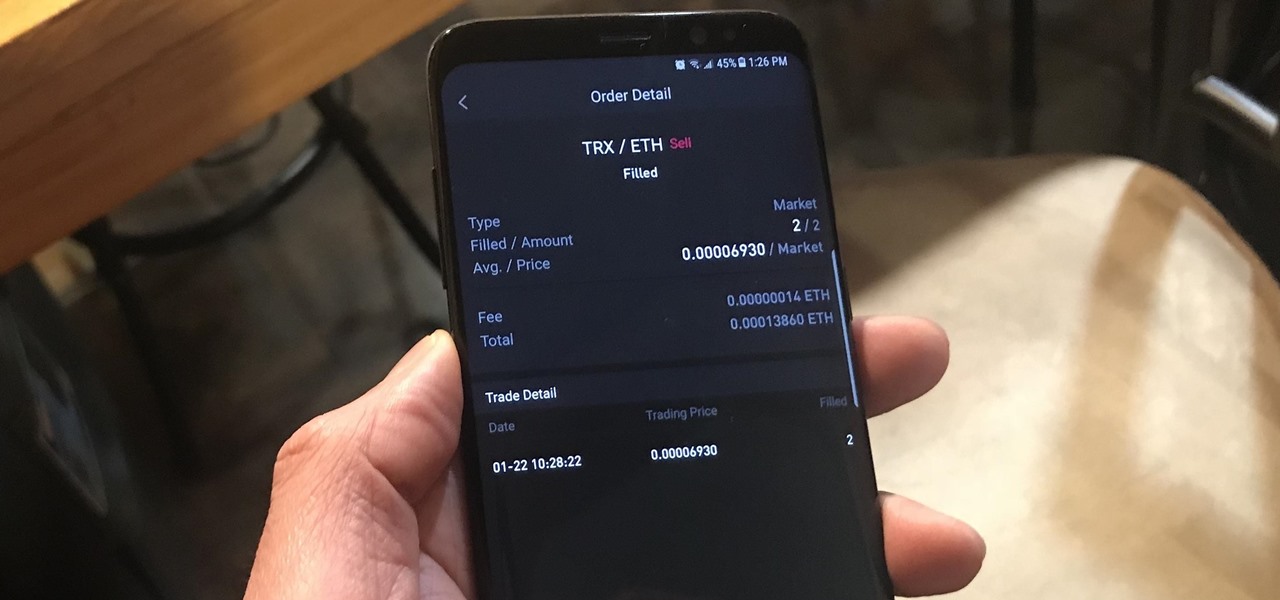
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, he instead decided to deliver a speech to the public about, what else, the future.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

I think I hate this game. I don't really see how you can play more than 15 minutes of Tap Mania without smashing your head into a wall. You do nothing but tap. Tap, tap, tap. At least they got the name right.

Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. When a smaller component like a proximity sensor fails, you're often left with no other choice but to take it to a professional.

In the tech world, when you're a small startup going up against the Goliaths and their massive marketing budgets, you're forced to find and produce something almost magical to help your product stand apart from the rest. And that's exactly what Occipital Inc. has done with their Bridge headset.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

After poor sales of last year's HTC 10 and the terrible reviews their first 2017 flagship received, HTC really needs the HTC U11 to succeed. But they're not taking things lying down, as they've come up with some interesting tech for their latest handset.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

If your iPhone has a Home button, such as either iPhone SE model, old or new, then it has a secret triple-click gesture to activate a suite of shortcuts. These options, dubbed accessibility shortcuts, can work wonders for folks that are hearing impaired, have limited use of their hands, or have vision problems. Still, the shortcuts have plenty of everyday applications that everyone should know.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

There was lots of new tech to check out at CES 2016, but you could argue that the majority of the big-ticket items weren't the most unique things in the world. Thankfully, there were a few innovative, unconventional ideas on display, and here are some of our favorites.

The stock Camera and Photos apps are great for taking basic pictures and doing some quick edits, but if you're serious about making your iPhone photos the best they can be, you can't stop there.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

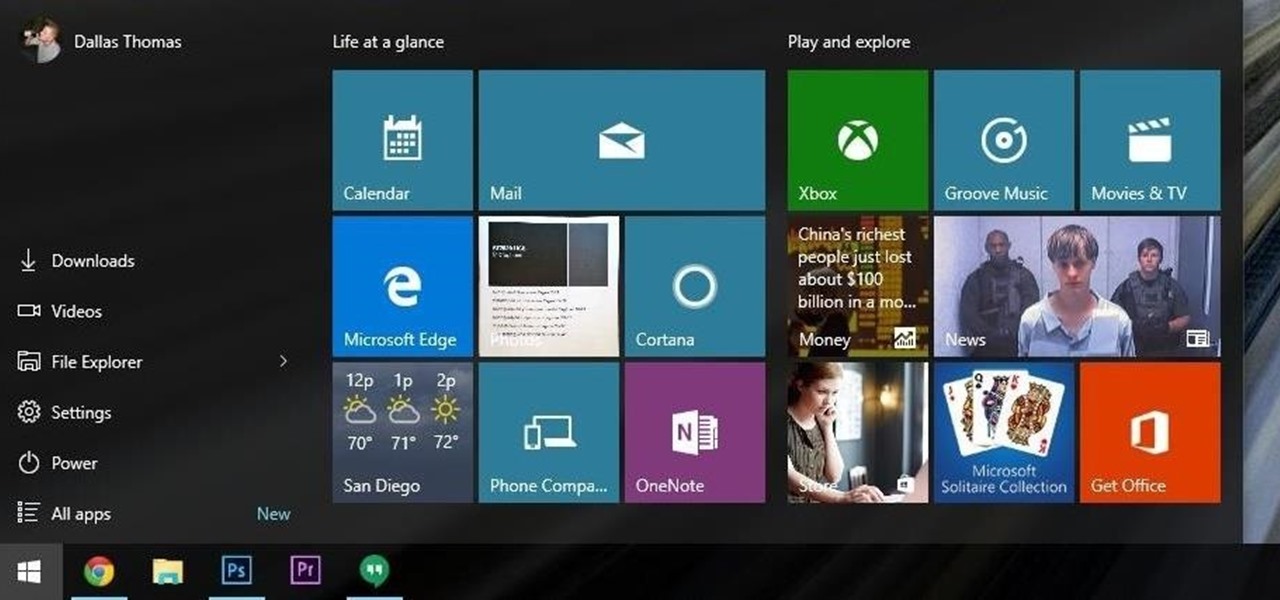
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.