It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Holographic technology has made a push towards becoming a reality for everyday consumers, most recently with the introduction of the Microsoft's HoloLens, which combines real-world and virtual elements in one awesome device.
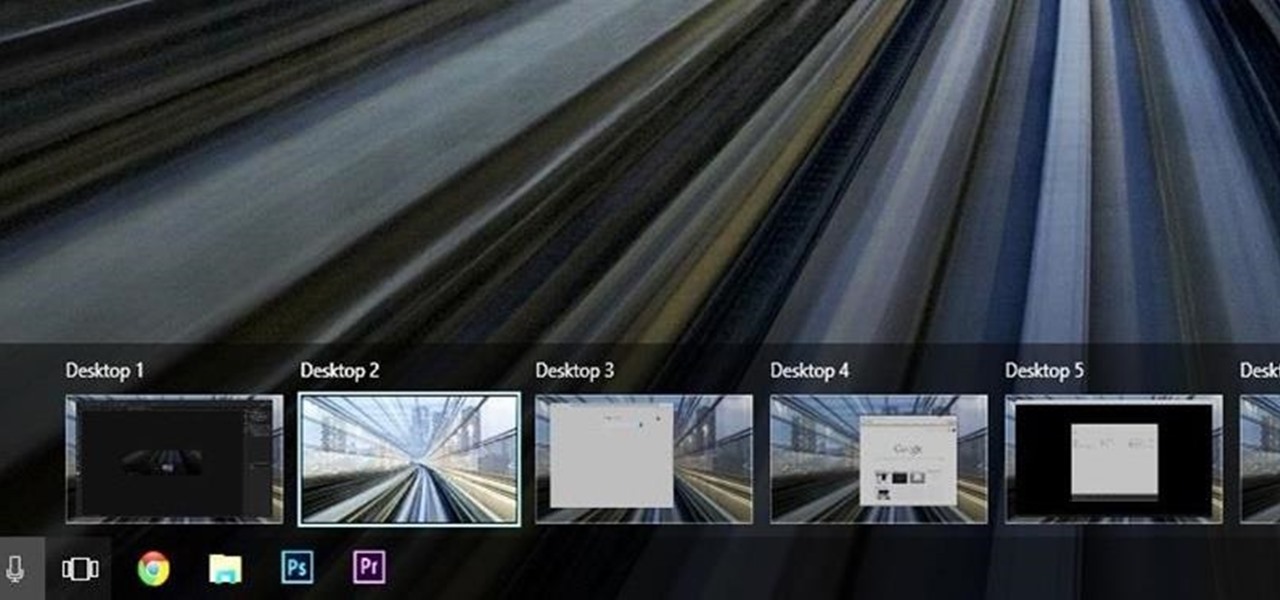
Linux and Mac users have long enjoyed the use of multiple virtual desktops to free up clutter on their home screen and keep individual workflow environments separated, but Windows users have always been stuck with one solitary desktop.
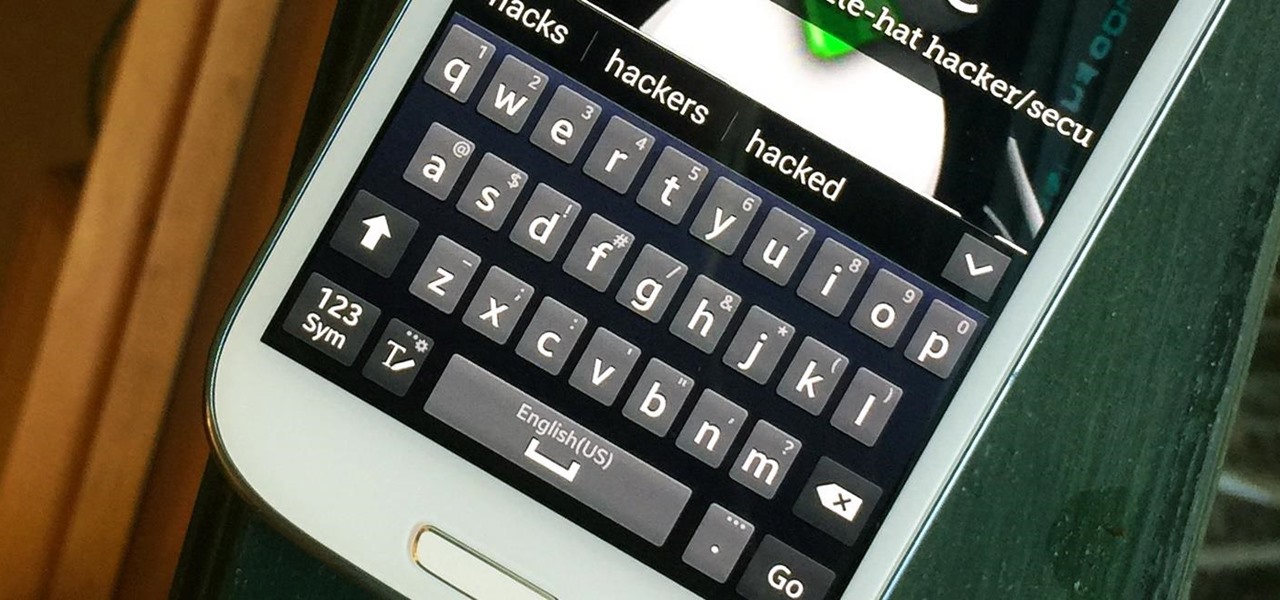
Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image as intended.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

It's late and dark, I'm playing Dying Light, and, admittedly, I'm a little creeped out. Working as a grown man's night-light, this is one instance where I actually appreciate the light bar on my PlayStation 4's DualShock controller. But outside of a few particular instances, I generally find it to be quite a nuisance.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

Samsung's Gear VR headset is a thing of beauty; unfortunately, it only works with the Samsung Galaxy Note 4. That's where ImmersiON-VRelia's Head-Mounted Displays come in to play. With four different HMD models, we got a hands-on look at "The Go," which is not only affordable (at $125), but also compatible with the majority of Android and iOS devices.

Minecraft is a simple game with a huge following, and is a great inspiration for easy, DIY Halloween costumes. We've already shown you guys how to make a Simple Steve costume and a Creeper costume—now it's time for a new Minecraft-inspired one.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

Mobile gaming, in case you haven't noticed, is huge. From the astronomical popularity of Candy Crush Saga, to the ease of using old school emulators, we love gaming on our mobile devices. The future is also bright, just take a look at the Oculus Rift, an immersive virtual world that just might change the way we view and play games.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

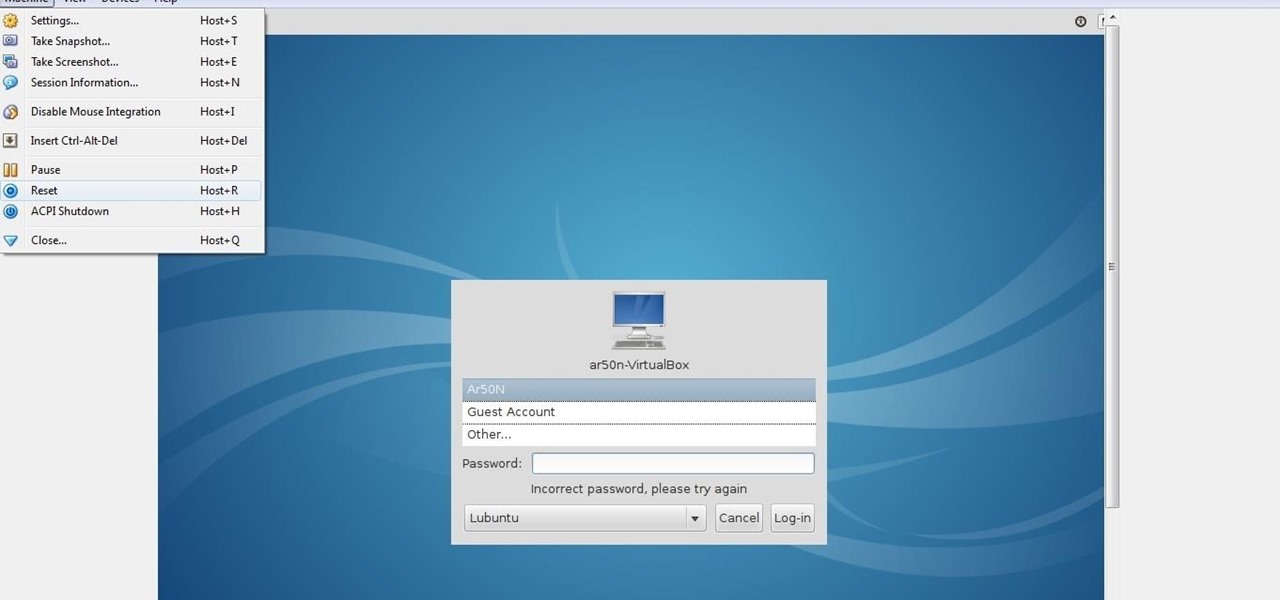
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

I've had this idea in my head for almost a year now. I knew what I wanted to do, but wasn't sure if it would work. After a long time of armchair-engineering, I decided that the best way to test my idea was with a soldering iron and a screwdriver.

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

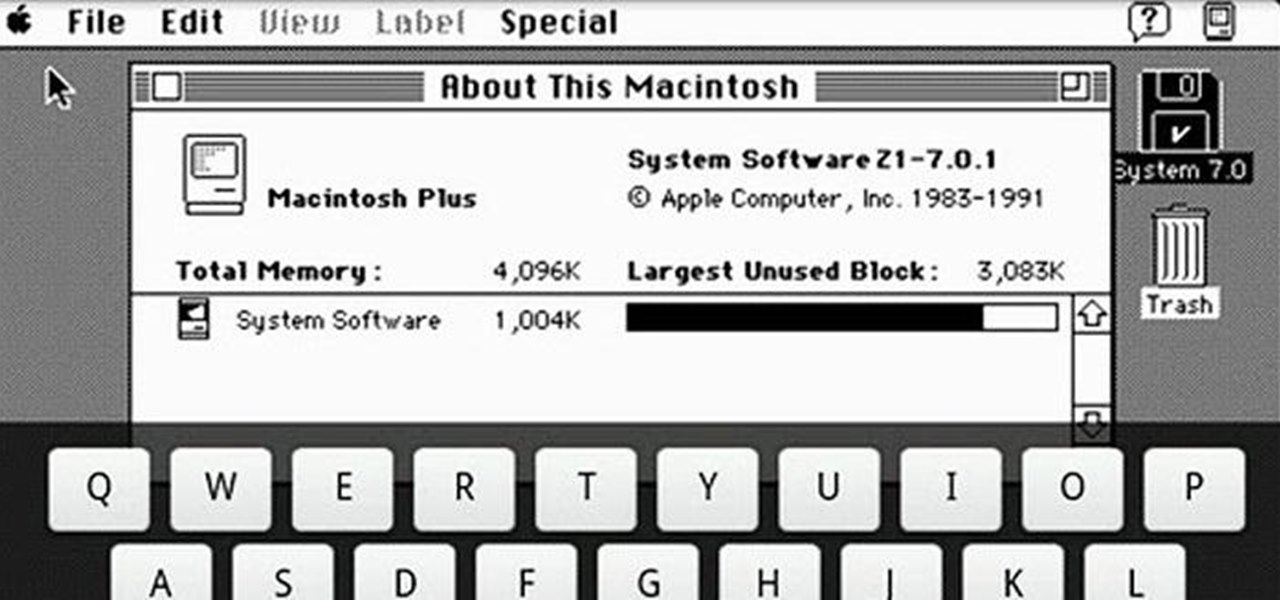
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

Google has just launched a new revolutionary augmented reality game for Android called Ingress. Their new mobile game centers around the fight for control of the minds of everyone here on Earth. It's a freaking worldwide fight—from your smartphone! While augmented reality in is nothing new in the smartphone gaming world, it has never seen the likes of this. With an almost Halo-like storytelling, Ingress seeks to bring out gamers all across the globe to perform physical activities by transform...

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

The Lens Studio community, now made up of more than 200,000 creators, has generated some impressive augmented reality effects in the last few years. Amazingly, the groundbreaking Lenses for Snapchat continue to come, often from the internal AR team at Snap.

The surging activity in augmented reality in both the business and consumer sectors is being matched with a wealth of updates and partnerships from Snap Inc.

For most mainstream users, LiDAR sensors for precision depth sensing remain the exclusive domain of Apple iPhones and iPads, but Google is helping Android device makers close the depth gap on the software side via its ARCore toolkit.

Snapchat's first foray into augmented reality started with the selfie camera and face-tracking technology, with the app's AR capabilities expanding from there.

Two years ago, the 50th anniversary of the moon landing gave flight to a handful of Apollo 11 augmented reality apps and experiences, including one from the Smithsonian Channel.

The team over at Spatial isn't done innovating its way through augmented reality in 2020. Just days after adding a mobile option to its groundbreaking Spatial virtual collaboration product, the company is releasing Tele, a new app geared toward more casual, AR-powered video chats.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.