I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

When I first started cooking, there were a few steps I always skipped in recipes. I never added zest to anything because it seemed like too much trouble, I rarely separated wet and dry ingredients in baking recipes because I was lazy, and I never let meat rest after it was done.

Update: May 7, 2014: Google's Camera has seen its first update, with a small yet important addition baked into the app—the ability to take pictures while recording a video. Now, when in video mode, simply tap on the screen to take a picture, while your recording continues as normal. The update to version 2.1.042 is set to hit today, but if you haven't yet received it, apply it manually by downloading the apk here.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.

It's about that time again: Facebook has announced the dates for its annual Facebook Connect (formerly known as Oculus Connect until last year).

We always know roughly when Apple events are coming, but when their new product events pop up, they're always a pleasant tech refresher from the Cupertino tech giant.

Since the start of the COVID-19 pandemic, Google has packed new functionality into Google Meet to compete with Zoom, Microsoft Teams, and other video conferencing platforms.

Many years ago, when I first traveled to Tokyo, Japan, I was amazed by the contactless IC card turnstiles embedded in the county's subway system.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Last week, Snap powered through a mountain of important software and (shock!) hardware updates, as well as a few very big business partnerships.

Android's open source nature means it gets modified quite a bit. First, the phone manufacturer will add their customizations, then your carrier will add even more on top of that. Between the two, someone almost always adds a startup sound so that you and everyone around you will hear their jingle every time your phone reboots.

During the Tuesday launch of Google I/O, the company's CEO, Sundar Pichai, pulled off a Steve Jobsian "one more thing" move near the end of his keynote address that was simply stunning.

Ever since the debut of the LiDAR Scanner in the latest batch of Apple's iPhones and iPads, the questions have swirled as to how this would benefit augmented reality interactions.

Who had Lil Nas X, blood-drop Nikes, and satan worship on your 2021 bingo card? In a story that's stranger than fiction, the "Old Town Road" rapper has ruffled some feathers with the video for his new single, "MONTERO (Call Me By Your Name)" filled with demonic imagery usually reserved for death metal bands.

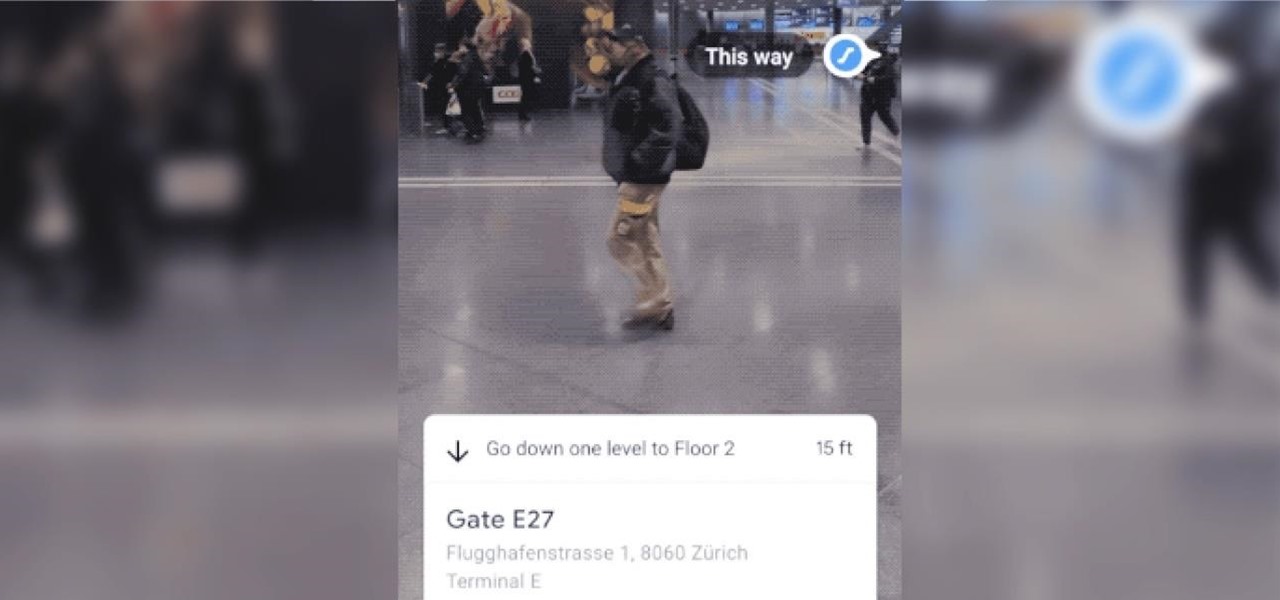
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

Even as the world continues to grapple with the pandemic, the tech industry continues to chug along, with some looking for ways to present new products, and in some cases continue major conferences that reveal the latest in augmented reality developments.

Since launching its web-based AR platform in 2018, 8th Wall has continued to push the boundaries of what brands can do with AR experiences outside of native apps.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

The movie theater business is hurting due to the pandemic, but that hurdle is actually the perfect set of circumstances for movie studios to lean hard into augmented reality marketing.

With the new season of The Mandalorian underway, Google has launched a new AR app that enables some Star Wars fans to connect with virtual characters in between new episodes.

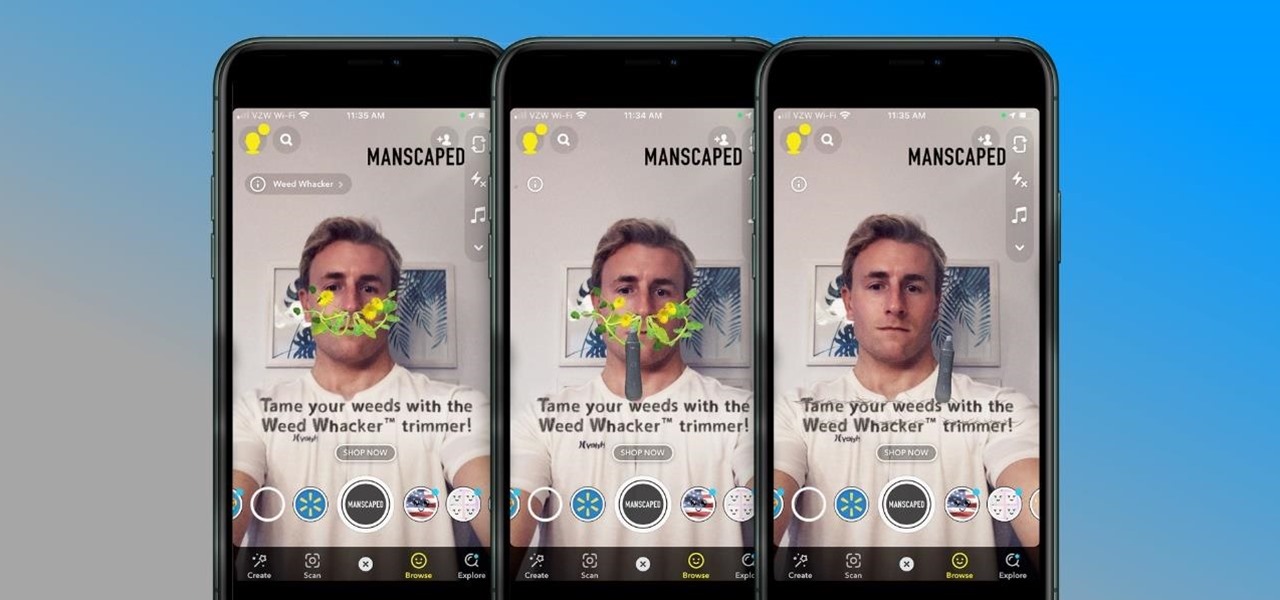
If you're a man and subscribe to podcasts or YouTube channels that cater to masculine interests, then you've almost certainly encountered sponsorships from Manscaped. And that means I don't have to explain what the company is selling you (for the uninitiated, it's a company dedicated to helping you trim your body hair—most notably, your nether regions, in addition to other areas).

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.