How To: Install Android OS on a PC Using VirtualBox.
Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.


Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.
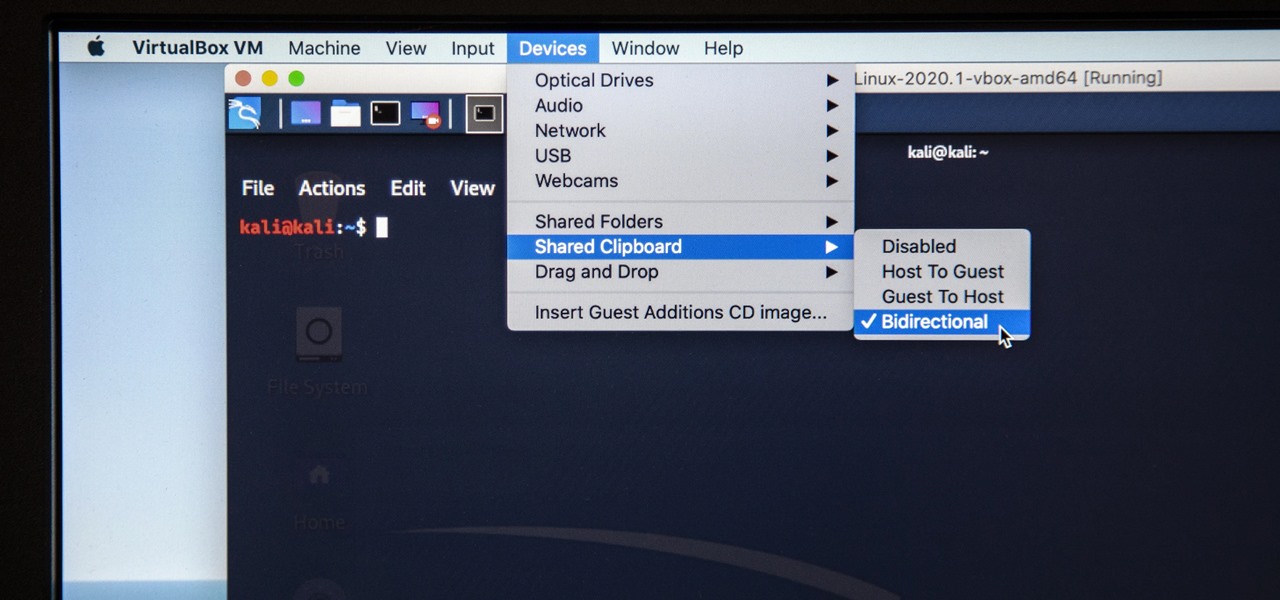
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

If you want to run Windows 8 inside of Windows 7 so that you can give the Windows 8 Developer Preview a try, take a look at this guide on how to run Windows 8 inside of VirtualBox. This will allow you to run Windows 8 within a virtual machine.
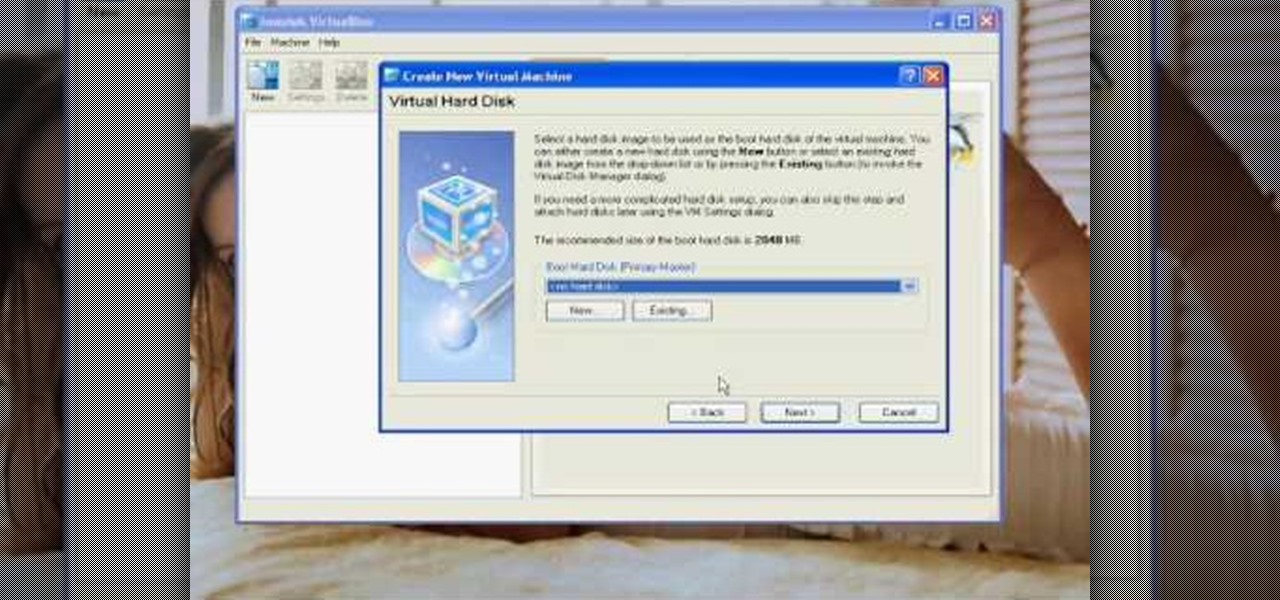
The author shows how to install Puppu Linux 4.3.1 in Innotek VirtualBox 1.5.2. He shows steps to create a new virtual machine in Innotek VirtualBox, by showing the various configuration settings like the RAM size, hard disk space etc. He shows how to boot the virtual machine with the Puppy Linux installation ISO file. Next, during boot up, he shows how to set the language and regional settings, resolution settings etc. In the next screen he shows how to access the local drive and partition it...

Want to know how to hide the Menu and Status Bars in VirtualBox? It's easier than you'd think! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, take a look.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to enable USB support in VirtualBox on Ubuntu Linux.
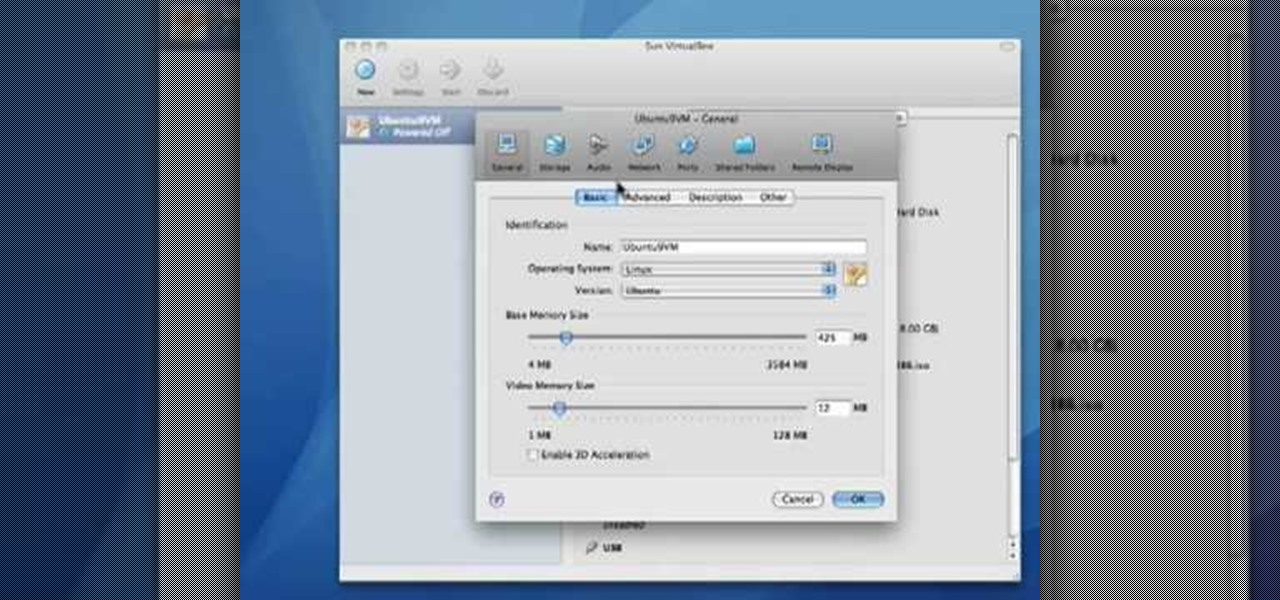
Before you can alter the settings of a virtual machine, you must first have the machine powered off. Load VirtualBox on your Mac desktop and make sure it is powered off on the left hand panel. Double-click General and a window should pop up allowing the changing of several settings. For example, you can include a description to keep many virtual machines separate, or adjust the size of the drive. You can even add virtual devices through ports if they are connected to the physical machine. The...

Can't decide if you prefer Windows or Mac OS X Snow Leopard? You don't have to! Check out this video to learn how to use Virtualbox to install Mac OS X on your PC. Follow all of the instructions in the video.

In this clip, you'll learn how to install Microsoft Windows 7 on a virtual machine with VirtualBox. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to update Nokia firmware via VirtualBox on Ubuntu Linux.
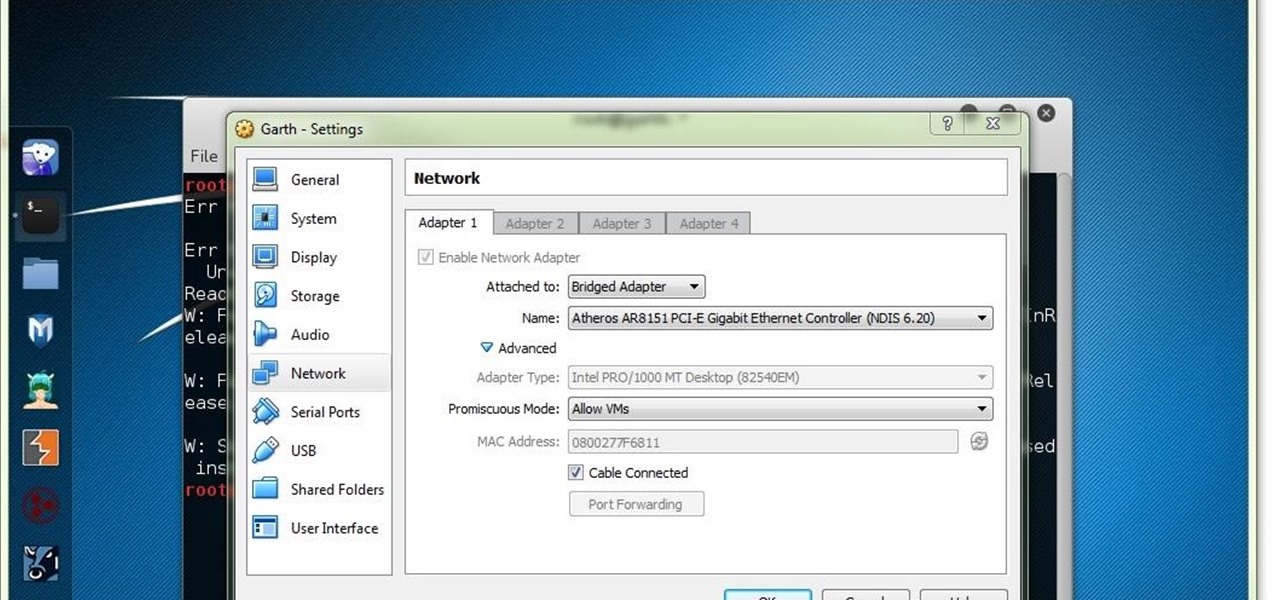
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

Things You'll Need A fully working operating system that supports VirtualBox (Windows, OS X, Linux or Solaris)

Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.

With the computer's rapid increases in power and efficiency, computer virtualization has taken the scene by storm. With virtualization software, and powerful enough computer hardware, your computer can run a virtual computer within itself. This effectively gives you multiple OS's on the host OS. This can be used for a lot of cool stuff that your computer would normally be limited by. Let's take a look at a few.

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.
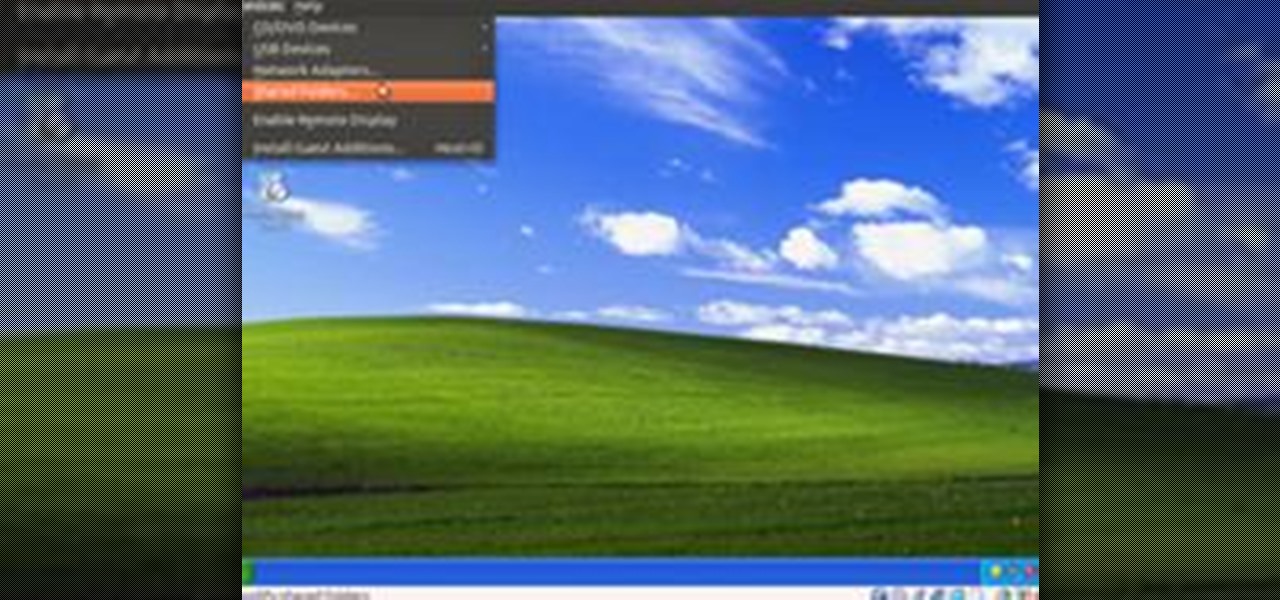
There are several virtual machine managers present in the market. However, the main functionality of all VMs are the same. Most people like to get free VM managers, so that they can install as many operating systems as they like over the host operating systems. One of these free VM managers is Oracle's VM VirtualBox, which can be downloaded from Oracle's website for all popular operating systems, such as Linux, Windows and Mac.
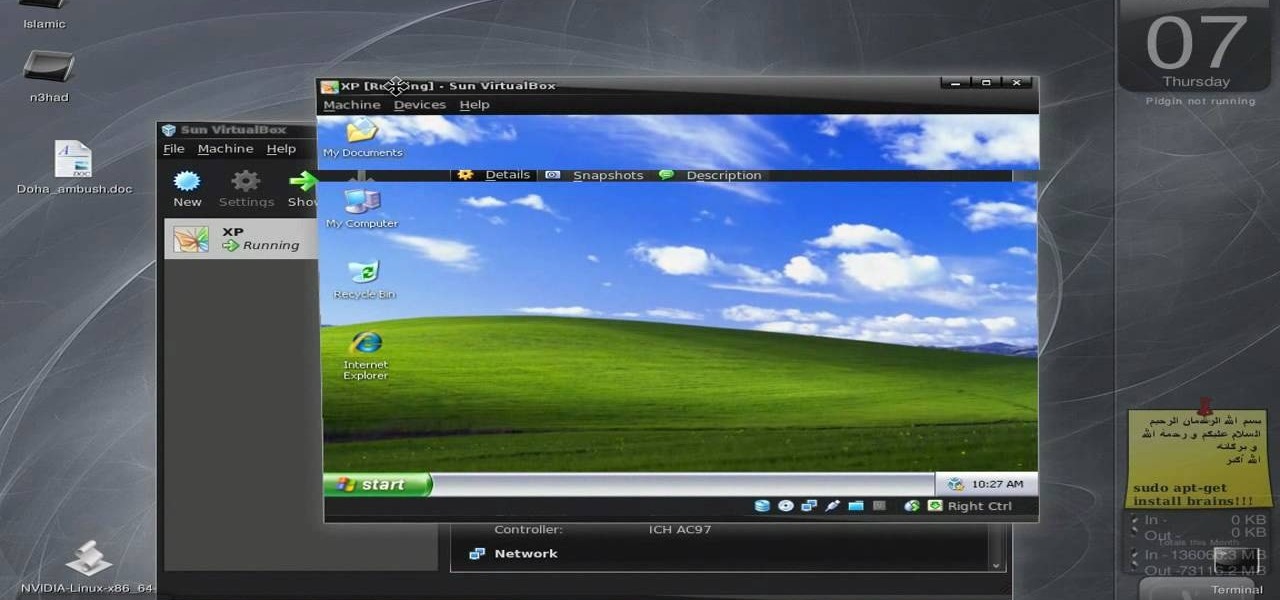
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to share files between Ubuntu (Host) & XP (Guest).

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.
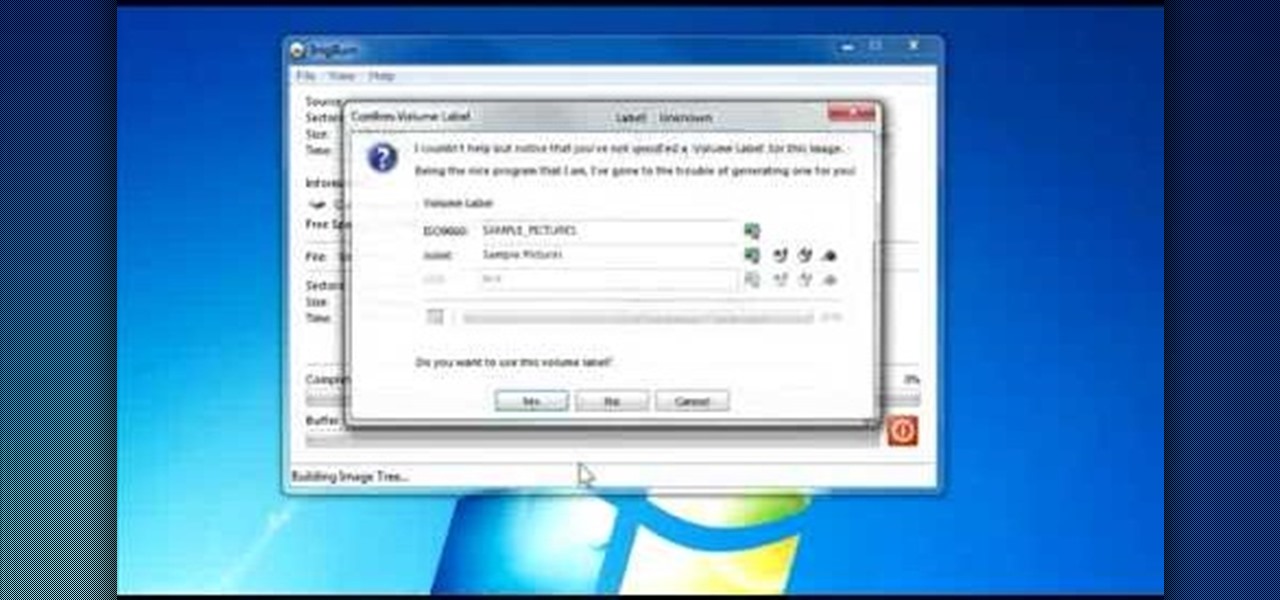
Download the software from Imgburn. Choose mode, build, advanced, bootable disk. Go to allbootdisk to get a bootable image of your operating system. Choose from Windows 95 through Vista. Download the diskette image. Name and save to desktop. Choose volume and label. Click ok. Make the output burn to image file. Name the file and save it to the desktop. Download Sun Virtualbox. Test the image by choosing settings, storage, add device. Choose media manager. Select make primary slave. After test...
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to update Nokia firmware via VirtualBox on Ubuntu Linux.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.