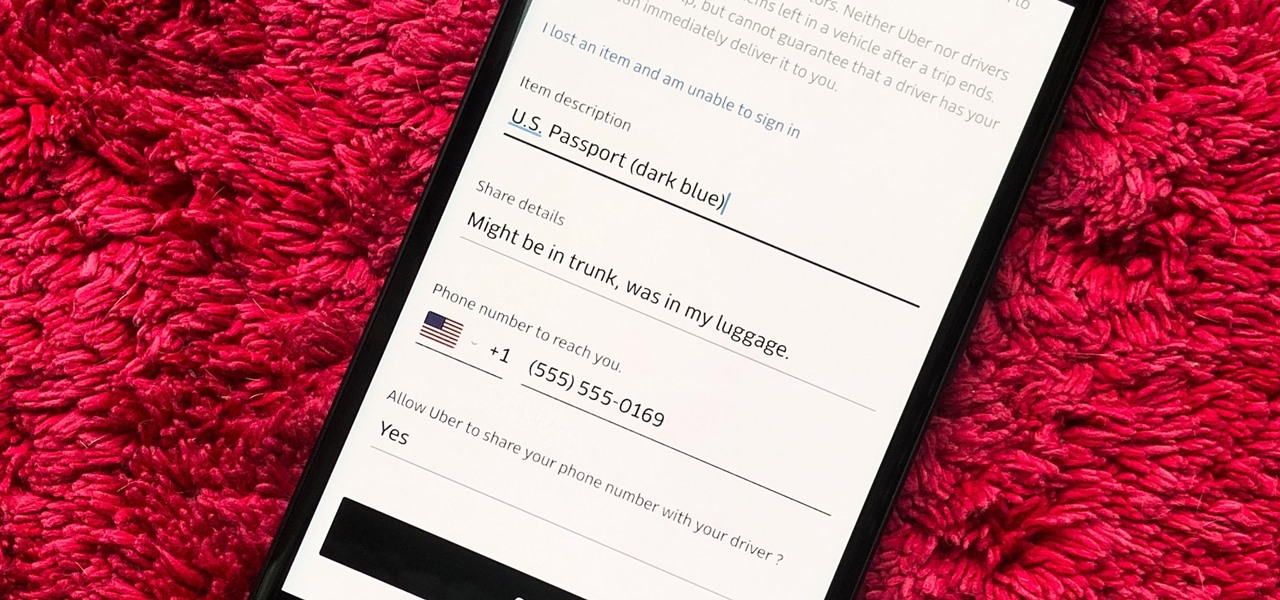
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

In recent years, many software publishers have tried to sell the business community on remote meetings via VR, but if social media chatter is any indication, it hasn't taken off in a big way just yet. However, for some, the notion of holding remote meetings using augmented reality, a medium in which you're still directly tied to the real world and not closed off in a blindfold-style VR headset, might be the better solution.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

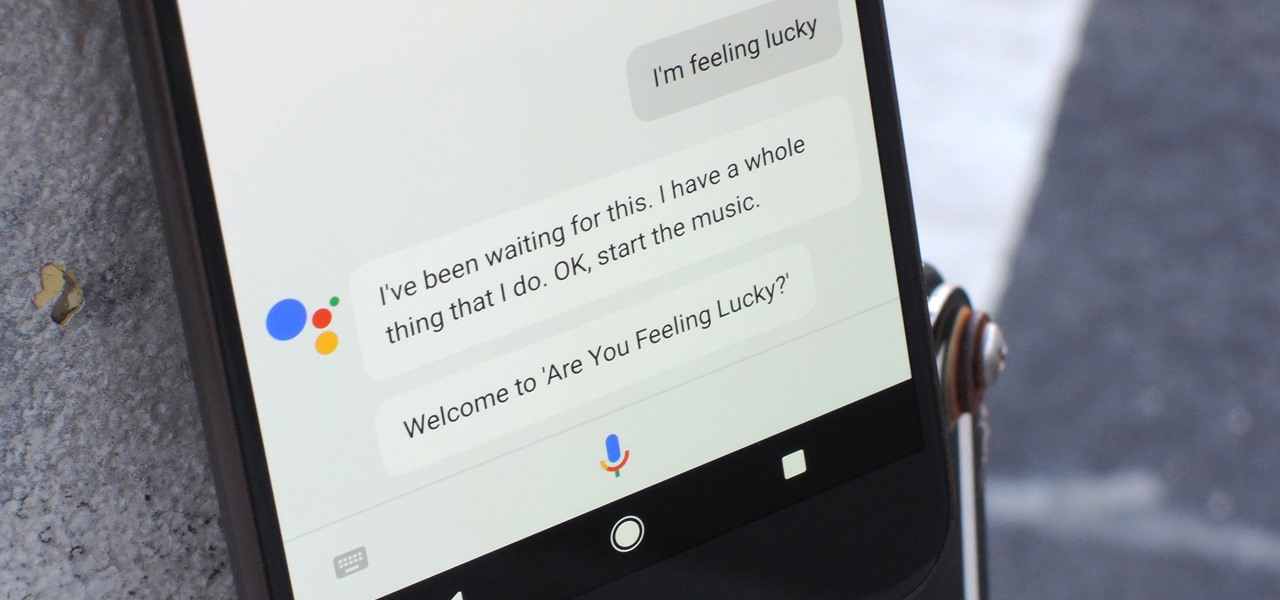
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Once upon a time in America, there was coffee and there was decaf. That's it. No capuccinos. No espressos. And certainly no Starbucks. Coffee was just coffee, something that you bought at a gas station or donut shop. If you made it at home, it was either in a metal pot or instant coffee.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

The latest 17.4 update for Safari includes a prompt for EU users to choose a different default web browser available in their region. It also gives us new ways to customize the Favorites Bar on an iPad. And Apple Cash virtual numbers are now supported as an AutoFill suggestion. But there are also some hidden changes in Safari 17.4 for iOS and iPadOS that you might not ever notice unless you keep reading.

In our review of Amazon's non-augmented reality Echo Frames smartglasses, we made the case for audio virtual assistants being the linchpin for AR wearables.

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.

This week, Google showed off some wild new and innovative AR experiences that showcase the WebXR protocol for browser-based AR content, while 8th Wall applied its own web-based AR platform in service of Captain Morgan.

While the new Google TV interface and its ability to run apps are the scene-stealers of the new Chromecast, Google's new hardware has many of the same hallmarks of its predecessors.

I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

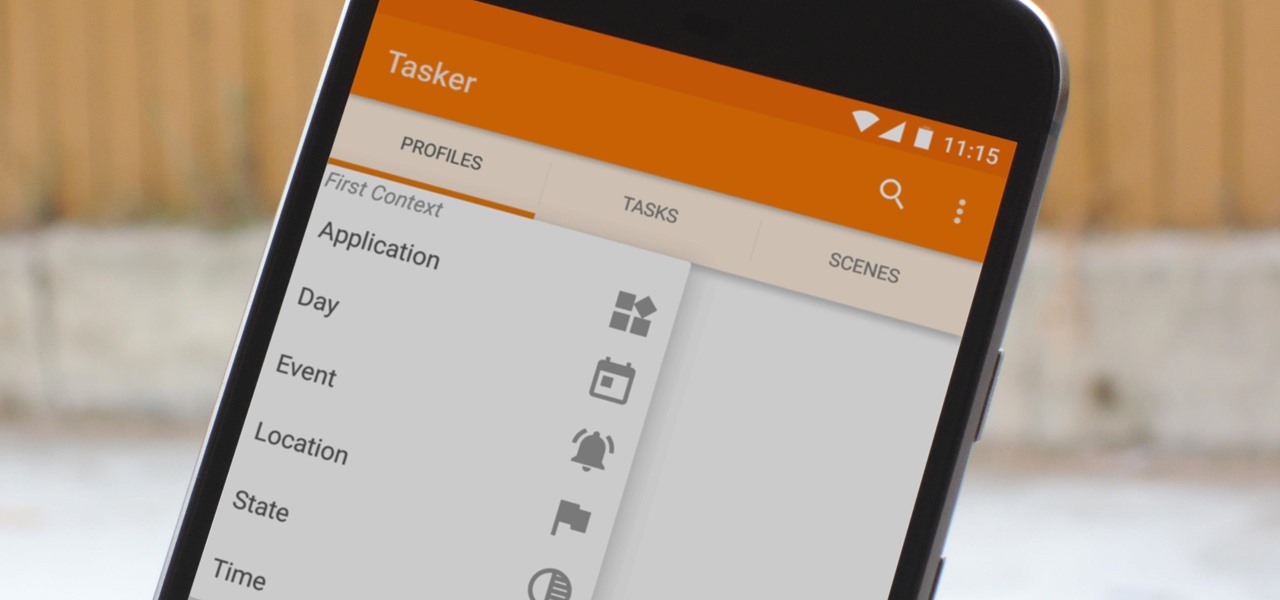
When you hear people say that Android is more flexible than iOS, it's because of things like Tasker. You can do virtually anything with the venerable automation tool, from saving battery life to controlling your smart home with your fingerprint. But before you get to that, you'll need a good understanding of all the basics.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

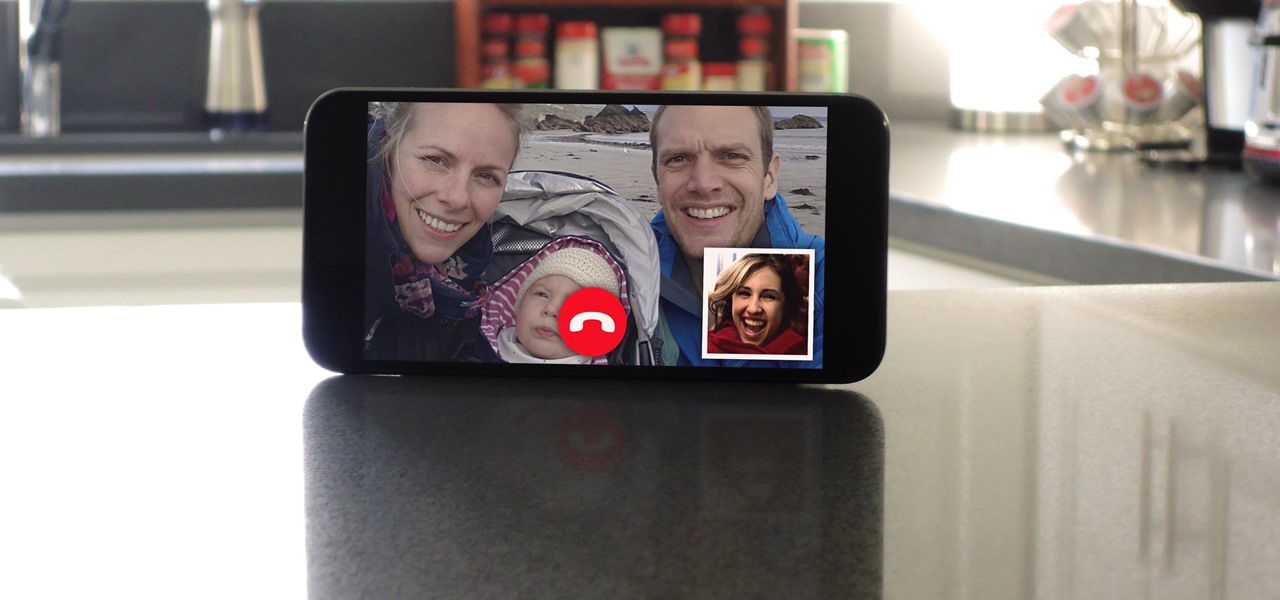
Video chatting has become an important factor in the overall smartphone experience. Even just a few years ago, 37% of teens were making video calls on a regular basis, and that number has surely grown. 85% of households with infants have used video chat apps to call relatives in other cities, and it's been shown that toddlers can create bonds and learn from visual cues in video calls.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

Thousands of emoji are available on iPhone, iPad, and Mac, and you can use these in many of the apps you have installed on your Apple devices. But there's one emoji you'll likely never see on any of Apple's official emoji keyboards, and its absence may surprise you at first, considering it's embedded in virtually every Apple product. That emoji is, of course, the Apple logo icon.

For the avid multitasker, listening to audiobooks and podcasts is the ultimate way to passively absorb knowledge while performing other activities — but there are other options. You can turn any written text on your Android phone into speech that's read aloud to you, so there's virtually no limit on what you can soak up audibly from your headphones or speaker.

While Snap may eventually compete with Apple and Samsung in selling smartglasses to consumers, today it is helping them achieve their business objectives via augmented reality.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

We're still awaiting the arrival of consumer-grade AR smartglasses from the likes of Apple and Facebook. But that doesn't mean there aren't AR products out there to try this holiday season.

There's a variety of brilliant colors in the iPhone 12 lineup, including the elegant Gold and show-stealing Pacific Blue finishes on the Pro models. It's difficult enough to choose an iPhone color as a customer, but deciding on accessories can make things even worse. Which color case looks best with what iPhone color? What about a MagSafe wallet attachment? Well, Apple has a tool to help you figure that all out.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.