Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Pumpkin carving and decorating is a favorite October pastime. After you've carved an amazing design or face into a pumpkin or two, you want to show it off through your window or set it out on your porch for the neighbors to see.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

As unappealing as it sounds, transplants with fecal material from healthy donors help treat tough Clostridium difficile gastrointestinal infections. Researchers credit the treatment's success to its ability to restore a healthy bacterial balance to the bowels, and new research has shown that the transplanted bacteria doesn't just do its job and leave. The good fecal bacteria and its benefits can persist for years.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

Getting spammed or too many viruses? This trick will protect your computer from websites trying to access or corrupt it.

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this tutorial helps you learn to use uTorrent.

Follow Monty Don's video advice on pruning shrub roses, including techniques that will keep fungal infection and viruses at bay, while encouraging flowering stems.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

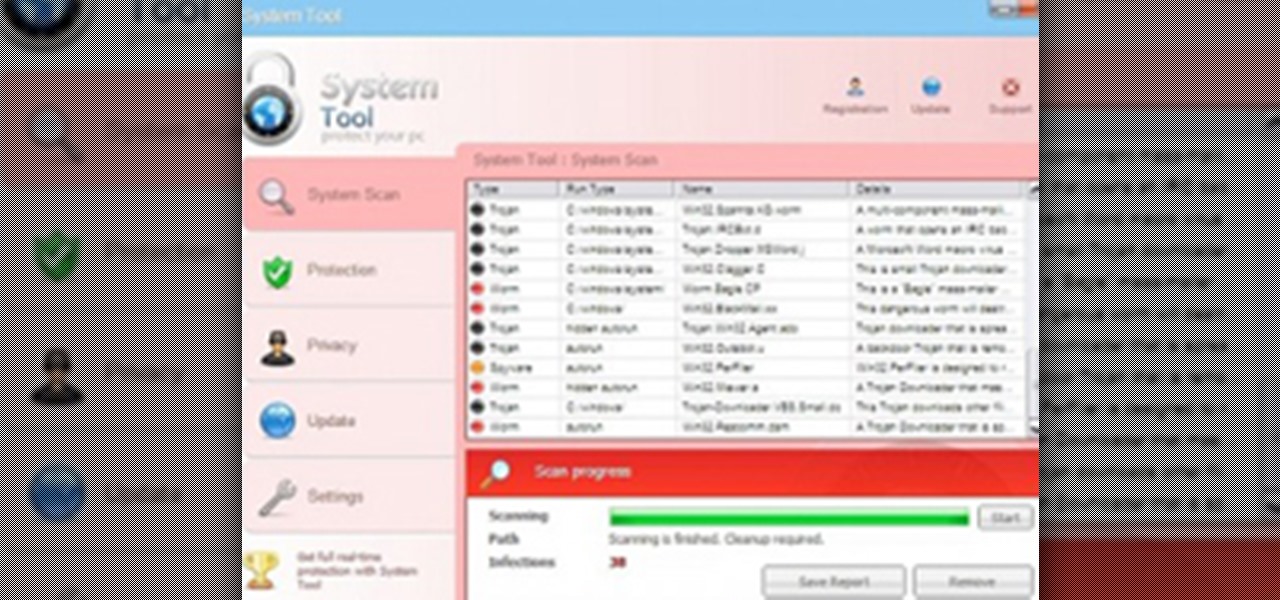
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

Learn how to care for canna plants with Carol Klein's comprehensive video guide covering planting, overwintering, and dealing with viruses such as canna yellow mottle, and bean yellow mosaic.

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.
Enter the dark and surreal world of Cyborg Virus. Use your hook-shot and electrifying abilities to defeat cybernetic viruses at the molecular level! Also features an online high score board. Do you have what it takes to defeat the main virus and save humanity?

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Merry Christmas all! I hope you are all having a very wonderful day!

Scrabble Bingo of the Day: MIASMIC [adj] Miasmic is an adjective for miasm (or miasma), which means a noxious vapor—"bad air" harmful to health. The word miasma comes from the ancient Greek word for pollution. And the concept of bad air also gave rise to the name malaria, from old Italian "mala" (bad) "aria" (air).

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...