Tinder, marketed as a free 'dating' app, is no stranger to paid features. The company has long allowed users to step up their game by spending money on their 'Tinder Plus' service. Tinder would like more of your money, it seems, as it rolls out a new paid service with a highly-desirable premium feature — the ability to see who has swiped right on your profile, without having to match.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

Australia is looking to the future and finding driverless cars and other autonomous vehicles to be a top priority. Spacial Source reports that the state government has put AU$10 million into their Future Mobility Land Fund "to drive local development of autonomous vehicle technology."
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

How many times have you thrown out the remaining cardboard tube from an empty roll of toilet paper? Most of the time, they don't even make it to the recycling bin, and with the average American using over 20 rolls each per year, that's over 6.4 trillion tubes being wasted each year. Yet these small tubes are particularly valuable helpers around the home, especially when it comes to cleaning, so why toss them out?

I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

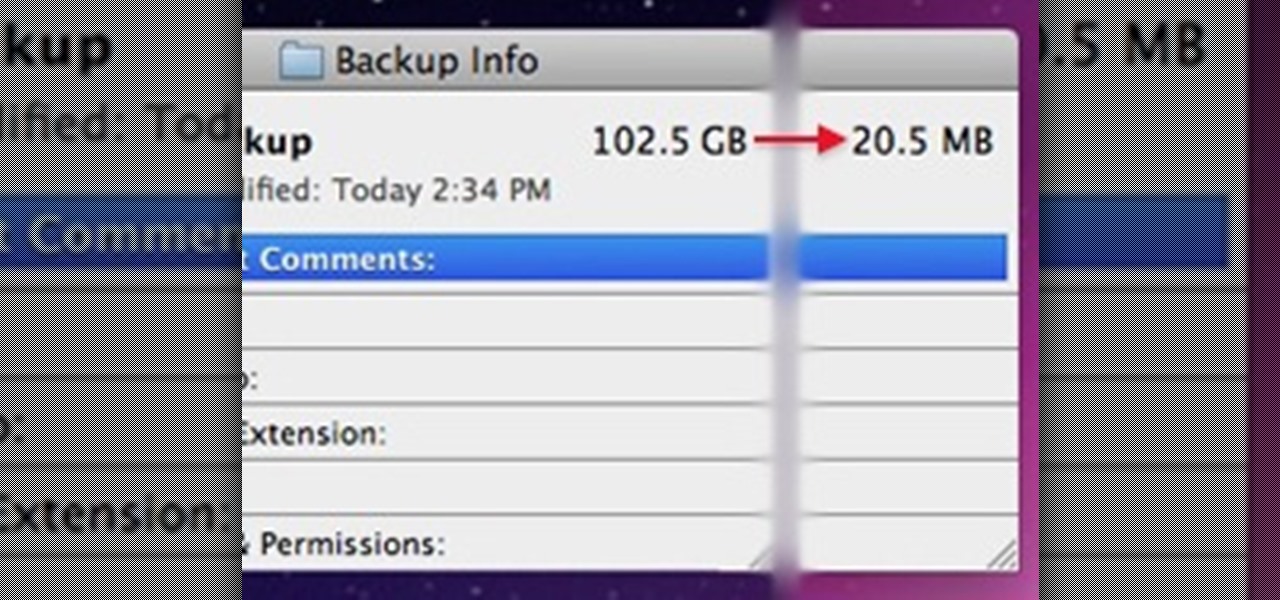
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

Going to the doctor can be an unsettling event for any child. This program is about preparing your toddler for a visit to the doctor.

Speech recognition software made it easy to search Google on your smartphone, and Google Goggles made it easy to find answers from camera snapshots on your device. But now Google's bringing similar technology straight to your desktop, and with faster results—faster than Google Instant.

¤¤ TRAVEL TIPS TO VISIT SIEM REAP ANGKOR WAT (CAMBODIA) IN ONLY 2 DAYS¤¤ How to visit and what to see in a short time in this popular resort town as the gateway to Angkor Temples, cultural villages and authentic old markets.

Learn how to visit the world's largest fish market in Tokyo, Japan named Tsukiji. Follow along as you learn what to wear, what to watch out for, and most importantly, how to get the best sushi you'll ever eat. Visit the world's largest fish market.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

If you've ever seen me glued to my iPhone, huddled on the corner of the 23rd St subway station fidgeting with my stupid hot pink nails trying to Instagram Story, then now you are about to find out exactly what I've been doing.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

How to pick plants and trees at a nursery

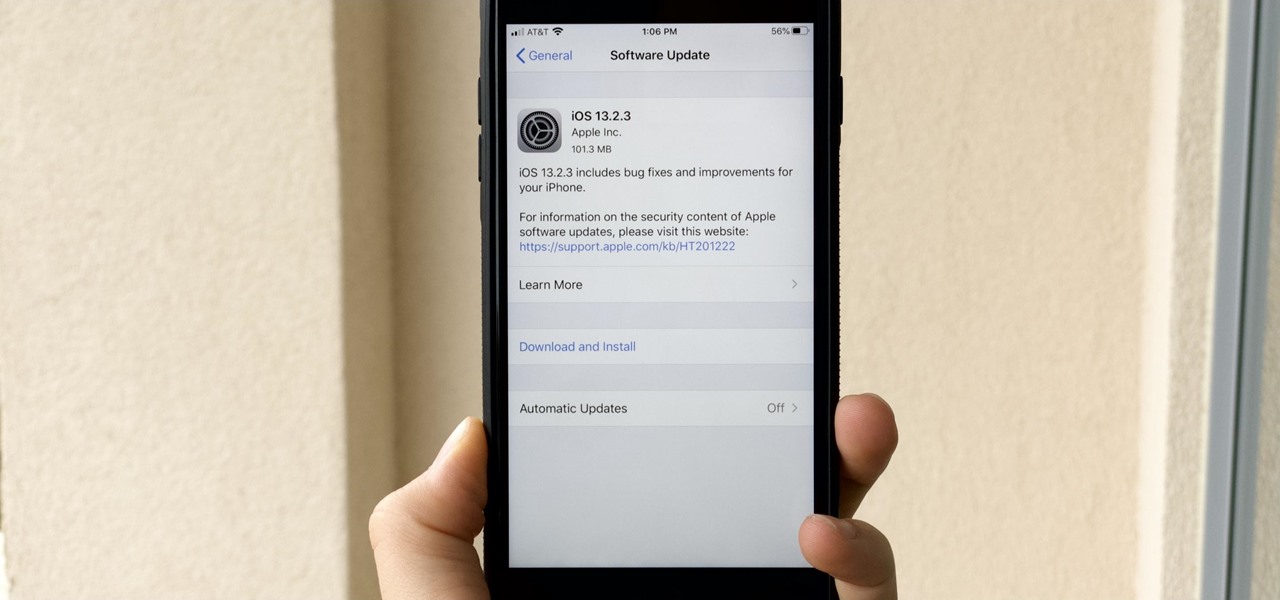
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

You've seen it in action before, but now it's finally got a solid release date, well... release month.

Popups citing every little detail of your friends' online lives get pretty bothersome, but you can actually learn how to make them beneficial - and profitable - for yourself by watching this video on hacking Frontierville (06/19/10). You'll learn how to use the popups (the publish screen) to stop the bonuses from fading while you're visiting neighbors for maximum coins.

YouTube is a great video service because it's free and has invaded the world… meaning, practically everybody has been on YouTube at one point or another. Another great aspect of YouTube is the ability to embed content on your website or blog… like your WordPress blog. You can also embed full YouTube playlists. This video will show you the steps to embedding YouTube playlists on your WordPress blog, and the principles can be applied for other sites as well.

Long term power outages can be an inconvenience. It means that you no longer can heat or cool things. This how to video talks about how to protect your home from a long term power outage, or how to protect your valuables from power loss with a generator.

Learn how to adjust the brakes on your bike. This information is valuable to teach you how to do maintenance on your bike by yourself.

In this "Quick Clip," I tried dunking inflated balloons into a container filled with liquid nitrogen until they were completely flattened and seemingly destroyed. Once out of the liquid nitrogen, the balloons come back to life and reinflate on their own—without even touching them!

Sure, "normal" is cozy and safe, like a glass of warm milk before bed. It gets the job done, but there's no pizzazz, no flair. We wake up, slug back some okay coffee (not good, certainly not great, but just okay), and we're shunted off to a gray cubicle in a gray building. Sure, we can't all be stuntmen and rock stars, but there is a way to inject a little zip into your day.

Disk space is a valuable commodity on your PC, and if you're running low, it's time to sell some of that unneeded property! This video shows you the steps to freeing up space on the hard drive of your Windows XP or Vista computer. There are many areas in Windows from which you can delete temporary files and hence, decrease your overall disk usage.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

1. To start a blog pick a topic on which you want to create your blog. 2. Select a blog software or platform where you can work like word press.

The SubStream's "Film Lab" provides valuable information for filmmakers, specifically cinematographers and gaffers, on how to use neutral density gels.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

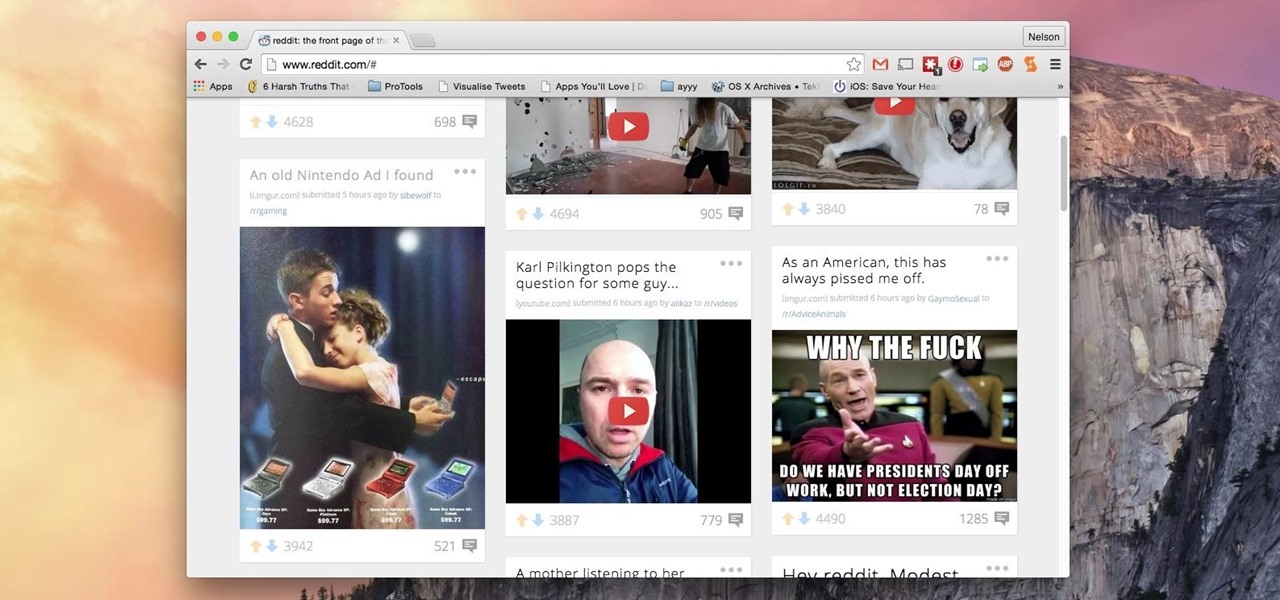
Reddit's overall design has stayed relatively unchanged for as long as I can remember. It's easy to use and is as popular as ever, so why mess with a good thing, right? Well, everyone's different, and if you're looking for ways to beef up your Reddit experience, try out the Chrome extension SHINE.

Parties are a great way to celebrate and have fun with your good friends, so to make sure your next party rocks, I've assembled some of the biggest life-hackers on YouTube to bring you 10 outrageous party tricks your guests will not forget.

This video shows how to check your hosts file for spyware. This is a valuable tool, if your computer has spyware it can greatly affect the performance of your computer.

According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the Wi-Fi version or the 3G model.