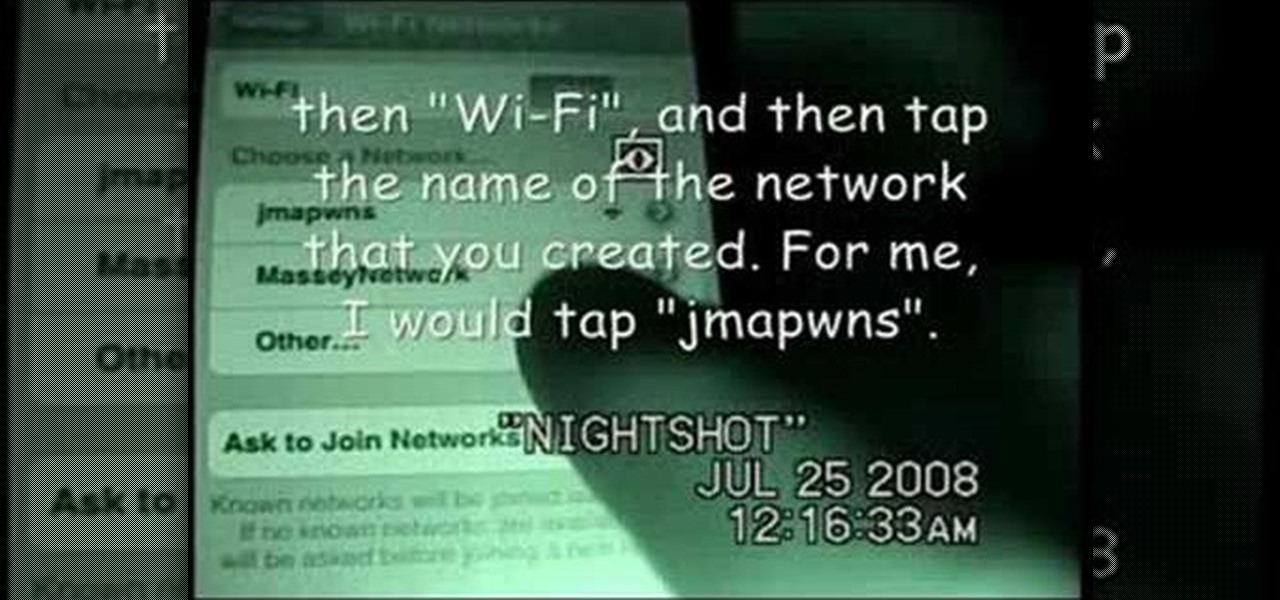
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.
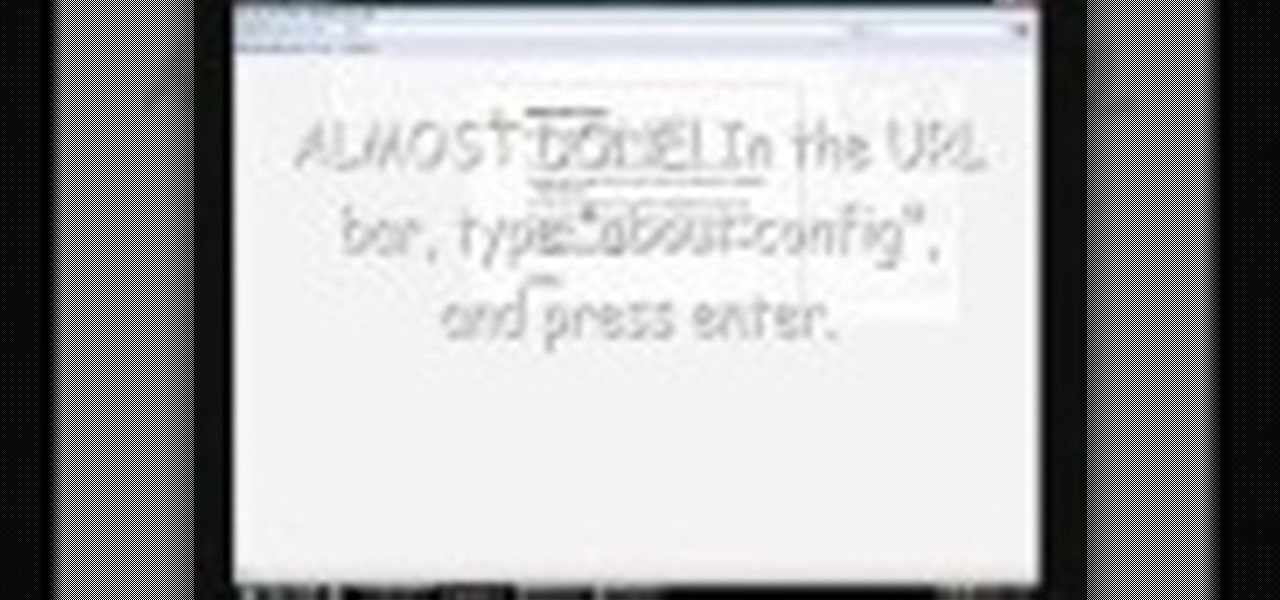
This video will show you how to tether an iPhone 3G in Windows Vista so that you can use its internet connection on your own computer!

Watch this iPhone video tutorial to learn how to save those iPhone Web apps so you can use them even when you have no connection. This how-to video will help you learn how to use offline iPhone applications like a pro in no time. Perfect for new iPhone owners.

BPS golf instructor Steve Bishop discusses a particular technique used to improve your mental connection between what you want to do, and what you are doing.

When working in a network, you can't always see the connection lines if you are too zoomed out. This tutorial shows you how you can quickly connect nodes in Houdini.

Watch this video to learn how to use Google docs. You can view and edit your documents offline, without an active internet connection.

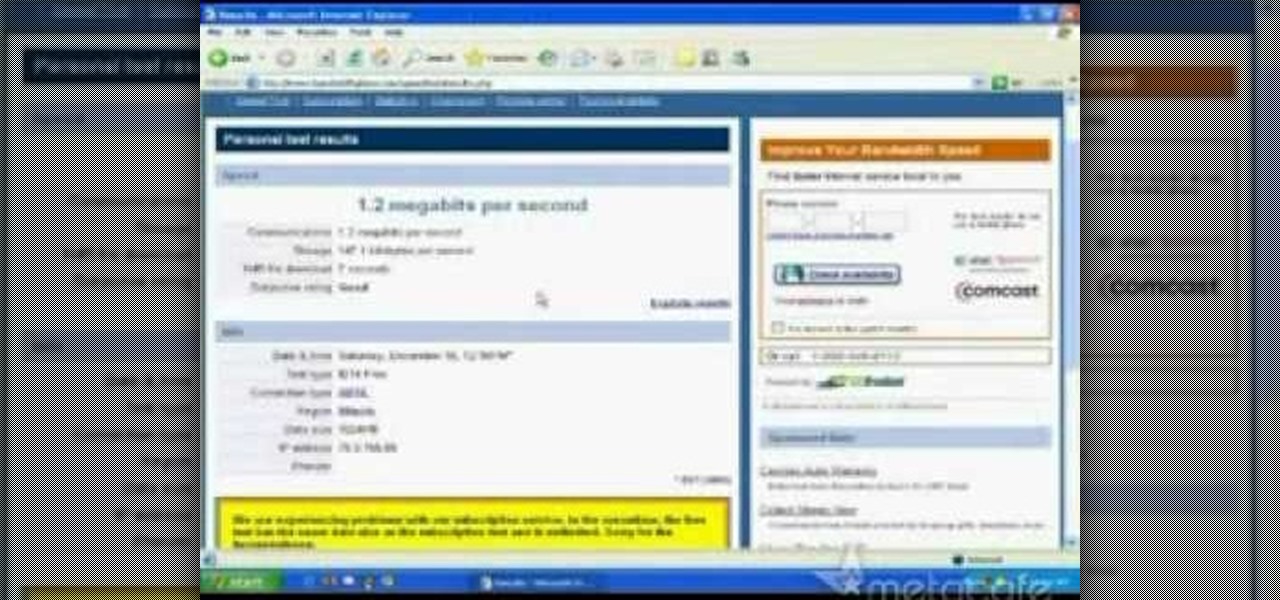
Learn how test and improve the speed of your DSL Internet connection.

An installer shows the steps needed to remove tail lights, make wiring connections, and complete installation of the wiring harness for a trailer hitch on a Jeep Lorado.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this video, Rodney Yee shows us how to do the half-fish pose. This yoga pose primarily aids in digestion. It is also a common hamstring stretch done in most sports, with no yoga connection.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

No more q-tips! No more alcohol! No more blowing in your cart! Did you know alcohol actually damages the carts? This is a much more effective, safe and long term way to restore the connection.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hold it to the frame using the safe-open pry tool. Run the tool between the case and the glass along all edges. Gently pull glass off and pry off the digitizer. Next, remove the small screw in the upper corner, lift up the ...

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

Syncing your bluetooth earpiece to your BlackBerry device can be tricky. But pairing your bluetooth enables BlackBerry with your earpiece is actually quite easy. Best Buy has answers. The Best Buy Mobile team explains how to connect a Bluetooth earpiece to your mobile device. See how to access connections set-up on your Blackberry and also see how to wear a Bluetooth headset.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

Learn to make your own super effective bass traps and acoustic panels with materials from your local hardware store, just by watching this home audio video tutorial.

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

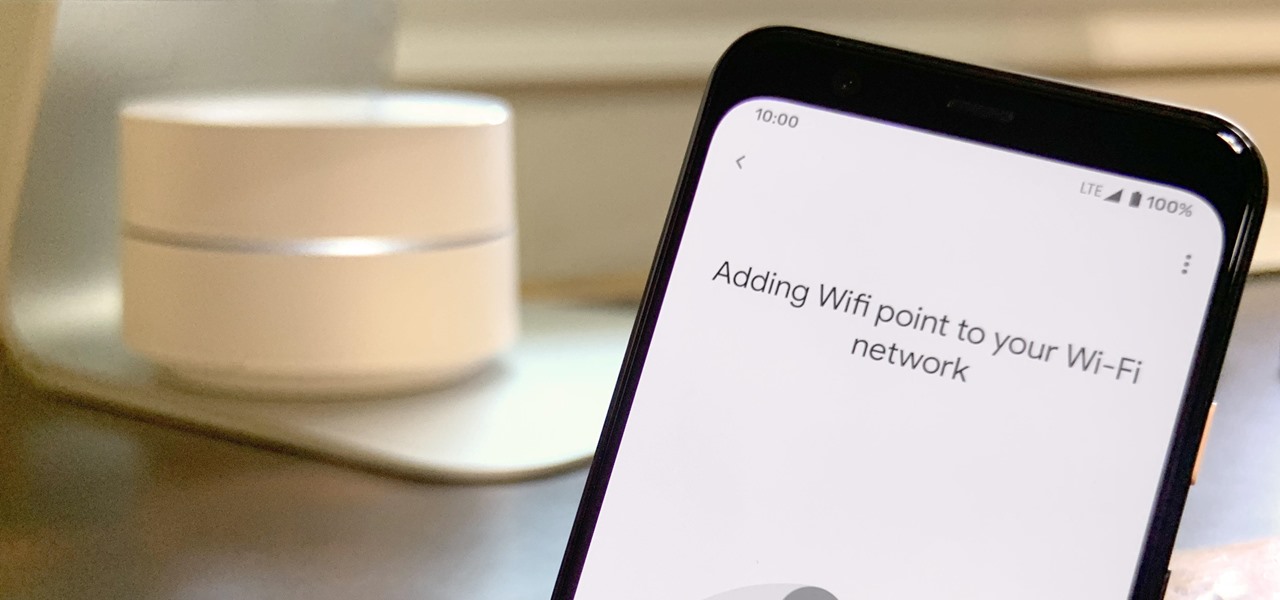
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

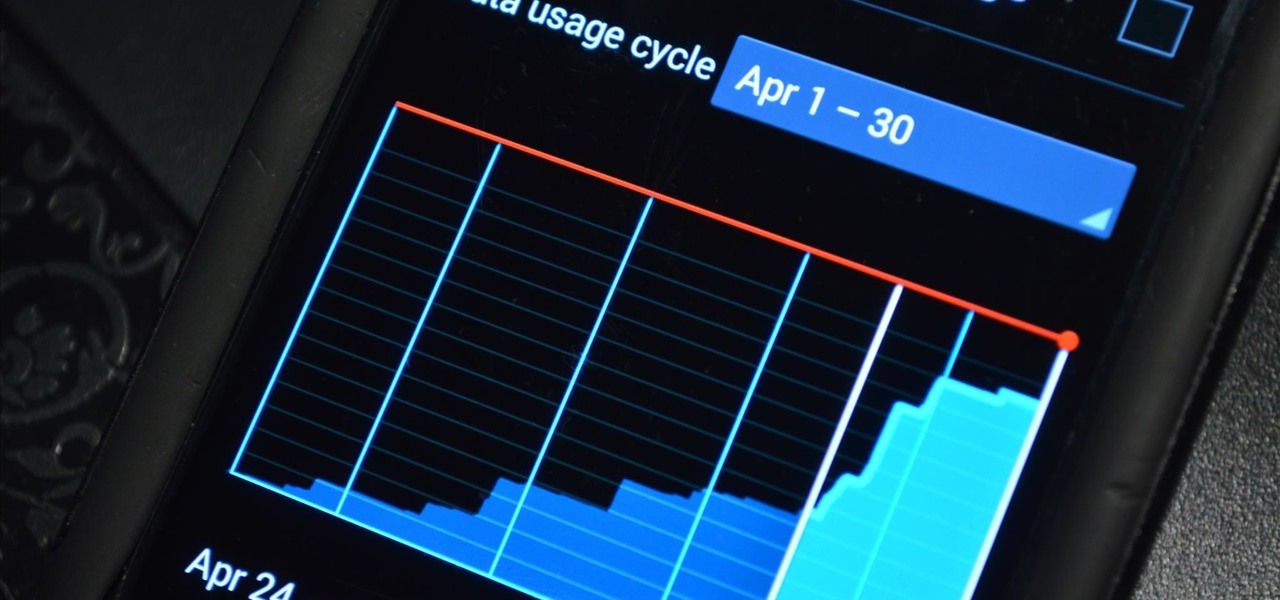
If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.