After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

We've heard the rumors for months, but it's finally official: The iPhone 7 will not include a traditional 3.5 mm headphone jack. Instead, you'll need to hook your favorite headphones up with a Lightning adapter (or use ones with a Lightning connector built-in) and connect to your phone using the same port that your charger occupies.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

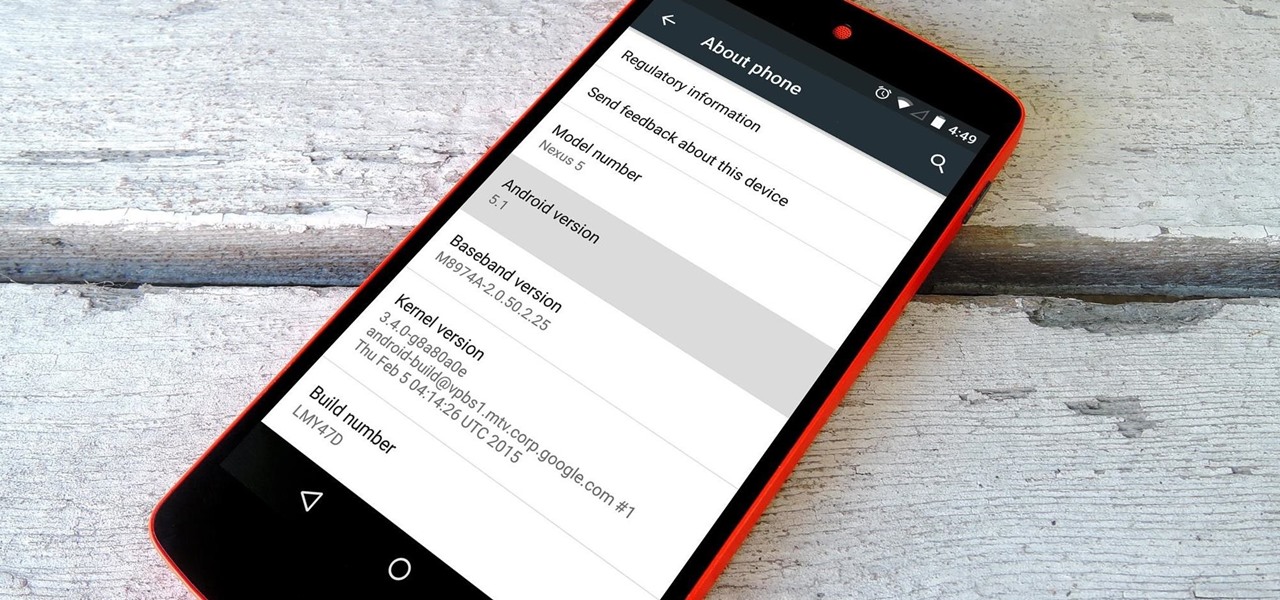
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Want massive, Arnold Schwartzenegger-worthy shoulders? Well, you'll have to work for it, but they're achievable with a few strategic exercises. Building muscle, especially big muscles like your biceps, requires heavy resistance.

Part of the process is to create plans to follow when making the cabinet for the arcade game. when cutting the wood you need to allow for the 1/8th of an inch that the band saw will be cutting. You will also need a piece of plexi glass to give the game an authentic feel, spray paint the piece of plexi. You will also need joysticks and buttons, which you can get at happcontrol.com. You need to cut a square hole in the plexi so that the buttons can be mounted in it. To integrate the buttons you...

How to instantly bond with anyone and persuade them

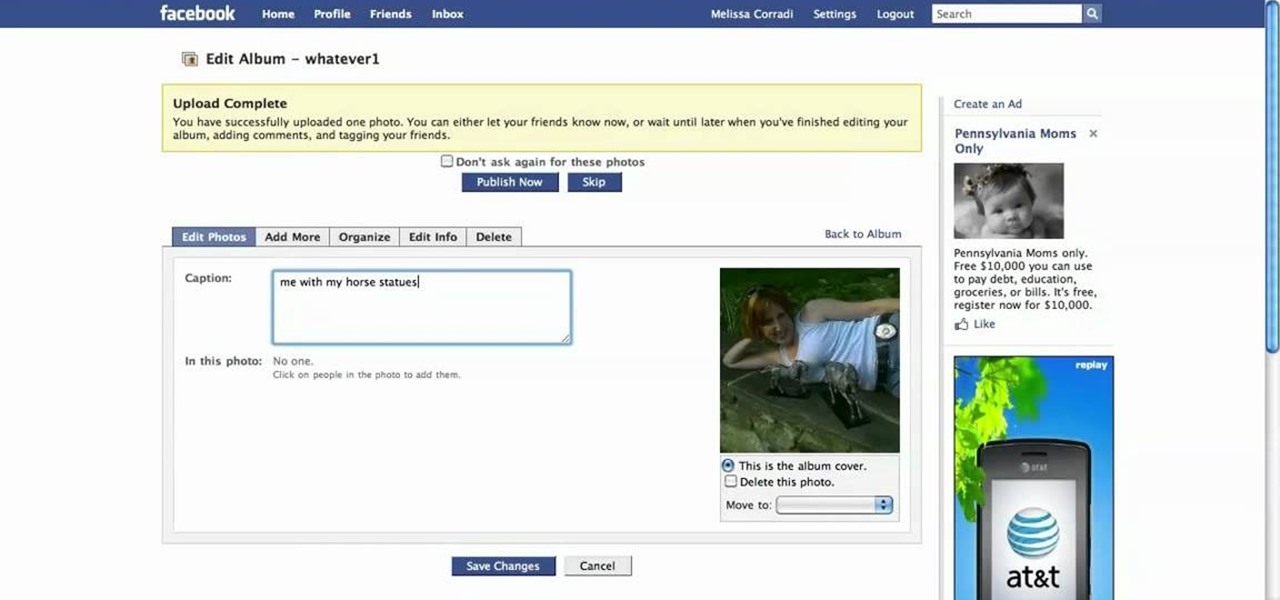
First log into your Facebook account and sign in. Then when you sign in click under your "profile". You will be redirected to another page. This will be your main page, with all of your information that you have put in and what not. Next click on 'Photos'. It will take you to another page. Once in your in there, you will click on 'create a photo album'. You need to name the new album and then create album. Next it will ask the location of the files. It will be located on your computer. Usuall...

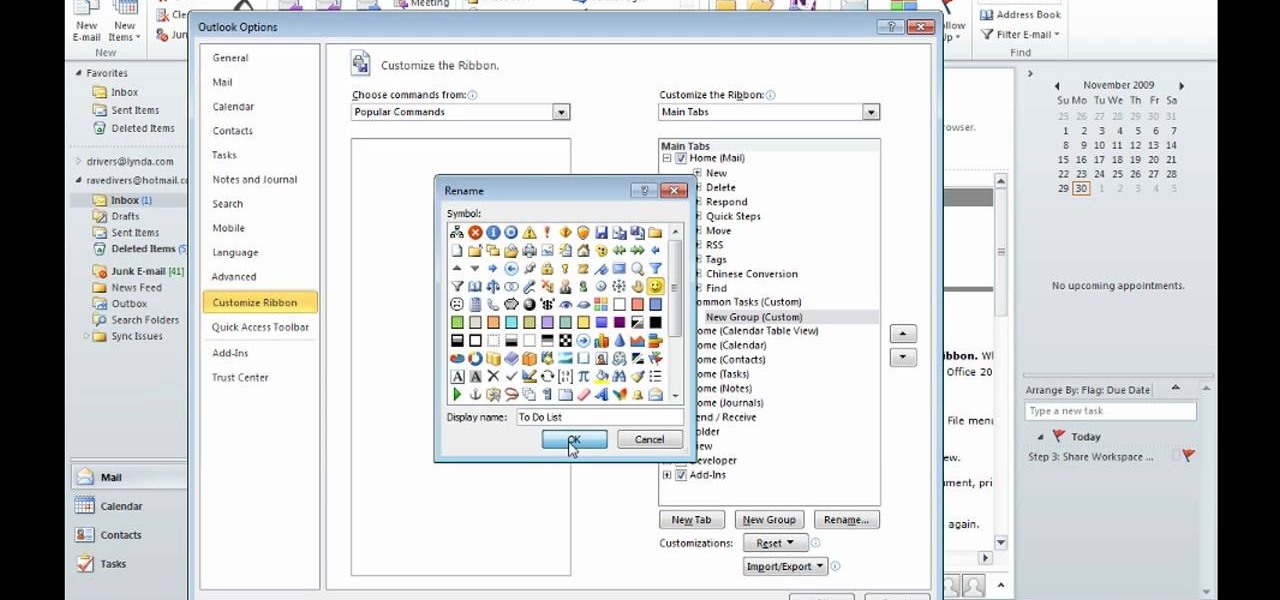
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Let us help you install your JVC Everio software and hook up your JVC HD Everio video camera to your computer. Just select your operating system.

For those of us living in any of the 49 states other than New York on Thanksgiving Day, checking out the famous Macy's Thanksgiving Day parade at New York is more a dream than reality. While the parade airs every Thanksgiving on television, it's also possible to catch the festivities online.

First of all you need to know that there are different types of Martingale Fit. In this tutorial you are first shown a running Martingale Fit. It is attached around the neck by wrapping it. You have to make sure to wrap it around the neck in such a way that it fits to come exactly in the middle of the horse’s chest. Here you have to make the connections. Now you have to go underneath the legs and attach it to the girth. You shall notice two rings hanging over from the chest. You have to attac...

I hope you haven't updated past here if you want to jailbreak your iPhone. Jailbreaking gives you access to many open ended applications and games. This video will demonstrate exactly how to jailbreak and unlock your iPhone 3G/3GS firmware 3.1.2 and 5.11.07 baseband.

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...