Connecting your Nokia N900 smartphone to a wireless hotspot or your home wifi network is just a few quick taps away! Take a look at this tech support video from Nokia that will tell you exactly where to find the available internet connections on the phone and select the one you wish to connect to.

If you are are creating a new computer network connection and aren't sure which IP range to use, watch this video. It will explain the differences between the three IP address ranges and which one would work best for a network of your size.

In this video from Lowe's we learn how to use a gas smoker. This tip comes from Lowe's. You can cook with a smoker anytime of year. He is using a gas smoker. Keep this away from siding. The fire source heats the moist wood chips, which release the smoke that flavors the food. You need tongs and a meat thermometer for sure. Before you cook for the first time, season the smoker by smoking some wood chips without food in it. He is cooking a pork shoulder which he uses a dry rub, wraps in plastic...

Epson printer setup is easy, let’s start by connecting the standard USB cable into the USB port in the back of your computer, the other end of the USB cable will go into the USB slot in the back of the projector. Simple as that your slides will start immediately! With the Epson plug n play projector you can use the page up page down keys in order to manage your slides which you cannot do with those other out dated connections.

This is a video guide to wireless broadband from Top10.co.uk. Learn about wireless broadband in this interesting video. This "how-to" guide for wireless broadband explains the basics of what wireless broadband is, how and where it works and who offers it, not to mention how to set up a home Wi-Fi connection in minutes using a wireless router. Follow the steps in this guide and go wireless today.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Watch this how to video to use a breathing theme with your stretches. Improve your flexibility and stronger mind body connection with yoga. This yoga breathing theme makes your stretches wonderfully fluid and helps you pace your breathing. It's a good strategy when flexibility is the goal.

This video explains how to use jumper cables to jump start a car. First, determine that a dead battery is the reason your car is not starting. If the engine cranks when you turn the key, the problem is not the battery and jump-starting won't help. If the windshield wipers, lights and heater blower all work, the battery is probably fine and you may have a bad starter. A jump-start won't help if you have a bad starter. If you hear no sound at all when you turn the key or if the engine cranks ve...

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on configuring and connecting to your 2Wire Gateway via DSL wireless Internet instead of through an Ethernet cable. make sure to follow this whole process to get your High-Speed Internet up and running on your computer.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing DSL 2Wire Gateway filters on home phones. Make sure to repeat the install process for the Gateway filters for each telephone in your house that uses the same phone number as your High-Speed Internet.

Wireless can be a pain sometimes with video games on the Internet, with disconnections and signal losses, but why not revert back to a wired connection? This video will explain how to connect your Nintendo Wii to a wired network using Actiontec Powerline Networking technology. This will enable your Nintendo Wii to connect to the Internet to download games, console updates, and other information.

As great as Macs are, they're often limited by the apps you have installed. Your computer might have the processing power to render a 4-hour movie in the time it takes you to have lunch, but if you don't have the right apps, you're not putting all that power to use. The All-Star Mac Bundle Ft. Parallels Pro gives you access to programs that will put your Mac to use and give you the best functionality out of it, and right now this whole bundle is on sale for $49.99.

Get your holiday shopping done early with these deals on software, e-learning classes, and gadgets. These Cyber Monday goodies include something for everyone at a can't-miss additional 20–70% off sale prices.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

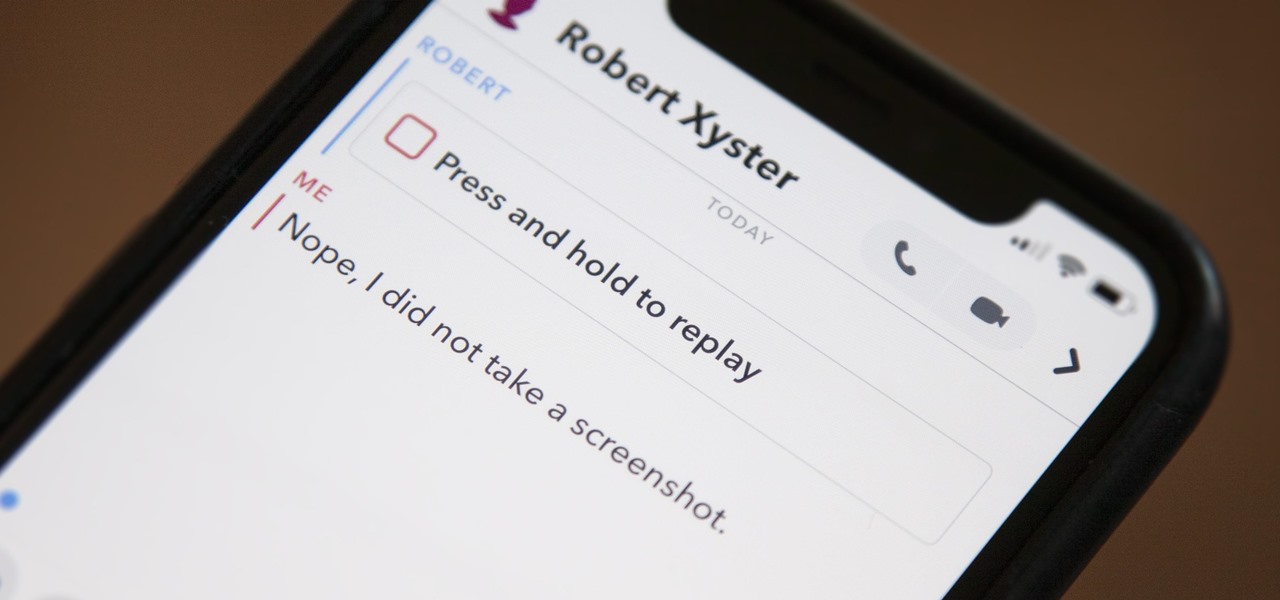
Snapchat doesn't prevent you from taking screenshots of snaps received, but the other user will get an alert either as a prominent push notification or a subtle note in the app. Snapchat has improved its screenshot detection abilities over the years, so it's much harder to circumvent its technology for truly undetected screenshots — but not impossible.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Up until April 2020, the iPhone XR was, for many new users, the first entrance into the world of Apple because it was the cheapest iPhone model since the original iPhone SE. Now, the second-generation iPhone SE has shown up at the same initial starting price as its predecessor, giving budget-friendly buyers another choice.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Mobile gaming has exploded, with roughly $70 billion in revenue in 2019. This gave rise to the so-called gaming phone, headlined by names like Razer and ASUS. While the Galaxy S20, S20+, and S20 Ultra are being marketed as everyman devices, make no mistake — these are unstoppable mobile gaming machines.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

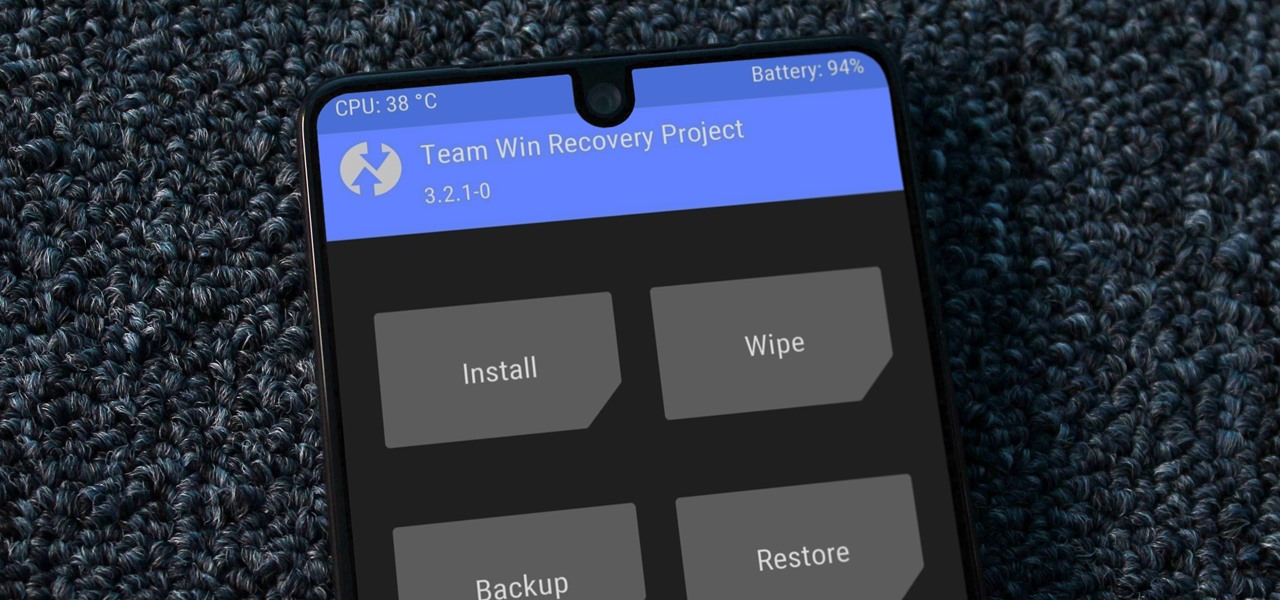
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.