The new 007 film, Skyfall, comes out this Friday, and dreams of becoming a super-spy have taken over my mind. Only I can't afford any of James Bond's awesome gadgetry or amazing cars—and you probably can't either.

People use search engines for a wide variety of subjects (just look at some of the results that pop up in autofill). The results you get with each different search engine are usually different, but almost all of them display the same number of results per page by default—ten. If you find what you're looking for at the top of the first page, great. But if you have to do a lot of digging, it can be a pain to load so many different pages to find it, especially if your connection is slow.

In this project, you'll learn how to re-purpose low-cost sprinkler parts into a high-powered CANDY CANNON. Be the coolest person on the block by building a pneumatic device that will launch candy 100 feet in the air—you can make it rain down all kinds of sugary treats!!!

Take everyday sprinkler parts and form them into a high pressure rocket launcher that will shoot paper rockets nearly 300 feet!!! It's cheap to make and a lot of fun!
The Internet has had a huge influence on many areas of our lives, but, in particular, has resulted in nothing short of a revolution in the way we work. The web has offered the sort of flexibility to the individual that few people would have dreamed of just a couple of decades ago. And where once a global marketplace was available only to a handful of multinational corporations, today thanks to the Internet, we can all access it.

You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Throughout the meticulous and dexterous process of jewelry making, when you get to the end of your bracelet or necklace, there's a feeling of accomplishment and satisfaction. But to seal the deal, you need to crimp. Crimping is a necessary process for the ends of your homemade jewelry. This demonstration video will help walk you through the process of this crimping end beads on soft flex.

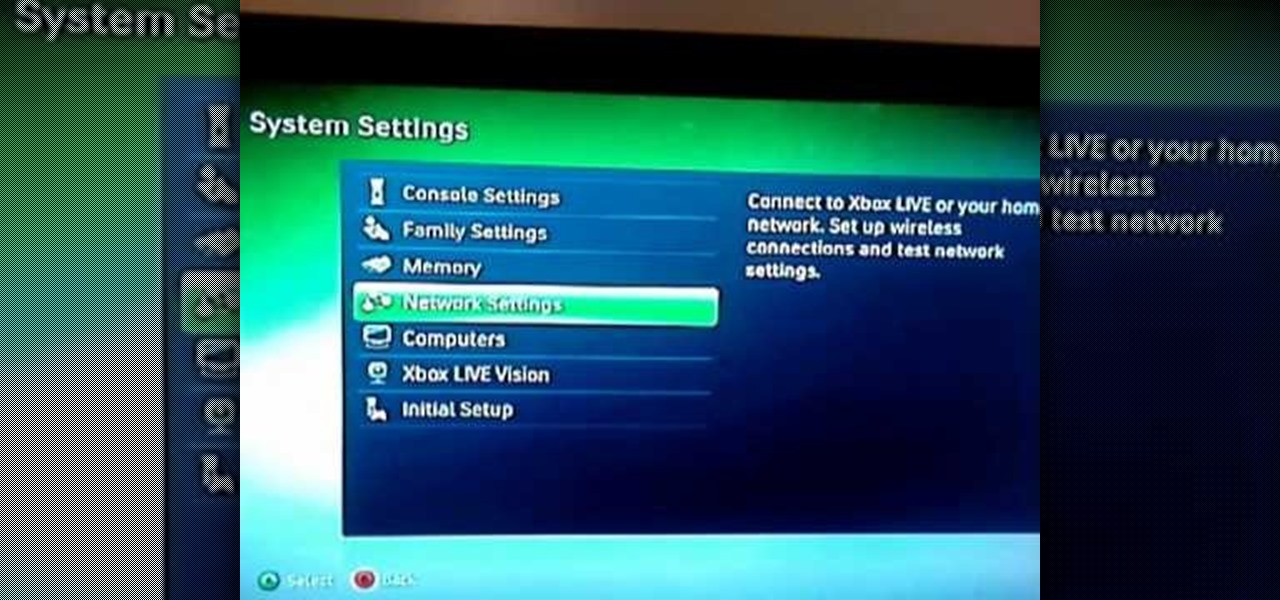
Your router is automatically equipped with firewalls meant to protect your PC from intruders. However, these firewalls often misread information needed to run online video games, and block necessary files from reaching your XBox. In this tutorial, learn how to change the NAT settings of your modem to "Open" and allow these files to get through. By doing so, you will be able to take full advantage of your XBox Live account.

In this video you will learn how to check your internet speed without using any software. In order to do that just follow these simple and quick steps and instructions: The first thing that you need to do is to double-click on your Local Area Connection icon. A window will appear and you will see what your speed is on the right of it. The speed of your internet will be in Mbps. If you follow these easy and quick steps you will now how to check your internet speed without using any software or...

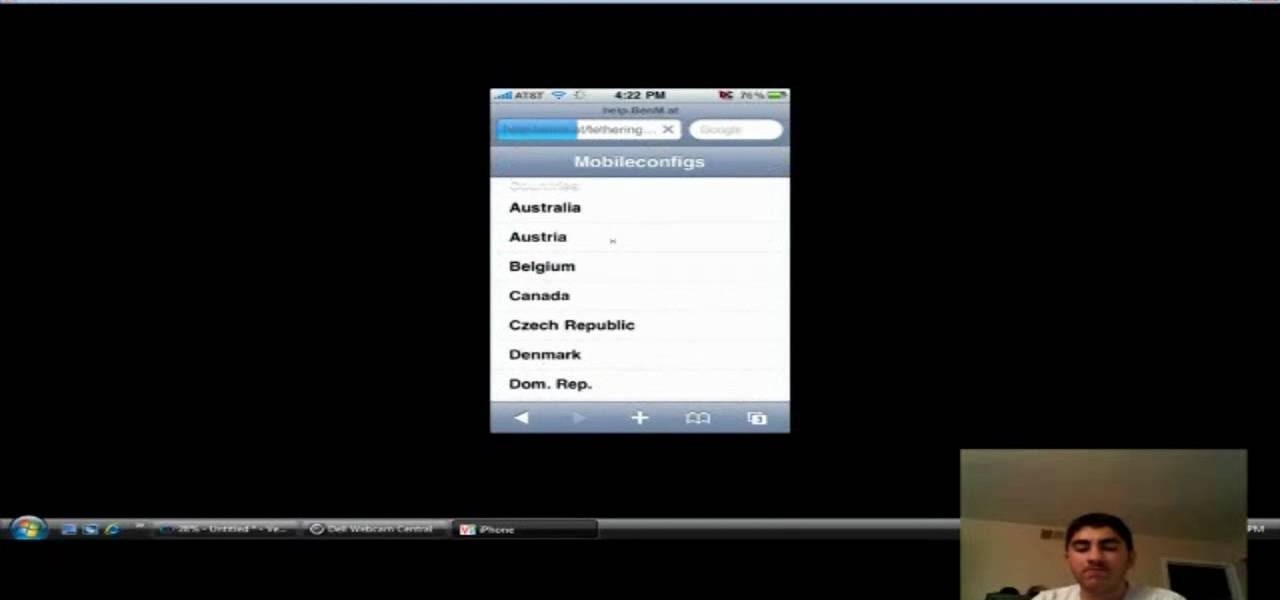
This video shows you how to enable internet tethering on your iPhone 3GS. What are the perks to internet tethering? Well, for starters, it allows you to log into the internet from just about anywhere by sharing your laptop's internet connection. This will also allow for faster browsing speeds if you don't have the fastest cell service at the time.

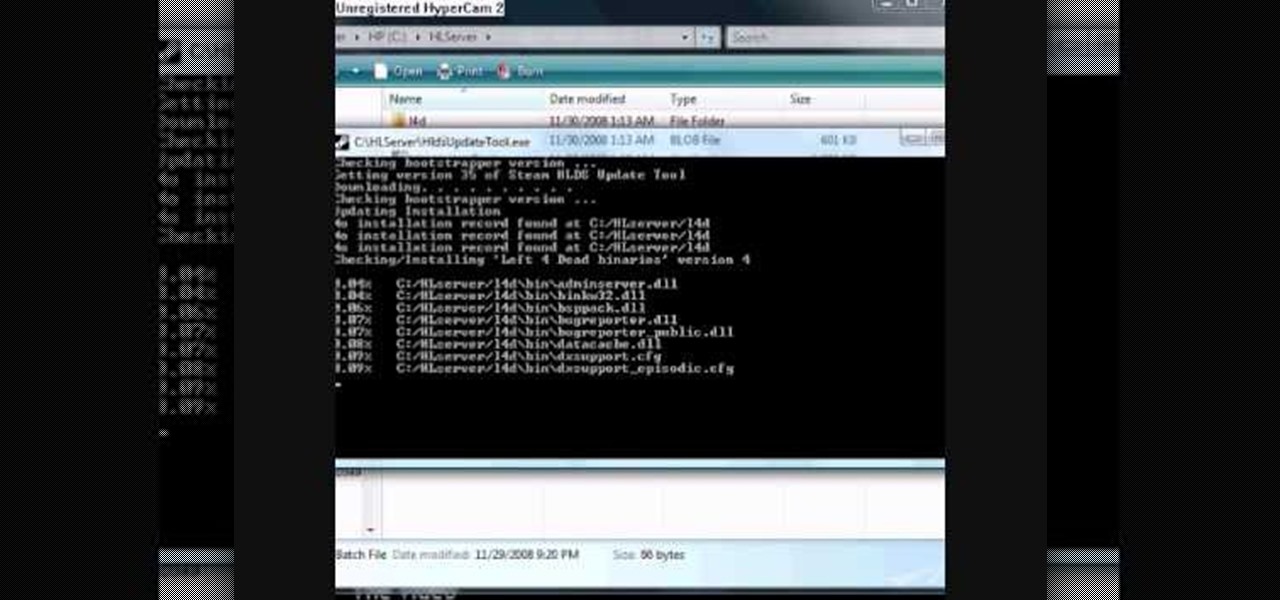
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

It's time for some golf! What's an 18-year-old know about distance? Justin James can belt it 400 yards and more, and with his power tip, you too can tack on a few extra yards. Well, maybe not 400 yards, but you get the idea. See how to get more power out of your golf drive.

This scooter modification tutorial gives you some tips on how to bolt a velocity stack to a 28mm Mikuni carburetor on a Honda Elite DIO scooter exhaust system. The video doesn't cover the actual install but gives tips on ways to make the connection easier.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

Vincentwiliamphilips teaches you how to install the ultimate vshmenu plug-in on a PlayStation Portable. This is an improved version of the vshmenu plug-in, with added features. You download the needed file, called Ultimate VSH Menu v2.00 for 5.00m33-6. Open the file and extract vshmenu.prx and the vsh text file to your desktop. Connect your PlayStation Portable to your computer. You will then see the root of your memory stick. Put the vshmenu.prx in your seplugins folder. If you don't have on...

Learn how to upgrade your M1000 Qwest DSL Modem with wireless. You'll see the easy steps on how to upgrade your M1000 Qwest DSL Modem for Wireless from Actiontec Electronics.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your 2Wire Gateway for EMBARQ High-Speed Internet. This will cover exactly how to install your EMBARQ 2Wire Gateway modem for Internet. This is the complete process step-by-step from box to connected online.