Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.
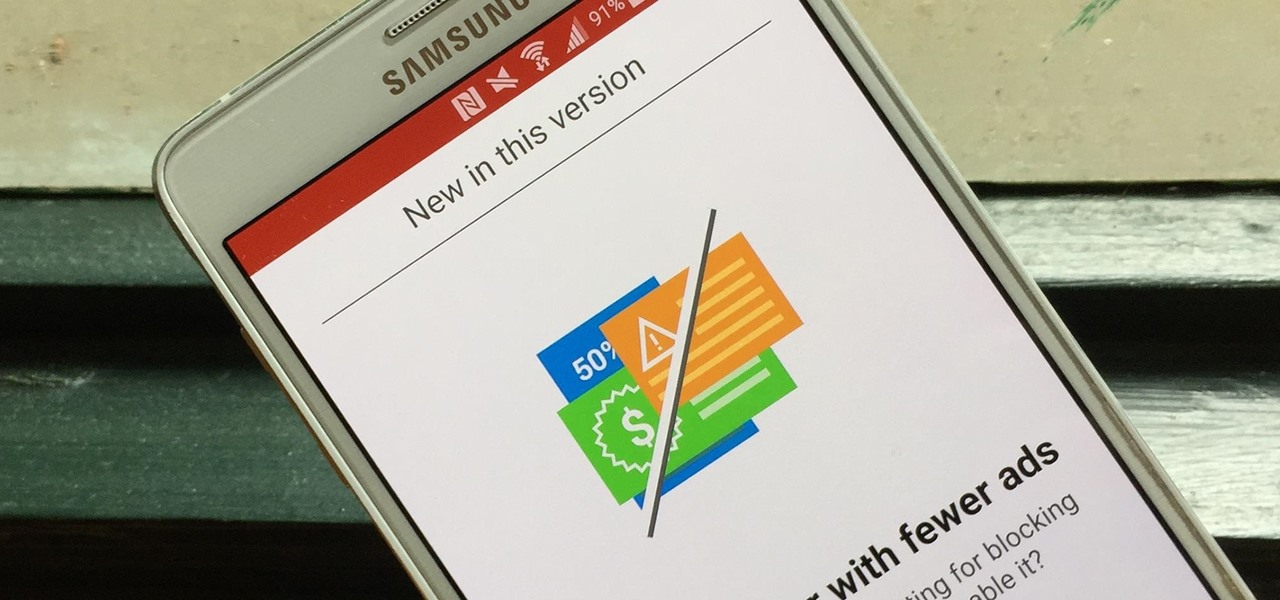
Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

Having the ability to stream music or video from practically any internet-capable device is a thing of wonder—especially at the airport. I don't know how many times Netflix has saved me from watching something like CNN for 5 hours straight at the gate during long layovers. But streaming video sites like Netflix only work in North American and few other regions. So, if you're a U.S. subscriber currently in Australia or France or any other international location, Au Revoir to your streaming cap...

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

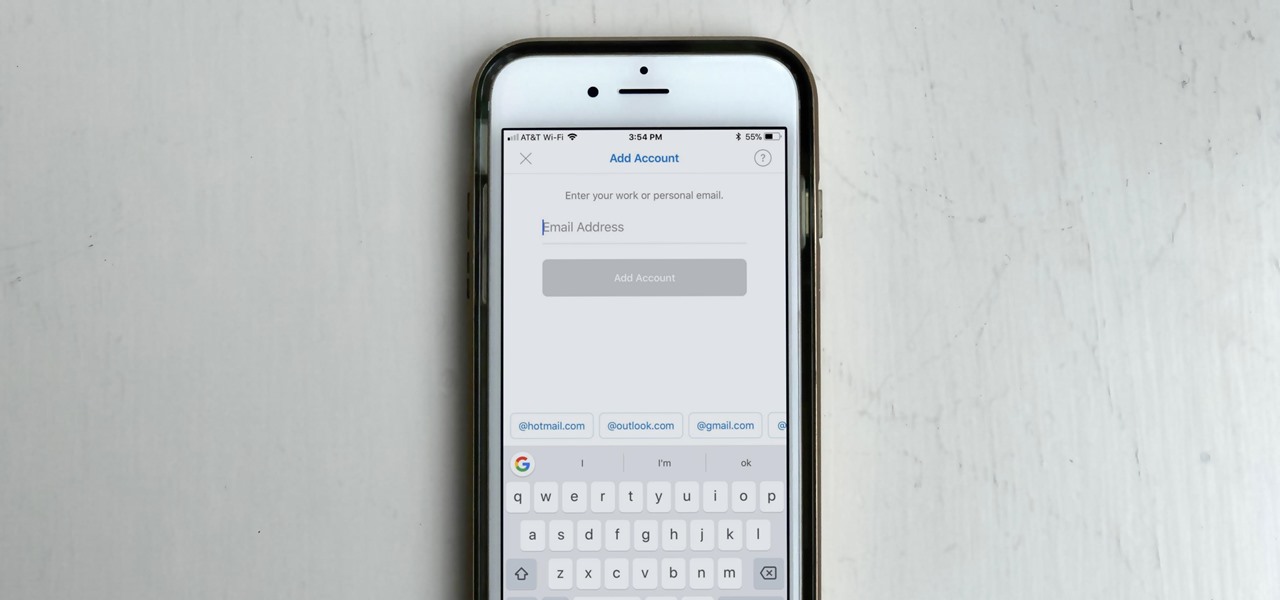
If you work with multiple email addresses, you need an app that can organize and declutter your day-to-day messages. Outlook is a great choice, but if you only have one account attached, it somewhat defeats the purpose. Lucky for you, adding additional email accounts is both quick and simple.

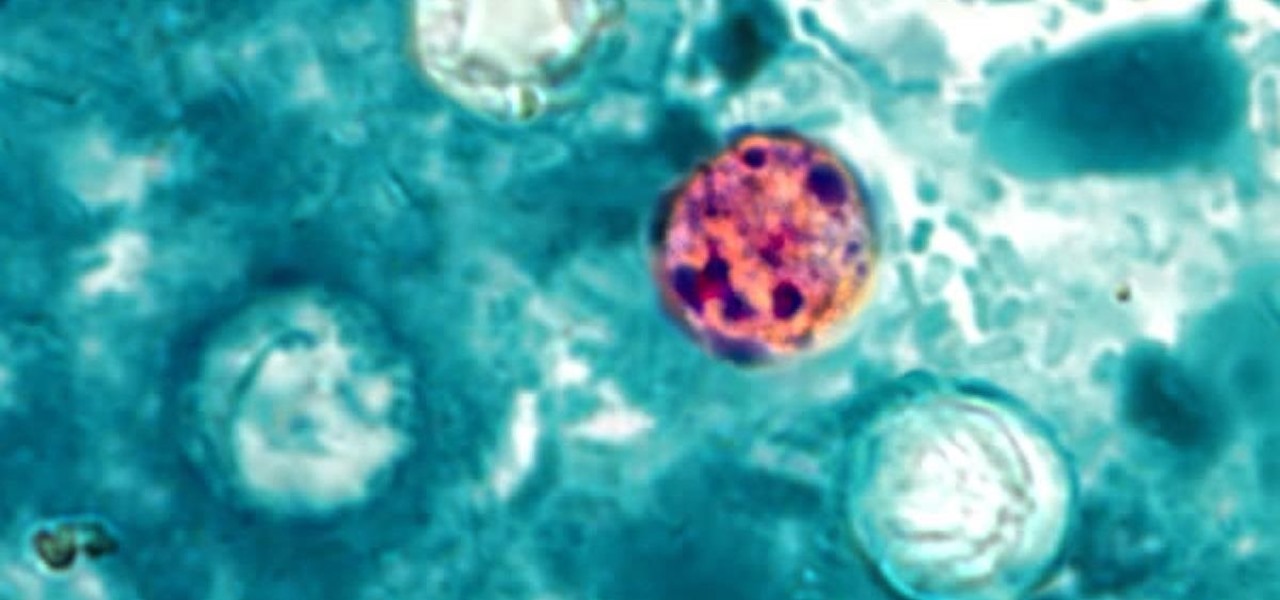
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

Unlocking the iPhone can save you a ton of money and irritation by getting you off AT&T and onto a better service provider. One way to do that is flashing the baseband to one that works on the iPad, and this video will show you how to do using Redsn0w that, provided you're working from a iOS 4.2.1 / 4.1 equipped iPhone 3G / 3GS on baseband 5.14 or 5.15 (about to be 6.15 when you're done).

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

MAKE magazine never fails to amaze. And this time, John Park tackles a DIY wind-powered generator—and he shows you how to do it! Before you start watching the video tutorial, make sure to download the PDF of this project for reference.

This is an Apple iPhone video tutorial that will show you how to unlock an Apple iPhone 2G or 3G for use with another mobile phone service provider other that AT&T. If you are using a Macintosh computer, you can unlock both the 2G and the 3G phones. If you're using a PC, then you can only unlock the 3G iPhone.

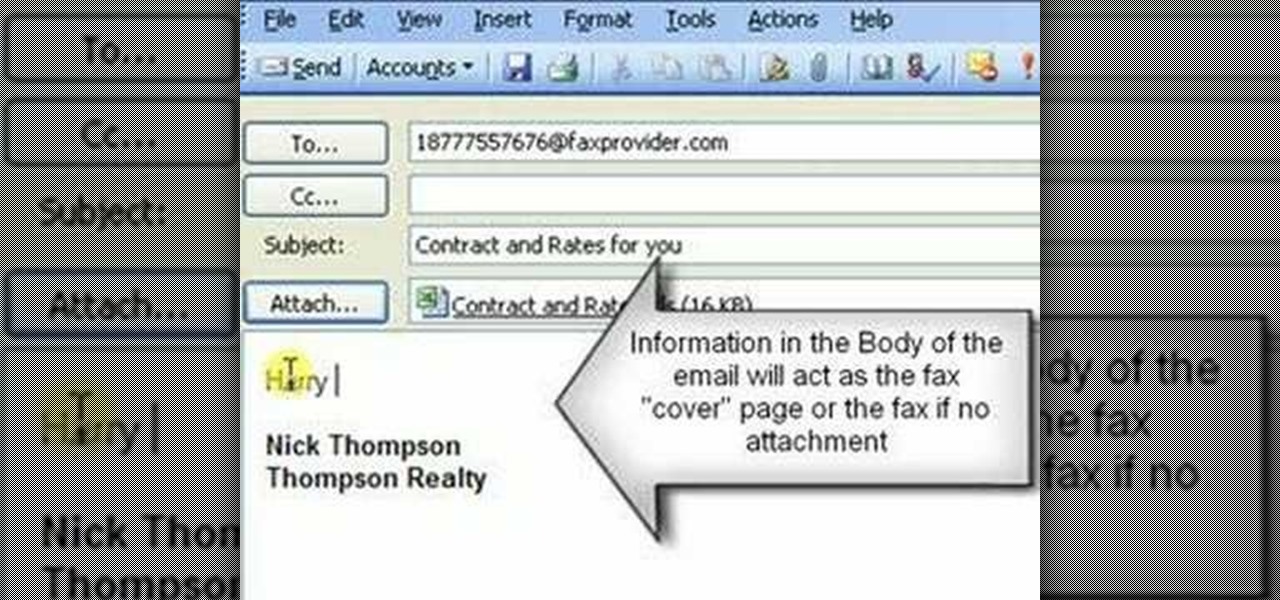
Check out this video tutorial on how to send a fax with email using Internet Fax. You'll need an Internet fax provider, and a phone number, so don't think it's easy as one, two, three.

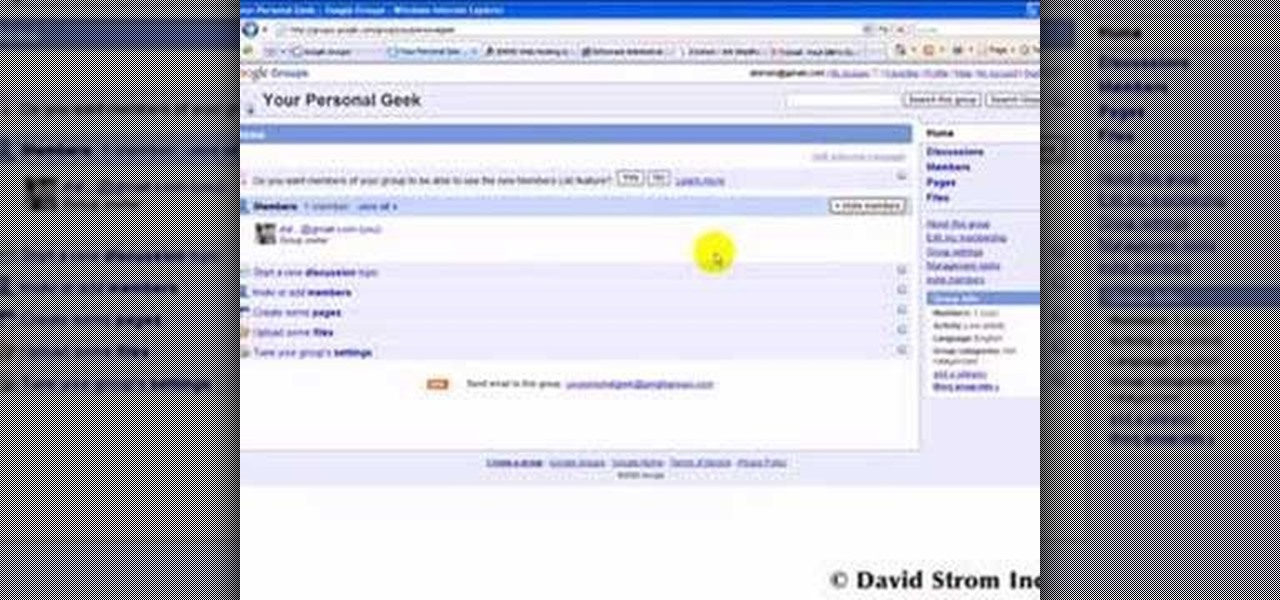
David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Now most of the free email providers allow upto 25 MB of file attachment. But we need more. This video will help you how to send or transfer big files upto 2GB over internet without any cost. Watch the video and follow all the steps to do it yourself.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

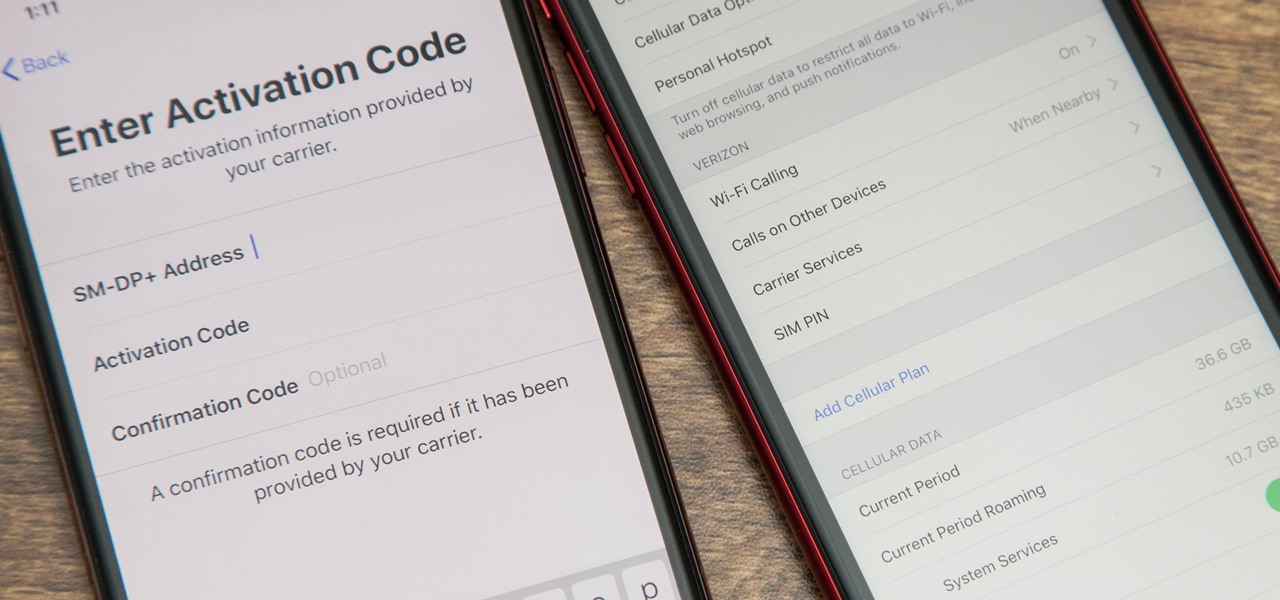
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

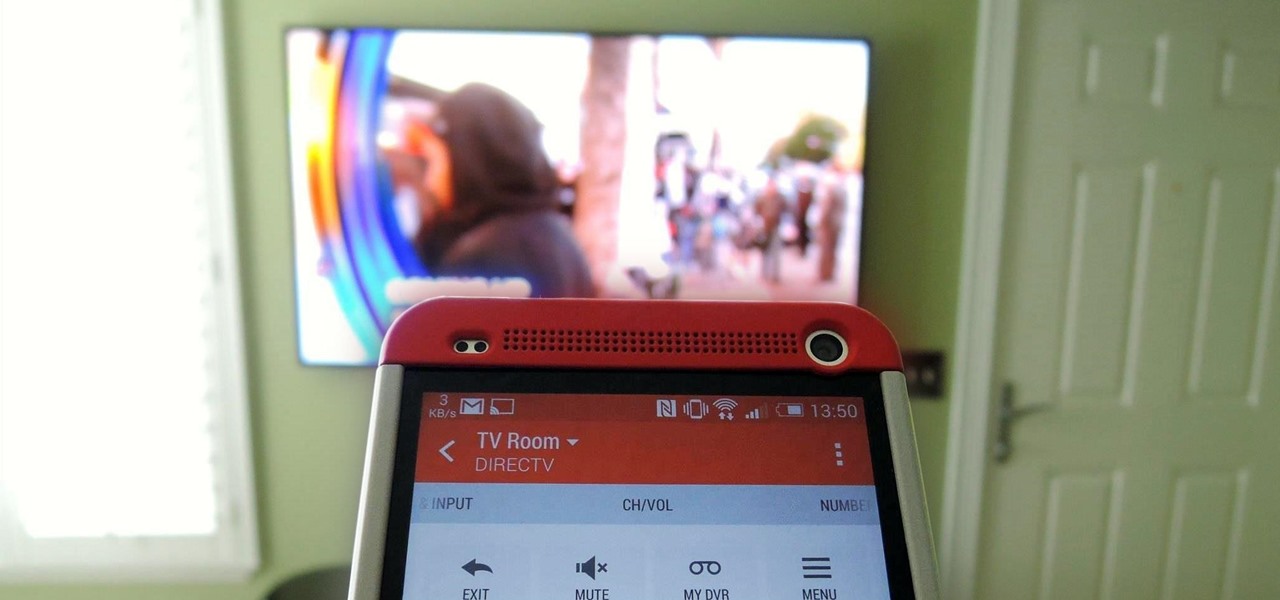
Let's face it, finding your remote, let alone finding something to watch, can take more time out of our days than we'd care to admit. There are remote locators and channel guides out there, but why use those when you have a perfectly good remote always on you—your HTC One. HTC put an IR blaster into their One and when it's coupled with their Sense TV app, it can make for one hell of a smart remote.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

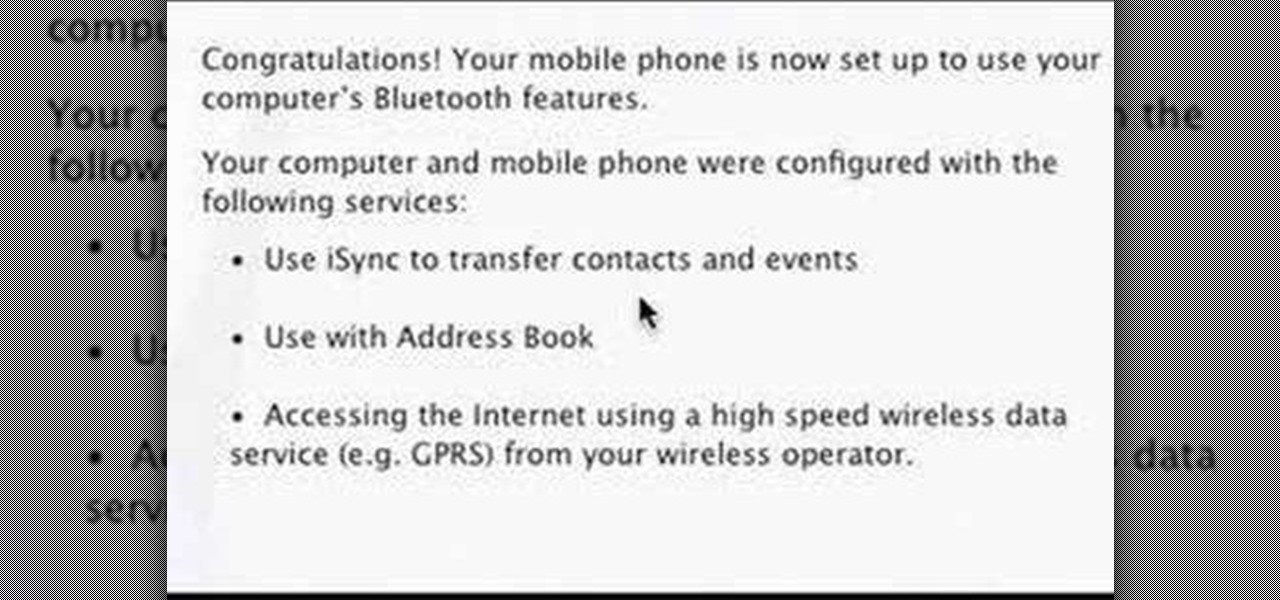
In this video you will learn how to setup a Bluetooth mobile phone in OS X. To do this go at system preferences select Bluetooth click on Discoverable, Open Bluetooth Setup Assistance and Show Bluetooth Status in the menu. Then click Sharing and mark all the options. Now go at devices, select set up new device, mark mobile phone, click continue, wait until the device will find your mobile device, click continue and you will get a pass key. Enter that passkey. A window will pop-up where you ca...

Studying to be a pediatric nurse? Then here is a nursing how-to video that teaches you how to properly use pediatric resuscitaion equipment in the hospital. Every nurse should know the basics, follow along and see how easy it is to use the Broselow Medical Guide and pediatric emergency tape. The Tape is intended to be a guide only in determining specific drug dosages. The clinical condition of the patient in combination with the providers clinical experience and training should always be used...

This video is specifically for the C530 Slate cell phone from AT&T, though this procedure will probably work on similar models of phone. You can hack, or jailbreak, your phone to allow you to use third party apps or switch to a different service provider. You will need a non-AT&T sim card for this hack to work (T Mobile is shown in the video). Then turn it on, hit the unlock key and then enter in your unlock code. Make sure you get it right!

In this video, we learn how to ease labor pains during birth. One way is to move your body and try different birthing positions. This will open up different parts of the pelvis and help more than lying down. Once you receive an epidural you won't be able to get up, so make sure you do these exercises during early labor. As long as your health care provider allows it, do these before you receive drugs. Any of these will help during contractions and help with pain during labor. Every woman is d...