Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

At the Google I/O keynote presentation today, Clay Bavor, Vice President of Virtual Reality for Google, shared a number of new initiatives in virtual and augmented reality. This included new services for the Tango platform called visual positioning service, or VPS.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

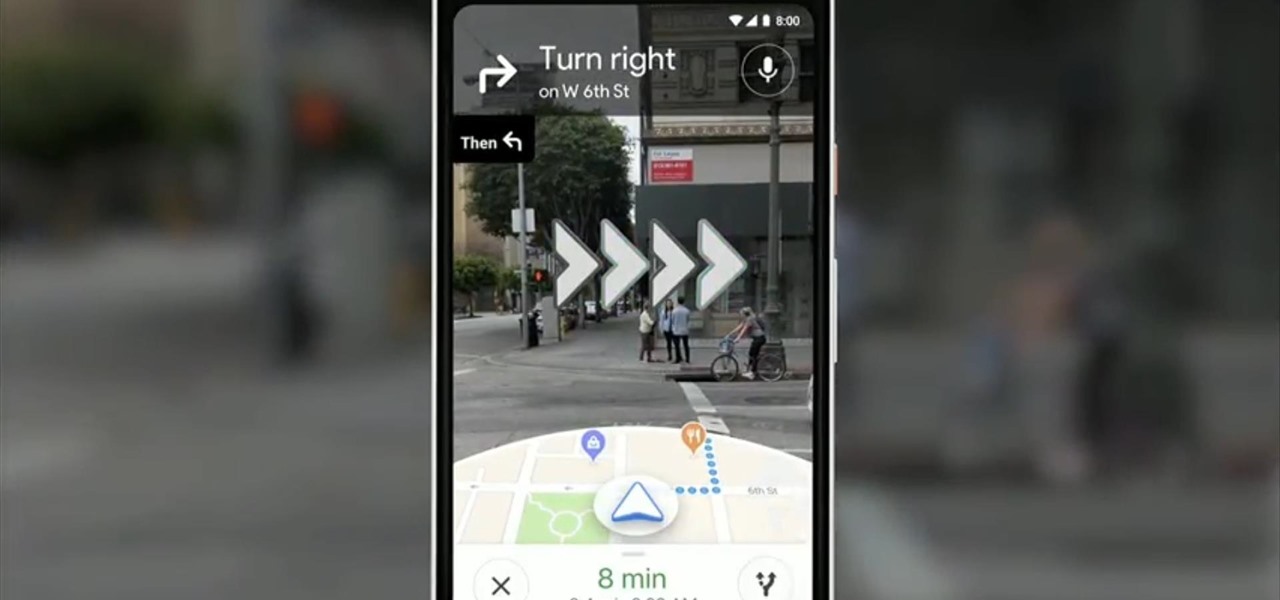
At Google's I/O developer conference keynote on Tuesday, ARCore may have been absent, but Google did preview a potentially trailblazing augmented reality feature for Google Maps.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

proxyFinderEnterprise is a tools for find proxylist . in this topic you learn how to use this tools for find a proxy list .

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.

Kings Dominion, an amusement park located in Doswell, Virginia, just announced a mobile augmented reality game for park visitors. Gameplay in The Battle for Kings Dominion — available on May 19 for iOS and Android devices — follows the playbook designed by Niantic through Ingress and Pokémon GO.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

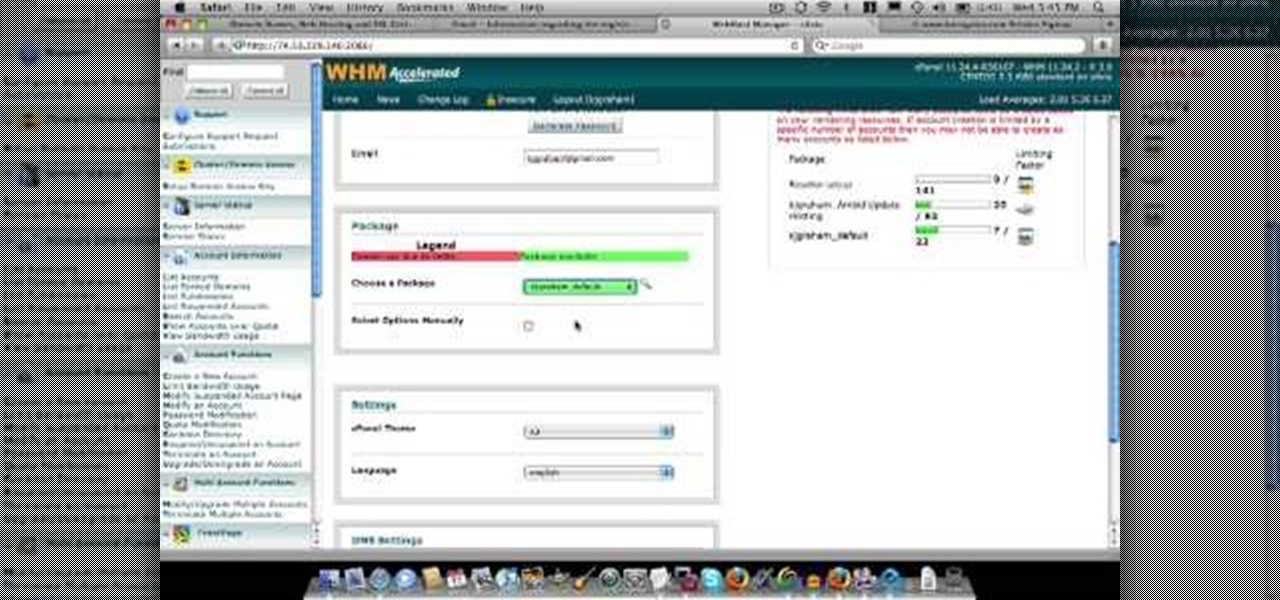
In this video about choosing a web hosting company. The narrator begins by saying that web pages are hosted on servers; the files that make up a web site are hosted or stored on a server. The narrator recommends a service called Host Gator. He indicated they are reliable and provide reasonably priced web hosting services. He briefly discusses the process they charge for their different levels of hosting services. Next he shows the steps to hook your domain name to the host account. He demonst...

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

This week, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that not only does Samsung have a new virtual reality headset coming, but that Samsung intends to enter the field of augmented reality, too. In fact, Hong talked very little about virtual reality and instead spoke at length about Samsung's move into augmented reality.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information on this hack, watch this helpful video guide.

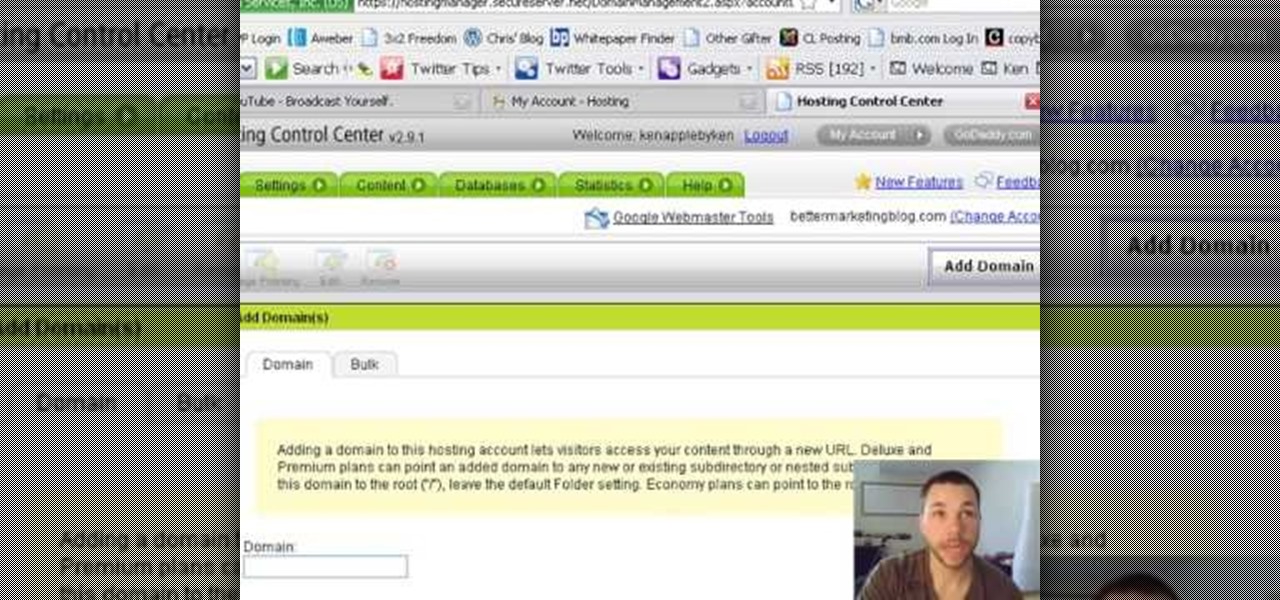
Adding domains to your GoDaddy hosting plan can be done by following the steps Ken Applebee outlines in this video tutorial. Once at the GoDaddy main home page, click on My Hosting Account under the Hosting tab at the top of the screen. Log in and go to your account with the hosting on it. Click on Your Domains and you will see your domain in there. On the right side you can choose to add a subdomain or you can just click on the Add Domain tab for a completely separate domain. This allows vis...

For those who enjoy the finer things in life, premium Scottish distillery The Macallan is bringing an augmented reality art gallery, viewable through the high-priced Microsoft HoloLens, to select cities in celebration of whisky season.

In this tutorial, you'll learn how to move a hosted domain from one hosting service to another. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Do you like going to parties but hate hosting them because it is just too work? Watch this video tutorial from Better TV to learn how to host a back yard barbecue party like a pro. Get the help of your friends and delegate tasks too to make the BBQ more fun and less overwhelming.

Living in a small space doesn't mean you have to forego hosting a holiday get together! This tutorial gives you some great tips on how you can not only host a party in a small house or apartment, but how you can do it on a budget, too.

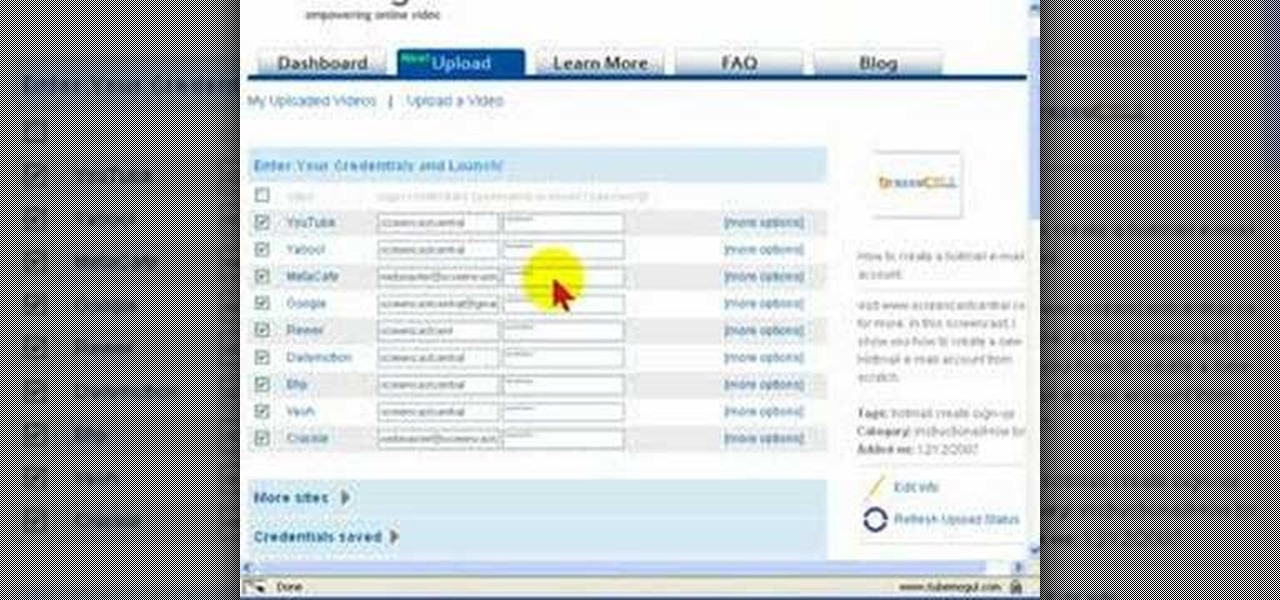
Uploading videos to multiple video hosting sites using Tubemogul.

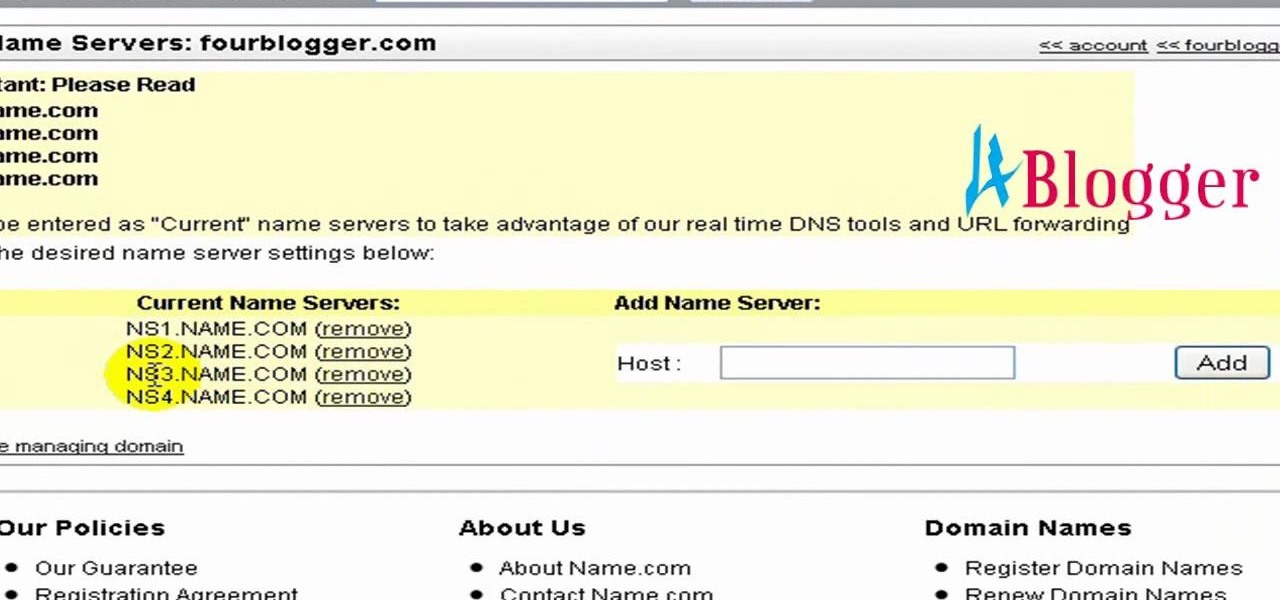
Edit name servers in the domain management area. If you're buying domain and web hosting from a single provider, like Hostgator, then the domain name automatically has a corresponding host.

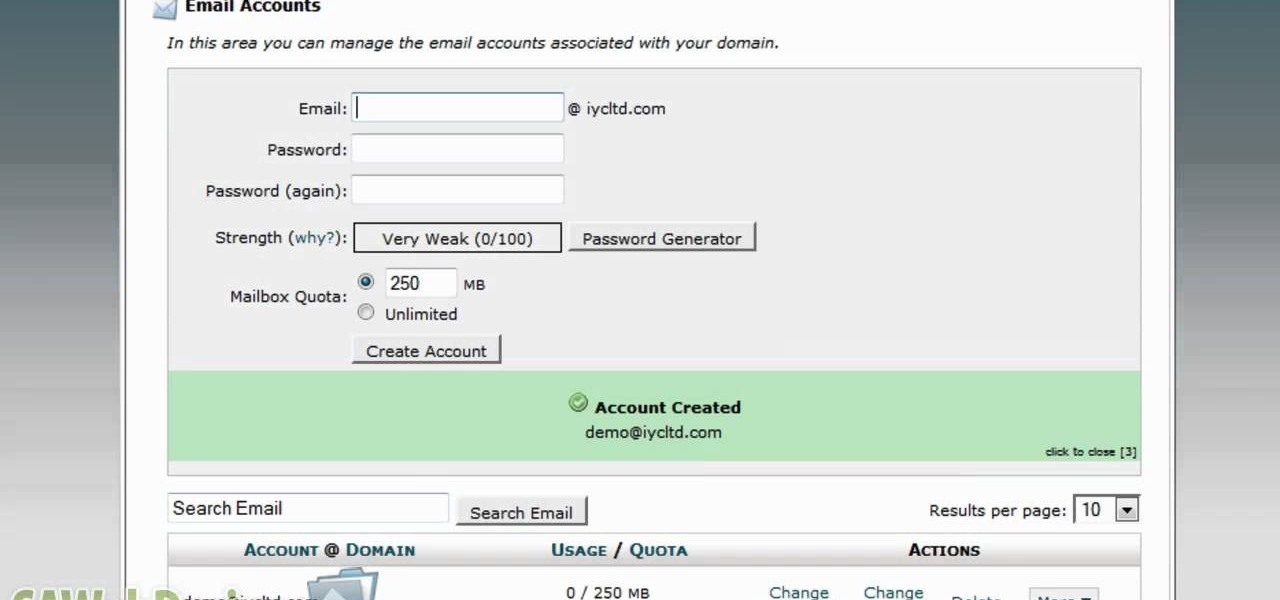
This tutorial is for people who are already using the cPanel Hosting account, and want to learn how to add a new email address to the existing account (such as for a new employee). It's an easy, quick process - this video shows you how!

Aspiring to be a game maker? You can get your start here. In this episode of the "All Things Adobe" hosted by the Chad and Todd podcast, co-host Todd Perkins tells you how to make Wii games in Flash! In this tutorial, you'll also learn how to play those games on your Wii after they're made.

"Every good party, needs some champagne," says Top Chef host Padma Lakshmi. In this tutorial hosted by Food & Wine, Padma along with Tom Colicchio (also from Top Chef) show us how to make raspberry champagne spritzers with some crushed strawberries, sorbet, and what else but champagne.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The term blog is a shorthand for web-log. It can be considered as a online and publically viewable diary of user generated content usually sorted by date.

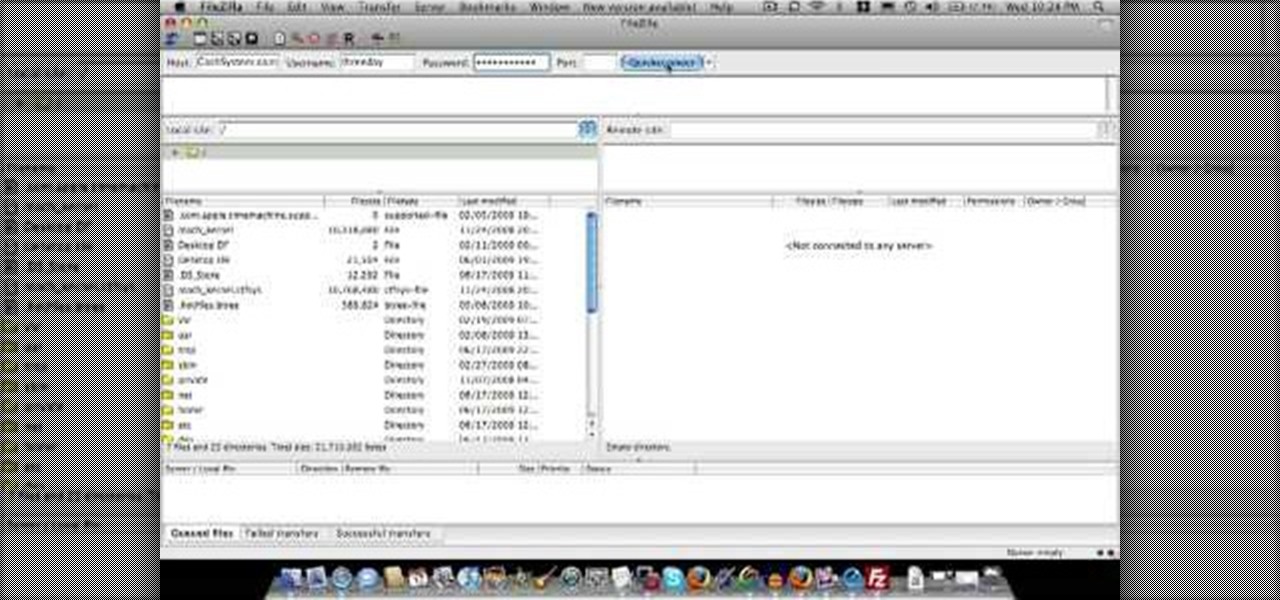
In this Computers & Programming video tutorial you will learn how to update a website with an FTP client (v† la FileZilla). Download FileZilla client from www.filezilla-project.org. Find your server IP address from your web host, which will be found in the hosting control center. In the video, it is GoDaddy.com. Open your filezilla client and put in the IP address of your web host and your username and password for your hosting account. Then click ‚Äòquickconnect‚Äô. This will connect you to ...

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

With the economy still rocky, many people can't afford to travel or host large, lavish Thanksgiving dinners. Even if you're planning on just having a small family gathering, here's how you can tweak some traditions to still have a memorable, intimate Thanksgiving.

In this video tutorial, viewers learn how to create a FTP from a local computer to a website. In this video, viewers are shown (once you've chosen a web host) how to perform FTP file transfers from your local computer to your website. FTP (File Transfer Protocol) is a process that you can use to transfer files from your local computer to a remote computer (your website). Once you've set up a hosting account, your hosting company will provide you with FTP login credentials. Using an FTP softwa...

This video shows how to get more value on your GoDaddy account. You have to have a deluxe account to share domains. You have to pay an extra $2 a month to get this account. Once you sign in go to "hosting" then my "hosting account". To add another domain you move it over to a new folder then put the site files in there. To do this, click add domain then go to bulk. Then create a folder and name it what you desire. Sometimes the file folder doesn't always appear immediately, but it is there, i...