The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

Cycling accidents are more common than you think. In the past month, two men have been hit and killed while cycling in New York City. I even saw a cycling accident occur yesterday morning here in NYC. It's dangerous enough to be cycling in populated areas, it's made worse by people wanting to text while riding.

Pokémon GO has been making the news since it was released last summer. But throughout the past year, the core gameplay has remained mostly the same. We're learning today that is about to change, as Niantic is gearing up to release a major update for the popular AR game.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

Niantic announced today that all gyms in Pokémon GO will be closed while the company prepares to celebrate two major anniversaries for the game. There will be updates, in-game celebration, and the first ever real-world Pokémon Go event.
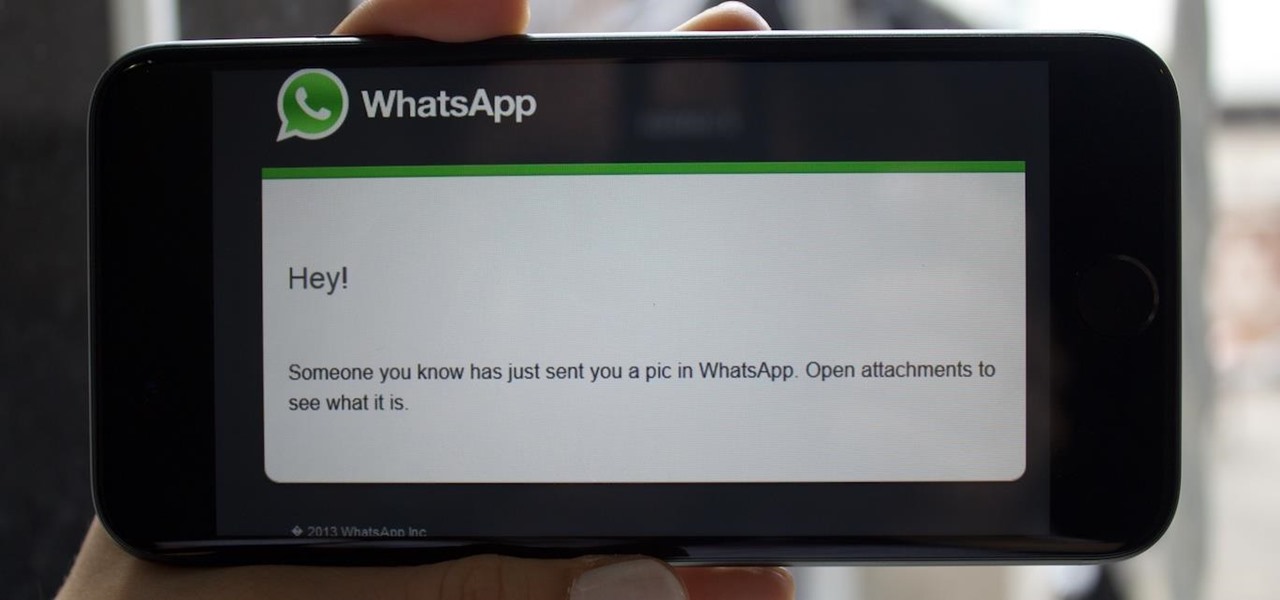
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update.

Texas has become only the latest state to face an unfortunate outbreak of mumps, but so far seems to be the hardest hit. On April 12, two days before the CDC's report was released, the Texas Department of State Health Services released a health advisory indicating this is the highest instance of mumps reported in 22 years.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Glitches can be extremely annoying when playing some of your favorite games, but sometimes, only sometimes, there are glitches in the game that give you an unprecedented advantage against the computer or other players online.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

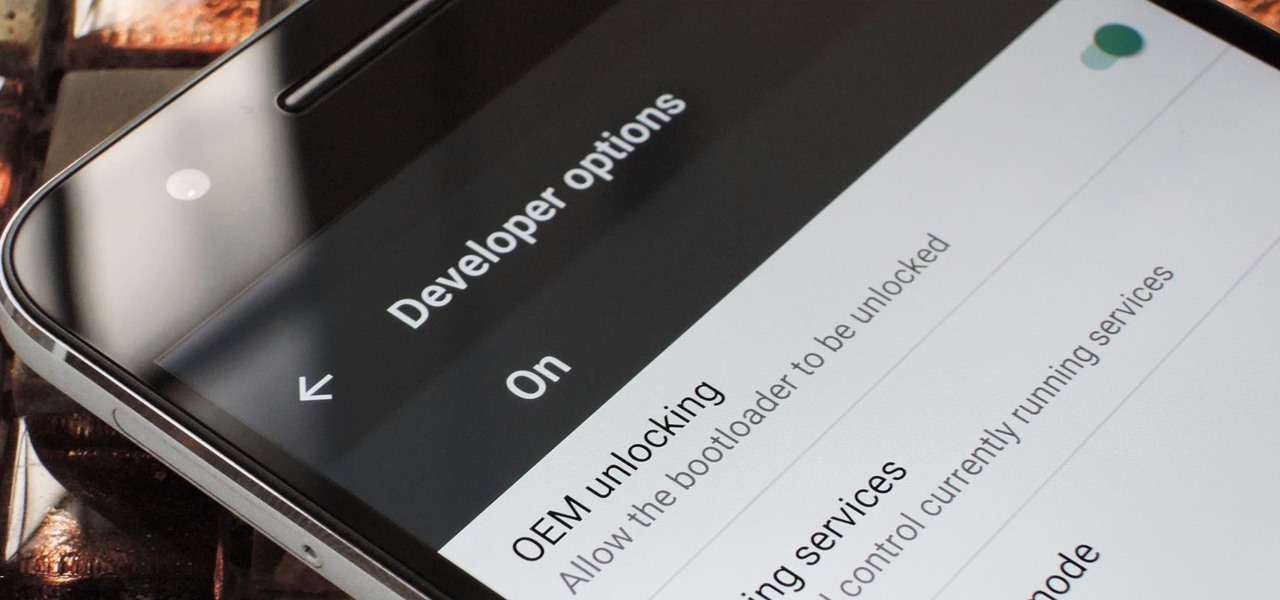
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.