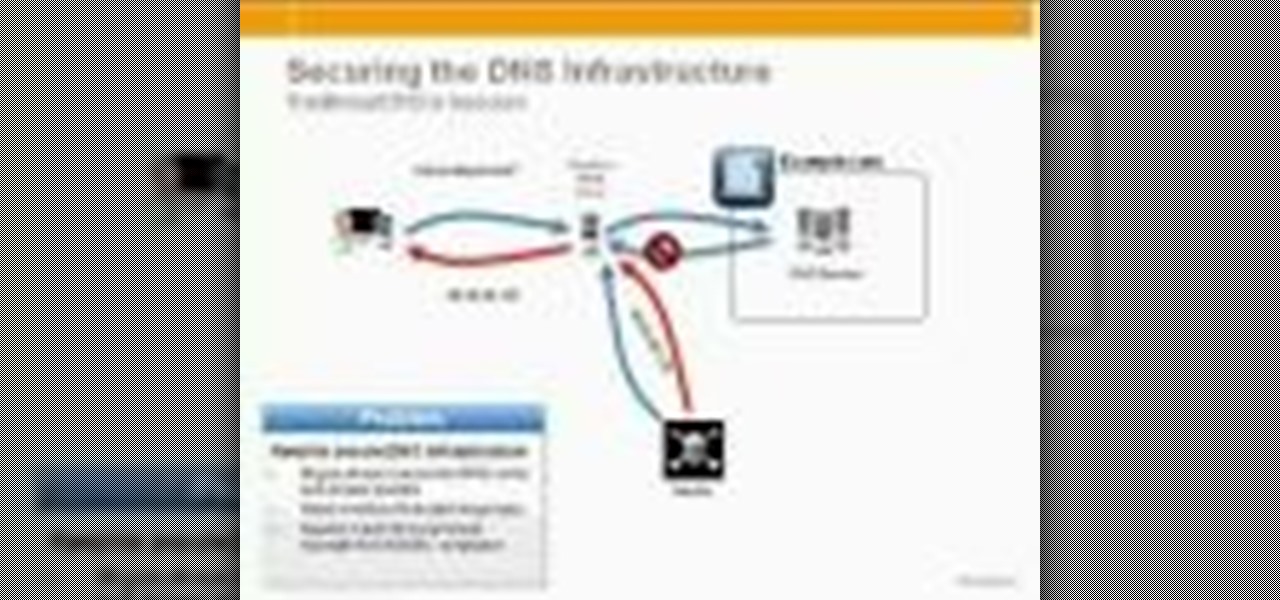
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

First, make sure that your image is hosted on a secure place online (such as your own Photobucket account). Then go to ImageMaps.com and use this free site to create your own image map that can now be added to your website.

Adding a SIM card to your Samsung Galaxy Tab is easy! If you have this new Android tablet and are looking to see how to install the SIM card, this video will clearly show you how it's done. Simply remove the slot's cover, insert the SIM card, making sure it's secure and snug, and then closing the cover. That's it!

If you have the chance to briefly talk and sit with a literary agent (such as at a convention), you only have so much time to impress them and pitch your book to them. These tips are the best ways to get an agent and secure representation.

MetaRL is a site you can sign up with that will let you accrue points that you can cash in for free online currency in your favorite online game. It's a very secure and perfectly legal way to get game currency without having to hack your games.

You can create some lovely and cute cloth pumpkins to decorate your house for Thanksgiving! All you need is some scrap material in fall or pumpkin colors, and a few rolls of toilet paper. Wrap the fabric around the toilet paper, tuck and secure!

When you film at home with just a regular camera using the built-in microphone, the quality can be bad to worse at best. If you are looking to improve the sound the best that you can with low budget solutions, check out this video. You will get tips on how to secure your locations and also how to monitor the sound going into your camera.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

Looking for an easy way to make certain that your sensitive personal information is secure? With Identity Finder, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.

VPN's are an invaluable set up for small business', and larger business', when it comes to keeping your information secure with remote employee's. This video details all of the info that you need to know about setting up and maintaining a great VPN!

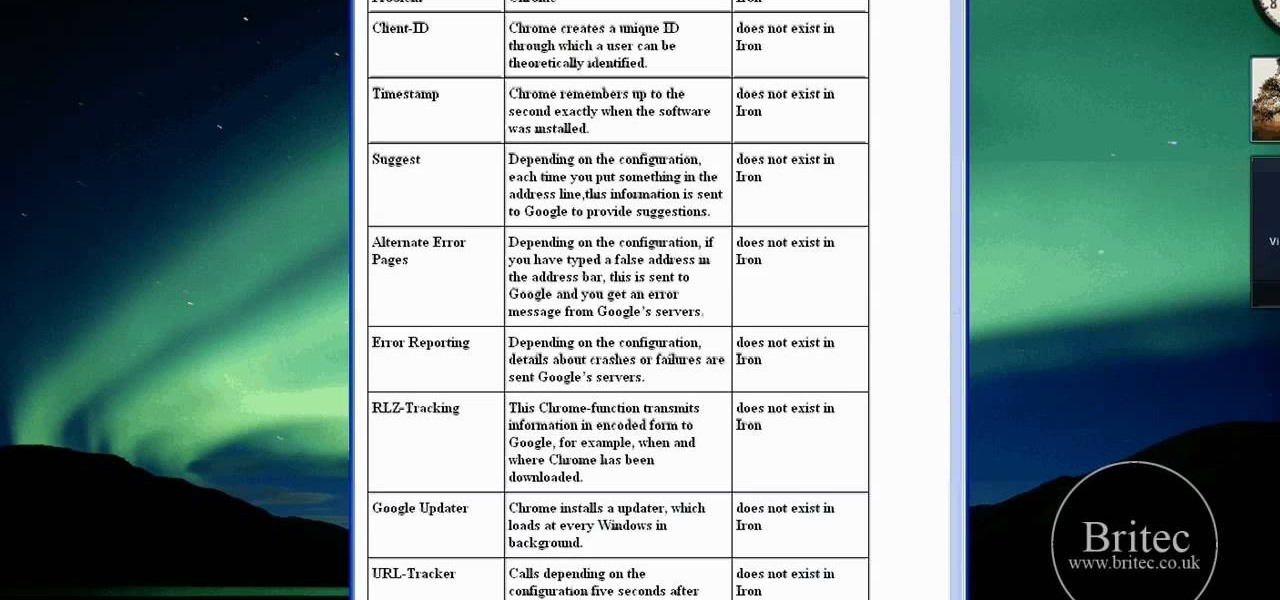
Interested in using Google Chrome but concerned about protecting your privacy while surfing the web? Meet Iron Browser, a secure but otherwise identical clone of the Google Chrome web browser. This clip from Britec will teach you where to find it, how to install it and how to get started using it.

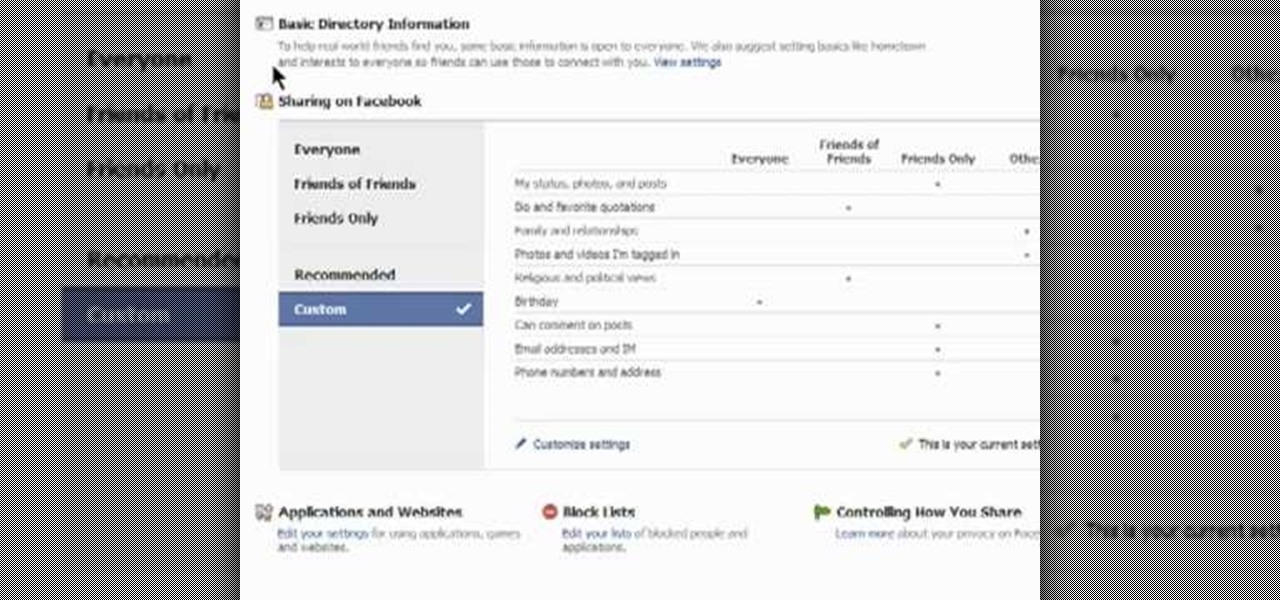
This clip presents an overview of the most important privacy settings on Facebook. Fortunately, with the right knowledge and the new Facebook Privacy Settings regime, protecting your data can be easy. So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions, take a look.

Materials: Scrap fabric, elastic thread, cardboard, scissors, cellophane tape, and other bits and bobs ie feathers, buttons

Installing beadlocks in your tires can help make sure that the wheel is secure and won't be going anywhere. There are many different types od beadlocks that can be purchased, but for this tutorial, you'll be finding out how to install one in an RC tire.

In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

From Ms Lola, learn how to attach a lace frontal so that it integrates with your existing hair. Lace frontals are designed to add thickness and length to thin and/or bald hair lines and crowns, where hair is needed. When applied correctly, they give a totally natural appearance, are extremely comfortable and stay secure for weeks! Learn how to strut your stuff in this unique style with help from this free video.

In order to put custom themes and such onto your iPod or iPhone, you will need to install SSH or Secure Shell. This tutorial will show you how to do this, step by step.

In this DIY clothes making tutorial, learn how to make a Japanese Obi belt, perfect to add to any little black dress. Traditionally, Obi refers to various Japanese belts and sashes used for attire such as formal kimonos and martial arts uniforms. Obi’s are often worn with kimonos to secure the robe in place as well for the purpose of decoration. In this tutorial, learn step-by-step how to make an Obi belt in the comfort of your own home.

You can make your own canopy for your boat and save hundreds of dollars from the store bought ones. You’ll need 1 inch pvc pipe, some nuts and bolts and you‘re set. You’ll set you’re canopy off of some swivel brackets that secure on the pvc pipe with 2 inch screws. This video will show you how to rig everything and you’ll be sitting in the shade in no time.

You will need about 3 yards of ribbon. Make a loop and twist it. Continue making more loops and twisting them until you have 4 or 5 loops. Make sure to secure the bow in the center with a tie of some sort. Snip off the edges. Following this video you can make a pretty bow for your friends gifts and they will love it.

This video tutorial shows you how to fix a collapsed volcano vaporizer. Replace vaporizer tubes with new ones. Trim them to fit with fingernail clippers. Use zip ties to secure tubes to vaporizer and other tubes to prevent future collapse. In the end, you want the square tube to jab into the side.

To join two strands of wool yarn, first you splay both ends about an inch or so. Next, overlap them and twist them together. Put the the twisted yarn in your mouth to moisten. Next, roll the moistened yarn between the palms of your hands to create a bond to and "felt" it. Tug to make sure it is secure and continue knitting.

Learn how to tie an Artillery Hitch or loop - A secure way of forming a loop in the standing part of a rope so that the loop lies perpendicular to the line. This is a good knot for sailing, boating, general outdoors and even bondage.

Learn how to tie a Round Turn and Two Half Hitches - a quick and secure way of attaching a rope to a railing or other fixed object. This is a good knot for sailing, boating, general outdoors and even bondage.

This is a cheap little hack from a $5 discount store headlamp. Check it out. Quick and easy. You need a bolt to secure to your camera. This is great if you are shooting long shots and need different brightnesses. Otherwise kind of ghetto.

This video tutorial will show you how to SSH file share on your Apple iPhone or iPod Touch, SSH meaning Secure Socket Shell. This is how you going to access your files on your iPhone or iPod, like videos and pictures. You will want to install the application OpenSSH in the system category on your device, and then download...

A new mailbox can change the look of your whole home. This how-to video offers tips for making sure your new mailbox is placed in a safe and secure location, and is installed so it will stay sturdy. Watch this video home improvement tutorial and learn how to install a mailbox.

This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information on this hack, watch this helpful video guide.

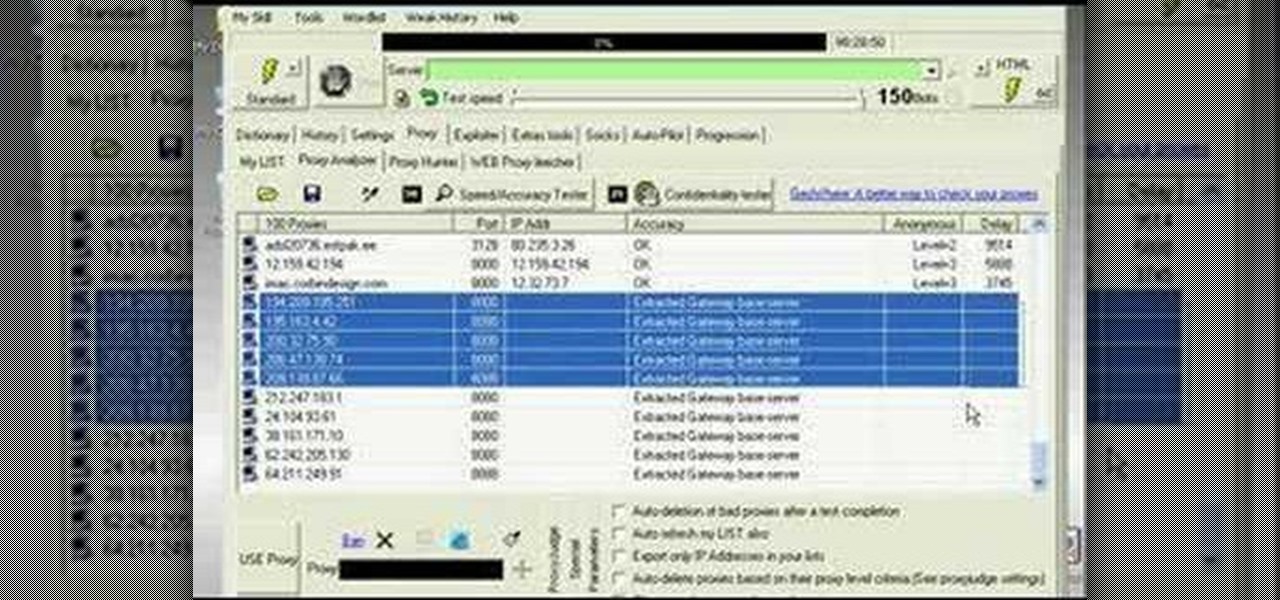
AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

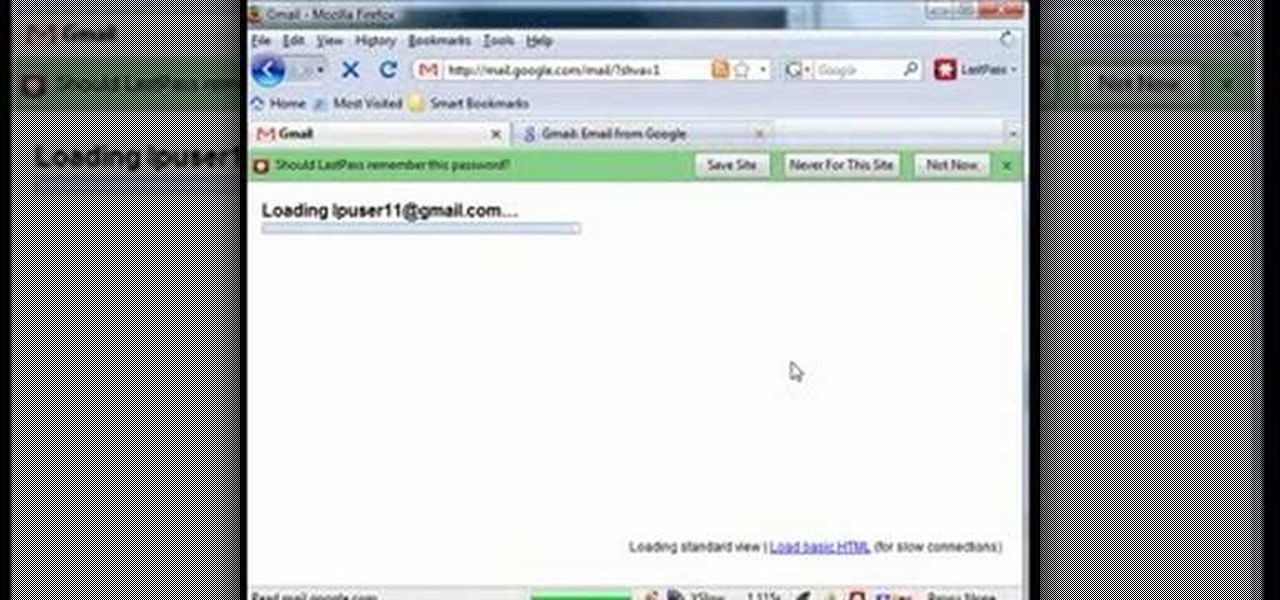
LastPass is a free password manager and form filler that makes your web browsing easier and more secure. This video tutorial presents a basic introduction, demonstrating the basics of using the LastPass Password Manager. Learn how to use LastPass with this how-to.

LastPass is a free password manager and form filler that makes your web browsing easier and more secure. This video tutorial presents a simple demonstration of new Form Fill feature from LastPass. Take a look.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about protecting your VBA code from snoopy little trolls. For more information on keeping your VBA code secure, watch this MS Access how-to.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Shoot a compound bow safely and accurately. Learn these great tips for shooting a compound bow in this archery video tutorial. Take action: use release for accuracy, push arrow until "click," secure everything, and use proper form. John Swindle, the instructor of this how-to video from Live Strong, is the owner of Arrowhead Archery in Tampa, Florida. He has been an archer and a bow hunter for over 18 years.

Watch this instructional quilting video to learn how to blind stitch. A blind stitch is terrific when you don't want stitching to show through on the face of your fabric. You will be able to attach a label, secure your binding, and attach appliqué pieces to your quilt.

How do I stop knitting? This instructional knitting video demonstrates how to do a basic knit bind off. Binding off is the process of taking the stitches off of your needle and securing them so that they don't unravel. The basic bind-off using knit stitches most popular with beginners. This version of the knit bind of is typically used with the stockinette stitch.

Use this camera modification to secure the Holga back to the camera and to provide a light blocker for the counter window. You will need a small package of velcro with industrial strength adhesive. This photography tutorial provides tips for making your vintage Holga camera easy to use in hectic shooting situations.

Check out this instructional boating video that demonstrates how to tie a cleat hitch for boating. This is a type of hitch used to tie a line to a cleat. All you have to do is make one full turn then a figure 8 with the last turn reversed and you've got your cleat hitch tied. Learn how to tie a cleat hitch or a cleat knot with this boating tutorial video and keep your boat secure to a dock.

Hitches are knots that are relatively adjustable, so they're not usually used for intense securing. The highwayman's hitch, as demonstrated in this how-to video, comes untied very quickly and easily by pulling on the release loop. Watch this video knot-tying tutorial and learn how to tie a variant of the highwayman's hitch knot.

Learn how to use the cable key to tighten your Knit Picks Options Interchangeable Knitting Needles. Each needle tip has a hollow base that is grooved to accept the threaded stem of the cable. To insure a secure fit, use a cable key to tighten the knitting needle tip. You can also use the cable key to unscrew your knitting needle when you are ready to start a new knitting project.