The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

It doesn't really matter what kind of cell phone you have—battery life is one of the most important features for any electronic device. We've written tons of articles on how to get better battery life from your Android, iPhone, Kindle, and more, but we've never really covered Windows Phones before—until now. The Nokia Lumia 920 and other devices running Windows Phone 8 suffer from battery problems just like any other mobile device. So, if you've got one in your hands that can't seem to make i...

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

Always downing a glass of red wine in the evening? Don't be ashamed. Red wine has some great health benefits when consumed in moderation, including improved memory, lower risk of heart disease, and even bone strengthening. Photo by Joe Shlabotnik
With how quickly technology evolves in this day and age, it's only natural that people replace their computers every couple years—even sooner. It seems that right when you get a new desktop, there's always a faster model with more features released the following week.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

If your battery in your Apple iPhone is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your battery in your Sony PSP is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your LCD screen in your Sony PSP is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your LCD screen on your Nokia N95 cell phone is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your LCD screen on your P4350 Herald Dash cell phone, otherwise known as the T-Mobile Wing or XDA Terra, is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your hard drive in your Microsoft Zune MP3 Player is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your battery or your LCD screen in your Microsoft Zune MP3 Player is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

If your battery in your Microsoft Zune MP3 Player is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Your iPhone has seen a lot of new features in a very short amount of time. For starters, iOS 13 introduced over 200 of them, including, among many others, system-wide Dark Mode. Before you even had a chance to breathe, however, iOS 13.1 came along and dumped an additional 22 features in your lap. For us beta testers, now its time to explore new features all over again with the first public beta for iOS 13.2.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

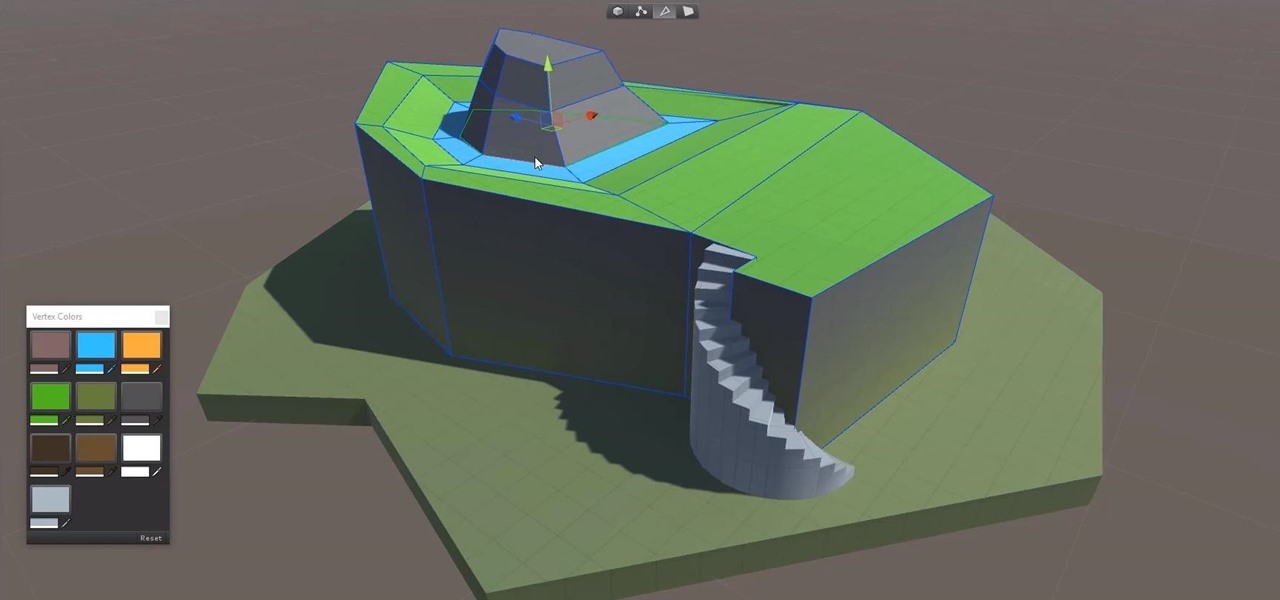
Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Even if your cat drives you a little nuts, don't worry, because a new study says that cats pose no risk to your mental health.

Wait, don't dump that milk! It may have a slightly sour smell and be expiring tomorrow, but you can still put it to good use by making sour milk jam.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

In my opinion, spices are the key to a successful kitchen. With a healthy array of spices and spice mixes, you have the foundation for nearly any dish that you want to make; the culinary world is your oyster. With a depleted cupboard of spices, however, nearly every recipe looks intimidating and unattainable.

Many of you have heard of "ricing" cauliflower. If you haven't, you're missing out making this one-note vegetable into a variety of main and side dishes. The ricing process is so simple, fast, and easy that even the most novice cook can swing this. One you complete this prep step, you will have an ingredient so versatile that you can easily fool your kids into eating their veggies without them ever knowing it.

You've heard the old saying, "When life gives you lemons, make lemonade." Well, the same goes true for snow. When Mother Nature dumps loads of the white stuff onto your neighborhood, then make the most of it with treats like maple snow candy, snow ice cream, and snow cocktails.

Okay, it's true: even the highest quality instant coffee is never going to replace really good fresh beans (and properly cleaning your coffee maker) when it comes to creating a great cup of joe. However, instant coffee does have all kinds of uses in the kitchen, as the smart folks over at Reddit observed.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.

It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort.

If you drop your smartphone in water, take it apart as much as you can and place it in rice. It's been the most recommended method of cell phone rescue since the days of clamshells. In fact, it's usually the only thing recommended when searching for "how to save your wet phone." Turns out, we've been wrong all along.