Android devices are known for their USB and Wi-Fi tethering abilities—rooted or unrooted—which comes in handy for those that travel and need internet on their laptops in areas that don't have any Wi-Fi networks available, but have a strong cellular signal.

As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.
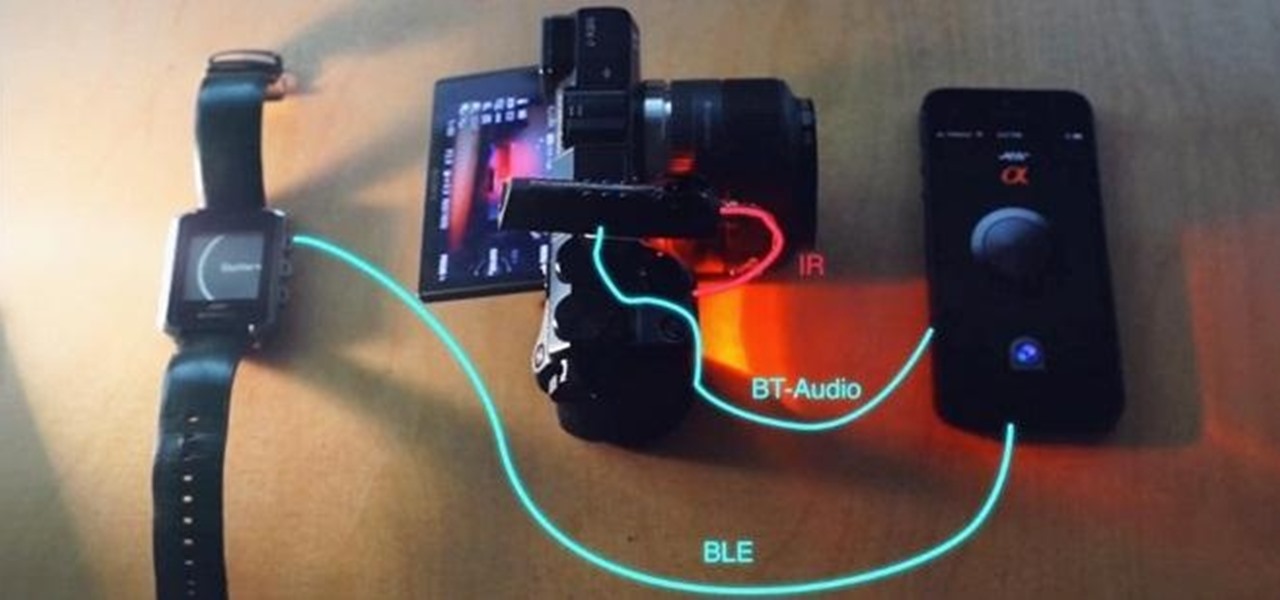
You can add Bluetooth capability to an old stereo, a retro mouse, or even your car's cassette deck. If you can think of a device, someone has probably found a way to control it with Bluetooth.

Most of us have traded our desktop systems for laptops, tablets, and mobile devices, meaning there's a lot of outdated hardware sitting in attics. Want to give your old computer a new purpose? Matthew Chappee turned his iMac G4 into an HDTV using the guide by Dremel Junkie. One thing to note before you take on this project yourself is that if you want to use it to watch cable, you'll need a converter box to get around the MPAA's HDCP restriction. But, a converter box is considerably less expe...

Combination locks in Minecraft can be really simple or frustratingly difficult, but no matter how complicated they are, some of them fall victim to the same simple exploits.

If you've ever been on your way to a party and felt that your outfit just wasn't flashy enough, engineering student 'Rambo' has got just the thing for you. His homemade LED suit lights up and dances to the beat of the music, and can even be controlled via Bluetooth.

Looking for a way to make your bike stand out? You could light it up with LED rim lights or turn signals. Or if you're looking for something a little less flashy, you could make your own set of custom wooden handlebars like these by furniture designer David Moore. To actually make these wooden handlebars, you will need some woodworking tools, not to mention some actual woodworking skill, or at least the tools and some knowledge on bending and forming wood. In his video below, David shows exac...

Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

Enjoyed throughout the Middle East, Arabic coffee is deliciously rich, and easy to make at home. Watch this video to learn how to make Arabic (or Turkish) coffee.

If you plan to travel in a remote location, grab a CD before you go it could save your life. Here's how to use a CD to make an emergency signal.

When it comes to used cars, it’s hard to make lemonade out of a lemon. So don’t get stuck with a piece of junk in the first place.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Impress dinner companions with your flawless manners—it’s as simple as observing a few key rules. You Will Need

In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

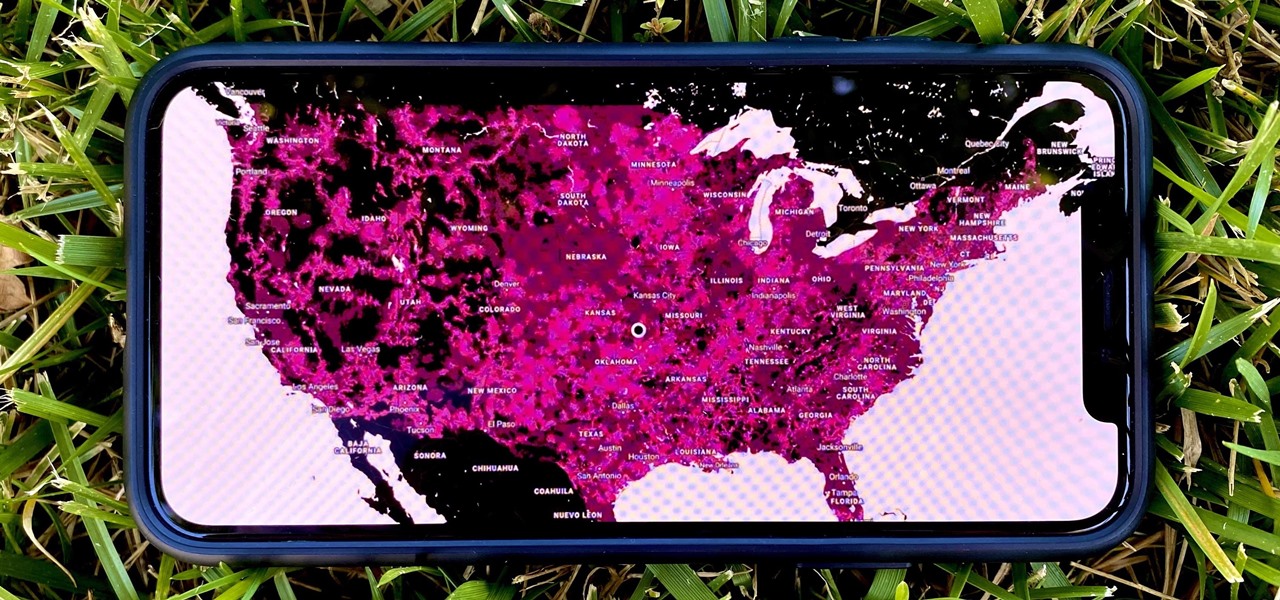
If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

From nursery rhymes, to rap songs, to love poems, rhyming is an important part of the English language. If you're feeling a little shaky on your rhyming abilities, glance over some of these simple rules and you'll be off and rhyming again.

In this brief video tutorial, you'll see how to properly use Agilent's InfiniiMax Active Probes for oscilloscopes, with multiple probe heads to connect to your high speed signals under various probing use models. First, begin by learning to use Agilent's Browser Probe Head under both handheld and probe stand use models. Also, see the use of their Solder-In Probe Head and the Socketed Probe Head. Then they conclude by showing how to use the SMA Probe Head.

Wireless can be a pain sometimes with video games on the Internet, with disconnections and signal losses, but why not revert back to a wired connection? This video will explain how to connect your Nintendo Wii to a wired network using Actiontec Powerline Networking technology. This will enable your Nintendo Wii to connect to the Internet to download games, console updates, and other information.

What Is Ferrofluid? Ferrofluid is a black, solvent-based liquid, that, in the presence of a magnetic field, becomes strongly magnetized. The fluid is made up of nanomagnetic particles coated with an "anti-stick" or surfactant compound, suspended in a "carrier", commonly an organic solvent. For mechanical applications, it is used in hard drives and speakers as a lubricant. However, it also has been implemented in artwork, as seen in the video below.

One sure fire way to add excitement to a summer day when you think it's just too scorching to go outside is by having a water balloon fight. This is a great way to stave off boredom and you'll be sure to feel like a kid again while getting some fun exercise.

You love your hooded sweatshirt but starting to feel like a weak person is strangling you all day long? With a quick snip with the scissors you can have a perfectly fitting sweatshirt and never have to worry about unnecessary discomfort again.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

One of the major additions in the Google Pixel 4 is the new Soli chip. It's the miniature radar sensor that powers Motion Sense, a new way to interact with your phone without touching it. There are a few new gestures you'll need to learn to take advantage of Motion Sense, so let me break them down for you.

Look Around in Apple Maps gives you a high-resolution 3D view of roads, buildings, and other imagery in an interactive 360-degree layout. We haven't had anything like this in Apple Maps since iOS 5 when Google's Street View was incorporated. Now, in iOS 13, seven years later, we have street-level views again, only better. But Look Around isn't available everywhere yet.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

Ever since Skynet took over the world in the Terminator film franchise, a large segment of the world's population has feared artificial intelligence.

Alongside its official unveiling of the lower-cost Pixel 3a smartphone at Google I/O, Google took the opportunity to extend its early preview of AR walking navigation in Google Maps to all Pixel devices.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

In recent years, Apple has assembled its augmented reality team and supply chain through a series of acquisitions, high-profile hires, and strategic investments, but at least one potentially major deal was recently ditched.

On Thursday, yet another piece of the Magic Leap puzzle fell into place at Twilio's Signal developer and customer conference in San Francisco.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.