If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?
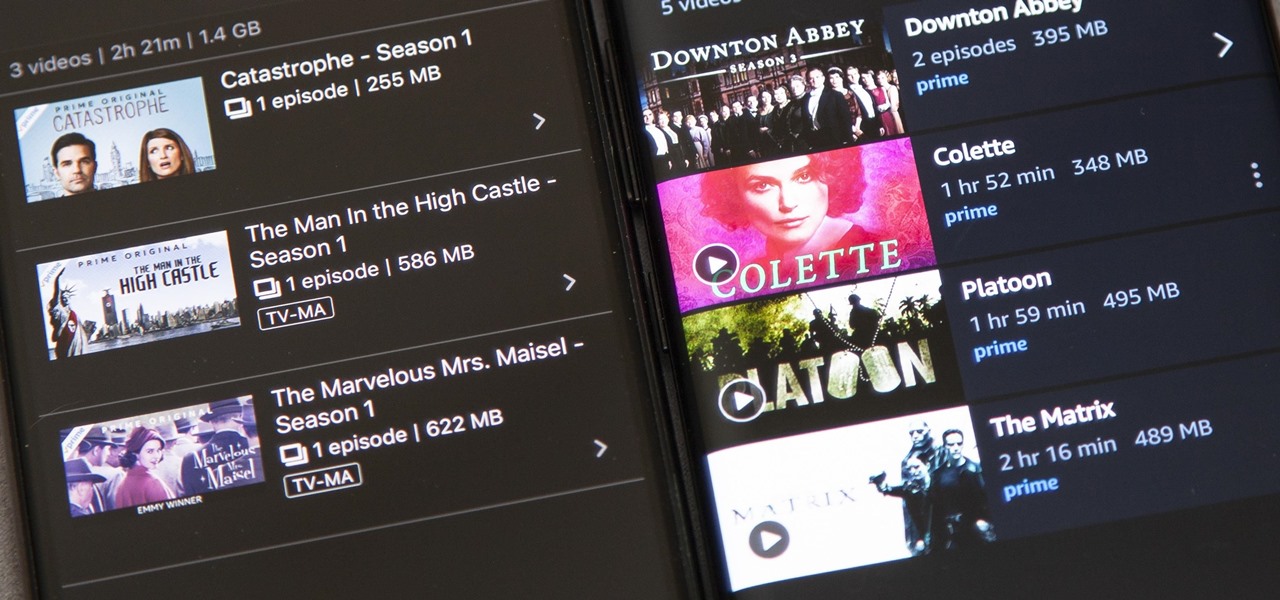
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Google just released the second developer preview of the Android 8.1 update for Nexus and Pixel devices, and even though it's just a point-one release, there are lots of cool changes. Before you run off to join the Android beta program and try the new version, it's worth reading up on what's new.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Lack of appetite often signals a cold or flu. Eating can be the last thing we want to do when we have a sore throat or are too fatigued or achy to even get out of bed. When hungry, we don't feel as strong as when we are well fed—and we more than likely aren't as strong.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

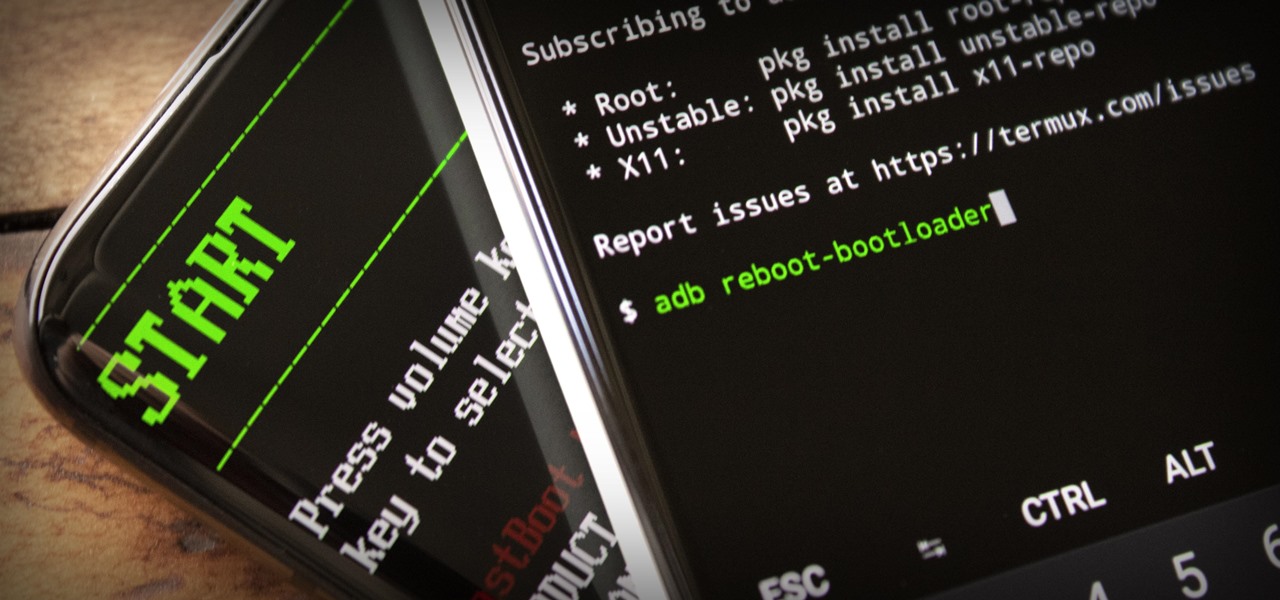
If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

Since 2020, you've been free to set your preferred web browser and email app as the default on your iPhone or iPad. Now, four years later, Apple is expanding this flexibility in the U.S., allowing even more apps to be set as defaults for specific actions. Plus, there's now a centralized menu to manage all these default app settings.

Your iPhone has a neat trick up its sleeves that gives you total control over the focal plane in all the portraits you've already snapped. This gives you the power to significantly enhance the composition and emotional impact of each image. In some cases, you can even focus on new subjects in regular stills and Live Photos.

Your iPhone has hidden apps that work behind the scenes to filter SMS messages, trust computers, deal with payments, test ads, and perform other actions. You won't find any of them in your App Library, but there are tricks you can employ to unlock and use some of these secret apps.

Microcontrollers like ESP8266-based boards have built-in Wi-Fi, and that's really cool, but what's even cooler is that certain pro models of the D1 Mini also have a port where you can connect a directional antenna. This can give you exceptional range, but if you were to just plug one in after opening the package, it most likely wouldn't work.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

Your Galaxy uses information from your SIM card to communicate with nearby towers and facilitate a connection. Which LTE bands you are assigned depends on a number of factors, including available bandwidth and your device's supported signals. But if speeds aren't great on your auto-selected tower, you can improve things by manually choosing a band.

In iOS 13 and under, whenever you were in an app or on the home screen, and a Phone or FaceTime call came in, the entire screen would be taken over by the incoming call. Apple changed it to a subtle banner notification in iOS 14 so that it doesn't wholly obfuscate what you're doing when the call happens. However, you can get the old design back if that works better for you.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.